At Oracle, we’re constantly working to help our customers secure their applications and workloads. We are excited to announce that our customers can now use KubeArmor, a runtime security engine, to secure their containerized applications on Oracle Container Engine for Kubernetes (OKE). The announcement affirms our commitment to embrace open-source ecosystem.
Maintaining a strong security posture of your Kubernetes clusters goes beyond the static security of container images and hardening the Kubernetes cluster – it also looks at the runtime security of containerized applications. Traditionally, the task of securing the application during runtime has been the responsibility of specialized security teams. However, the rapid pace and intricate nature of agile and cloud-native development have led to developers playing a larger role in identifying and mitigating security vulnerabilities in their code. As a result, developers are embracing a “shift left” approach, incorporating security considerations from the start. The security duties of developers have expanded to include the entire container lifecycle, encompassing not just planning, coding, scanning, and deployment, but also the runtime environment. They must now keep security in mind not only while they are developing, but also once their containers are in use in the runtime environment.
When it comes to the runtime security of applications running in the Kubernetes clusters, the common solutions that come to mind are KubeArmor, Falco, and Tracee. In this blog, we are going to discuss the runtime security provided by KubeArmor.
KubeArmor is an open source zero-trust security tool for Kubernetes from AccuKnox. It provides runtime protection for Kubernetes clusters with the following functionality:
- Restricting the behavior of containers at the system level
- Enforcing security policies on containers in runtime
- Produce container-aware audit logs
- Provide easy-to-use semantics for policy definitions
Oracle Container Engine for Kubernetes (OKE) is standard upstream-based managed Kubernetes service for running containerized applications at scale while reducing the time, cost, and operational burden of managing the complexities of Kubernetes infrastructure. This service enables you to quickly create, manage and consume Kubernetes clusters that leverage underlying compute, network, and storage services without the need to install and maintain complex supporting Kubernetes infrastructure.
Oracle Linux is a highly optimized and secure operating environment for application development and deployment that is supported in hybrid and multicloud environments. Oracle Linux is an ideal choice for users who need a stable Red Hat Enterprise Linux (RHEL)-compatible alternative. In addition to the Red Hat Compatible Kernel, Oracle Linux includes Unbreakable Enterprise Kernel (UEK). The focus of UEK is to provide superior performance, stability, and minimal backports by tracking the mainline source code as closely as possible.
KubeArmor, a cloud-native security solution, has added support for Oracle Kubernetes Engine (OKE) to secure pods and containers using Berkeley Packet Filter-Linux Security Module (BPF-LSM). This helps prevent attacks through inline mitigation. In a Kubernetes environment, pods are the units of execution and are often accessible to external entities, making it crucial to have a defense mechanism within the pods to limit the attacker’s ability to exploit vulnerabilities through system primitives. KubeArmor, being a Kubernetes-native solution, leverages Linux kernel primitives on Oracle’s Unbreakable Enterprise Linux (UEK) to harden the pods, strengthening the overall security of the Kubernetes engine.
KubeArmor leverages extended Berkley Packet Filter (eBPF) for observability of workloads and Linux Security Modules for security enforcement. This approach helps KubeArmor differentiate its solution by providing inline mitigation instead of post-attack mitigation. This inline mitigation is performed using policies which interact with the kernel to deny access (file system, execution, network access) to pods and containers. The image below shows the high-level architecture of this solution. You can learn more by reading the KubeArmor documentation.
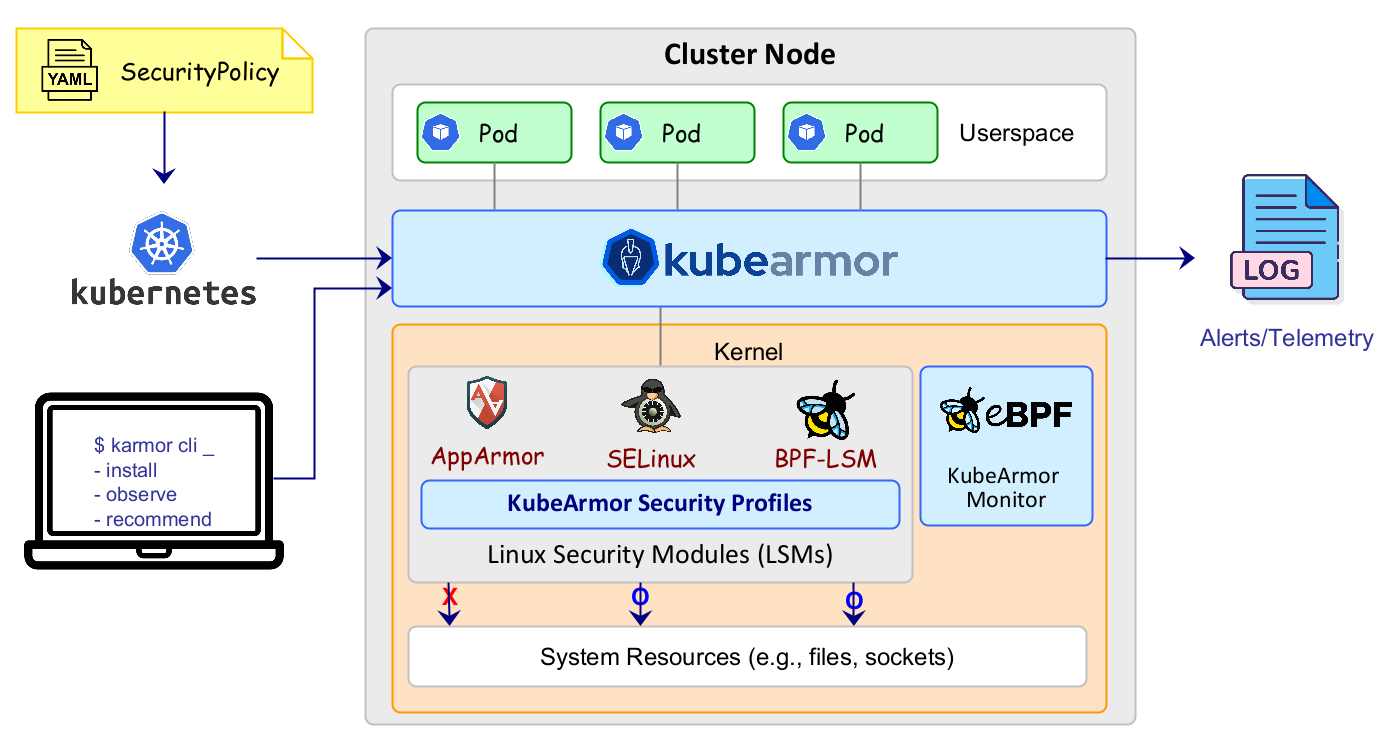
KubeArmor Architecture – image source
KubeArmor (with version 0.5) supports pod and container-based policy enforcement on OKE running with Oracle Linux nodes leveraging the BPF-LSM. BPF-LSM is a new LSM (Linux Security Modules) which was introduced in the newer kernels (version > 5.7). Unbreakable Enterprise Kernel Release 7 (UEK R7) is based on Linux kernel 5.15 LTS, which supports BPF-LSM, and is available for Oracle Linux 8 Update 5 onwards. UEK R7 can be installed on Oracle Linux 8.6 by following the easy-to-follow instructions provided in this blog.
Using KubeArmor with OKE (running Oracle Linux nodes), you can protect the Kubernetes pods and containers by restricting process execution, file access, and networking operations. To learn more, you can read this blog post from KubeArmor.
Signup for OCI Free Tier and spin up a OKE cluster to enhance the runtime security of your applications.
References and Additional Information:
