One of the most interesting new capabilities in Oracle Database 23ai is SQL Firewall, and we’re happy to introduce a new Oracle LiveLabs workshop to help you come up to speed quickly on this exciting new feature.
SQL Firewall can help customers mitigate common database risks like SQL injection attacks and compromised accounts. It helps ensure that only authorized SQL statements from trusted database connections are permitted for processing inside the Oracle database, while blocking and logging unauthorized SQL or database connections.
Oracle Data Safe helps you train and manage the SQL Firewall. Data Safe automatically collects SQL Firewall violation logs and lets you analyze and report on violations. Data Safe enables you to manage your database’s SQL Firewalls centrally and provides a comprehensive view of SQL Firewall violations across your fleet of Oracle databases.
Key benefits of SQL Firewall
SQL firewall provides the following benefits:
- Gives real-time protection against SQL injection attacks by allowing only approved SQL statements from trusted database connections for the database user.
- Mitigates the risk of credential theft by enforcing trusted database connection paths.
The new LiveLabs workshop for SQL Firewall gives you hands-on experience in training and managing SQL Firewall in Data Safe. With this new workshop, get started with SQL Firewall in Data Safe with only a few steps!
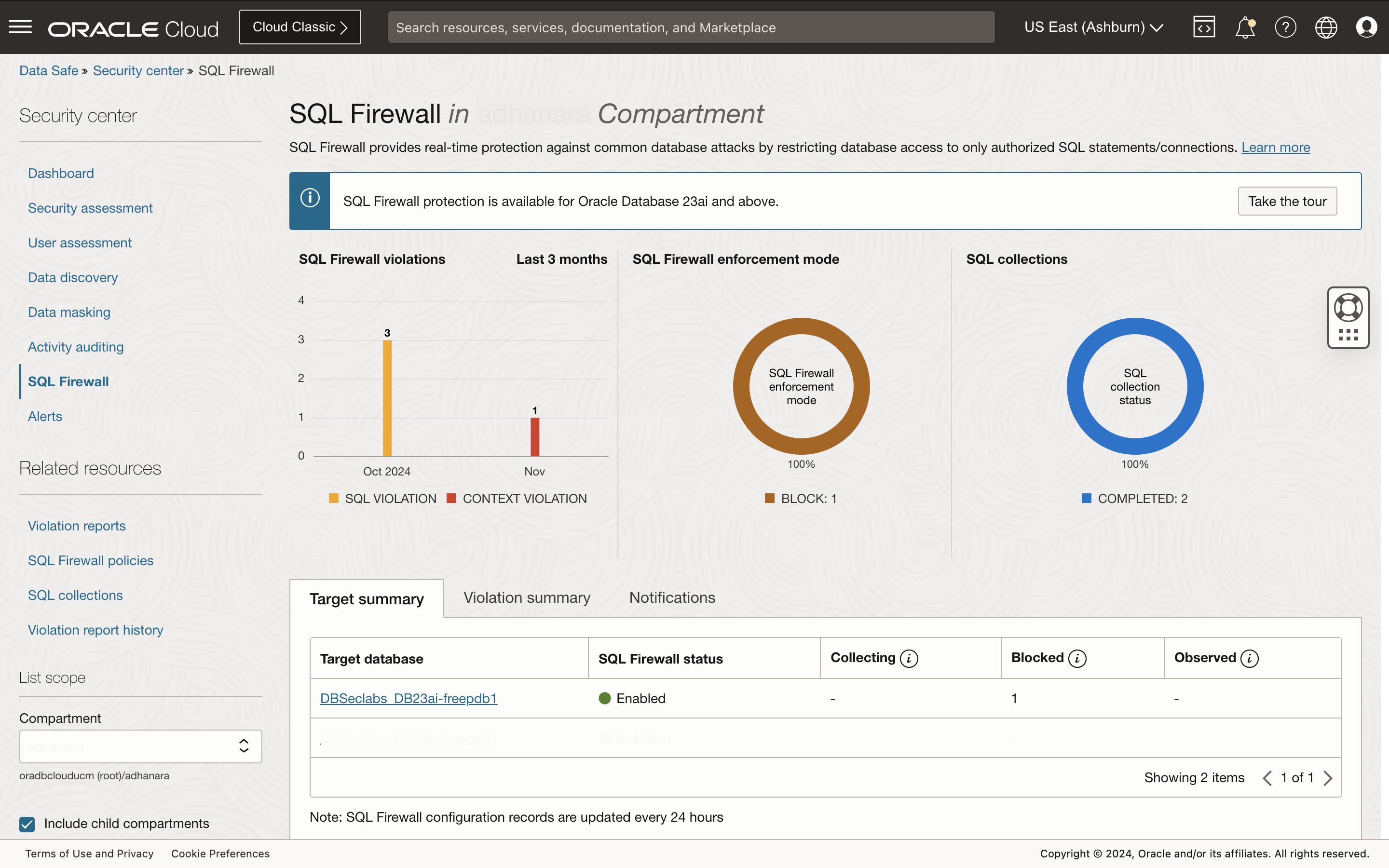
Step 1: Ensure SQL Firewall is enabled for the target database in the SQL Firewall dashboard
In the database target, view the configuration details and enable SQL Firewall, if needed. The dashboard provides a comprehensive view of SQL Firewall violations and configurations across all targets with SQL Firewall enabled.
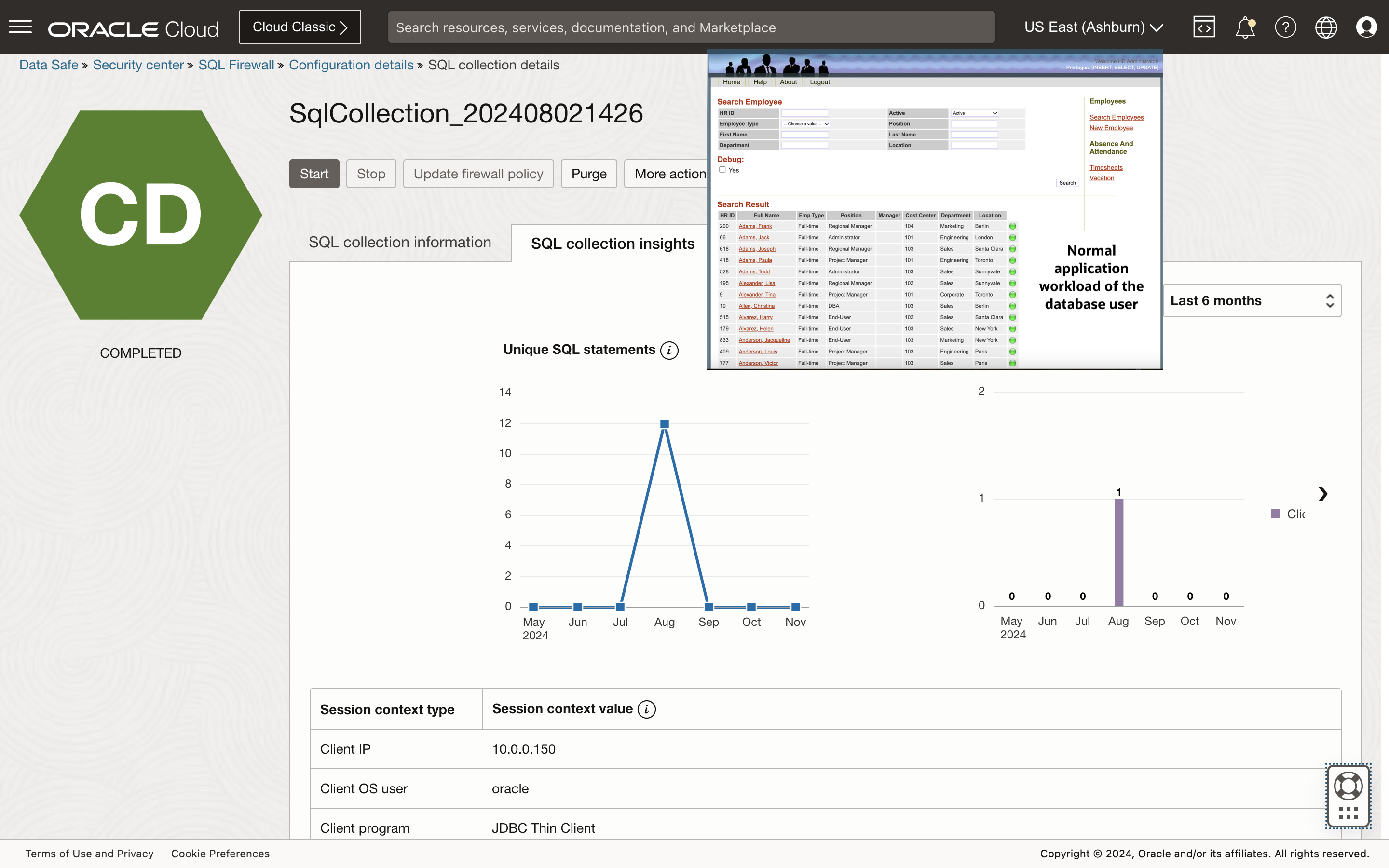
Step 2: Create a SQL collection to capture normal activity for a database user
As the database user runs the typical application workload from trusted database connection paths, Data Safe lets you monitor the progress of SQL collection with insights. Stop the collection when you see new activity drop to zero and generate a firewall policy with allowlists.
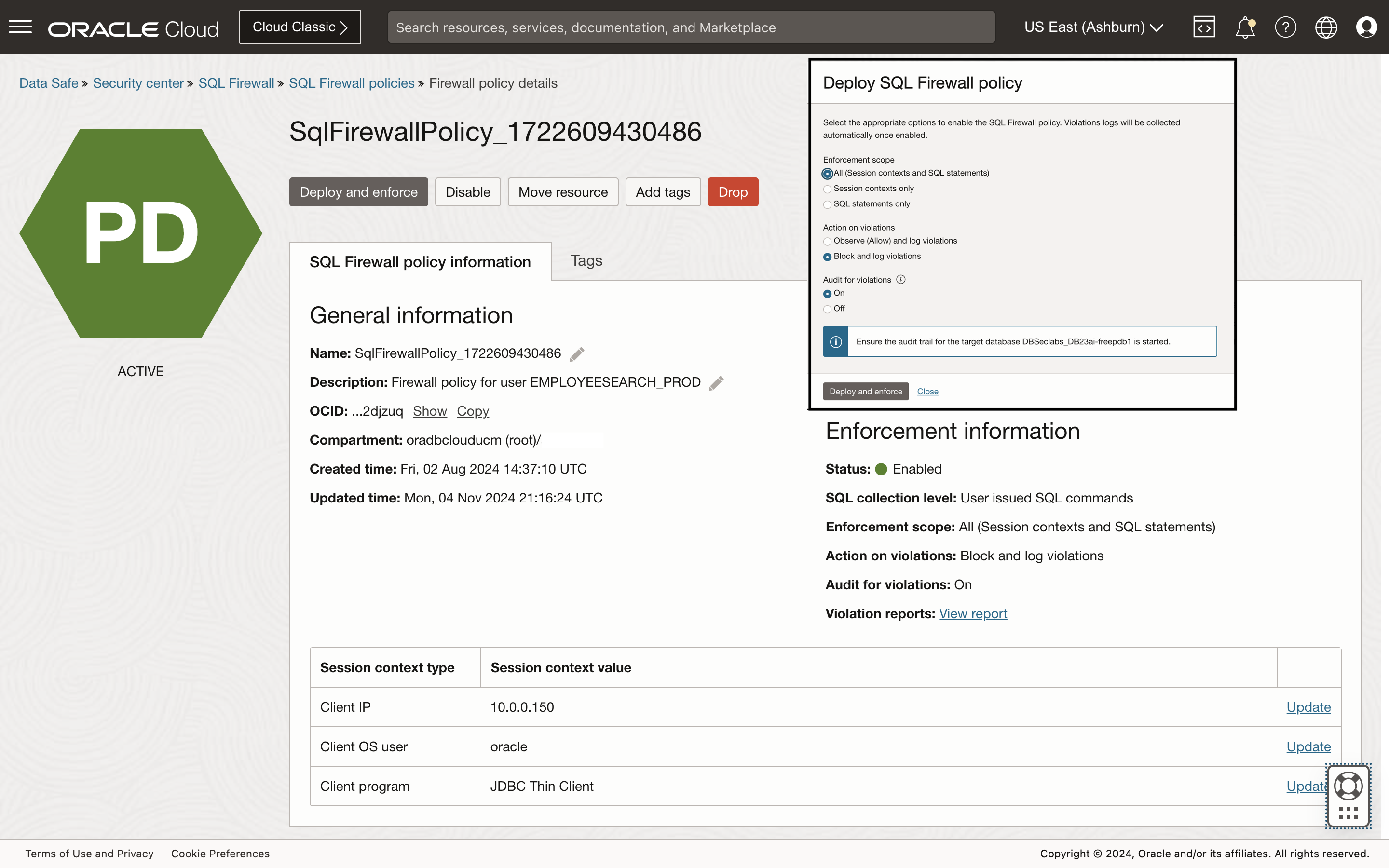
Step 3: Deploy and enforce the SQL Firewall policy based on the SQL collection
When the user connects to the database and issues SQL statements, SQL Firewall enforces checks on the policy’s allowlists.
With those simple steps, you’re ready to go!
If the database connection paths or SQL statements in the incoming SQL traffic don’t match the entries in the firewall policy allowlists for the user, a SQL Firewall violation is triggered and logged in the violation log. Data Safe automatically collects violations from the target database and makes them available in the Data Safe console for online analysis and reporting across your database fleet.
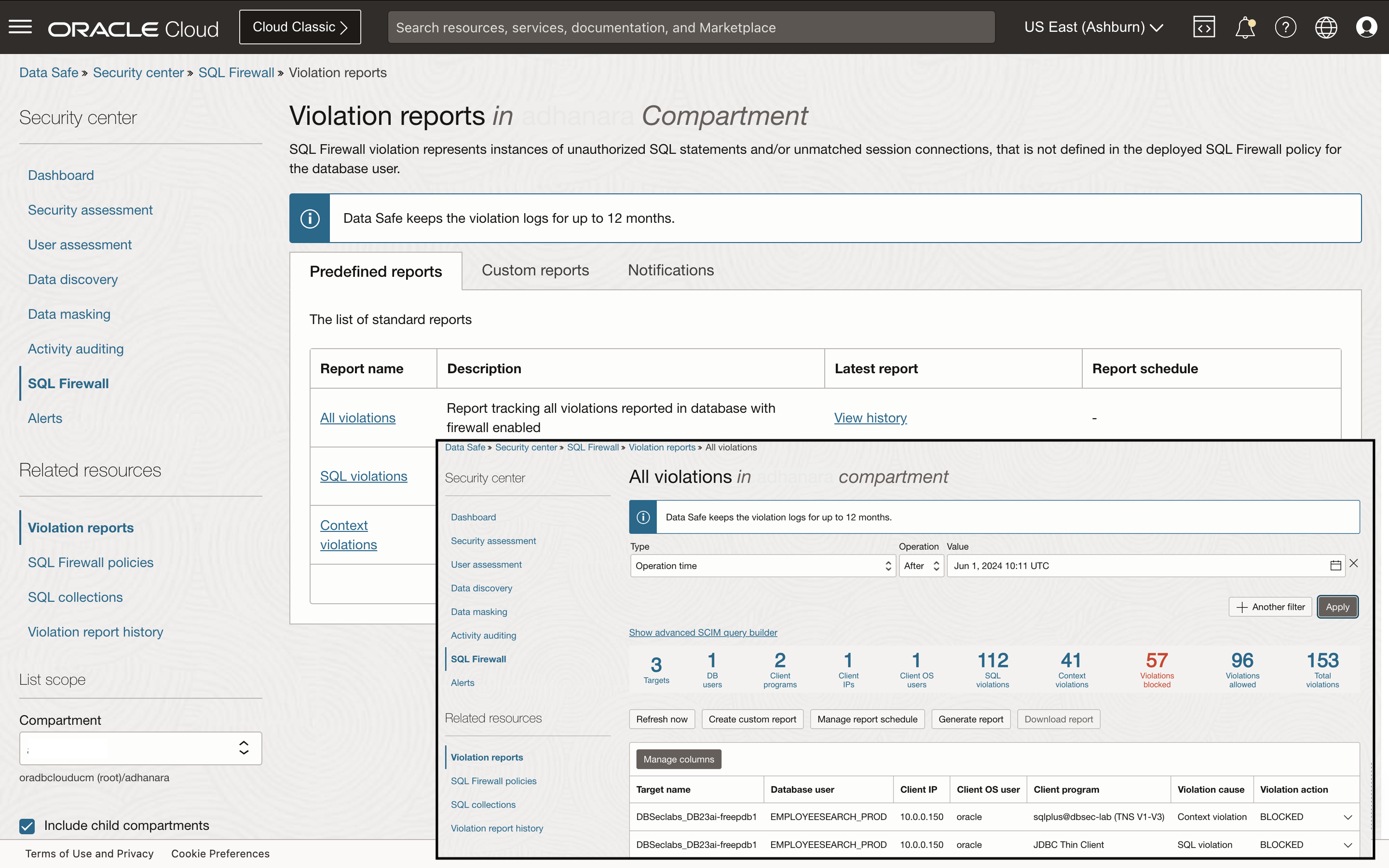
The Livelabs workshop demonstrates two practical scenarios of how SQL Firewall mitigates the risk of stolen credentials and SQL Injection attempts.
Get started today
Check out the new LiveLabs workshop for SQL Firewall to get started with SQL Firewall in Data Safe. To see SQL Firewall in action when it’s configured, refer to the video, Introducing SQL Firewall – a new security capability in Oracle Database 23ai.
To learn more, see the following resources:
- Announcement blog post on SQL Firewall in Oracle Database 23ai
- SQL Firewall in Data Safe User Guide
- SQL Firewall documentation guide
- Technical report on mitigating risks of SQL Injection
