Enhancing Cloud Cyber Security with Immutable Oracle Zero Data Loss Autonomous Recovery Service
This blog discusses technology choices to address the recently adopted USA Securities and Exchange Commission (SEC) rule on Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure and the EU Digital Operational Resilience Act (DORA). While the nature of the blog is technical, it does not require deep subject matter expertise and should help your conversations with the Chief Information Security Officer (CISO).
As we previously discussed in the Strengthen Oracle Database Cyber Defense and Recovery with Zero Data Loss Air-Gapped Backups, there are two distinct approaches to providing Air-Gap capabilities for enhanced Cyber Security and Ransomware protection:
- Logical Air Gap – Backups are received by the appliance in real-time and time-locked for immutability, isolating them from any user modifications and deletions. The administration of backups is separated from database administrators, and backups are continuously validated to ensure they have not been tampered with. This provides a very high level of protection while backups are immediately accessible to production database hosts to meet low RPO and RTO requirements.
- Physical Air Gap – The same data protection capabilities exist in a physically Air-Gapped environment as in a logical Air Gap. In addition to those capabilities, the Air-Gapped appliance receives backup copies sent by the production appliance through a physically isolated, non-routable replication network that is only open for replication traffic during limited, randomized time periods to synchronize with the latest backups. It provides an additional layer of defense against lateral attacks that move across the network to backup infrastructure and storage. A physically air-gapped secondary appliance does not support the same RTOs and RPO as it is generally inaccessible by production systems and does not continuously receive the most current production backups.
On-premises Oracle Zero Data Loss Recovery Appliance (ZDLRA) supports both approaches: the Logical Air Gap through built-in access controls, immutability, and backup validation, as well as physical network isolation with two appliances in Cyber Vault configuration.
While Oracle Zero Data Loss Autonomous Recovery Service (ZRCV) is based on the same ZDLRA infrastructure and capabilities deployed in Oracle Cloud Infrastructure (OCI), physical Air Gap is not a practical approach in a cloud environment for a number of reasons, starting with the backend network isolation. To better meet customer Cyber Resiliency requirements for cloud databases, ZRCV adopted a new approach beyond existing ZDLRA capabilities to become an Immutable Cloud Service. Let’s define what we mean by the Immutable Cloud Service and review its fundamentals and capabilities.
ZRCV as an Immutable Cloud Service is an isolated Oracle-managed solution that provides automated lifecycle management with strict policy-based retention management which prevents deletion or alteration of backup data.
This is a drastic departure from the traditional definition of “immutability,” which primarily focuses on the storage layer, i.e. a type of data storage where once data is written, it cannot be modified or deleted. While this definition and approach are valid for on-premises storage array use cases, they are less relevant for cloud environments, which provide a much higher level of security and access control around the underlying infrastructure.
Let’s review the fundamental capabilities of what makes ZRCV an Immutable Cloud Service for Oracle database protection in OCI:
- OCI security and Oracle Maximum Availability Architecture (MAA) best practices are always used with ZRCV. While available, these practices may not be consistently enforced or implemented for on-premises environments.
- Transparent Data Encryption (TDE) is mandatory and enforced for all backups of Oracle-managed database services
- ZRCV will reject non-encrypted backup data
- Encryption is maintained throughout the backup and long-term retention lifecycle
- TDE Key management is maintained outside of ZRCV and stays with the database. Backups and encryption keys are never stored together, and ZRCV has no access to them.
- ZRCV is located in an Oracle-managed tenancy, fully isolated from customer access tenancy. Customers are only allowed to use RMAN to send backups and request restores via a Private Endpoint. In addition to it:
- RMAN DELETE workflows are blocked
- Backup deletion is controlled solely by the ZRCV Protection Policy, which enforces retention management.
- Backups cannot be immediately deleted even when a primary database is deleted. This is done for prevention from malicious activity: even if the policy-based lifecycle is not enforced, ZRCV will preserve all backups for a minimum of 72 hours.
- ZRCV Protection Policies have a Retention Lock option, which prevents the backup retention time from being reduced, providing an extra level of backup immutability.
- ZRCV infrastructure deployment leverages two physical ZDLRA systems for a highly-available configuration.
- The two physical systems are deployed across two datacenters (Availability Domains or Zones) or different Fault Domains in a single Availability Domain/Zone region.
- OCI Identity and Access Management is integrated with ZRCV for granular Role-Based Access Control (RBAC)
- Mandatory OCI Government Regulations and Regulatory Compliance for any deployed Service, including ZRCV
The following diagram presents ZRCV operational deployment, connectivity, and DR topology support in OCI and multi-cloud (Azure, GCP, AWS) in Oracle-managed tenancy, which is isolated from customer tenancy access controls.
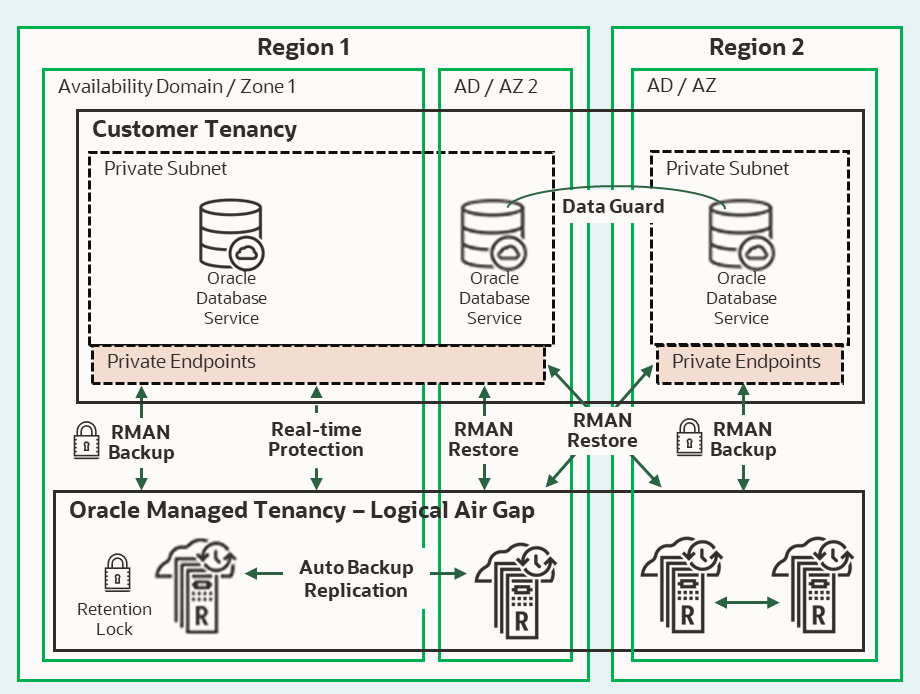
Let’s now review what ZRCV, as the Immutable Service, delivers with the logical Air Gap capabilities. It is based on the ZDLRA platform implementation, as it was outlined in the “Strengthen Oracle Database Cyber Defense and Recovery with Zero Data Loss Air-Gapped Backups” blog:
- Built on the industry-proven Exadata platform, ZDLRA is fully fault-tolerant, offers extremely high performance, and scales easily. The platform is security-hardened and includes security and emergency fixes to address vulnerabilities.
- The unique architecture of the ZDLRA protects the backup data on internal storage, even if the compute nodes are compromised.
- All system access and changes are audited and can be sent to a central audit log aggregator to detect any discrepancies. In OCI, ZRCV sends all the critical data to the Metrics Explorer and OCI alerts while user access to the infrastructure is disabled.
- Continuous data anomaly detection of all backups identifies any issue that can compromise recovery due to cyber or ransomware attacks. With ZRCV, any such incident is immediately reported to the customer cloud operations for analysis and remediation using health status reporting tools.
- Anomaly detection is performed throughout the data protection lifecycle: at the source database before backups are sent to ZRCV, while backups reside on ZRCV backend storage before they are replicated cross-AD for HA purposes, and as replicated backups are received by and stored on the secondary appliance in the HA pair.
- Changes to the protected databases are sent in real-time to ZRCV, supporting zero to sub-second RPO with the Zero Data Loss option.
Conclusion:
To wrap up this discussion on ZRCV as an Immutable Cloud Service, let’s summarize by outlining the major differences of this service compared to on-premises solutions and, by extension, when compared with the same solutions being delivered in public clouds in Software-as-a-Service (SaaS) offerings.
- Air-gap technology approaches and implementations greatly differ across these offerings:
- On-premises is controlled by a customer alone, and hardware is physically accessible, as well as public network accessibility.
- Third-party Backup Software solutions delivered as SaaS can leverage public cloud infrastructure but lack the tight integration of security controls with the underlying platform. That leads to increased exposure to vulnerabilities due to customer-managed installation and configuration.
- For Oracle databases in OCI and Multi-Cloud (Azure, Google Cloud (GCP), AWS), ZRCV as an Immutable Cloud Service is designed to provide enhanced Cyber Resiliency capabilities, including:
-
- Separate Oracle-managed service tenancy, isolated from customer access
- Private endpoint networks for all customer tenancy interactions with ZRCV
- Mandatory end-to-end encryption of production data to backups and Long-term Retention
- Security-hardened Exadata platform hardware and OS
- Oracle MAA best practices for database security and high availability
- Enforced access controls to meet service immutability, not just storage-level alone or its SaaS implementation
- End-to-end encryption throughout backup and long-term retention lifecycle
- ZRCV provides end-to-end complete backup and recovery lifecycle management
- with database-aware protection health monitoring and reporting
-
While all solutions we discussed above use similar terminology and can be leveraged to help address compliance with the new government regulations, in reality, they are not equal. Choices that are available for on-premises are not comparable to options available in the cloud, and SaaS backup solutions are inferior to native cloud services Cyber Security. New Cyber Resiliency requirements significantly accelerated cloud migration as the best and the most efficient way not just for the implementation of advanced security technologies but also as a way to ensure corporate compliance.
