Oracle AI Agent Studio empowers organizations to design, manage, and interact with intelligent agents across multiple pillars. For a secure and seamless experience, establishing correct security settings and user access is critical. Below is a step-by-step guide (based on 26A documentation), to help you properly secure and provision your Oracle Fusion AI Agent Studio.
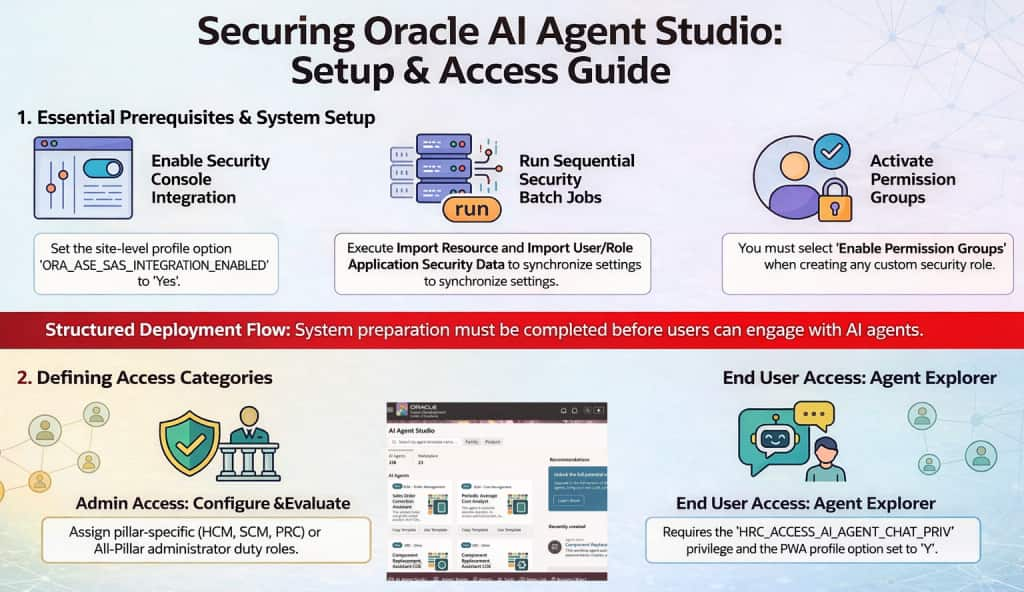
1. Essential Prerequisites & System Setup
Enable Security Console Integration\Sync with SAS Policy Store
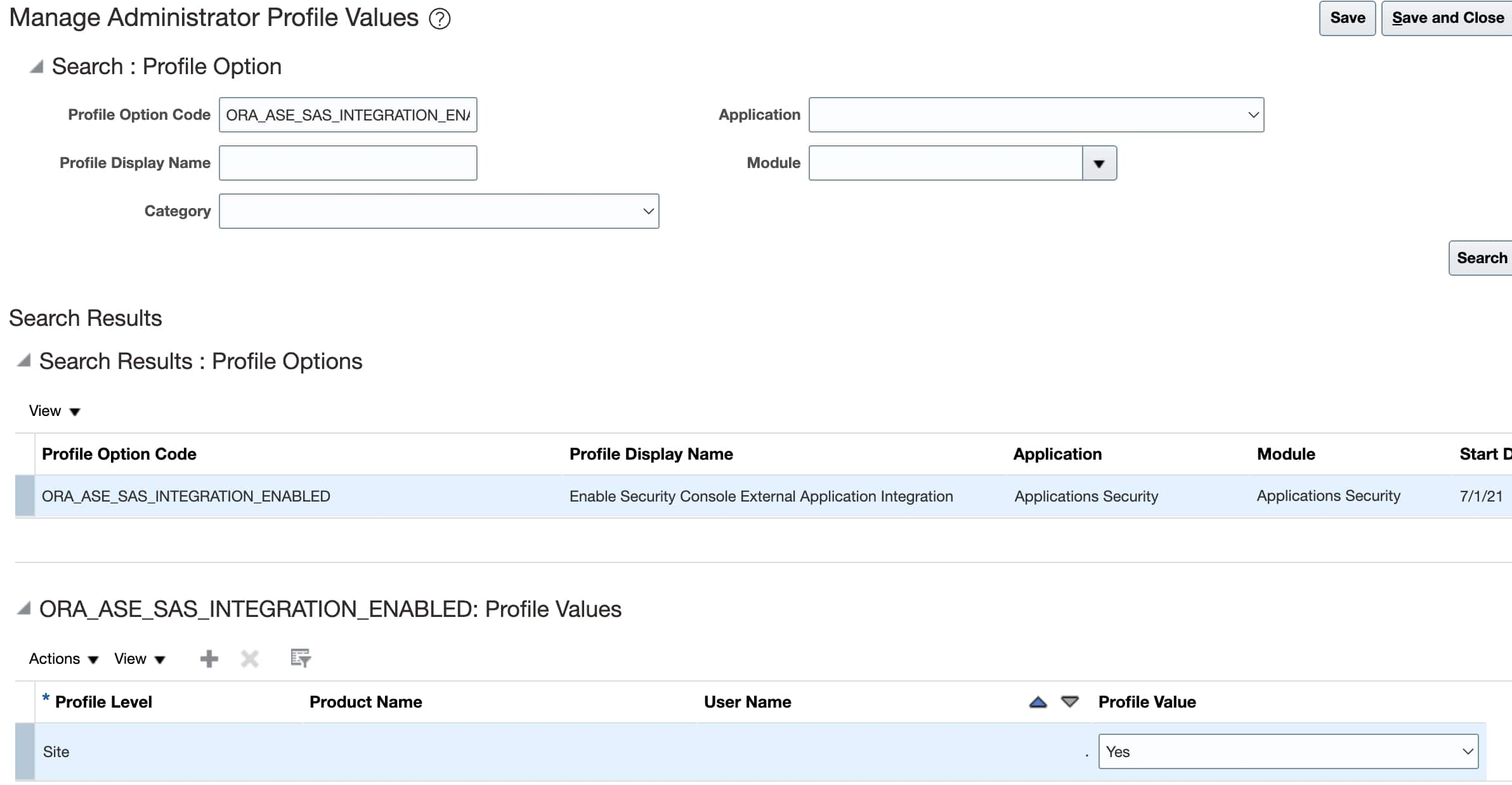
You must set the profile option ORA_ASE_SAS_INTEGRATION_ENABLED toYes at the Site level to allow the Security Console to work with permission groups.
- Navigate to Setup and Maintenance > Manage Administrator Profile Values.
- Search for the profile option code: ORA_ASE_SAS_INTEGRATION_ENABLED.
- Set the value at the Site level to Yes and save your changes.
Run Security Batch Jobs
To import resources from LDAP and populate security tables, you must execute the Import Resource Application Security Data and Import User and Role Application Security Data jobs sequentially
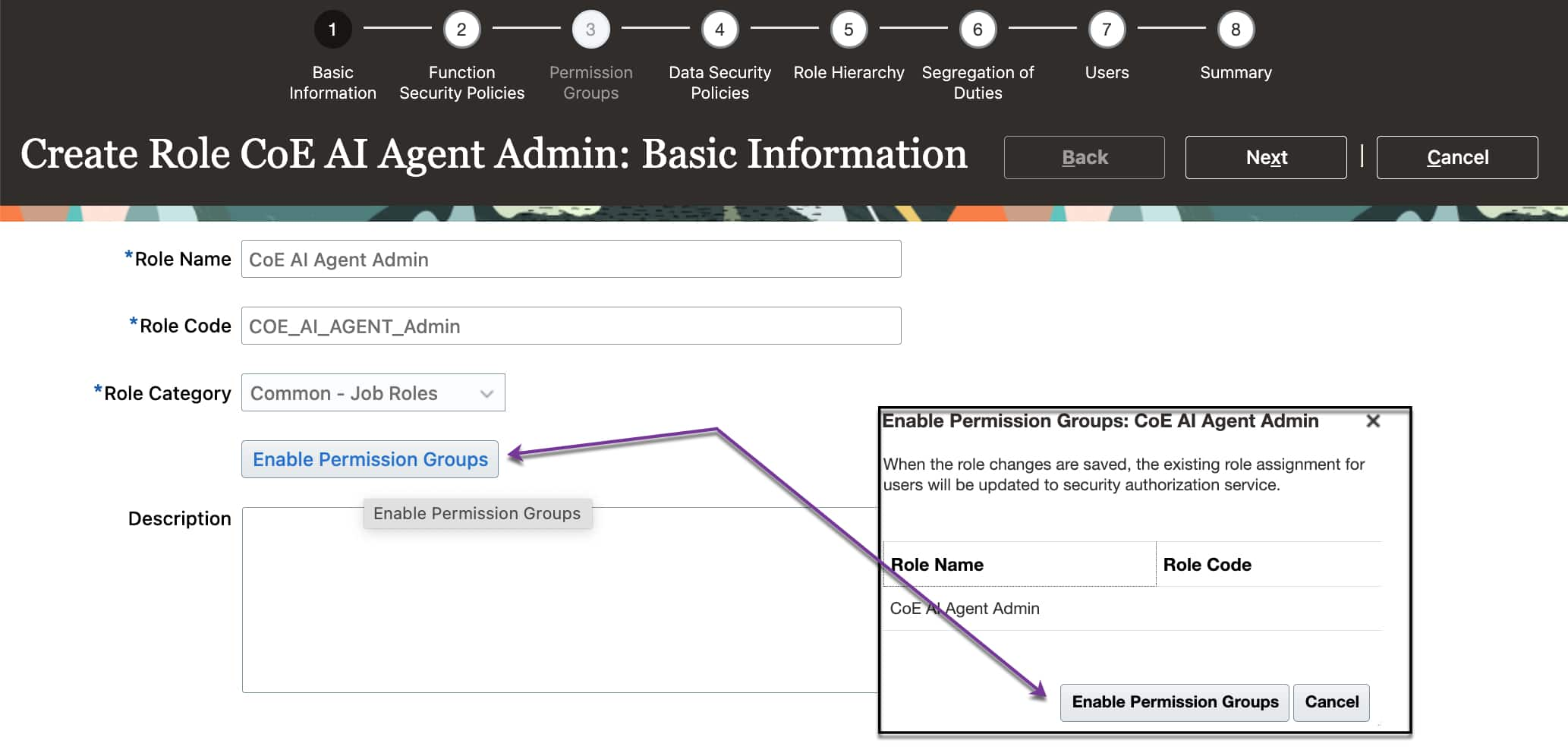
Enable Permission Groups
When you create or edit a custom security role for AI Agent Studio access, make sure to select Enable Permission Groups in the role creation workflow. This flag will enable the permission groups tab, which can be used to configure policies for the agent studio components.
2. Defining Access Categories
Admin Access
Give administrators the ability to configure and manage agents within a specific business pillar (or across all pillars): Assign the appropriate duty role: For e.g.
- HCM: ORA_DR_FAI_GENERATIVE_AI_AGENT_HCM_ADMINISTRATOR_DUTY
- SCM: ORA_DR_FAI_GENERATIVE_AI_AGENT_SCM_ADMINISTRATOR_DUTY
- PRC: ORA_DR_FAI_GENERATIVE_AI_AGENT_PRC_ADMINISTRATOR_DUTY
- All Pillars: Assign the set of all administrator duty roles for cross-pillar control
Next, we’ll walk through an example for the HCM pillar. I’ll also summarize everything in a table near the end of the blog.
AI Agent Studio Admin Role for Human Capital Management
- Create a custom role and Enable Permission Groups.
- Connect your custom role to:
- Fai GenAI Agent HCM Admin Duty (Code: ORA_DR_FAI_GENERATIVE_AI_AGENT_HCM_ADMINISTRATOR_DUTY)
- HCM Intelligent Agent Management Duty (Code: ORA_HRC_HCM_AI_AGENT_MANAGEMENT_DUTY)
- **To make it easier, I have also added the explorer user role for the admins. After all admins do need to be able to run the agents! You can decide to create this as separate role as listed in the next segment or simply add these privileges to the admin role itself.
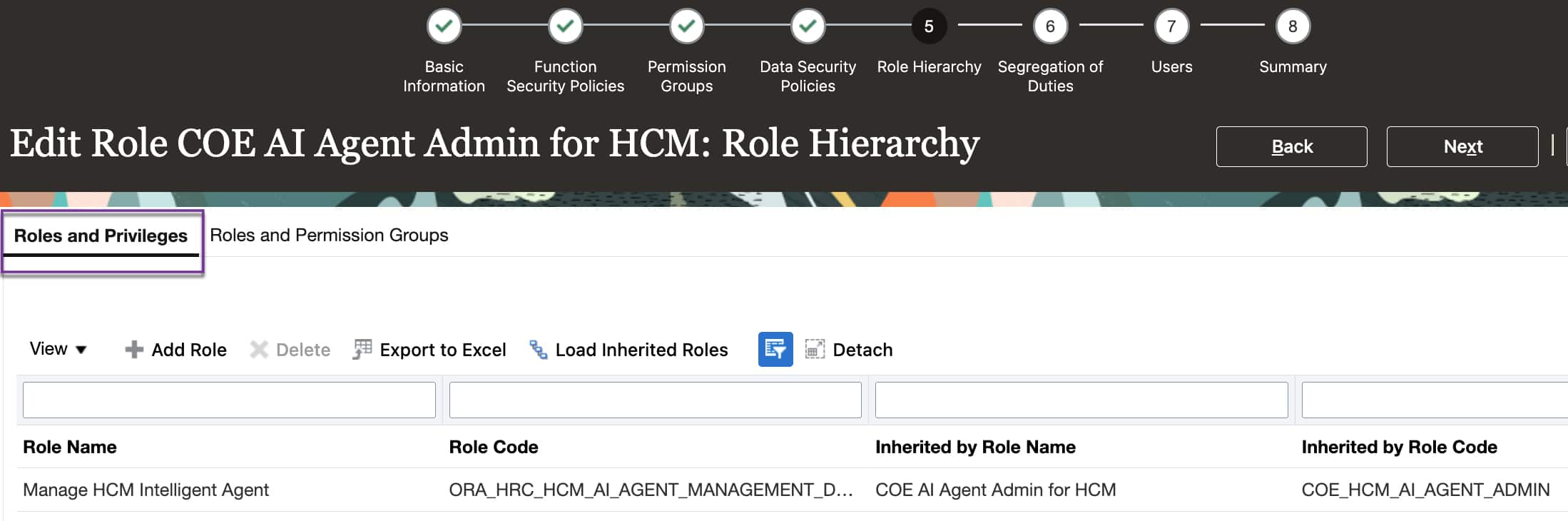
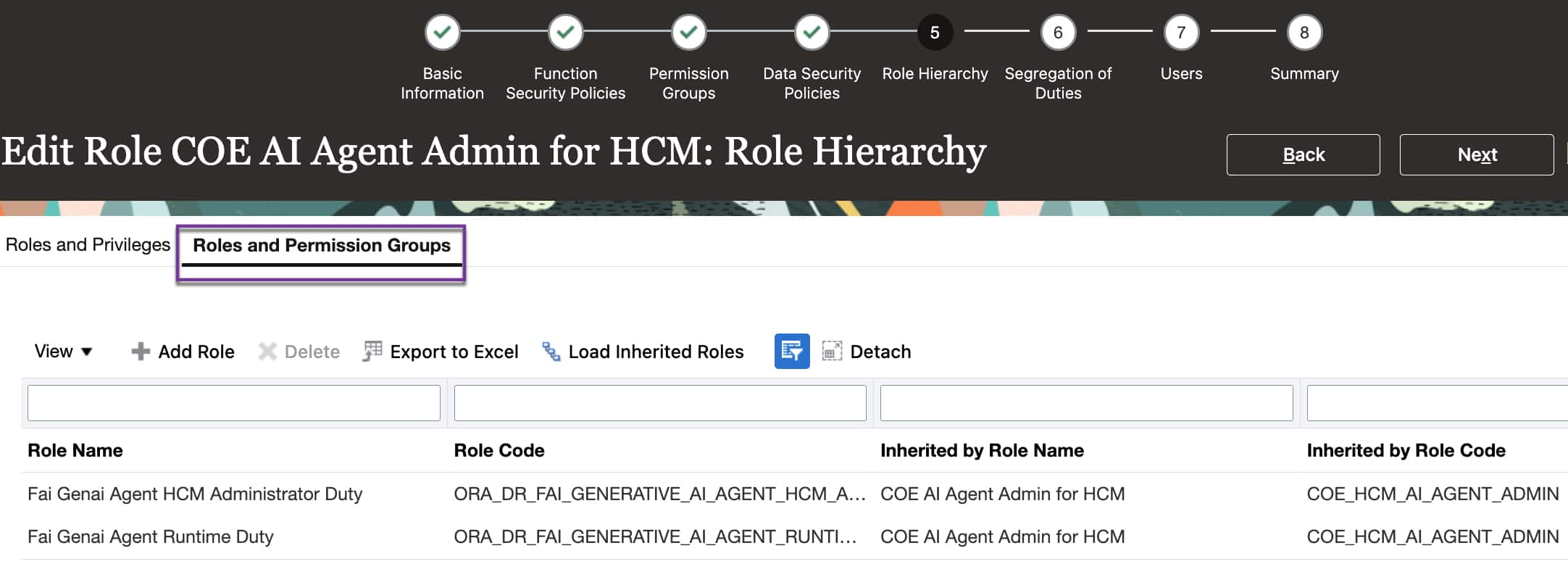
End User Access (Explorer Users)
Allow business users or employees basic access to interact with agents:
- Make sure the profile ORA_HCM_VBCS_PWA_ENABLED is set to ‘Y’.
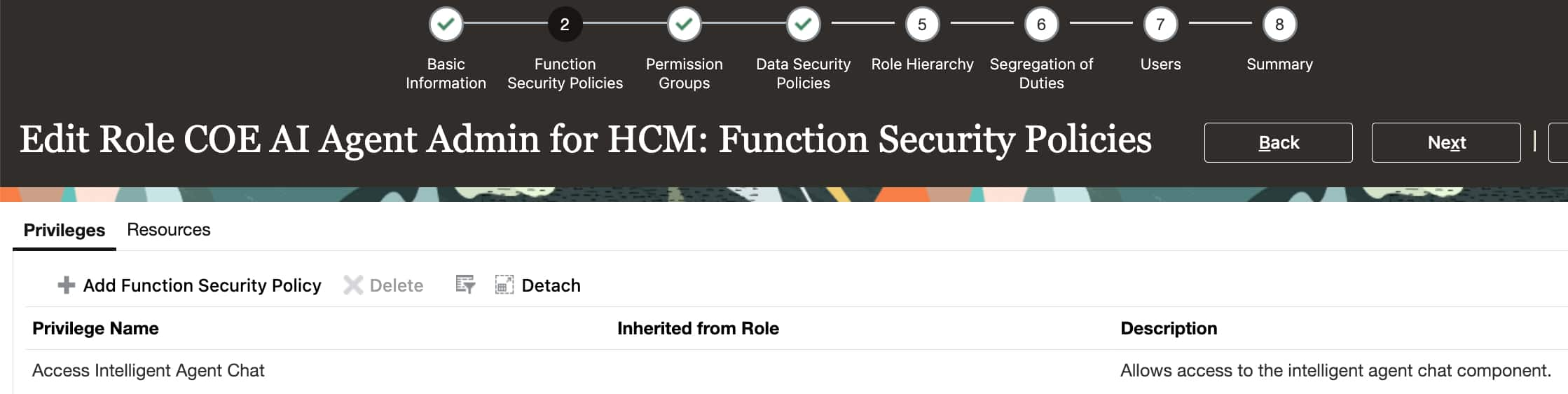
- Function Security Policies:: Add Function Security Policy: Access Intelligent Agent Chat (HRC_ACCESS_AI_AGENT_CHAT_PRIV)
- Role Hierarchy section:: Roles and Permission Groups tab: Fai Genai Agent Runtime Duty (ORA_DR_FAI_GENERATIVE_AI_AGENT_RUNTIME_DUTY)
- Assign the custom Explorer role to relevant users. Only permitted agents will be visible to each user, based on further Agent team-level access controls
- Please note: The end user access (explorer users role) doesn’t let users see all deployed agents. They will only see the agents they’re allowed to access, which is usually managed at the agent team level. (The LOV on the agents team settings will only show the roles where process group is enabled)
3. Other Access Tasks
Privilege for External REST API Tools
To authorize users to manage authentication section for external REST API tools within Agent Studio:
- Add the Create and Edit Backends for Visual Builder Studio (ORA_FND_TRAP_PRIV) privilege to their custom role.
Permission Groups for Channels
For users to create channels (e.g. Slack, MS Teams) from the Credentials tab:
- Add permission groups to a duty role and assign to the user’s custom role. Required permission groups include:
- create:ChannelManifest, read:ChannelManifest, update:ChannelManifest, delete:ChannelManifest
- create:ExternalChatCorrelation, read:ExternalChatCorrelation, update:ExternalChatCorrelation, delete:ExternalChatCorrelation
- For each, add the AllRowsAllFields security view within Details > Security Views.
- Remember to save and assign the updated duty role to the target job role.
Summary of Flow
- System Prep: Enable SAS integration, schedule and run the security import jobs, and activate permission groups on all new or existing custom roles.
- Access Assignment: Assign admin duty roles for configuration capabilities, and end user privileges for interaction, according to organizational needs. Add REST API and channel permissions to the Admin role (as needed)
| Pillar | Roles Hierarchy::Roles and Privileges | Role Hierarchy section:: Roles and Permission Groups | Function Security Policies | Enable Permission Groups? |
| HCM | ORA_HRC_HCM_AI_AGENT_MANAGEMENT_DUTY | ORA_DR_FAI_GENERATIVE_AI_AGENT_HCM_ADMINISTRATOR_DUTY | N/A | Yes |
| SCM | ORA_RCS_SCM_AI_AGENT_MANAGEMENT_DUTY ORA_RCS_SCM_AI_AGENT_MANAGEMENT_DUTY_HCM | ORA_DR_FAI_GENERATIVE_AI_AGENT_SCM_ADMINISTRATOR_DUTY | N/A | Yes |
| PRC | ORA_PO_PRC_AI_AGENT_MANAGEMENT_DUTY ORA_PO_PRC_AI_AGENT_MANAGEMENT_DUTY_HCM | ORA_DR_FAI_GENERATIVE_AI_AGENT_PRC_ADMINISTRATOR_DUTY | N/A | Yes |
| All Pillars | ORA_FAI_MANAGE_ALL_AI_AGENTS | ORA_DR_FAI_GENERATIVE_AI_AGENT_CX_ADMINISTRATOR_DUTY ORA_DR_FAI_GENERATIVE_AI_AGENT_FIN_ADMINISTRATOR_DUTY ORA_DR_FAI_GENERATIVE_AI_AGENT_GRC_ADMINISTRATOR_DUTY ORA_DR_FAI_GENERATIVE_AI_AGENT_HCM_ADMINISTRATOR_DUTY ORA_DR_FAI_GENERATIVE_AI_AGENT_PRC_ADMINISTRATOR_DUTY ORA_DR_FAI_GENERATIVE_AI_AGENT_PRJ_ADMINISTRATOR_DUTY ORA_DR_FAI_GENERATIVE_AI_AGENT_PSC_ADMINISTRATOR_DUTY ORA_DR_FAI_GENERATIVE_AI_AGENT_SCM_ADMINISTRATOR_DUTY | N/A | Yes |
| Explorer Users | None | ORA_DR_FAI_GENERATIVE_AI_AGENT_RUNTIME_DUTY | HRC_ACCESS_AI_AGENT_CHAT_PRIV | Yes |
***Important Note: If you decide to include Agent Explorer capabilities within an Admin role itself, be sure to also assign the runtime/explorer duty roles (from the last row in the table) to the Admin role.
Useful Links
- Let’s Talk Tech – Cloud Customer Connect Live Demo and Recording:
https://community.oracle.com/customerconnect/events/606876-hcm-lets-talk-tech-getting-started-with-ai-agent-studio?utm_source=community-search&utm_medium=organic-search&utm_term=AI+Agent+Studio - Product Documentation:
https://docs.oracle.com/en/cloud/saas/fusion-ai/aiaas/access-ai-agent-studio.html
