The Zero Data Loss Recovery Appliance (ZDLRA) provides both a logical air-gap and a physical air-gap to protect Oracle Database backups. Other blog posts have talked about how to leverage the capabilities of the ZDLRA in a physical air-gap architecture, but in this post I am going to talk about how the ZDLRA provides superior logical air-gap protection.
To learn more about the ransonmware protection that the ZDLRA provides, you can read Marco Calmasini’s blog on this topic and you can read this recently release tech brief.
What is an air-gap ?
First, l’m going to start with the Wikipedia definition of an air-gap, “an air gap, air wall, air gapping or disconnected network is a network security measure employed on one or more computers to ensure that a secure computer network is physically isolated from unsecured networks, such as the public internet or an unsecured local area network”.
As you can see, in a traditional air-gap the backups are stored in a network segment that is permanently, physical isolated from the rest of the network. For backups this was often implemented utilizing tapes, and ensuring that the tape was removed from the tape array, and could not be overwritten.
Most IT departments have moved away from creating physical tapes, but with the rise of cyber attacks, they still need the same level of protection that tapes provided.
This protection is implemented through a logical air-gap, and if a higher level of protection is also needed, IT departments often utilize a physical air-gap and replicate backups to a network isolated cyber vault.
First let’s start with defining a physical air-gap, and a logical air-gap.
In researching this topic, I could not find any real consistency on the definition of a physical air-gap, and a logical air-gap.
Because of this inconsistency, I turned to NIST (National Institute of Standards and Technology) to find a definition to start with.
In special publication NIST_SP.800-209 NIST mentions two types of air-gaps. NIST defines both a strict implementation of air-gapping, involving full, permanent network isolation, and a less strict implementation that involves enabling shutting down data ports and opening them during a limited time for the periodic sync with a production system. NIST recommends using immutable storage (e.g., retention locking, immutable policies) to further isolate and protect recovery data.
Physical air-gap : Because complete, permanent network isolation is not possible in most cases, a physical air-gap architecture follows NIST’s definition of a less strict air-gap implemention. A physical air-gap is implemented by having an isolated network between the primary data center, and a cyber vault. That network connection is severed utilizing various methods, and for the majority of the time provides no direct connection between the primary datacenter and the vault. The image below shows what a typical cyber vault architecture looks like with a clean room for restoring from backups in isolation.
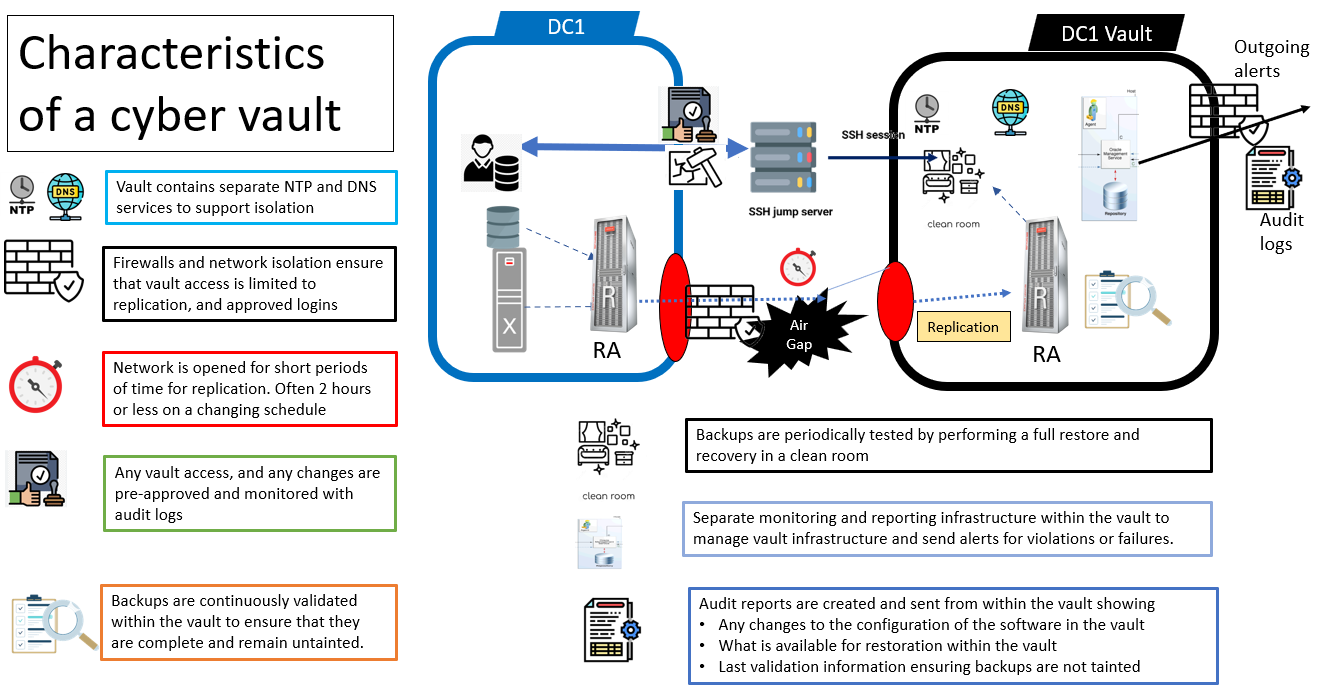
Logical air-gap : A physical air-gap provides superior protection of backups through isolation, but by severing the direct connection, backups protected by the physical air-gap are often hours if not days old. These backups don’t provide an easily accessible, up-to-date backup for normal recovery scenarios. A logical air-gap provides protection by means of logical processes following NIST’s practices defined in a Zero Trust Architecture (ZTA) to protect the backups.
These practices include :
- All communication is secured regardless of network location.
- Access to individual enterprise resources is granted on a per-session basis. Trust is evalutated before the access is granted.
- Access to resources is determined by role based dynamic policy
- Micro-segmentation of both networks and accounts
- The enterprise monitors and measures the integrity and security posture of all owned and associated assets.
- Identifying users with special privileges, limitting their privileges to those necessary to perform the mission, but also ensure there is auditing and logging of all actions
Summary : A logical air-gap can protect your backups while ensuring you meet your RTO and RPO. A physical air-gap is used as a seconday backup in the event of a breach of the primary backup.
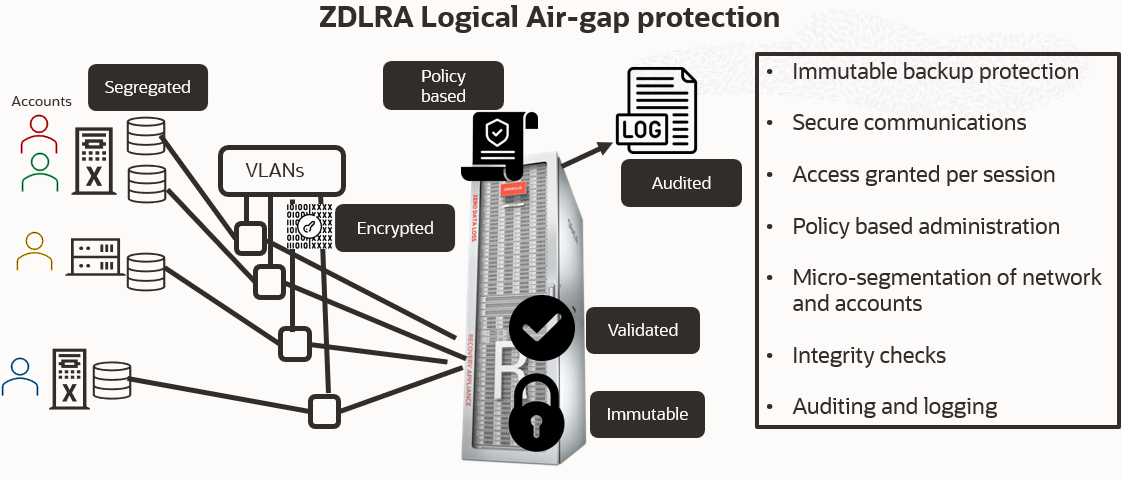
Logical air-gap features of the ZDLRA
The ZDLRA follows all of NIST’s best practices for a Zero Trust Architecture (ZTA).
ZDLRA provides immutable backups to protect database backups
Backups sent to the ZDLRA can be protected with a locked retention window. This protects database backups from any changes or deletions and ensures that they are immutable. When archival backups are created by the ZDLRA and combined with an external immutability strategy, both the metadata, and the backup data is also protected from any changes or deletions.
All communication is secured regardless of network location.
Communication with the ZDLRA is secured in a number of ways
- By utilizing the Space-Efficient Encrypted backup feature, backups are fully encrypted by the database client. The encryption keys are controlled by the client, and the backup remains encrypted. This protects the data from exfiltration.
- Network connections from the protected database to the ZDLRA can be encrypted to ensure that the communication itself is protected.
- Firewalls can be configured to only allow the limited traffic necessary over specific ports used by the protected database to communicate with the ZDLRA.
- Traffic between the protected database and the ZDLRA uses a proprietary API further protecting the backup information
Access to the ZDLRA is granted on a per-session basis.
Each backup session establishes a new connection, and at that time, privileges are validated and granted. Any removal of privileges takes effect immediately. In the event of a cyber attack, privileges can be quickly revoked, immediately stopping the spread of an attack.
Access to Database backups is determined by role based dynamic policy
Access to Databases backups is granted by user to protected databases, and retention settings for databases are controlled through dynamic policies. Changes to policies immediately affect backups that are protected by that policy. This provides a flexible, central way to view and manage protection policies.
Micro-segmentation of both networks and accounts
The ZDLRA excels in the area of micro-segmentation of networks and accounts external to the ZDLRA and provides internal micro-segmentation within the components of the ZDLRA.
External segmentation
Network segmentation: The ZDLRA supports network segmentation by allowing a virtually unlimited number of VLANs network connections. Protected database backup traffic can be isolated to a separate backup network VLAN limitting the exposure to a single database.
Account segmentation: The ZDLRA supports account segmentation by allowing a virtually unlimited number of individual backup acounts which are granted access to a subset of protected databases. It is possible to grant access in a one-to-one strategy of having an individual account for each protected databases backups.
A fully secure environment can segment backups to both separate accounts and separate network segments giving full isolation to backup traffic and authorization.
Internal segmentation
The unique archecture of the ZDLRA protects the backup data stored on internal storage cells, even if the compute nodes are compromised. An internal firewall system obfuscates the backup volumes giving them a higher level of protection from attack
The enterprise monitors and measures the integrity and security posture of all owned and associated assets.
Monitoring and measuring the integrity of Oracle Database backups is a unique challenge. This is because Database backups are different from OS backups of applicaiton data. Oracle Database backups are performed by Oracle’s Recovery Manager utility (RMAN) and contain ONLY DB blocks stored in an optimized proprietary format. Because they are blocks of data, rather than libraries or executables, scans for ransomware signatures, dormant viruses, etc. do not apply to Oracle Database backups.
Best practice for determining the integrity of Oracle Database backups is to perform regular “restore validate” tests , and “restore preview” through the RMAN utility which validate both the integrity of the backups, and the contents to ensure recoverability.
The ZDLRA uniquely leverages Oracle’s proprietary knowledge of a backup’s structure and contents to internally execute these periodic integrity checks of all backups stored within the appliance, and along all points of data movement. Any integrity failures are immediately reported and can be quickly addressed before a cyber attack can spread.
Because the ZDLRA does this internally, it is able to provide far superior periodic integrity checks both within the primary backup copy, and within all replicated copies, even when replicated to an isolated physical air-gapped ZDLRA.
Identifying users with special privileges, limitting their privileges to those necessarily to perform the mission, but also ensure there is auditing and logging of all actions
The ZDLRA allows the creation of individual accounts, and can be connected to a central identity management system. Changes that could compromise the backups on the ZDLRA have to be approved by multiple individual administrators through a quorum approval process protecting against an attack from a single compromised set of credentials. All changes on the ZDLRA are logged and can be audited to quickly detect any security breaches.
Summary : Logical air-gap features of the ZDLRA
Through it’s numerous security features, the ZDLRA provides a logical air-gap to ensure backup protection. This protection goes beyond what other vendors can provide by performing constant integrity checks to ensure that the backups remain untouched.