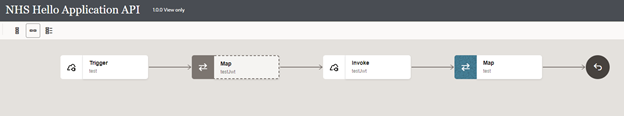
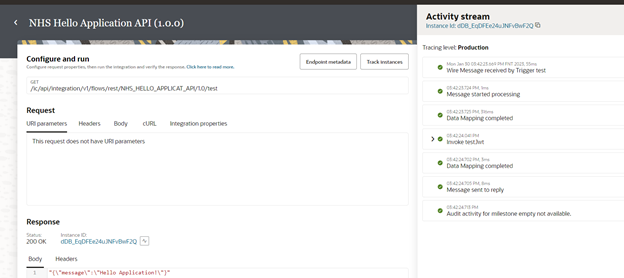
This blog is to outline the process of invoking a service using JWT Assertion Security policy in REST adapter of OIC.
So, let’s take a service which secures their APIs using JWT Assertion. I could find NHS is a perfect choice to showcase this use case. NHS has detailed information of consuming their APIs using JWT here. Let’s take this as reference and perform the connectivity from OIC to NHS using REST adapter
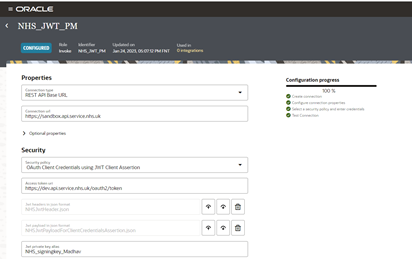
Connection page requires below details to establish the connection.
- Connection URL – can be pulled from NHS documentation
- Access Token URL – can be pulled from NHS documentation
- JWT Private key alias
- JWT Payload
- JWT headers
JWT Private Key alias: I have taken help of https://mkjwk.org/ to generate the keys. For production cases, please follow the prescribed mechanism of your organization.

Copy the private key in pem format, and this needs to be uploaded into the OIC certificates section as a signing key.
Note: Please mention the Key ID while generating the keys as above, as the same key is required at multiple places.
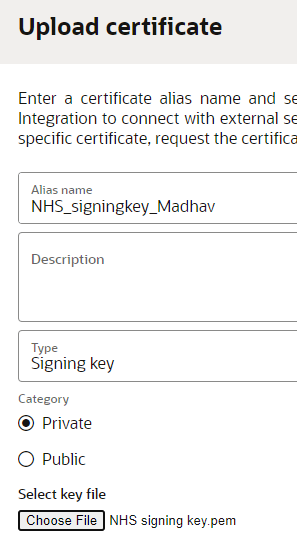
Take the alias and maintain the same in connection page.
Along with it, register the public key in NHS app, details explained here to create the app NHS. Copy the public and private key set generated in the previous step and upload in the NHS app created.
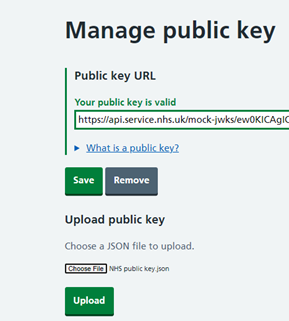
Once public key is uploaded, collect the API Keys from the App, and these should be maintained in the JWT payload.

Provide approvals for APIs required to execute with these keys. (all APIs belongs to sandbox and NHS App (External Development))
JWT Payload: Prepare the JWT payload as per the structure mentioned in NHS documentation and upload this file in the connection page.
{
“iss”: “5a66yrNsbzu9WxxxxxxxxxxxMWvDf7AfEY”,
“sub”: “5a66yrNsbzu9WxxxxxxxxxxxMWvDf7AfEY “,
“aud”: “https://dev.api.service.nhs.uk/oauth2/token”,
“exp”: 1669859997,
“jti”: “2c59e3b4-982a-44ea-94a2-3785e926df01”
}
Please note, iss and sub will be same for the “OAUTH Client Credentials using JWT Client Assertion”, which is the API key generated in the above app created in the NHS.
Incase, if you are using the security policy as “OAuth using JWT User Assertion”, then Sub should be mentioned with the username used in the app creation.
Hence your JWT payload looks as below.
{
“iss”: “5a66yrNsbzu9WoRaWMjfkEMWvDf7AfEY”,
“sub”: “madhav.poosarla@oracle.com”,
“aud”: “https://dev.api.service.nhs.uk/oauth2/token”,
“exp”: 1669859997,
“jti”: “2c59e3b4-982a-44ea-94a2-3785e926df01”
}
Please Note: NHS application does not support “OAuth using JWT User Assertion”.
JWT headers: it does have 2 params as below.
Both the params must be updated as per the details provided while creating the keys.
{
“alg” : “RS512”,
“kid”: “NHS_Demo_PM”
}
Upload both JWT headers and JWT payload in the connection page and test it.
Lets now test the integration with a hello world API available in NHS service.
This integration just executes the hello world API and sends a standard response, this is to check whether the connection is working as expected or not.