Oracle Exadata is engineered for extreme database performance and rock-solid security, integrating advanced protection across infrastructure, data, processes, and the operating system. Oracle Exadata System Software is the core component that powers the platform, delivering advanced database functionalities and optimizations. Oracle Linux serves as the operating system, providing a stable and secure environment for Exadata’s operations. It is tightly integrated with Exadata’s hardware and software stack to help ensure optimal database performance and operational efficiency.
Oracle Linux integrates security features, such as Security-Enhanced Linux (SELinux), to provide enhanced protection. Starting with Exadata System Software 25ai, Release 25.2, SELinux is enabled in ‘permissive’ mode by default, ensuring that access monitoring is active out-of-the-box. The enablement benefits all Exadata servers, including Bare metal, KVM hosts, KVM guest Database servers, and Storage servers. Update August 2025: With security as the primary objective, SELinux in permissive mode has now been enabled by default with new installs of Exadata System Software Release 24.1.12 and Release 25.1.6, and in all subsequent releases.
Security with Access Detection
SELinux manages security by monitoring interactions between users, processes, and resources per established security policies. It leverages Mandatory Access Controls (MAC) to strictly report or control what users, processes, and services can access on the system, beyond normal file permissions. On Exadata, critical platform and database access policies are provided in the Exadata system image. Access policies and rules are structured on the principle of least privilege, designed to flag any access that is not explicitly permitted.
Specifically, SELinux verifies that a user/process/service can:
- Read, write, or execute a file
- Communicate over a network port
- Access a specific device or resource
Operational Modes
SELinux is a Linux security feature that supports three operational modes:
- Enforcing: Actively blocks unauthorized access to system devices, resources, ports, and files
- Permissive: Logs policy violations without enforcement
- Disabled: Performs no checks or enforcement
Starting with Exadata System Software 25ai Release 25.2, SELinux is set to permissive mode by default. All new Exadata software deployments with Release 25.2 will use this mode as the default. Exadata systems updating to Exadata System Software 25ai Release 25.2 will retain their prior set mode, but administrators can choose to change SELinux mode through explicit configuration action. Update August 2025: SELinux in permissive mode has been enabled by default with new installs of Exadata System Software Release 24.1.12 and Release 25.1.6, and in all subsequent releases.
Access Decision Workflow
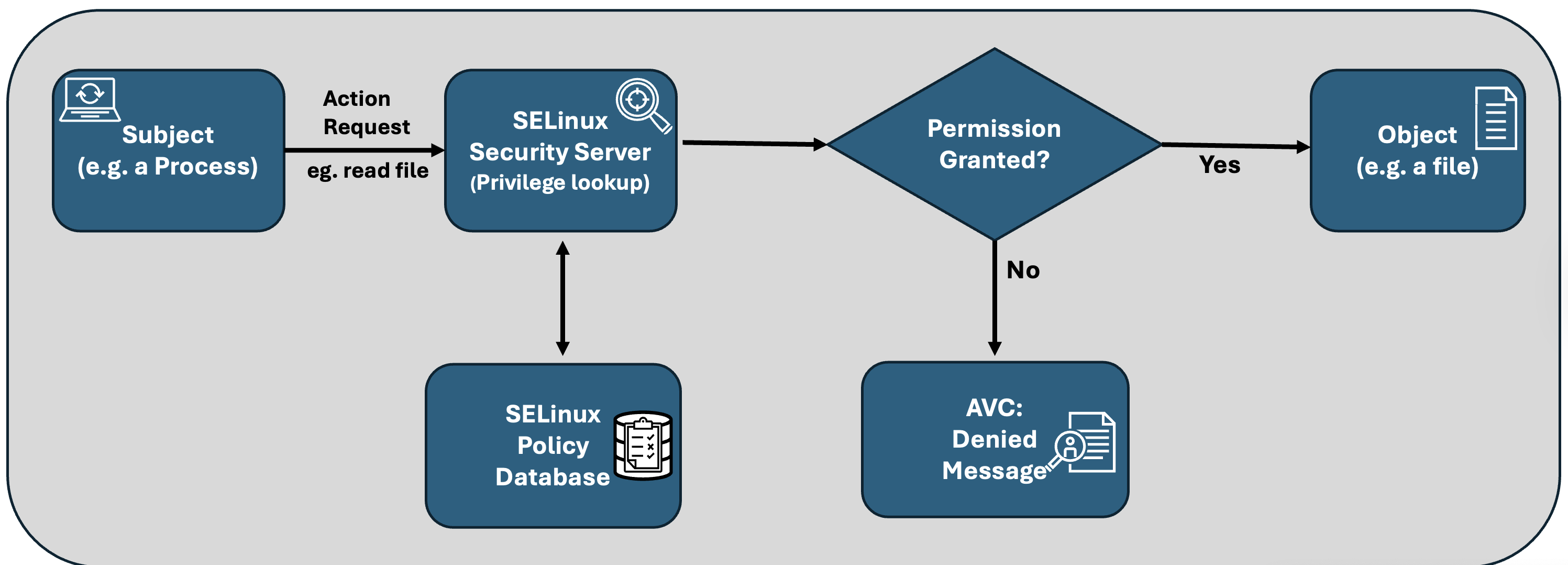
When a user or process tries to access an Exadata resource object, the Linux kernel consults with a core component within SELinux, called the SELinux Security Server, that evaluates security policies and makes access control decisions. The security server checks the user or process label (which defines what a running program is allowed to do) and the target resource’s label (which represents the security context of accessed resources like files, ports, or devices) and consults the Policy Database for active policy rules and context tables. When the kernel detects that this access is not explicitly allowed, this results in a policy denial. However, the access is permitted. The Access Vector Cache (AVC) logs these decisions as “AVC: denied” messages.
This diagram shows a high-level view of the functional decision workflow.
Managing Configuration
In Exadata system software versions before 25.2, SELinux is disabled by default. To benefit from the latest enhancement, administrators may want to switch SELinux mode manually. This section introduces the necessary CLI commands and options to guide one through the configuration process.
Exadata includes the Host Access Control (hac) command, which can be used to view and configure SELinux parameters. While native Linux tools or editing /etc/selinux/config can also be used to change SELinux configuration, the recommended best practice is to use this command.
| $ hac selinux --help # Host Access Control command SELinux configured state control |
The command output above displays a summary of available options and usage instructions. The available options are descriptive and help users configure, view, manage, and troubleshoot SELinux settings and modes directly from the command line.
Mode Change Impact
Before a new SELinux mode change takes effect system-wide, all processes must start under an updated security context. Because of this, changing the SELinux mode setting typically requires a system reboot. When Exadata System Software 25.2 is newly deployed, and the default setting of ‘permissive’ is the desired mode, no user action is required. If the default mode setting of ‘permissive’ is changed, the system will need to be rebooted. Update August 2025: SELinux in permissive mode has been enabled by default with new installs of Exadata System Software Release 24.1.12 and Release 25.1.6, and in all subsequent releases.
Monitoring and Triaging Access Events
Monitoring and triaging access events is vital for detecting security threats and ensuring a prompt response to unauthorized activities. A Linux command is available to view SELinux events, such as denials, login attempts, and system changes. The command is typically used to search SELinux audit logs, including AVC messages, which record access denials based on prebuilt Exadata policies. The audit logs are essential for system administrators, as they provide detailed insight into what access was blocked, which process attempted it, and why it was denied. The command syntax for viewing audit logs for AVC denial messages is:
| $ ausearch -m avc # filters audit logs for AVC denial messages |
With the ability to monitor, view, and triage access denials using the output of ausearch, SELinux empowers Exadata environments with both proactive protection and responsive diagnostics, strengthening overall system resilience without compromising performance. This ability makes it straightforward to integrate SELinux AVC event monitoring with existing monitoring tools and Security Information and Event Management (SIEM) platforms, supporting centralized analysis and alerting. As a result, an enterprise can incorporate SELinux auditing into broader security operations workflows.
Impact of Software Updates
Exadata System Software is designed to preserve existing SELinux settings during normal operation and software updates. Additionally, SELinux policy updates are automatically applied through software updates and upgrades to accommodate changes in the system, kernel, software, or filesystems that may affect security contexts or access controls.
Exadata: Secure by Default
Exadata security is not an afterthought; it is engineered and embedded. SELinux on Exadata monitors fine-grained access control at the OS level, and instead of blocking actions that violate set policies, it records the violations to audit logs, adding a critical layer of protection to the platform’s multi-tiered security architecture. This permissive mode is highly valuable, as it allows administrators to monitor, analyze, and fine-tune policies without disrupting operations. The non-disruptive audit trails help identify necessary policy adjustments, enhancing the long-term security posture.
SELinux fortifies Exadata with intelligent, adaptive security, empowering organizations to confidently deliver mission-critical workloads at scale with uncompromised protection.
Acknowledgements
Special thanks to Alex Blyth, a seasoned Exadata product manager, technologist, and operational specialist, for his invaluable insights and support.
