ZPR Release Announcement: Advancing Zero-Trust Security in OCI
Organizations running critical applications on Oracle Cloud Infrastructure (OCI) must safeguard the most sensitive data—customer records, financial transactions, or healthcare data stored in Oracle Database. These organizations face the constant challenge of preventing unauthorized access and protecting critical data. Their mission is clear: ensure data remains secure against any attempt to gain access. This is the challenge that keeps CISOs awake at night.
Here’s where Zero Trust Packet Routing (ZPR) comes in. Launched last year in collaboration with Applied Invention, ZPR provides a simple, human-readable way to define and enforce robust trust boundaries. Unlike complex, error-prone IP rules, ZPR lets you control which workloads can communicate, where data flows, and what services are reachable—all while default-denying everything else. In short, ZPR turns network intent into enforceable zero-trust controls that help keep your most critical workloads safe.
With this latest release, ZPR is part of Oracle Acceleron, supporting for complex enterprise workloads by enabling multi-VCN deployments, expanding coverage for services such as MySQL and Oracle Functions, improving visibility through Network Path Analyzer (NPA), and integrating seamlessly with Private Service Access (PSA) and IAM Deny Policies. These updates help prevent lateral movement across networks, block data exfiltration, and mitigate risks from compromised credentials. Together, they provide organizations with a cohesive zero-trust framework that is designed to secure critical workloads, simplify management, and support compliance in complex environments.
Building Stronger Barriers Against Lateral Movement
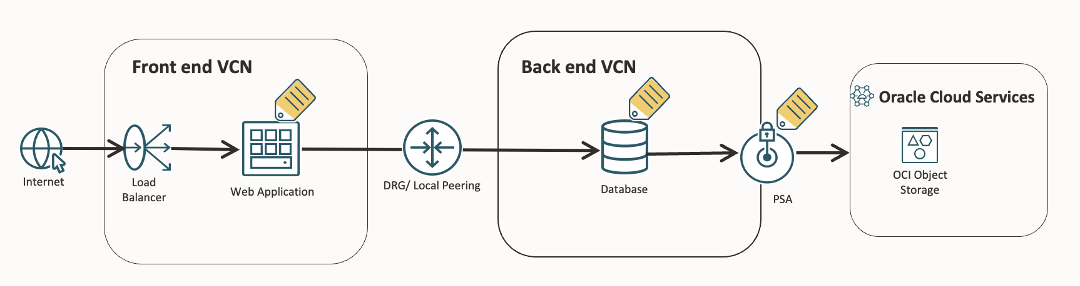
For modern cloud deployments, workloads often span multiple Virtual Cloud Networks (VCNs). While this architecture strengthens isolation, it adds operational complexity- making it challenging to consistently enforce security across environment.
ZPR’s cross-VCN policies unify security across these VCNs, surpassing traditional network security groups or routing tables. With a single, human-readable policy, you can enforce clear trust boundaries across tiers: front-end servers exposed to the internet may talk only to mid-tier services over secure protocols like HTTPS, while mid-tier services alone can reach the back-end databases holding sensitive customer data.
If an attacker compromises a front-end node, ZPR prevents them from bypassing these boundaries. They cannot move laterally across tiers or traverse multi-VCN environments to reach the database, effectively stopping lateral movement before it threatens critical systems.
This unified approach not only strengthens zero-trust enforcement but also simplifies policy management. Instead of juggling separate rules for each VCN or tier, a single policy governs your entire application architecture, reducing complexity and enforcing compliance with security rules. By closing security gaps across distributed workloads, ZPR helps keep your environment secure and your operations efficient.
Closing the Door on Data Exfiltration
You also want to make sure that if an attacker gets into your network, they can’t exfiltrate data—especially the sensitive customer information, transaction records, or regulatory reports that entities like financial institutions must protect.
To these customers, this means database backups, account statements, or compliance reports are always restricted to private, authorized paths. ZPR, paired with Private Service Access (PSA), helps ensure sensitive data, like reports in Object Storage or database backups, never touches the public internet. PSA routes traffic to OCI services such as Object Storage or Functions privately, while ZPR’s attribute-based policies allow only trusted workloads to connect.
Even if an attacker infiltrates your network, they can’t exfiltrate data to external tenancies, as ZPR and PSA enforce private, authorized paths only. This seamless integration delivers robust protection without operational overhead. By keeping data flows within your trust boundaries, ZPR and PSA safeguard sensitive information and maintain security compliance, so that your security strategy scales as effortlessly as your cloud environment.
Neutralizing the Risk of Stolen Credentials
Even with strong protections against lateral movement and data exfiltration, attackers often try the simplest route: compromised credentials. Phishing, leaked passwords, or insider misuse could hand over valid logins to the wrong person. To our example customer, this could mean someone gaining access to a workload that handles payments or stores sensitive account data.
IAM Deny Policies act as an additional layer of defense. They enforce tenancy-level guardrails that block access from untrusted paths—even if credentials are valid. For instance, you can deny public endpoint access to Object Storage buckets or critical workloads, which helps ensure that sensitive data is only reachable via private service access. This means that for our financial institution, customer records, payment systems, and compliance databases remain protected, even if credentials are compromised.
Securing More of Your Cloud Footprint
Part of modernizing your workloads means being able to use the whole stack of cloud offerings – without compromising security. As your OCI environment grows with diverse services like MySQL for transaction databases and Oracle Functions for real-time analytics, ZPR extends its attribute-based security to these critical services, offering consistent zero-trust enforcement across your expanding cloud footprint.
This expanded coverage helps you make safe your entire cloud footprint in a world where security is paramount, tying directly to the zero-trust foundation established by cross-VCN policies and PSA. Your financial institution can protect its environment—whether compute, databases, or serverless functions—with the same rigorous standards, all while keeping management simple and scalable.
Seeing Clearly with Network Path Analyzer
A zero-trust architecture is only as strong as your ability to validate it. ZPR’s integration with Network Path Analyzer (NPA) provides clear insights into traffic paths, making it easy to confirm policies or troubleshoot blocked connections. If legitimate traffic is stopped, NPA pinpoints the issue without compromising security, keeping your trust boundaries intact. This visibility complements ZPR’s robust controls, enabling you to maintain a secure, efficient environment with confidence.
Delivering Zero-Trust Security with Confidence
With these enhancements, ZPR keeps workloads and data protected by design. Cross-VCN trust boundaries, PSA private paths, and tenancy-wide guardrails with IAM Deny Policies provide layered, enforceable control. Expanded service coverage and Network Path Analyzer visibility make it simple to manage and validate policies, giving you clarity, control, and peace of mind.
This release transforms your OCI environment into a resilient, zero-trust cloud, containing risk at every layer while letting your teams focus on innovation rather than firefighting.
Learn more: oracle.com/cloud/networking/zero-trust-packet-routing
