As organizations increasingly adopt multi-cloud and hybrid cloud infrastructures, managing identity and access across multiple environments can become a complex and challenging task. Traditional Identity and Access Management (IAM) solutions often struggle to keep up with the evolving cloud landscape, leaving organizations vulnerable to security breaches and compliance issues.
To address these challenges, a multi-cloud/hybrid cloud IAM solution offers a comprehensive approach to manage identities, access, and security across multiple environments. By providing a centralized platform that can manage access to multiple cloud services and applications, a multi-cloud/hybrid cloud IAM solution simplifies IAM administration and strengthens security. Oracle Cloud Lift Services has implemented solutions that address these challenges.
OCI IAM
Along with various IaaS, PaaS, and SaaS services, Oracle cloud Infrastructure (OCI) offers Identity as a Service (IDaaS), which provides Identity Governance (Joiner-leaver-Mover) and sign-on (authentication-authorization) capabilities to customers (Service name is OCI-Identity-Domain/IDCS).
OCI-Identity-Domain supports various standards (SAML, OAuth, OIDC, WS-Fed etc.) to integrate with the majority of industry’s known IAM platforms (i.e., Okta, Sailpoint, Savyint, Forgerock, IBM, Microsoft, Azure, ADFS, SiteMinder, ForgeRock, OIM, OAM, PingFederation. etc) and target applications. Such integrations are already designed and implemented for various enterprise customers by Oracle Cloud Lift Services.
In this article, we are covering a hybrid cloud architecture scenario in which Okta is playing the role of centralized Identity Provider (IdP) and OCI-Identity-Domain serves as the Service Provider (SP). The trust setup between Okta and OCI-Identity-Domain not only provides a way to manage identities in OCI-Identity-Domain using Okta, but also a way to access Oracle SaaS and PaaS applications and resources through Okta credentials.
This way users and applications can be authenticated, authorized, and granted access to resources based on their roles and permissions, regardless of the environment they are using. This helps organizations ensure consistent security policies and access controls across their entire cloud infrastructure, reducing the risk of unauthorized access and data breaches.
Architecture
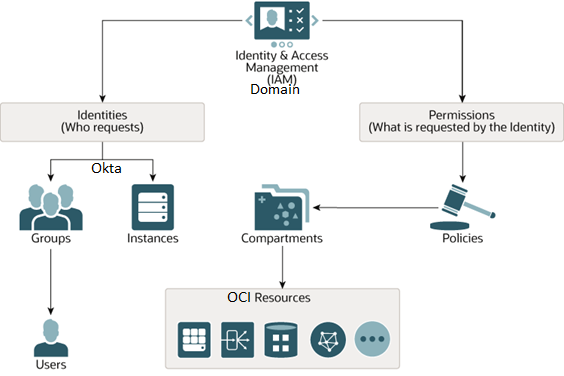
In this architecture, Okta serves as the authoritative source, so once authentication is completed at Okta level, authorization is handled by the OCI-Identity-Domain via written policies/permissions. The customer can access OCI resources using Okta credentials. The customer’s user identity management will happen via Okta, with the changes being pushed in OCI-Identity-Domain via System for Cross-domain Identity Management (SCIM) mechanism.
This architecture supports the following components:
- Single Sign On (SSO): Single sign-on is an authentication scheme that allows a user to log in with a single ID to any of several related, yet independent, systems
- Federation: Enables users who have a Cloud Identity Service account to seamlessly access services that are provided by one or more partner organizations, without a separate login at the partner site
- Security Assertion Markup Language (SAML): Is XML-based open-standard to setup federation trust between IdP(Okta) and SP(OCI-Identity-Domain)
- System for Cross-domain Identity Management (SCIM): SCIM protocol is used for Identity Federation
- Identity Federation: Is the management of identities in federation trust setup between IdP (Okta) and SP (OCI-Identity-Domain)
Before You Begin
Before you set up federation trust between Okta and OCI-Identity-Domain, please ensure the following:
- You have access to OCI-Identity-Domain with authorization to manage IdPs (Identity Domain Administrator or Security Administrator role).
- You have an Okta subscription and an admin/developer account, as well as having hands-on experience working with the Okta platform.
- You know how to create a security group in Okta and also add users to it.
- You have a Unique identifier (UserName/Email/UPN etc) to map with SAML NameID attribute.
Configuration Steps
1. Configure SCIM Client application in OCI
2. Configure Okta as the IdP
3. Configure OCI-Identity-Domain as a SP
4. SSO and Provisioning setup in Okta
5. Set up policies in OCI
Testing Steps
For testing follow these steps:
- Login to Okta and create test account
- Set Okta credentials for newly created account
- Assign this user to applications created in Okta for OCI
- Wait for user to be synced from Okta to OCI-Identity-Domain
- Access OCI Login URL and select Okta Identity provider option to login
- Provide user’s Okta credential and observe seamless login
A multi-cloud/hybrid cloud IAM solution provides a powerful tool for organizations looking to streamline IAM management and improve their overall security posture in an increasingly complex cloud environment. This blog provided steps for Okta integration, but the same is also applicable for other IAM platforms.
