Review Part I of this Blog post here
How Companies Can Protect Themselves
There are several ways in which companies can protect themselves against cyber threats and attacks, as ’it’s just a matter of “WHEN,”” not “IF” anymore. A good start is to make employees aware of what social engineering and phishing attacks look like; as previously stated, most cyber-attacks begin with human error.
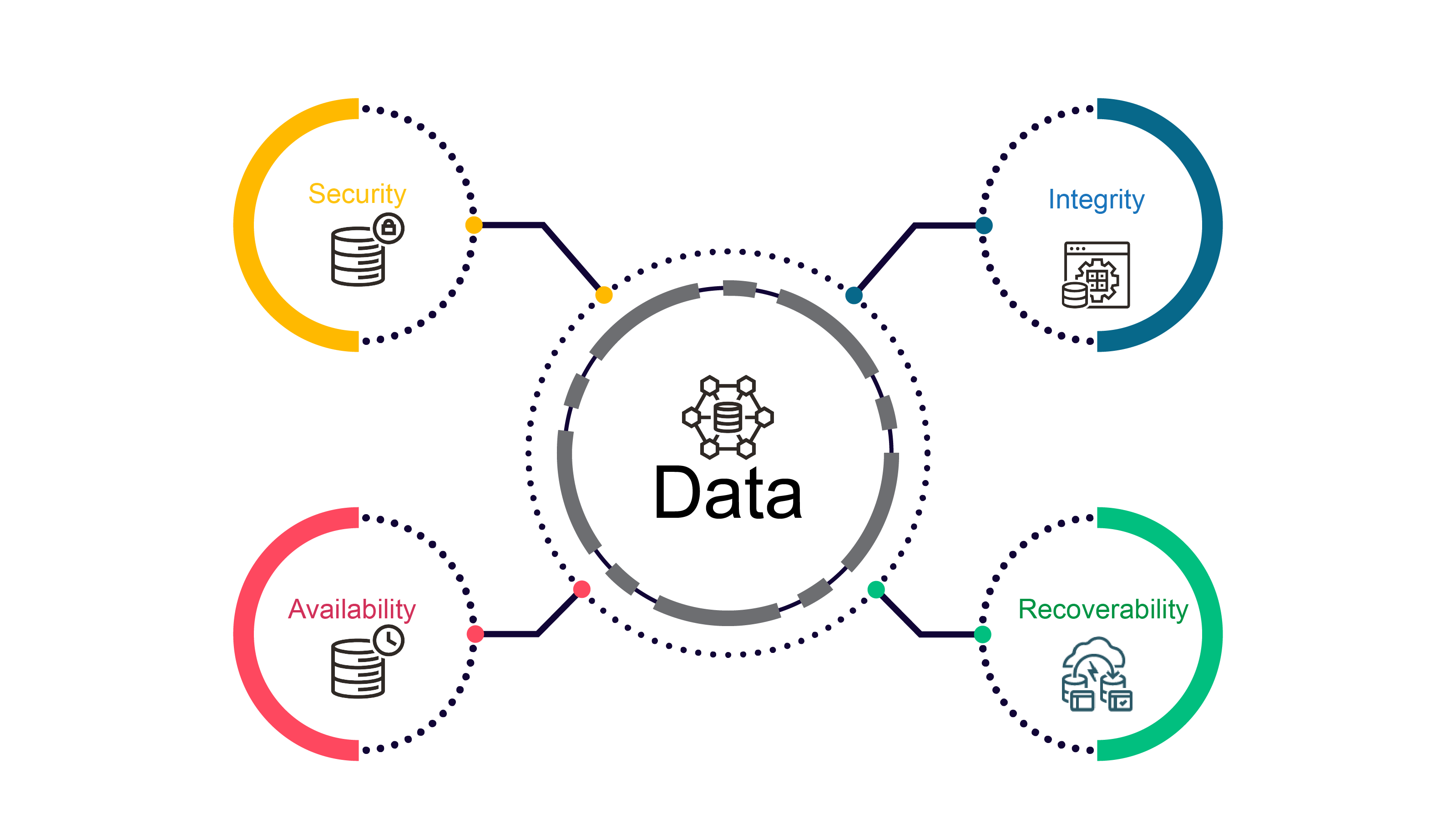
Companies should also consider implementing architectures such as Oracle MAA and Oracle MSA to improve their data security, integrity, availability, and recoverability. These Oracle frameworks are based on industry best practices and could become the foundation to help your organization to achieve industry-specific security certifications.
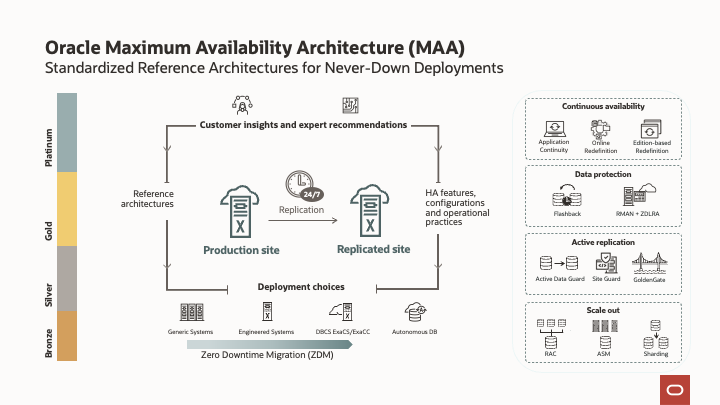
Oracle MAA helps organizations quickly patch security holes as they pop up without compromising your data availability and business continuity. In other words, patches can be applied without downtime, making it easy to act and solve any weaknesses within your IT that could make your infrastucture vulnerable to hackers. Oracle MAA also gives your data a valuable extra level of protection against ransomware by improving your data recoverability, integrity, and security. For example, the following MAA technologies play a crucial role in protecting your application infrastructure and data:
-
ASM, Oracle Automatic Storage Management – First released by Oracle in version 10.1 (2003, 19 years ago). The original purpose was to simplify database datafile management so that Oracle DBAs (Database Administrators) could manage storage without requiring any storage administrator involvement; it also eliminated the need for LVM (Logical Volume Management) software and improved performance. ASM achieved the above tasks by storing data files on raw disks without a” cooked file system.” Ransomware technology corrupts file systems but currently is unable to corrupt raw disks like ASM. So, by using ASM, your data is protected against ransomware.
-
Data Guard/Active Data Guard – Contrary to storage replication and snapshot technologies that mirror every write to every file, including those that are corrupted or encrypted by ransomware, Data Guard and Active Data Guard do not replicate data at a physical level (storage) but does it at the memory level. This means that if your primary database is affected by ransomware, it is not replicated to your standby (Disaster and Recovery) environment. Additionally, as standby databases are ransomware free, a failover can be easily triggered without any data loss (depending on the level of protection in use).
-
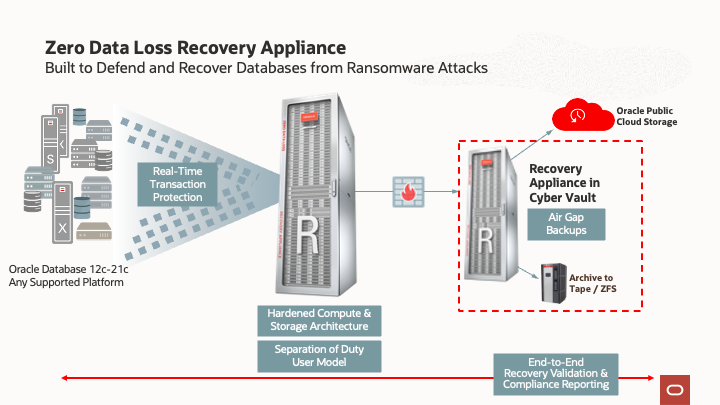
Zero Data Loss Recovery Appliance, Zero Compromises – Achieve a resilient Ransomware protection level with Zero Data Loss Recovery Appliance (ZDLRA). An engineered system designed to provide your data with real-time protection, recovery validation, and a cyber vault with an air gap that allows complete network isolation inside the data center itself. ZDLRA technology enables administrators to validate the integrity and recoverability of your data, empowering your organization to scale to protect thousands of databases incorporating backup protection across the entire lifecycle of security. This also includes disk backups, tape and cloud archiving, remote replication, and more.
As no single product or option can fully secure or protect your data, it takes a combination of many different technologies working together to allow you to access all configurations and detect any possible drifts (like missing security patches), minimize the attack surface (like removing excessive or unused privileges, and sensitive data from non-production environments), encrypt all data on rest and in transit (remembering to also protect your encryption keys from loss or theft), strengthen authentication to the maximum degree possible (like enabling multi-factor authentication for interactive accounts), control all access to your data (enforcing separation of duties) and finally monitor all activities for any possible anomalies.
All these areas previously mentioned provide the core foundation of Oracle Maximum Security Architecture (Oracle MSA). Some examples of products or options covered in Oracle MSA are (including some references towards PCI audits):
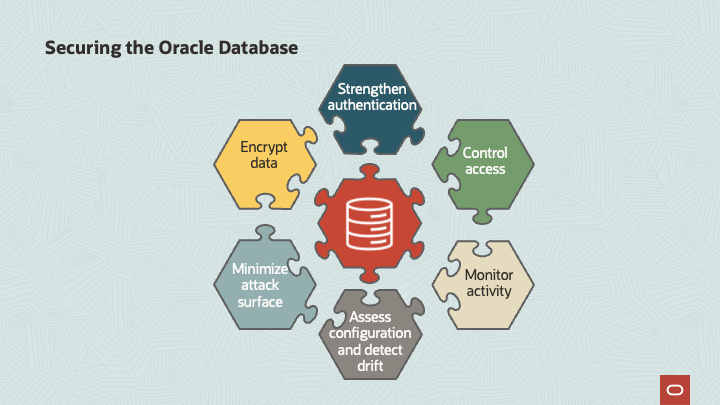
-
Oracle Database Security Assessment Tool (DBSAT) – DBSAT is a free command line tool that lets you quickly identify and assess your database configuration and identify deviations from best practices (Download from My Oracle Support Doc ID 2138254.1). It can differentiate between on-premises or cloud databases including Autonomous Databases (Shared or Dedicated). Depending on the type of database used as a target, it performs different checks and provides target-specific observations. For example, this tool can help you with a PCI audit, as it would identify the use of vendor-supplied passwords and other security parameters that are required on the “Requirement 2” of a PCI audit and become part of your ’organization’s regular security tests “(“Requirement 11”).
-
Oracle Data Safe – A unified cloud-based control center for Oracle Databases that helps your organization understand the sensitivity of your data (discovering the amount and location of all your sensitive data), evaluate risks, mask the sensitive data, monitor all security controls including user activity, ensure your databases are securely configured, and addresses many data security compliance requirements (including PCI).
-
Oracle Exadata Security Benefits – Oracle Exadata is an end-to-end security platform that is security-optimized, security-focused, and security hardened, following the Oracle MSA framework. This fantastic engineering system includes a small installation footprint that reduces the attack surface by only having software components that are specifically required to run an Oracle Database (e.g., minimum Linux distribution) and a secured optimized network access to storage (it includes a cellwall service that implements a firewall on each storage server that has no connectivity to a client network, plus SSH server that is configured to respond to connection requests only on the management network and the RDMA network fabric). Additionally, it implements the principle of least privilege by removing unnecessary and insecure services such as telnet and FTP that are disabled by default in the system. Per best practices, each process will run with the lowest possible privileges needed to perform a task; for example, Smart Scan and select ExaWatcher processes now run as non-privileged users. Note that the previously mentioned security features are only a fraction of this ’system’s security capabilities. It is also important to say that each Exadata release includes security and emergency fixes to address vulnerabilities discovered by our internal scanning tools.
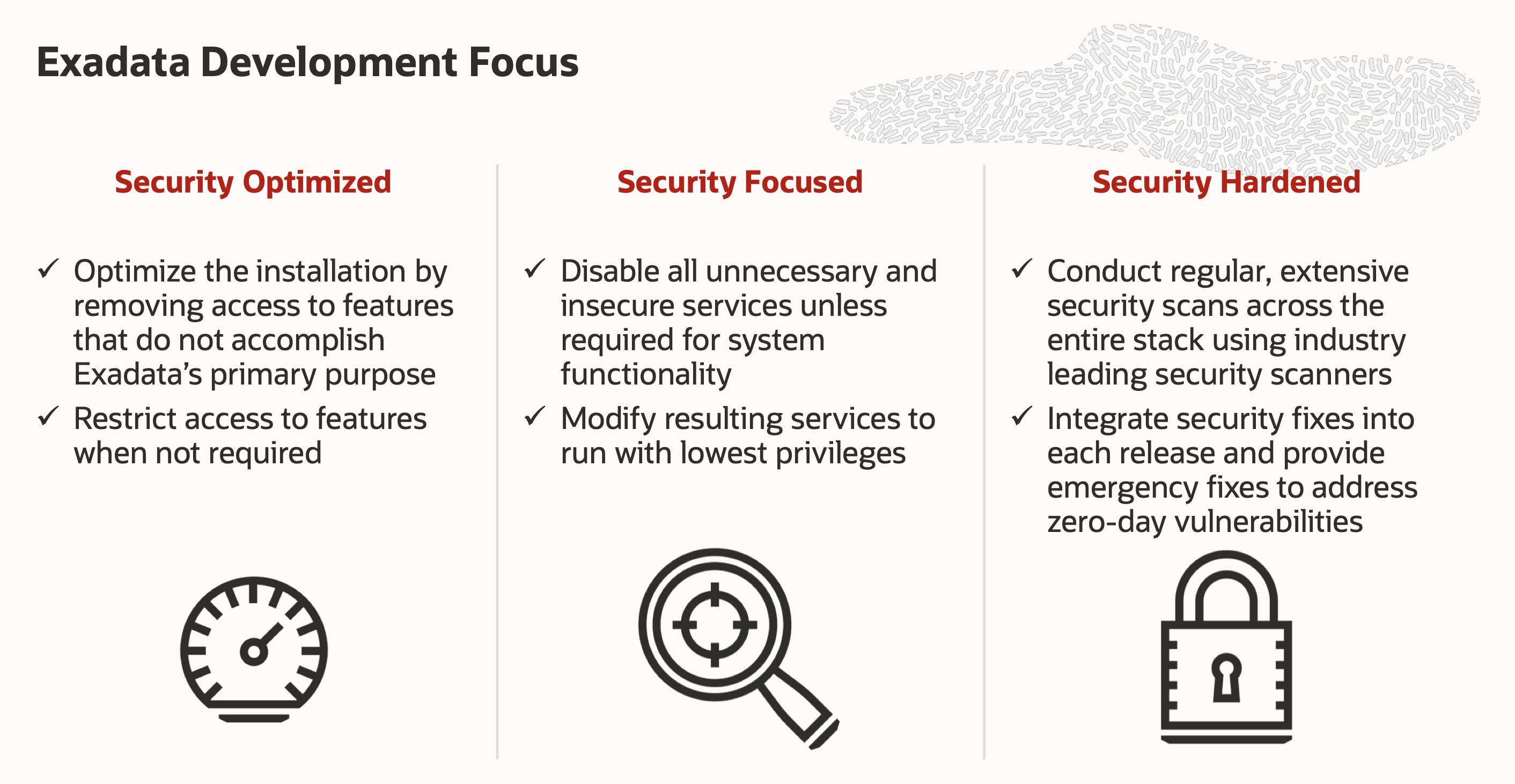
-
Transparent Data Encryption (TDE) – A database option unique to Oracle that encrypts data at rest within Oracle databases without generating any storage overhead. It can encrypt entire applications tablespaces or only specific sensitive columns (making it fully transparent to applications, so no changes at the application level is required at all) going even further by encrypting entire database backups using RMAN and Data Pump exports. TDE is part of the Oracle Advanced Security Options (ASO) available for Oracle Enterprise Edition databases. It also includes key management, strong protection for data in transit, strong authentication, and much more. This fantastic security package from Oracle can also immensely help your organization within a PCI audit. It would protect any existing cardholder data by encrypting all sensitive data at rest or in transit, implementing strong authentication, and much more.
Note: When using Data Guard with TDE at OCI and not using ASO (Advance Security Options) on-premises, note that the technology behaviour has now changed from 19.16 RU (Release Update). For more information on this topic, please refer to this announcement post here.
Conclusion
Cybercrime is growing every year and doesn’t show any signs of stopping anytime soon. Therefore, it’s so essential for organizations and companies from all industries, from healthcare to retail, to educate themselves on what to look at within their emails and online communications for signs of malware and phishing. In addition, organizations must invest in a cybersecurity architecture whose job is to monitor the safety of all data and servers. Your business can be secure if you take the time to consider your options and look for safe and effective solutions.
Security is a marathon, not a sprint! Let Oracle MAA and MSA be your strategy to win this race and maintain your data integrity, availability, recoverability, and security today! Make sure you are not tomorrow’s headline!
Want to learn more?
Check these amazing resources about Oracle MAA and MSA:
-
Oracle Maximum Availability Architecture (MAA) Main Page – https://bit.ly/3ysinDY
-
Database Security Main Page – https://bit.ly/3NSJWw3
-
Cyber Security Blog – https://bit.ly/3yPVZpG
-
Cyber Security Technical Paper – https://bit.ly/3akX1Ao
-
Securing the Oracle Database – a technical primer (free 4th edition) – https://bit.ly/3bUYQVa
-
Security Free Labs – https://bit.ly/3NLjCDW
-
Disaster and Recovery Free Labs – https://bit.ly/3yms6vK
-
Exadata Security Guide – https://bit.ly/3z84iMh
-
Exadata MSA presentation– https://bit.ly/3PD2ty9
