Welcome back! Today, let us have a look at Policies in Oracle Cloud Infrastructure Data Integration.
Introduction to Policies
A policy is a document that specifies who can access which Oracle Cloud Infrastructure (OCI) resources that your company has, and how. A policy allows a group or service to work in certain ways with specific types of resources in a particular compartment.
- Policies cannot be attached to users, only to groups
- Policies are comprised of one or more statements that specify what groups can access what resources and at what level of access
- Policies can be attached to a compartment or at the tenancy level i.e. root compartments
Policies come under Identity and Access Management (IAM), to understand more about Users, Groups, Compartments, and Policies refer to Overview of Oracle Cloud Infrastructure Identity and Access Management
Oracle Cloud Infrastructure Data Integration uses standard authentication and authorization offered by Oracle Cloud Infrastructure. Policies required for OCI Data Integration will be an addition to the regular policies used in Oracle Cloud Infrastructure for accessing other necessary resources.
Service Policies for Oracle Cloud Infrastructure Data Integration
The below table provides you with the policies required for the minimum execution of Oracle Cloud Infrastructure Data Integration. These policies need to be defined either at Tenancy or at Compartment level
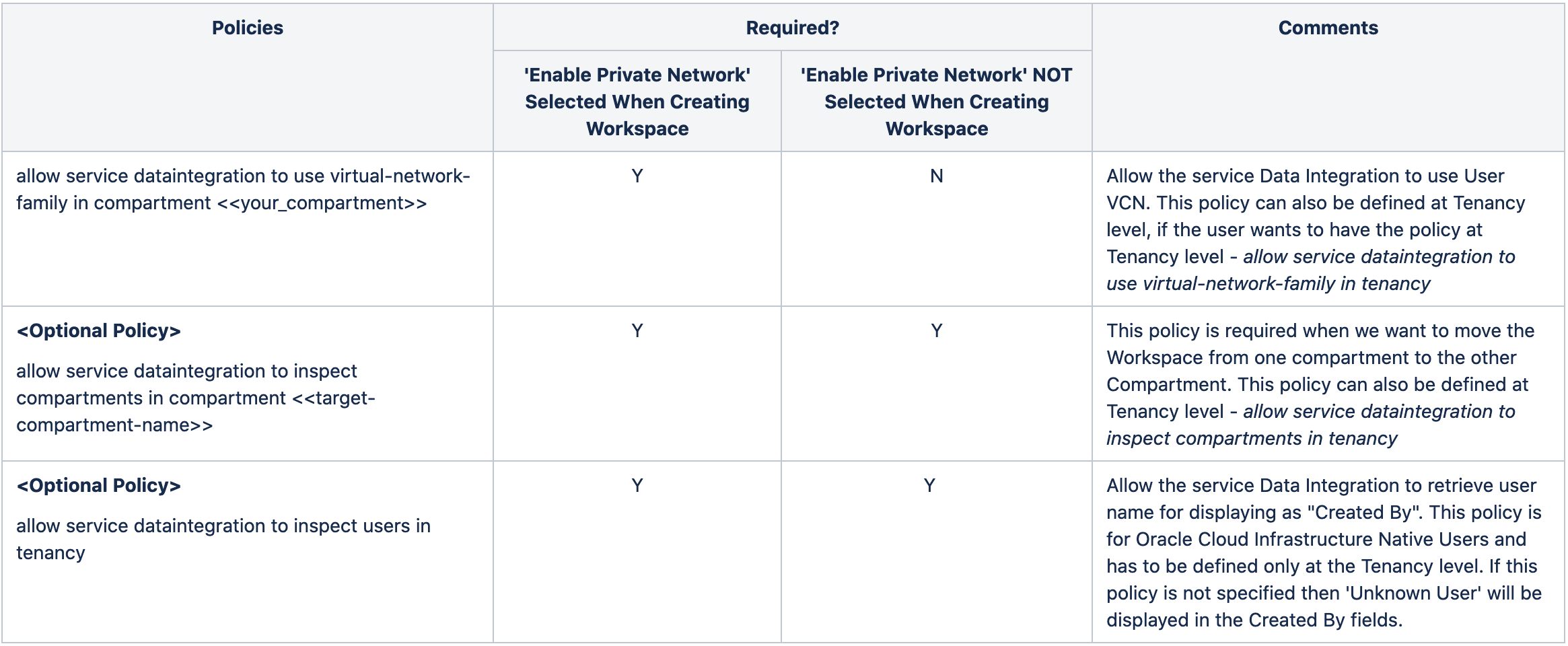
Policies required for user groups to Create Workspace
The following policies are required for the user groups using Oracle Cloud Infrastructure Data Integration depending on the following activities:
- To create/list Workspace –
- allow group <<group-name>> to manage dis-workspaces in compartment <<compartment-name>> (or)
- allow group <<group-name>> to manage dis-workspaces in tenancy
- To move Workspace –
- Require create/list Workspace policy and,
- allow group <<group-name>> to manage dis-workspaces in compartment <<target-compartment-name>>
- To check the status of Workspace while creating it –
- allow group <<group-name>> to manage dis-work-requests in compartment <<compartment-name>> (or)
- allow group <<group-name>> to manage dis-work-requests in tenancy
- To select VCN and regional subnets while creating Workspace –
- allow group <<group-name>> to use virtual-network-family in compartment <<compartment-name>> (or)
- allow group <<group-name>> to use virtual-network-family in tenancy
- Assign tag-namespaces to Workspace –
- allow group <<group-name>> to manage tag-namespaces in compartment <<compartment-name>> (or)
- allow group <<group-name>> to manage tag-namespaces in tenancy
Get the Workspace OCID –
To restrict the policies at the Workspace level, you would be requiring a Workspace OCID. To get the Workspace OCID of the corresponding Workspace in Oracle Cloud Infrastructure Data Integration, click on the Action menu “three dots” and click on “Copy OCID” to copy the Workspace OCID –

Policies to access Object Storage –
Two types of policies are required related to Object Storage, they are Resource Principal and On Behalf Of (OBO) Policy.
-
Resource Principal Policy – These policies need to be defined either at the Tenancy/Compartment level and use the subject as any-user. These policies help Oracle Cloud Infrastructure Data Integration to create/execute a Data Flow or Task and validate/test the Data Assets related to Object Storage.
Note – To use “any-user” in the policy for Oracle Cloud Infrastructure Data Integration, the “WHERE” clause should always be provided. -
On Behalf Of (OBO) Policy – These policies allow the logged-in user to perform Oracle Cloud Infrastructure Data Integration functionalities based on the permissions given to the user already.
Section 1 – Policies to access Object Storage from Oracle Cloud Infrastructure Data Integration in same Tenancy
In this section, we have mentioned policies that are required for accessing Object Storage. These policies are also used when using Autonomous Databases (ADW/ATP) as a target since Object Storage will be used as a staging area.
-
- Admin has to define the following Policy at Tenancy level – allow group <<group_name>> to inspect compartments in tenancy
Along with the above policy, The following are the options that can be referred based on the access level of the user.
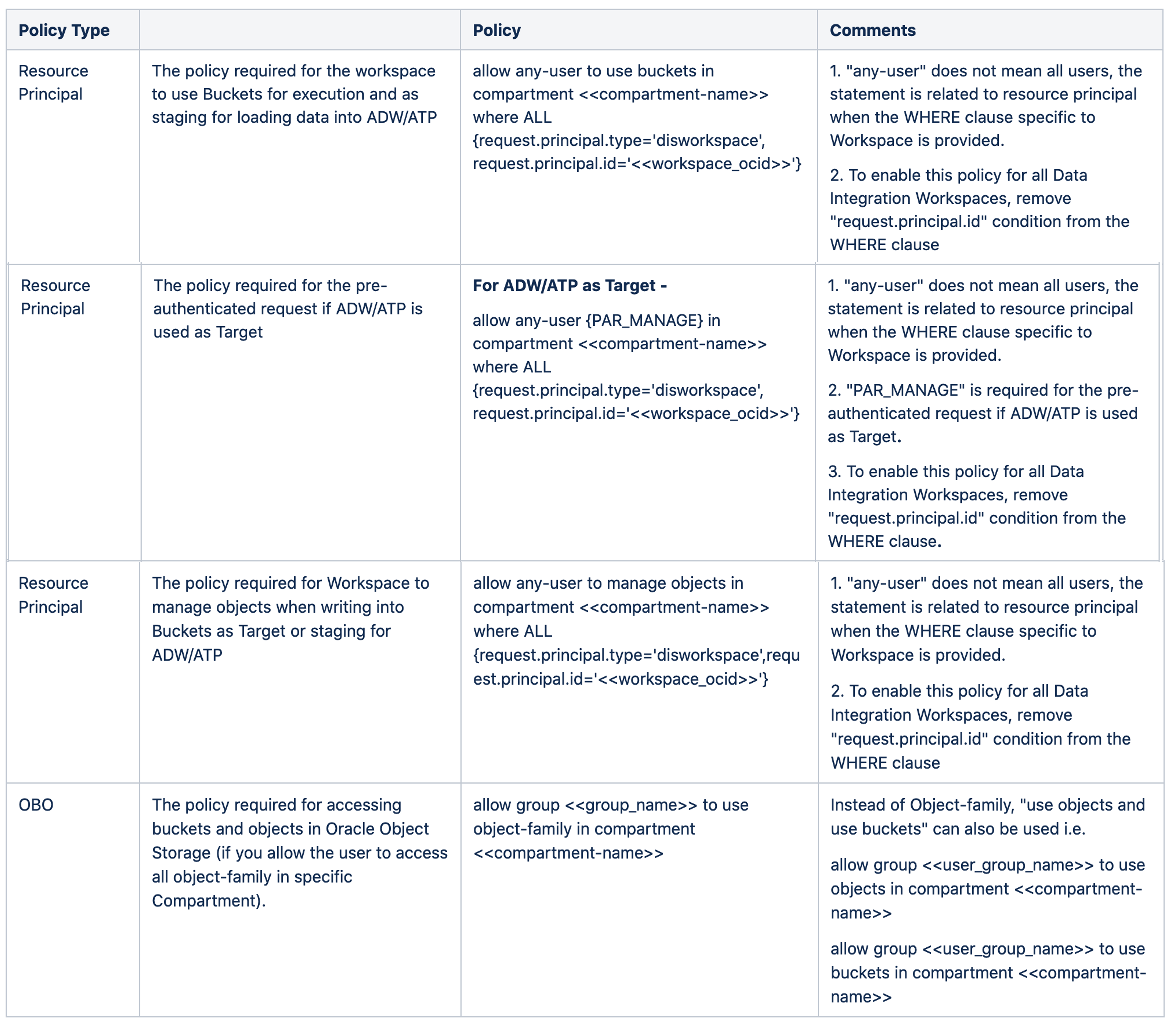
Option 1 – Compartment Level Policies (Recommended)
The below table can be referred to in order to restrict Oracle Cloud Infrastructure Data Integration access at the Compartment level. All the policies mentioned below are required for the minimal access of Object Storage from Oracle Cloud Infrastructure Data Integration. Policies can be created using any-user.
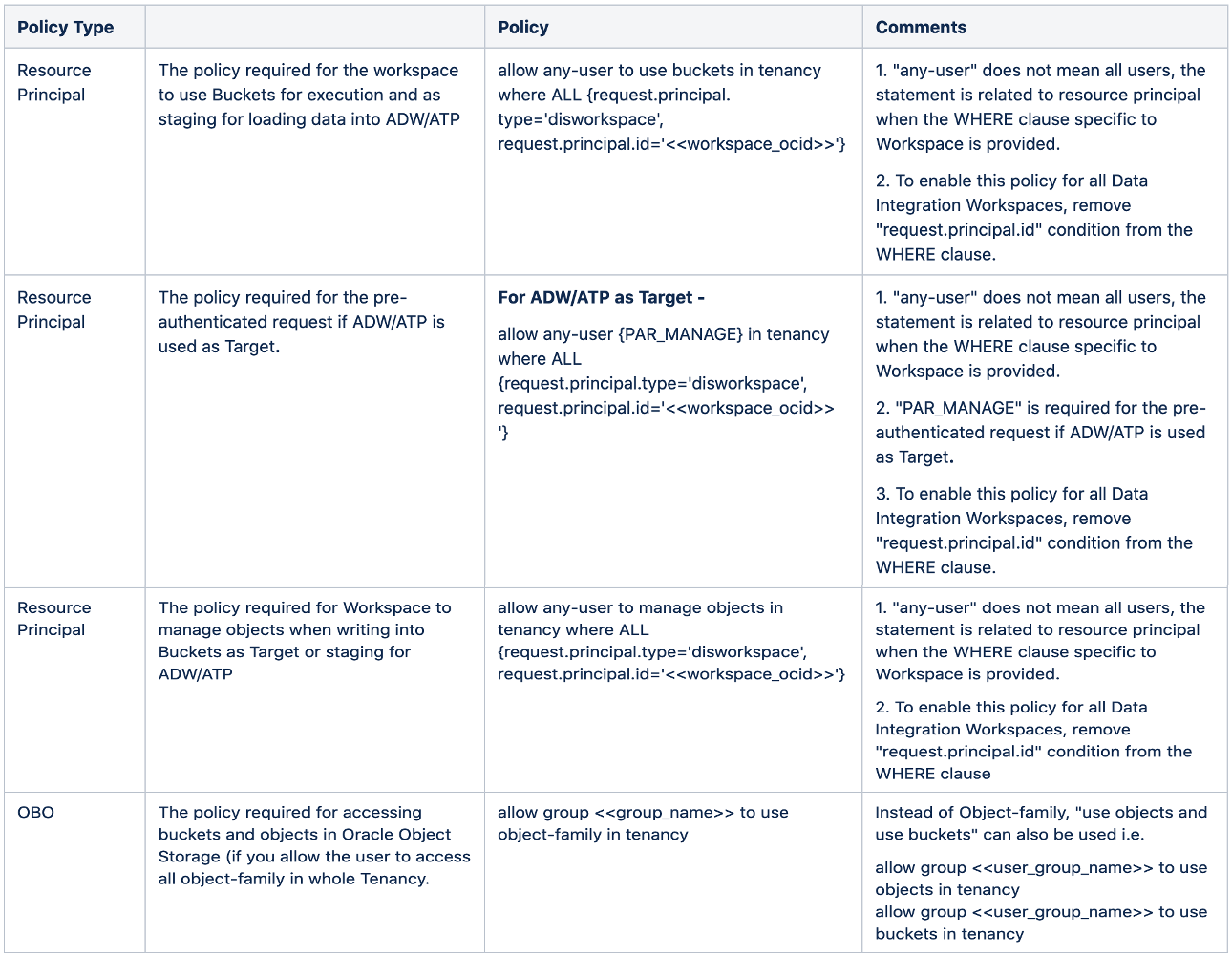
Option 2 – Tenancy Level Policies
The below table can be referred to in order to restrict Oracle Cloud Infrastructure Data Integration access at the Tenancy level. All the policies mentioned below are required for the minimal access of Object Storage from Oracle Cloud Infrastructure Data Integration. Policies can be created using any-user.
Option 3 – Tenancy level, Full Access to Oracle Cloud Infrastructure Data Integration, and user group
If the user wants to provide full access to Oracle Cloud Infrastructure Data Integration without any restrictions, then simple policy statements to access Object Storage can be used –
- allow any-user to manage object-family in tenancy where ALL {request.principal.type=’disworkspace’ }
- allow group <<group-name>> to manage object-family in tenancy
(OR) - allow any-user to manage object-family in compartment <<compartment-name>> where ALL {request.principal.type=’disworkspace’ }
- allow group <<group-name>> to manage object-family in compartment <<compartment-name>>
Section 2 (Advanced) – Policies to access cross-tenancy Object Storage from Oracle Cloud Infrastructure Data Integration
In this section, we have mentioned policies that are required for accessing cross-tenancy Object Storage where your Object Storage and Data Integration Workspace are located in different tenancies.
- Policy in the Workspace tenancy:
On Behalf of (OBO) Policy –
Define tenancy <<name>> as <<Object_Storage_Tenancy_OCID>>
Endorse group <<group_name>> to inspect compartments in tenancy <<name>>
Endorse group <<group_name>> to use object-family in tenancy <<name>>
Resource Principal Policy –
Endorse any-user to use buckets in tenancy <<name>> where ALL {request.principal.type=’disworkspace’,request.principal.id = ‘<<workspace_ocid>>‘}
Endorse any-user to manage objects in tenancy <<name>> where ALL {request.principal.type=’disworkspace’,request.principal.id = ‘<<workspace_ocid>>’}
Endorse any-user {PAR_MANAGE} in tenancy <<name>>where ALL {request.principal.type = ‘disworkspace’,request.principal.id = ‘<<workspace_ocid>>’}
- Policy in the Object Storage tenancy:
On Behalf of (OBO) Policy –
Define tenancy <<name>> as <Workspace_Tenancy_OCID>
Define group <<group_name>> as <<group_OCID>>
Admit group <<group_name>> of tenancy <<name>> to inspect compartments in tenancy
Admit group <<group_name>> of tenancy <<name>> to use object-family in compartment <<compartment-name>>
Resource Principal Policy –
Admit any-user of tenancy <<name>> to use buckets in compartment <<compartment-name>> where ALL {request.principal.type=’disworkspace’, request.principal.id=’<<workspace_ocid>>‘}
Admit any-user of tenancy <<name>> to manage objects in compartment <<compartment-name>> where ALL {request.principal.type=’disworkspace’, request.principal.id=’<<workspace_ocid>>‘}
Admit any-user of tenancy <<name>> {PAR_MANAGE} in compartment <<compartment-name>> where ALL {request.principal.type = ‘disworkspace’,request.principal.id = ‘<<workspace_ocid>>‘}
(OR)
Admit any-user of tenancy <<name>> to use buckets in tenancy where ALL {request.principal.type=’disworkspace’, request.principal.id=’<<workspace_ocid>>‘}
Admit any-user of tenancy <<name>> to manage objects in tenancy where ALL {request.principal.type=’disworkspace’, request.principal.id=’<<workspace_ocid>>‘}
Admit any-user of tenancy <<name>> {PAR_MANAGE} in tenancy where ALL {request.principal.type = ‘disworkspace’,request.principal.id = ‘<<workspace_ocid>>‘}
For more detailed information on Oracle Cloud Infrastructure Data Integration Policies, refer to – Data Integration Policies. In the next blog, we are going to discuss more use-cases related to policies for Oracle Cloud Infrastructure Data Integration. We hope you are finding these blogs helpful! Let us know what you think. More Oracle Cloud Infrastructure Data Integration blogs here.
For more details on Oracle Cloud Infrastructure Data Integration, check out the Tutorials and Documentation as well.
