Oracle HeatWave is a fully managed cloud database service that integrates with MySQL, combining transactions, analytics, machine learning, and generative AI capabilities. It features an in-memory query accelerator for real-time analytics, eliminating the need for ETL processes to separate databases. Available on Oracle Cloud Infrastructure (OCI), AWS, and Azure, HeatWave automates tasks like backups and patching, offering high performance, scalability, and security for OLTP and OLAP workloads.
Cloud database security isn’t just a best practice—it’s an absolute necessity. With sensitive data flowing into the cloud, protecting your business-critical assets is non-negotiable, and Oracle Cloud Infrastructure (OCI) HeatWave MySQL provides robust features to help. This blog explores customer managed encryption key, the related backup strategies, and the required security policies so you can keep your databases both agile and secure.
Why do we need the encryption key?
Security is not static—stale keys lead to risk of systems being compromised. By default, Oracle provides data encryption for data at rest using Oracle managed keys. Many customers as a security policy, require that they control the encryption for their sensitive data. With this new capability, customers can now change (rotate) the customer-managed encryption key (CMEK) at any time. This is vital for:
-
Adhering to compliance mandates for regular key rotation.
-
Quickly responding to a suspected security event by rendering previous backups and data volumes inaccessible without the new key.
Storing data securely begins with encryption, ensuring that even if the physical media is compromised, your data remains unreadable.
How the encryption key works
-
When you create a HeatWave MySQL DB system or HeatWave cluster, you can select a customer-managed key from Oracle Cloud Vault.
-
This “Advanced Option: Encryption Key” means encryption and decryption don’t rely only on internally managed keys; you determine and control the key lifecycle.
-
Your selected encryption key protects the HeatWave MySQL data volumes and the automatic backups taken by the service.
Note: Database operations will be affected if the key is disabled, scheduled for deletion, or deleted. You can enable a disabled key or cancel the deletion of a key in pending deletion state to restore the full operations of the database. But if the key has been deleted without any backup, access to the database or backups will not be possible.
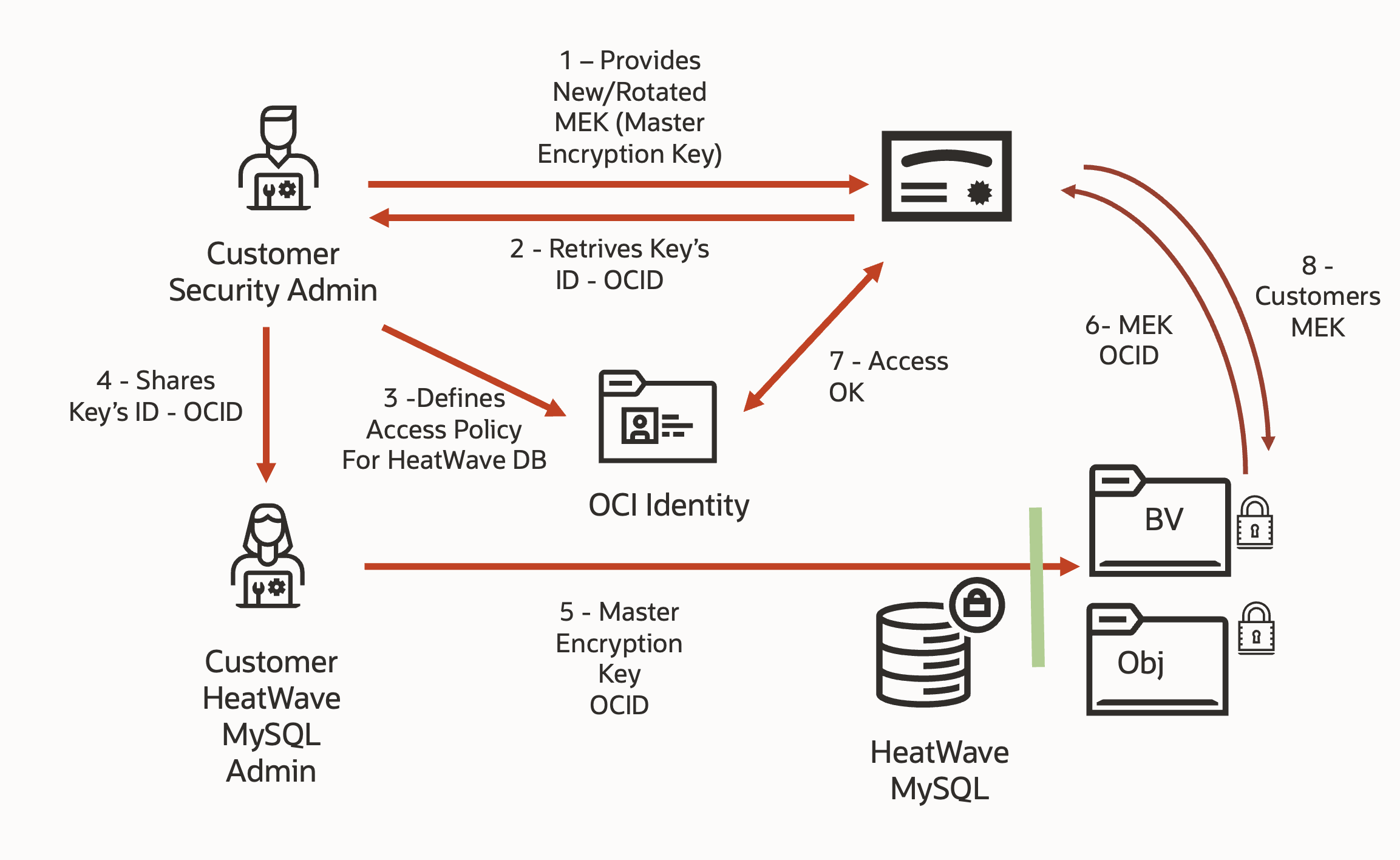
Set up and configuration of CMEK
All of these capabilities depend on having the right permissions in place. OCI uses IAM policies to control access to HeatWave MySQL and Oracle Cloud Vault.
Mandatory Policies and Permissions
To enable key management and backup operations, ensure the following:
- Setup necessary Vault permissions (to use, manage, and update keys).
- Enable access to create, update, and restore backups.
- Cross-region operations require explicit permissions in both source and destination regions.
- Set up OCI Key management services for storing and managing keys for your region.
-
Create a new vault or use an existing vault and setup encryption keys.
-
The customer-managed key can be any valid key in target region that the user owns.
-
Ensure the customer-managed key uses AES encryption.
-
- Set up mandatory policies (under section “bring your own key”) for user groups to read vaults required for Customer managed key. This ensures your team can manage the tasks related to copy and restore of the DB system.
Mandatory Policies:
Allow group <group_name> to read vaults in compartment <vault_compartment_name>
Allow group <group_name> to read keys in compartment <key_compartment_name>
Allow any-user to use key-delegate in compartment <key_compartment_name> where all {request.principal.type = 'mysqldbsystem', request.resource.compartment.id='<DBsystem_compartment_OCID>'}
Allow service blockstorage, objectstorage-<region> to use keys in compartment <key_compartment_name> where target.key.id='<key_OCID>'
Endorse any-user to {VOLUME_UPDATE, VOLUME_INSPECT, VOLUME_CREATE, VOLUME_BACKUP_READ, VOLUME_BACKUP_UPDATE, BUCKET_UPDATE, VOLUME_GROUP_BACKUP_CREATE, VOLUME_BACKUP_COPY, VOLUME_BACKUP_CREATE, TAG_NAMESPACE_INSPECT, TAG_NAMESPACE_USE} in any-tenancy where request.principal.type = 'mysqldbsystem'
Endorse any-user TO associate keys in tenancy with volumes in any-tenancy where request.principal.type = 'mysqldbsystem'
Endorse any-user to associate keys in tenancy with volume-backups in any-tenancy where request.principal.type = 'mysqldbsystem'
Endorse any-user to associate keys in tenancy with buckets in any-tenancy where request.principal.type = 'mysqldbsystem'
-
Check KMS key lifecycle and ensure KMS key is ‘enabled’.
DB system creation flow:
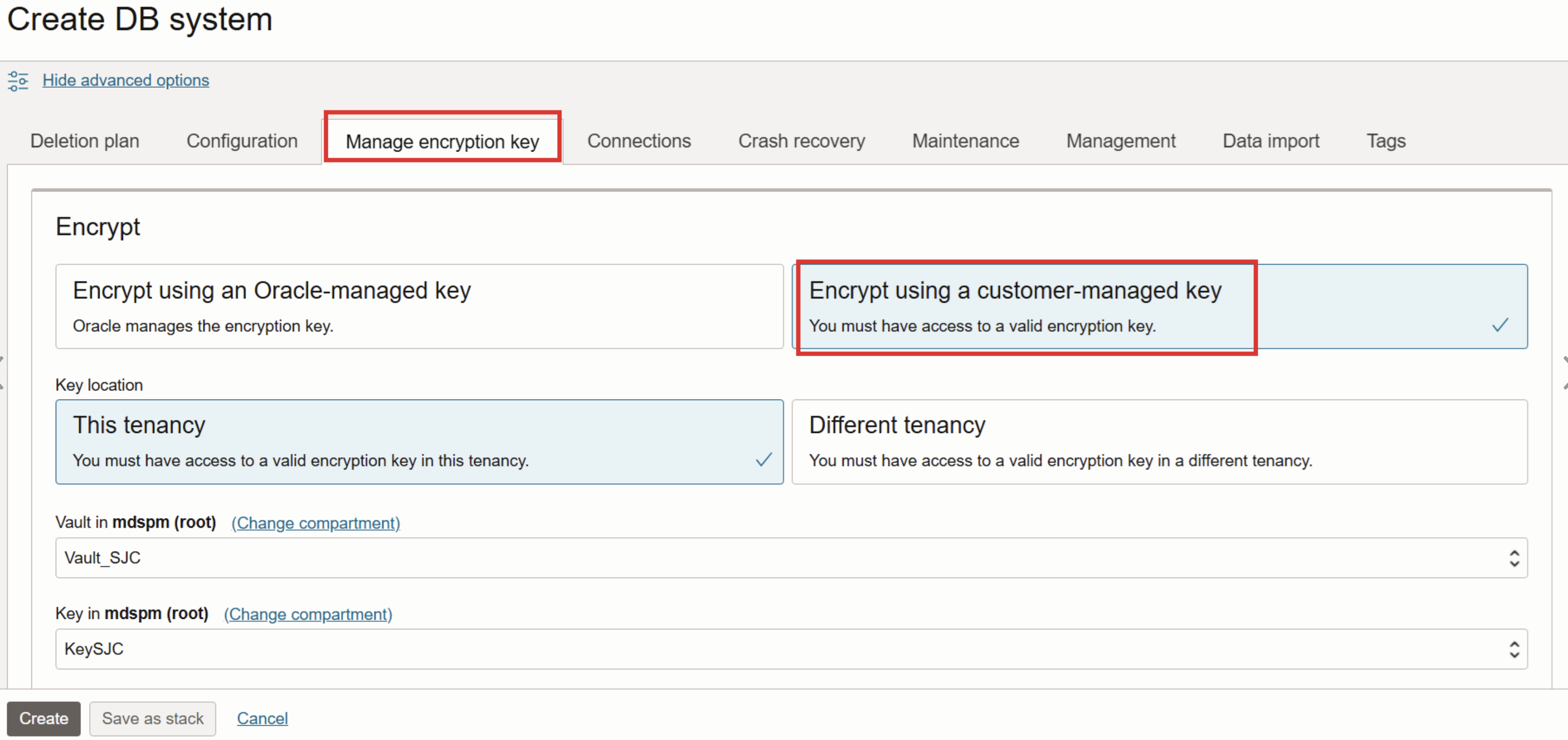
During the initial DB system creation setup, follow the below steps to setup customer-managed keys.
In the OCI console, navigate to Databases, HeatWave MySQL, and on the DB systems page, click Create DB systems. Navigate the sections of the provisioning flow and in the advanced options section – select the option ‘Encrypt using a customer-managed key’.
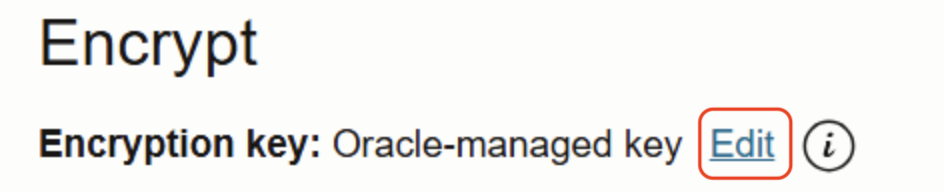
Update option:
If you already have an established Database System and then you can edit the encryption method.
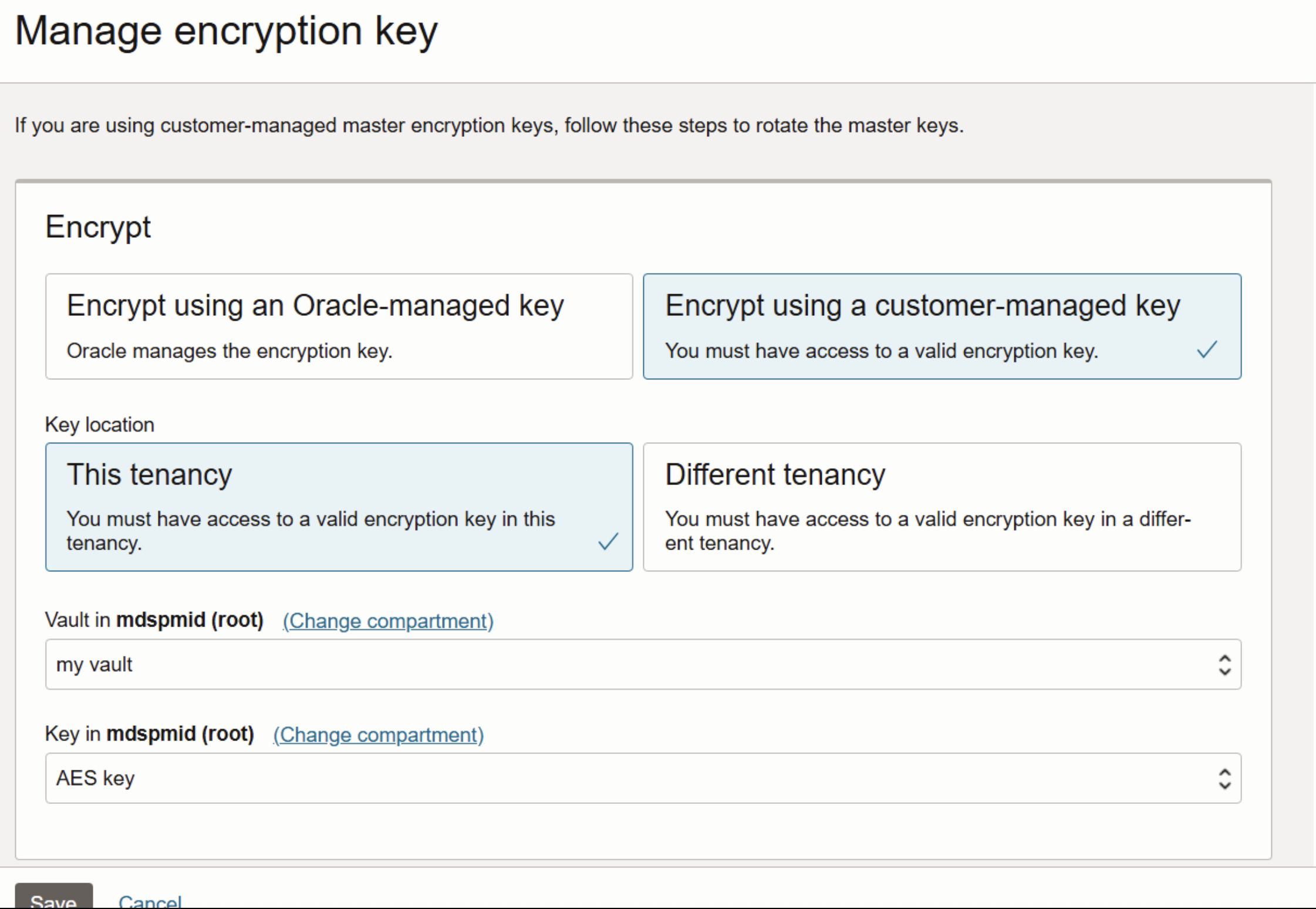
In the OCI Console, click on DB systems you want to edit and navigate to Encrypt section –>Edit→ Select Encrypt using a customer-managed key.
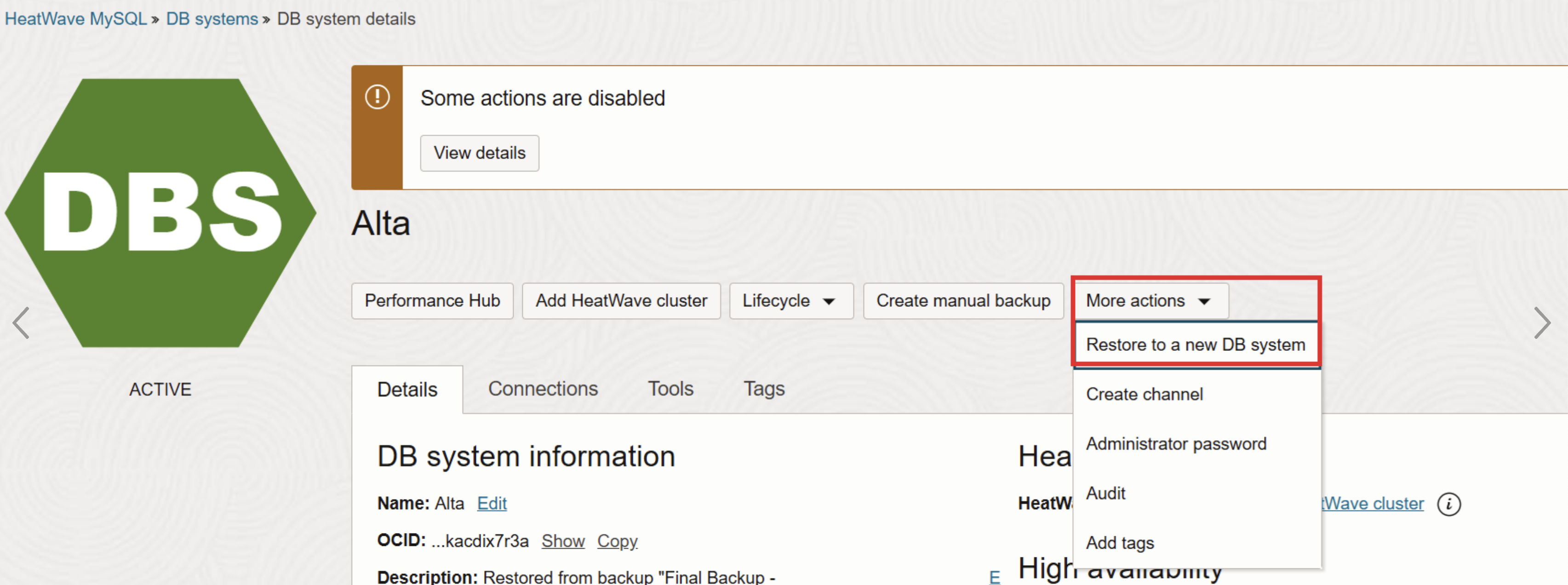
Restore backup to new DB system
In the OCI console, navigate to Databases, HeatWave MySQL, and on the DB Systems page, select the DB System. Click on ‘More actions’ drop down.
Select the ‘Restore to new DB system’.
Select the source of the backup to be restored.
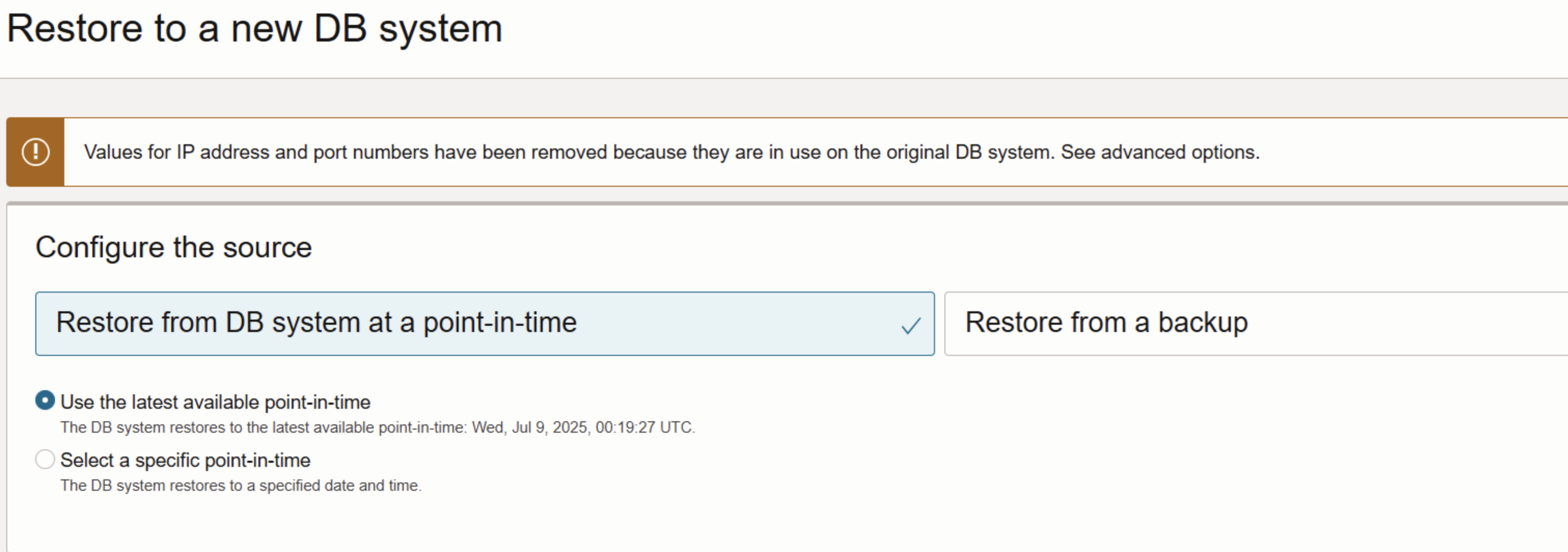
A backup restore can be done in the same region or cross region. The new DB system won’t use the key from the backup. While restoring, the user must select a CMEK for the new DB system to use, otherwise the new DB system will use Oracle-managed key.
Copy backup to another region
Disaster recovery and geo-redundancy are essential parts of business resilience. HeatWave MySQL makes it straightforward to copy a backup to another region, letting you recover from regional outages or migrate workloads effectively. DB system backup can also be restored to another region with customer-managed key.
By default, a backup copy will use Oracle Managed key, if a CMEK is not selected during copy backup. The user must select a valid key from the OCI Vault valid in the destination region to encrypt the backup.
This feature helps achieve high availability and meet compliance obligations around data residency.
This seamless process ensures uninterrupted service during key updates, combining security with business continuity. See how to update your encryption key.
Conclusion
Managing encryption keys, performing seamless failover backups, and enforcing robust IAM policies form the backbone of a secure HeatWave MySQL deployment.
Choose OCI HeatWave to empower your business with a secure, scalable, and high-performance database solution that meets the most demanding compliance requirements. Unlock the full potential of your data today with OCI’s cutting-edge technology and take control of your security like never before.
Ready to fortify your cloud data strategy? Start exploring the Oracle Cloud MySQL Database Service docs.
Resources:
Advanced Option: Encryption Key
Copying a Backup to Another Region
