Introduction
The European Union’s Digital Operational Resilience Act (DORA) establishes stringent standards for Information and Communication Technology (ICT) risk management in financial institutions. DORA, a new EU regulation promoted by the Council of the European Union and the European Parliament, is dedicated to achieving a high level of operational resilience in digital Information and Communication Technology (ICT) for regulated financial entities. DORA mandates that financial entities must go beyond simple defense. They must be able to resist disruptions by building, ensuring, and reviewing the operational integrity and reliability of ICT systems throughout an incident. As a key ICT vendor, Oracle must assist financial entities in adhering to these regulations.
Exadata (available in multiple deployments) and Recovery Appliance (available as Zero Data Loss Recovery Appliance (ZDLRA) on-premises and Zero Data Loss Recovery Service (ZRCV) in the cloud) play a pivotal role in managing and deploying infrastructure for entities subject to DORA. Exadata’s engineered architecture, optimized for high-performance Oracle Database workloads, seamlessly aligns with DORA’s requirements through its built-in resilience, automation, and security features. Deployable on-premises, via Oracle Cloud Infrastructure (OCI), in hyperscalers such as Oracle Database@Azure, Oracle Database@Google Cloud, and Oracle Database@AWS, or as Exadata Cloud@Customer, it helps financial entities to withstand disruptions while ensuring data sovereignty and performance. The Recovery Appliance is built on the same core architecture as Exadata, making it part of Oracle’s broader family of Engineered Systems. This shared foundation ensures seamless integration, consistent management, and inherited enterprise-grade qualities. The Oracle Zero Data Loss Recovery Appliance provides data protection for Oracle databases. In addition, it offers resilient Zero Data Loss Recovery by continuously protecting databases and ensuring reliable recovery. Recovery Appliance provides Cyber Vaults and Clean Room/Isolated Recovery Environments (IREs) serve as pillars of resilience. A Cyber Vault functions as an immutable, offline repository that enforces Write Once, Read Many (WORM) policies and air-gapping protocols. This ensures backups remain tamper-proof and inaccessible to attackers even during an active breach, thereby minimizing data loss and enabling rapid restoration with minimal disruption.
What is DORA?
DORA mandates that financial institutions adhere to rigorous guidelines to safeguard against ICT-related incidents, encompassing protection, detection, containment, recovery, and repair measures. The regulation specifically addresses ICT risks, introducing rules for risk management, incident reporting, operational resilience testing, and oversight of third-party ICT providers. DORA went into effect starting January 17th, 2025.
DORA guidelines consist of nine chapters with fifty-eight articles, followed by six additional articles in the Amendments section. DORA Articles 7-12 are directly relevant to the ICT systems covered in this blog.
This technical blog explores how Exadata and the Recovery Appliance meet the specific requirements of DORA articles 7-12 as applicable to these systems, offering actionable insights for financial entities striving to achieve DORA compliance.

Figure 1 – What is DORA
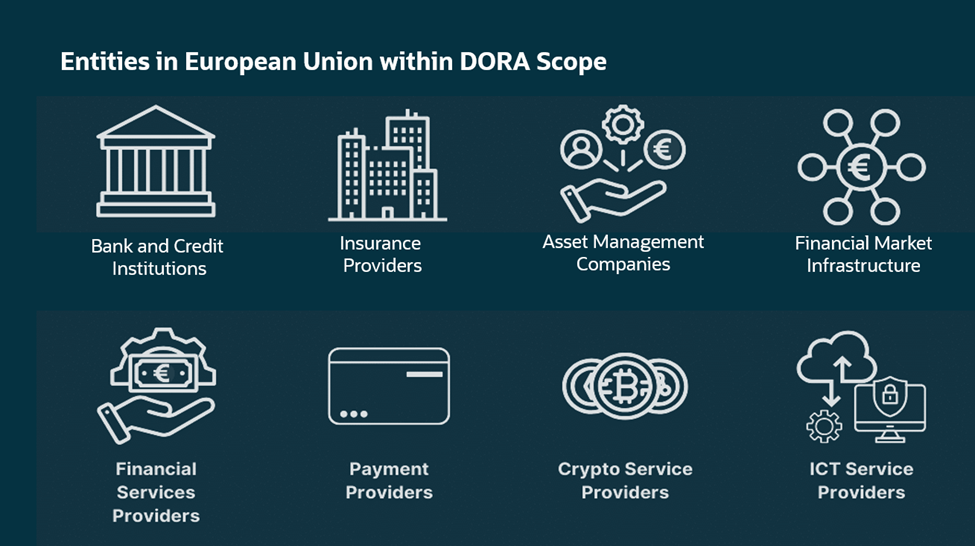
Figure 2 – Entities in EU under DORA purview
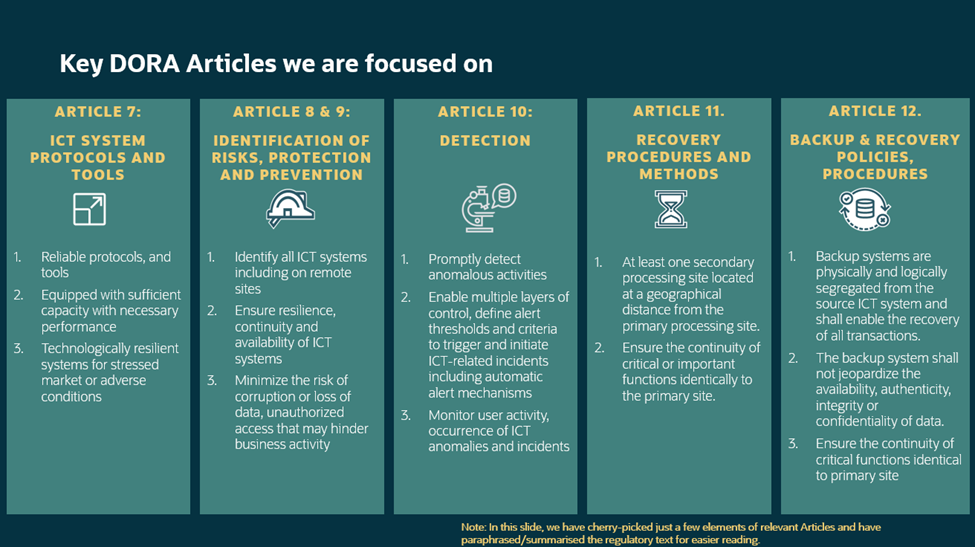
Figure 3 – Relevant DORA Articles
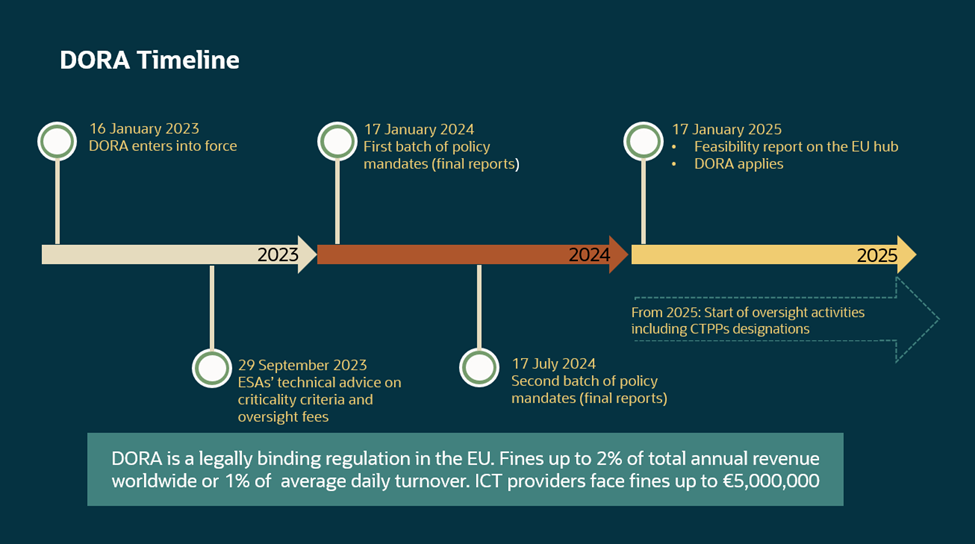
Figure 4 – DORA Timeline
ICT Systems, Protocols, and Tools: DORA Article 7
Article 7 mandates that financial entities use and maintain updated ICT systems, protocols, and tools that are appropriate, reliable, scalable, and resilient. The ICT systems must have enough capacity to accurately process the necessary data for performing activities and providing timely services. Oracle Exadata and Recovery Appliance integrate compute, storage, and networking in a scale-out architecture optimized for Oracle Database and its recovery, excelling in AI, Online Transaction Processing (OLTP), and analytics workloads with up-to-the-second recovery.
Requirement: Entities must identify and classify all ICT assets, map dependencies, and assess risks continuously. ICT systems must be reliable, equipped with sufficient capacity and performance, and resilient.
Exadata and Recovery Appliance Alignment: Exadata, with its integrated architecture, provides a full-stack, scale-out platform for running Oracle Database workloads, including AI-driven analytics and transaction processing, with built-in optimizations for performance and security. Exadata ensures tailored deployments across on-premises, Cloud@Customer, OCI, and multicloud (Database@Azure, Database@Google, Database@AWS), allowing independent scaling of compute and storage to match workload needs without over-provisioning. This enables financial entities to consolidate diverse operations (for example, OLTP, Analytics, etc.). The Recovery Appliance provides policy-based management for lifecycle control (for example, retention, immutability), with storage savings through compression.
Exadata delivers high availability through online patching, intelligent storage offloading for SQL processing, Oracle Real Application Clusters (Oracle RAC), Data Guard, and Oracle GoldenGate. Exadata ensures SLAs with MAA Diamond, Platinum, Gold, and Bronze validation, reducing downtime and ensuring consistent performance for financial applications. Recovery Appliance provides continuous integrity validation, real-time metrics for recovery windows, and immutable backups to prevent deletion/corruption. It achieves sub-second RPOs with up to 35 TB/hour restores, alerting SLA breaches for proactive management.
Exadata provides dynamic scaling from small to petabyte-sized databases, with multi-terabyte scan throughput and thousands of cores. Pay-per-use models handle peak demands dynamically. The Recovery Appliance scales from 274 TB to 1.57 PB of backups in a single rack, with an option to add multiple racks like Exadata.
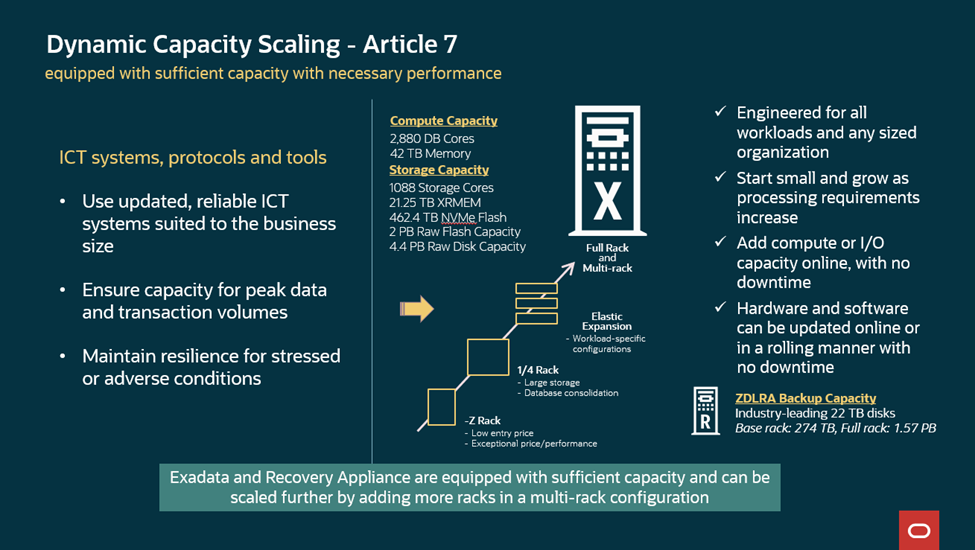
Figure 5 – Dynamic Scaling
Identification: DORA Article 8
Article 8 requires financial entities to identify, classify, and adequately document all ICT-supported business functions, roles, and responsibilities. Financial entities must continuously identify all sources of ICT risk. All information and ICT assets (including remote sites, network resources, and hardware) must be identified, with critical ones mapped along with their configurations, links, and interdependencies.
Requirement: Financial entities shall identify and map all information/ICT assets (including remote sites, networks, hardware), configurations.
Exadata and Recovery Appliance Alignment: Exadata and the Recovery Appliance integrate with Oracle Enterprise Manager (OEM) and other tools to facilitate the identification requirements. They enable automated discovery, mapping, and monitoring in Oracle database environments, helping financial entities document assets and dependencies while supporting compliance through Oracle’s Maximum Availability Architecture. OEM cloud control discovers and classifies Exadata and Recovery Appliance components by type, criticality, and dependencies. Exadata’s OEM and Audit Vault provide real-time anomaly detection and logging. OEM’s machine learning-based diagnostics identify deviations in performance metrics, while Audit Vault captures all database access and changes.
OEM has built-in automation, updatable inventories for discovered assets, configurations, and dependencies, which are revised post major changes. OEM conducts annual ICT risk assessments, including compatibility checks and vulnerability scans, before and after new integrations. Real-time redo transport and anomaly detection identify risks such as data corruption or cyber threats in Recovery Appliance backup streams. The Recovery Appliance also supports ongoing vulnerability assessments with metrics on recovery windows, reviewed periodically for evolving threats. It catalogs all the dependencies on external storage and third-party tools in recovery workflows.
Technical Detail: Exadata’s storage cells monitor I/O patterns to detect anomalies, such as unexpected spikes indicating potential attacks. OEM integrates with Oracle Advanced Security for real-time threat detection, flagging SQL injection or privilege escalation attempts. Security Information and Event Management (SIEM) integration enables centralized alerting.
Benefit: Exadata’s proactive detection meets the requirement for rapid identification of ICT incidents, minimizing response times.
Protection and Prevention: DORA Article 9
Article 9 requires financial entities to continuously monitor and control the security and functioning of ICT systems and tools and minimize the impact of ICT risk on ICY systems through the deployment of appropriate ICT security tools, policies, and procedures. Financial entities shall implement ICT solutions and processes to ensure the security of the means of the transfer of data, minimize the corruption or loss of data, unauthorized access, and breaches of confidentiality of data.
Requirement: Article 9 of DORA requires financial entities to establish and implement proportionate policies, procedures, and ICT systems to protect networks and information systems from ICT risks. This includes continuous risk identification, security measures for data and systems, backup and continuity procedures, and physical controls. They must deploy mechanisms to detect ICT anomalies and incidents promptly, with continuous monitoring.
Exadata and Recovery Appliance Alignment: Exadata’s layered security—spanning server, network, database, and storage—delivers robust protection. Oracle Transparent Data Encryption (TDE) secures data at rest, while network micro-segmentation isolates traffic. Oracle Database Vault enforces least-privilege access. Exadata enforces confidentiality, integrity, and availability (CIA) using Transparent Data Encryption (TDE), role-based access control (RBAC), and network firewalls. Regular updates through automated patching and vulnerability scans ensure ongoing protection. Exadata integrates with Recovery Manager (RMAN) for policy-based backups; supports recovery testing using clone databases and snapshot simulations without production impact, achieving RTO in a few minutes. Oracle Transparent Application Continuity (TAC) enables applications to automatically recover from database interruptions – planned (for example, maintenance) or unplanned (for example, outages, failovers) without manual intervention or application awareness. Financial entities can use Application Continuity to demonstrate proactive compliance through resilience simulations aligned with DORA’s testing mandates.Oracle Data Safe service is designed to protect Oracle databases, including those on Exadata infrastructure. Oracle Data Safe is particularly valuable for Exadata users handling high-volume, mission-critical workloads with sensitive data. It provides sensitive data discovery and masking, security posture assessment, activity auditing and monitoring, and regulatory compliance acceleration.
The Recovery Appliance provides robust, end-to-end encryption to secure backups against data breaches while maintaining performance for real-time protection. It integrates seamlessly with Oracle Transparent Data Encryption for database-level protection (if backups arrive encrypted with TDE, the Recovery Appliance ingests them as-is; otherwise, it applies its own encryption, decrypting only for recovery as needed. The Recovery Appliance implements Role-based Access Control (RBAC) to enforce least-privilege access, harden security, and support auditing for compliance. RBAC restricts operations using named user roles, which enforce permissions, quorum requirements for sensitive actions, and disable powerful default users.
Technical Detail: Exadata provides out-of-the-box security choices, including Exadata RDMA Secure Network Isolation, Security Enhanced Linux, and close adherence to the US DOD STIG security framework, to increase data confidentiality. Exadata runs an optimized Oracle Linux with only the essential packages required for Oracle Database. Exadata’s 100 GbE RDMA Network Fabric uses VLANs to segregate traffic, reducing attack surfaces. TDE leverages hardware-accelerated encryption on Exadata storage cells, minimizing performance overhead. Immutable backups through Zero Data Loss Recovery Appliance (ZDLRA) protect against ransomware. Data is stored redundantly on Exadata with a minimum of 2 copies (normal redundancy) of every file extent; Oracle recommends 3 copies (high redundancy) for all databases. In addition, Exadata employs Oracle’s Hardware Assisted Resilient Data (H.A.R.D.), a protocol to check data as it is written to disk. HARD checks eliminate a large class of data resilience failures that other platforms are unable to address. Exadata also automatically and transparently scans for and repairs silent corruptions (also known as bit-rot). Oracle Data Safe helps protect sensitive data in Oracle databases on Exadata infrastructure by providing automated data discovery and data masking features.
Benefit: Exadata’s encryption and access controls align with Article 9’s protection mandates, ensuring data integrity and confidentiality. Sensitive data can be protected using Oracle Data Safe.
Detection: DORA Article 10
Article 10 of DORA requires financial entities to implement and regularly test detection mechanisms to identify anomalous activities. These mechanisms should incorporate multiple layers of control, predefine alert thresholds and criteria to activate ICT incident response processes, and automatic notifications of alerts to responsible staff.
Requirement: Financial entities shall have mechanisms in place to promptly detect anomalous activities, including ICT network performance issues and ICT-related incidents, and to identify potential material single points of failure. The detection mechanisms shall enable multiple layers of control, define alert thresholds and criteria to trigger and initiate the ICT-related incident response process, including automatic alert mechanisms for the personnel in charge of ICT-related incident response.
Exadata and Recovery Appliance Alignment: Exadata detects network anomalies, storage failures, or single points (for example, RDMA fabric health checks). Oracle provides regular testing through simulated incidents via MAA validation that ensures prompt identification. Exadata System Software includes dedicated monitoring with a focus on cyberthreats. Exadata also provides oversight with low-overhead logging for user sessions and attack patterns. Real-time redo transport monitoring detects backup anomalies or failure points in replication chains with the Recovery Appliance. The Recovery Appliance provides layered validation (for example, checksums on changed blocks) with configurable thresholds for RPO breaches. OEM’s auto alerting integrates with response workflows such as isolating compromised streams. Oracle provides various monitoring and observability tools to proactively monitor the system, including Enterprise Manager, Automatic Service Requests (ASR), Exachk, and Automatic Intrusion Detection Environment (A.I.D.E). Exadata has a provision for installing third-party security software for further detection. ExaPortMon automatically detects stalled switch ports and moves the IP address of the stalled port to the other active RoCE port on the database or storage server, enabling network traffic to flow. The IP address is moved back to its original port when the switch port issue is resolved
Technical Detail: RAC’s active-active clustering redistributes workloads during node failures, achieving recovery time objectives (RTO) under 4 hours. Data Guard’s Fast-Start Failover automates switchovers to standby databases, while ZDLRA’s real-time redo transport ensures no data loss. Exadata’s automated patching via OEM minimizes vulnerabilities during recovery.
Benefit: Exadata and the Recovery Appliance provide detection of anomalies through advanced monitoring, AI analytics, and automated alerting capabilities of Oracle Enterprise Manager. HA and recovery mechanisms satisfy Article 10’s detection requirements, supporting critical financial operations.
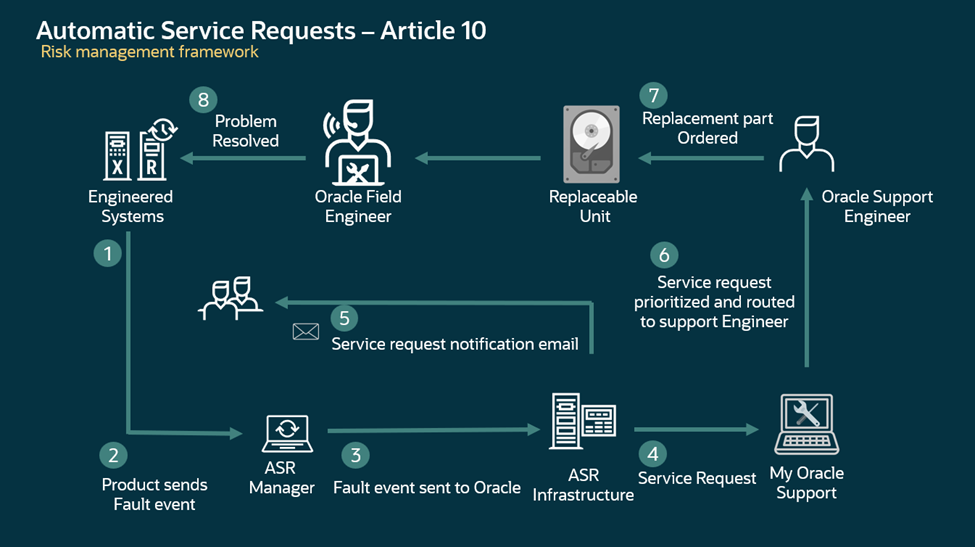
Figure 6 – Oracle Automatic Service Request (ASR)
Response and Recovery: DORA Article 11
Article 11 of DORA requires financial entities to implement an ICT business continuity policy through dedicated, documented plans, procedures, and mechanisms to ensure continuity of critical functions; enable rapid response, resolution, containment, and recovery from ICT incidents while minimizing damage. Financial entities should develop response and recovery plans, maintain and periodically test business continuity plans.
Requirement: Response and Recovery – Financial entities shall put in place a comprehensive ICT business continuity policy. The financial entities shall quickly, appropriately, and effectively respond to and resolve all ICT-related incidents in a way that limits the damage and prioritizes the resumption of activities and recovery actions. Financial entities shall test the ICT business continuity plans and ICT response and recovery plans in relation to ICT systems supporting all functions at least yearly, as well as in the event of any substantive changes to ICT systems supporting critical or important functions. Financial entities shall include in the testing plans scenarios of cyber-attacks and switchovers between the primary ICT infrastructure and the redundant capacity.
Exadata and Recovery Appliance Alignment: Exadata facilitates incident response with built-in redundancy, automated failover, and OEM-driven workflows for rapid recovery and communication. Exadata and the Recovery Appliance support automated orchestration, playbook integration, and testing tools via Oracle Enterprise Manager. Oracle MAA on Engineered Systems provides MAA best practices and blueprint recommendations in an integrated deployment that is found on Engineered Systems, such as the Oracle Exadata Database Machine. OEM orchestrates timely, coordinated responses via automated diagnostics and containment. MAA supports automated backup testing via ZDLRA and RMAN, with integration into OEM for test orchestration.
Technical Detail: The Recovery Appliance’s Validated Backup feature verifies backup integrity, while RMAN automates point-in-time recovery tests. Exadata’s snapshot cloning creates isolated test environments simulating disaster recovery scenarios. OEM generates compliance reports for test outcomes, supporting European Banking Authority (EBA) audits.
Benefit: Exadata’s automated testing aligns with Article 11, ensuring recovery processes meet DORA’s stringent standards.
Backup policies and procedures, restoration and recovery procedures and methods: DORA Article 12
Article 12 of DORA requires financial entities to implement backup policies and procedures (specifying data scope and minimum frequency based on criticality/confidentiality) and restoration/recovery procedures to minimize disruption and business loss. They shall establish activatable backup systems that preserve network/information security and data attributes (availability, authenticity, integrity, confidentiality), with periodic testing of all procedures
Requirement: DORA requires financial entities to develop, document, and implement backup policies and procedures, restoration, and recovery methods to minimize downtime, disruption, and data loss during ICT incidents. This includes defining data scope and frequency, activating secure backup systems with periodic testing, maintaining segregated restoration environments, ensuring redundant capacities, establishing secondary processing sites, determining recovery time objectives (RTO) and recovery point objectives (RPO), and performing integrity checks during recovery.
Exadata and Recovery Appliance Alignment: Exadata (a high-performance, resilient database platform) and the Recovery Appliance (a dedicated backup and recovery system) directly address these requirements through automated, policy-driven mechanisms, real-time replication, and integration testing via tools like Oracle Enterprise Manager (OEM). The Recovery Appliance specializes in zero-loss backups and automated recovery, using incremental forever strategies and immutability for robust compliance.
Technical Detail: OEM and Recovery Appliance configurable policies define backup scope (for example, full, incremental backups for critical data) and frequency based on confidentiality/criticality. MAA tiers and procedures outline restoration methods, achieving sub-minute RTOs for database recovery at the primary or the remote site. Secure backups with Recovery Manager (RMAN) with added encryption preserve CIA. The backups on Recovery Appliance are self-validated after each full and incremental backup is taken. Periodic OEM-orchestrated tests (for example, quarterly, annually) validate procedures without security compromise at the local or remote sites. Exadata and the Recovery Appliance both support geographically distant secondary sites (on-premises, OCI, multicloud) with identical capabilities and immediate accessibility through automated failover, meeting both RPO and RTO. During recovery, automated multilevel checks (for example, block validation, reconciliations) ensure data integrity; this applies to external reconstructions for system consistency post-recovery.
Benefit: Exadata and Recovery appliance work in tandem (for example, Recovery Appliance backs up Exadata environments seamlessly), offering end-to-end automation through tools like OEM for policy enforcement and audits.
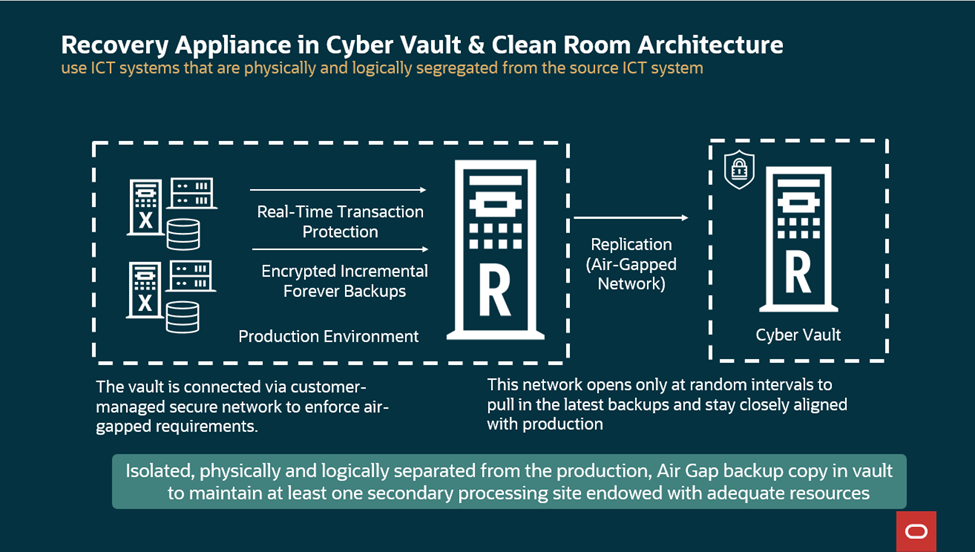
Figure 7 – Recovery Appliance supports geographically distant sites with immutability
Conclusion: Exadata and Recovery Appliance help EU customers to be DORA compliant
Oracle Exadata’s engineered resilience, automation, and security features align directly with DORA Articles 7-12, providing financial entities with a robust platform to manage ICT risks. By leveraging Exadata’s capabilities—whether on-premises, in OCI, in multicloud, or via Cloud@Customer—organizations can transform DORA compliance into a strategic advantage. Oracle Exadata and the Recovery Appliance together form a resilient foundation for financial entities seeking compliance with the Digital Operational Resilience Act (DORA). By ensuring high availability, fault tolerance, and streamlined disaster recovery, both the Engineered Systems align with DORA’s core principles – data integrity, operational continuity, and incident recovery readiness. Exadata’s optimized database performance enhances real-time risk monitoring, while the Recovery Appliance automates backup validation and minimizes data loss, directly addressing DORA’s regulatory compliance for ICT continuity and resilience testing. The integrated architecture of both Exadata and Recovery Appliance simplifies governance and auditability – key elements under DORA’s resilience framework. Implementing Exadata and the Recovery Appliance empowers organizations to move beyond mere compliance, building a proactive, robust digital ecosystem that not only meets regulatory demands but also strengthens trust, security, and long-term business continuity.
