Oracle Cloud Infrastructure (OCI) Full Stack Disaster Recovery manages the transition of infrastructure, platforms, and applications between OCI regions from around the globe with a single click using OCI Console, CLI, and REST API.
Before you can start using Full Stack DR, you need to configure proper Identity and Access Management (IAM) permissions. We’ll walk through creating the specific IAM components needed—users, groups, dynamic groups, and policies—to securely operate Full Stack DR while maintaining control over your OCI resources. For more details refer to best practices of IAM in OCI.
In this blog post, we will go through the process of an OCI administrator creating various OCI IAM components like users, groups, dynamic groups, policies, etc., which are required to use Full Stack DR and other IAM policies to interact with OCI core services. Refer to OCI IAM documentation to understand more about various IAM components. Finally, we will verify accessing Full Stack DR by logging into the newly created OCI user.
Creating Your IAM Foundation
You may skip Steps 1 and 2 if a user already exists and the necessary groups are available
1. Create a user for managing Full Stack DR
a. Login to the OCI console with administrator credentials and select your home region.
b. From the menu, navigate to Identity & Security ->Domains-> Default Domain->Users->Create user. Provide First name, Last name, Email id, and click Create
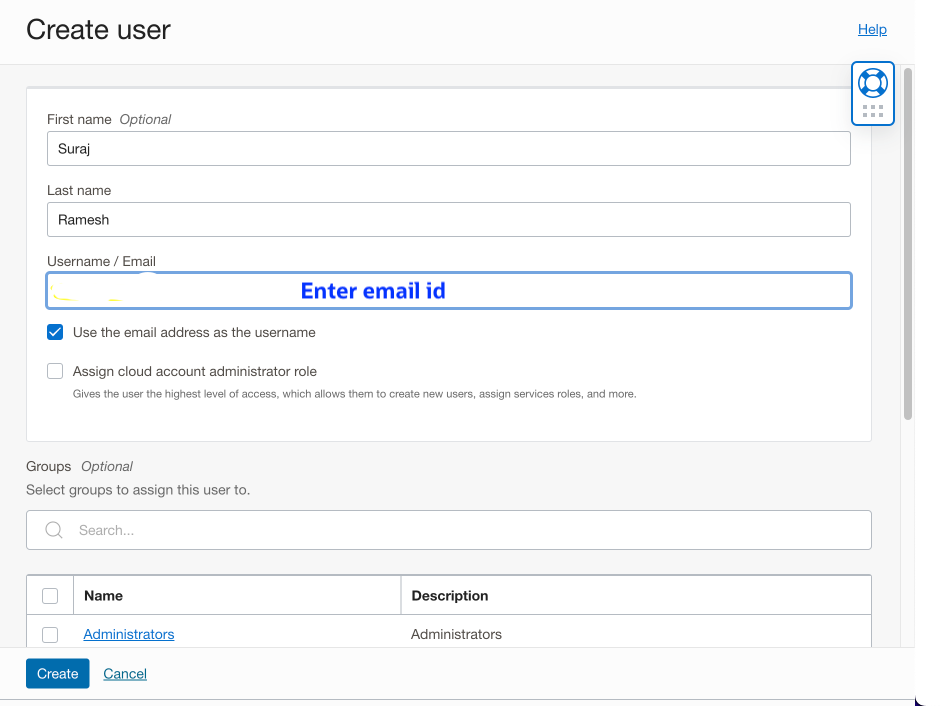
You will get an email (provided above) about activating the user account and must follow the instructions to activate the account.
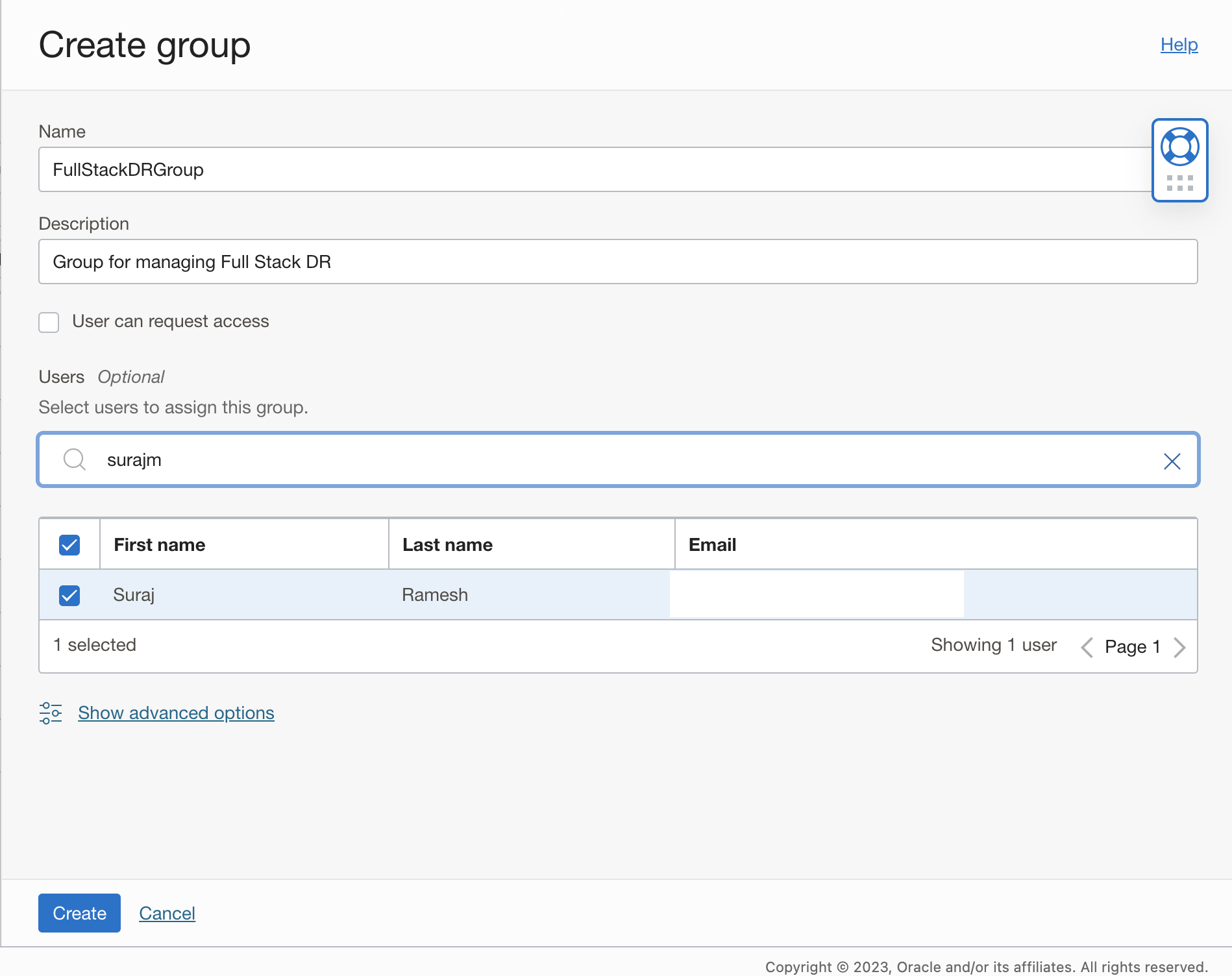
2. Create a group
a. Login to the OCI console with administrator credentials and select your home region.
b. From the menu, navigate to Identity & Security ->Domains-> Default Domain->Groups->Create group. Provide Name, Description, and select users to assign this group. You should select the user, which you created in Step 1 and click Create.
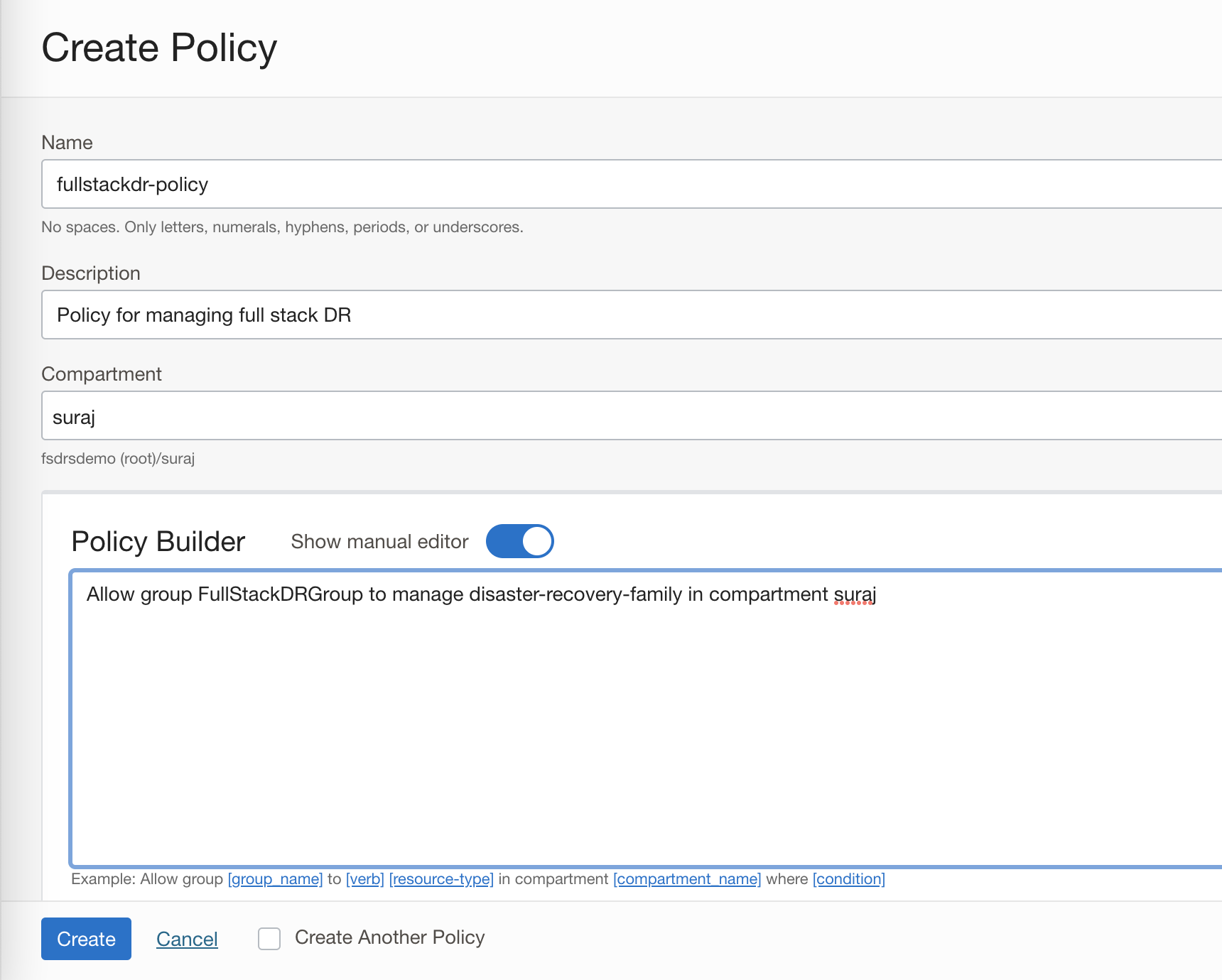
3. Create a policy and provide access to Full Stack DR
a. Login to the OCI console with administrator credentials and select your home region.
b. From the menu, navigate to Identity & Security -> Policies-> Create Policy. Provide Name, Description, Compartment, Policy Builder, enable Show manual editor and add the Policy below.
Select the appropriate compartment in which you will create the policy. In this example, the compartment “suraj” is chosen. This assumes that the “suraj” compartment exists directly under the root compartment and policy is created in root compartment. If you are working with nested sub-compartments, you must specify the full compartment hierarchy.
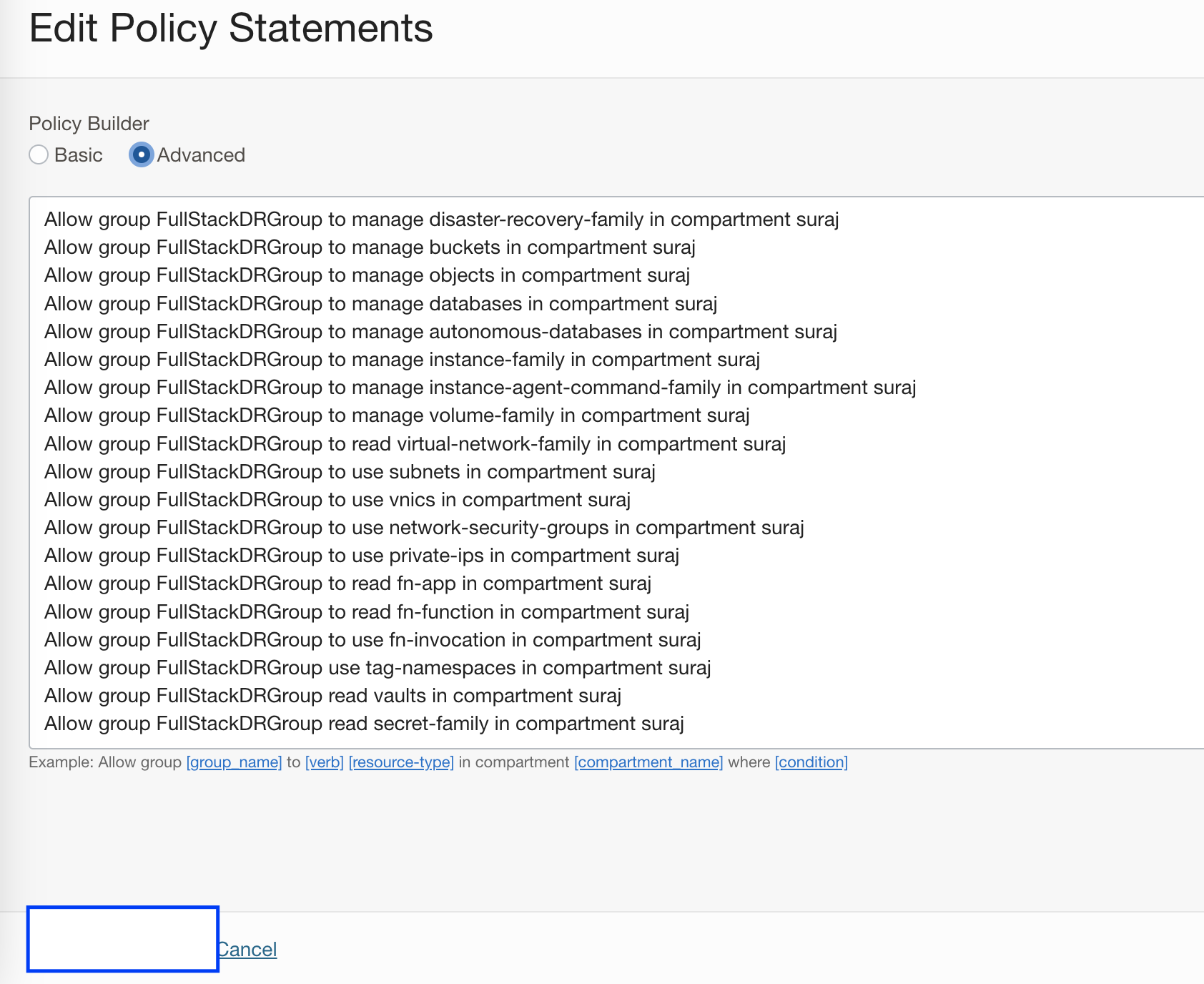
Allow group FullStackDRGroup to manage disaster-recovery-family in compartment surajYou should use the correct group name (created in step 2) and compartment name in the policy syntax.
In the policy syntax, I have provided “manage disaster-recovery-family” access for using Full Stack DR. If you need to have granular access to different Full Stack DR resource types, you have that option as well. Refer to Full Stack DR policies documentation for more details and modify the policies accordingly.
4. Add policies to access other OCI services
Full Stack DR doesn’t work in isolation—it orchestrates disaster recovery by interacting with various OCI services like Compute, Databases, Block Storage, Object Storage, Functions, Vaults, and Virtual Cloud Networks. You’ll need to add policies that allow Full Stack DR to manage these resources.
We will add these below policies to the policy “fullstackdr-policy” created in step 3. Policies can be modified depending on the resource types (members) which are used with Full Stack DR.
Allow group FullStackDRGroup to manage object-family in compartment suraj
Allow group FullStackDRGroup to manage database-family in compartment suraj
Allow group FullStackDRGroup to manage autonomous-database-family in compartment suraj
Allow group FullStackDRGroup to manage instance-family in compartment suraj
Allow group FullStackDRGroup to manage instance-agent-command-family in compartment suraj
Allow group FullStackDRGroup to manage volume-family in compartment suraj
Allow group FullStackDRGroup to manage object-family in compartment suraj
Allow group FullStackDRGroup to read virtual-network-family in compartment suraj
Allow group FullStackDRGroup to use subnets in compartment suraj
Allow group FullStackDRGroup to use vnics in compartment suraj
Allow group FullStackDRGroup to use network-security-groups in compartment suraj
Allow group FullStackDRGroup to use private-ips in compartment suraj
Allow group FullStackDRGroup to read fn-app in compartment suraj
Allow group FullStackDRGroup to read fn-function in compartment suraj
Allow group FullStackDRGroup to use fn-invocation in compartment suraj
Allow group FullStackDRGroup use tag-namespaces in compartment suraj
Allow group FullStackDRGroup read vaults in compartment suraj
Allow group FullStackDRGroup read secret-family in compartment suraj
Allow group FullStackDRGroup to manage load-balancers in compartment suraj
Allow group FullStackDRGroup to manage network-load-balancers in compartment suraj
Allow group FullStackDRGroup to manage file-family in compartment suraj
Allow group FullStackDRGroup to manage mysql-family in comparment suraj
Allow group FullStackDRGroup to manage cluster-family in comparment suraj
Allow any-user to manage objects in tenancy where all { request.principal.type = 'workload',request.principal.namespace = 'brie', request.principal.service_account =
'brie-reader',request.principal.cluster_id = 'OKE_CLUSTER_OCID'}
Allow any-user to manage objects in tenancy where all { request.principal.type = 'workload',request.principal.namespace = 'brie', request.principal.service_account =
'brie-creator',request.principal.cluster_id = 'OKE_CLUSTER_OCID'}
a. Login to the OCI console with administrator credentials and select your home region.
b. From the menu, navigate to Identity & Security -> Policies-> select the policy created in Step 3-> select Edit Policy Statements->Policy Builder->Advanced
Copy the list of policies as above and hit save changes. Verify whether all the added policies are reflected correctly.
You should use the correct group name (created in step 2) and compartment name in the policy syntax.
Refer to the complete set of services that current integrate with Full Stack DR. Based on the documentation, you can provide restrictive access to other OCI services accordingly.
5. Create a Dynamic Group and modify the Policy
Oracle recommends using resource principal authentication for Full Stack DR, which allows the service to access OCI resources without embedding credentials. This is particularly important for advanced features like user-defined plan groups, which let you add custom scripts that run on compute instances during DR operations.
To enable this, create a dynamic group that treats your OCI resources as principals (similar to how user groups work for people). Navigate to Identity & Security → Domains → Default Domain → Dynamic Groups and create a new group with these matching rules:
a. Login to the OCI console with administrator credentials and select your home region.
b. From the menu, navigate to Identity & Security ->Domains-> Default Domain->Dynamic Groups->Create Dynamic Group. Provide Name, Description, Matching rules-> Match any rules defined below -> In Rule 1, provide the below details. Make sure you modify your compartment OCID -> click Create . You can narrow it down to specific instances, if so use instance.id.
c. We recommend to create the dynamic group at the specific compartment level and add these matching rules. First rule is running commands using OCI compute, second rule is for launching container instance required for OKE and MySQL members and last one is for Full Stack DR.
ALL {instance.compartment.id = 'compartment_ocid'}
ALL {resource.type='computecontainerinstance', resource.compartment.id = 'compartment_ocid'}
ALL {resource.type='drprotectiongroup', resource.compartment.id= 'compartment_ocid'}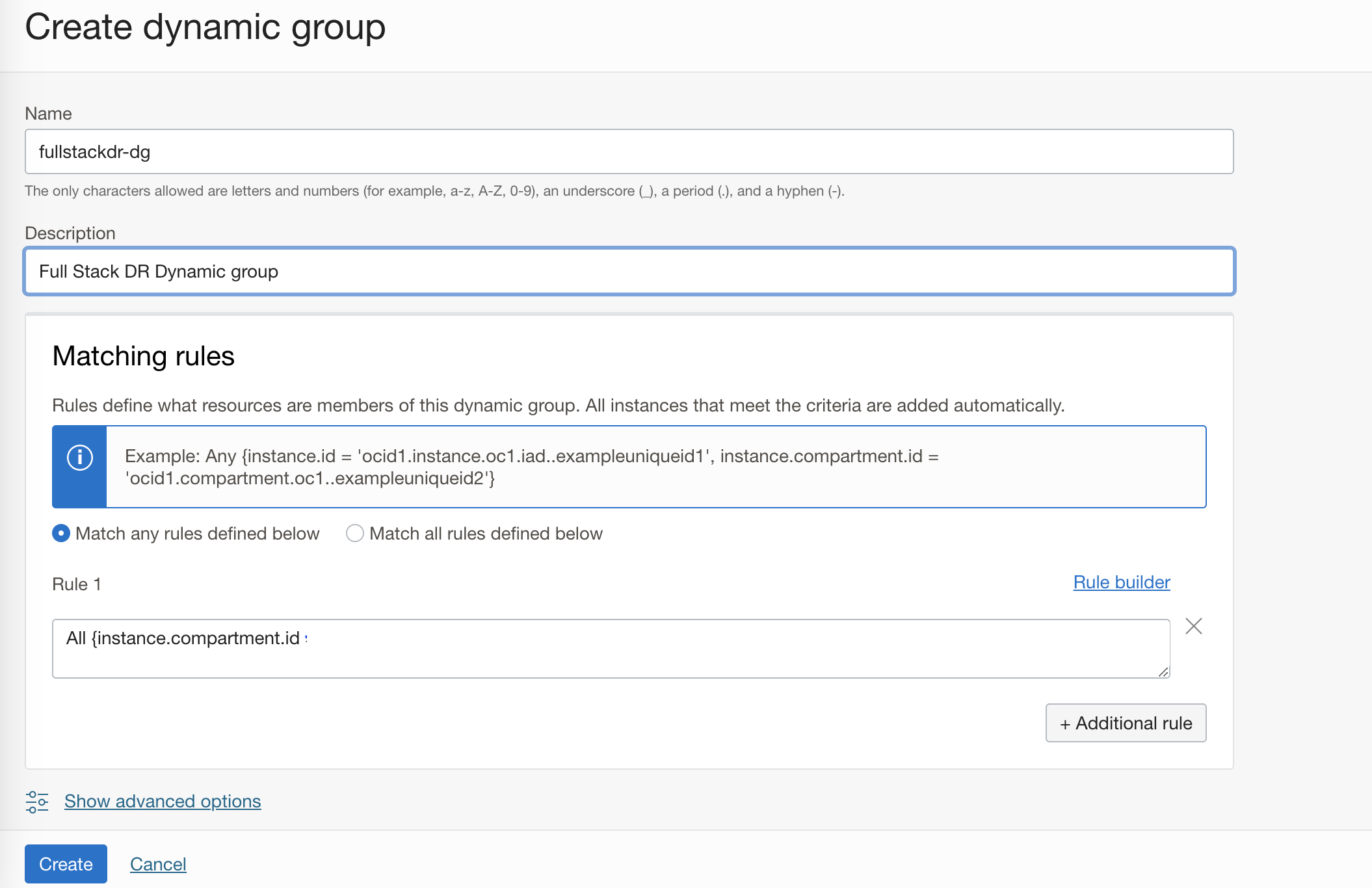
d. Update the “fullstackdr-policy” policy with dynamic group allow commands. This is assumed the dynamic group “fullstackdr-dg” in the default domain. If you use different domain, you must add the domainname/dynamicgroup.
Allow dynamic-group fullstackdr-dg to manage disaster-recovery-family in compartment suraj
Allow dynamic-group fullstackdr-dg to use tag-namespaces in compartment suraj
Allow dynamic-group fullstackdr-dg to read all-resources in compartment suraj
Allow dynamic-group fullstackdr-dg to manage instance-family in compartment suraj
Allow dynamic-group fullstackdr-dg to manage instance-agent-command-family in compartment suraj
Allow dynamic-group fullstackdr-dg to manage instance-agent-command-execution-family in compartment suraj
Allow dynamic-group fullstackdr-dg to manage instance-agent-plugins in compartment suraj
Allow dynamic-group fullstackdr-dg to manage cluster-family in compartment suraj
Allow dynamic-group fullstackdr-dg to manage cluster-virtualnode-pools in compartment suraj
Allow dynamic-group fullstackdr-dg to manage compute-container-family in compartment suraj
Allow dynamic-group fullstackdr-dg to manage load-balancers in compartment suraj
Allow dynamic-group fullstackdr-dg to manage network-load-balancers in compartment suraj
Allow dynamic-group fullstackdr-dg to manage volume-family in compartment suraj
Allow dynamic-group fullstackdr-dg to manage file-family in compartment suraj
Allow dynamic-group fullstackdr-dg to manage object-family in compartment suraj
Allow dynamic-group fullstackdr-dg to manage objects in compartment suraj
Allow dynamic-group fullstackdr-dg to manage buckets in compartment suraj
Allow dynamic-group fullstackdr-dg to manage databases in compartment suraj
Allow dynamic-group fullstackdr-dg to manage autonomous-database-family in compartment suraj
Allow dynamic-group fullstackdr-dg to manage mysql-family in compartment suraj
Allow dynamic-group fullstackdr-dg to read virtual-network-family in compartment suraj
Allow dynamic-group fullstackdr-dg to use subnets in compartment suraj
Allow dynamic-group fullstackdr-dg to use vnics in compartment suraj
Allow dynamic-group fullstackdr-dg to use private-ips in compartment suraj
Allow dynamic-group fullstackdr-dg to use network-security-groups in compartment suraj
Allow dynamic-group fullstackdr-dg to read secret-family in compartment suraj
Allow dynamic-group fullstackdr-dg to read vaults in compartment suraj
Allow dynamic-group fullstackdr-dg to read fn-app in compartment suraj
Allow dynamic-group fullstackdr-dg to read fn-function in compartment suraj
Allow dynamic-group fullstackdr-dg to use fn-invocation in compartment surajFor additional information about policies and dynamic groups, please refer the OCI Full Stack DR policies documentation,
6. Running Commands on an Instance
Full Stack DR uses OCI run command feature to perform tasks like to run iSCSI commands, user-defined scripts ( user-defined plan groups), mounting file system etc. It is essential to prepare the compute instance which is part of the DR protection group with the necessary pre-requisites.
On the compute instance – connect and execute the below commands to provide the ocarun user with admin access.
For Linux, perform the below tasks.
echo “ocarun ALL=(ALL) NOPASSWD:ALL” > /etc/sudoers.d/101-oracle-cloud-agent-run-command
systemctl restart oracle-cloud-agentIf Windows,perform the below tasks.
Powershell version >=5.1
Add-LocalGroupMember -Group “Administrators” -Member “NT SERVICE\OCARUN”
Restart-Service -Name OCARUN -Force Power shell version < 5.1
net localgroup Administrators /add “NT SERVICE\OCARUN”
Restart-Service -Name OCARUN -Force 7. Verify Full Stack DR access
You have now set up all of the necessary prerequisites. You should now login into the OCI console as the user (created in step 1) and verify the Full Stack DR functionality. Please make sure you have the necessary user credentials before proceeding further.
a. Login to the OCI console with user credentials and select your home region.
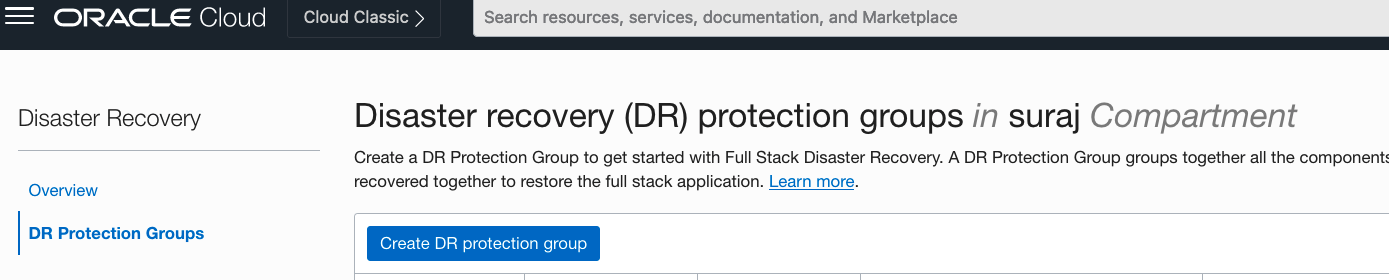
b. From the menu, navigate to Migration and Disaster Recovery->Disaster Recovery->DR Protection Groups
Now you should be able to Create a DR protection group and start working with Full Stack DR.
As part of this blog series, we will discuss various components in OCI Full Stack DR and multiple use cases as well as tips and tricks to take full advantage of Full Stack DR in subsequent blogs. Please stay tuned for the next blog post in the series!!
Additonal Information
Full Stack Disaster Recovery OCI Full Stack Disaster Recovery
Full Stack Disaster Recovery Documentation