In 2021, we have seen a dramatic shift in the way we enable our employees to do their job. More flexibility in work locations, when we work, and how we use technology. With this increase in remote working, we have seen our risk profile change from that of employees residing behind hardened network environments utilizing highly tuned security controls across the layers to analyze, prevent, detect, and respond. What are these same employees to do when their primary security control suddenly becomes the router provided by their residential Internet Service Provider (ISP)? Suddenly a higher degree of security awareness and due diligence has been placed on the employees at a time when organizations are aware of increases in phishing attacks against highly desirable account owners. Attackers have taken advantage of the relaxed rules business gave their employees to work from personal devices and computers, on less secure network connections, all to help fulfill the urgent needs of the business while giving employees choice in how they work. This leaves individuals and their organizations at risk. Phishing attacks, specifically spear phishing attacks, are on the rise and any organization could be at risk.
October is Cybersecurity Awareness month, a time for us to stop and think about some of the risks we are facing personally and within our organizations. As technology advances, many of the old phishing schemes attackers used are no longer effective. Attackers have pivoted to the well-crafted spear phishing method. Instead of a blanketing victims with a generic email, attackers spend time researching their targets to craft highly tailored messages. Unfortunately, most of the information they need is readily available and provided by their victims openly online. So, what are some of the ways people fall for these tailored attacks, why do they matter for your organization, and what can you do to stop them?
Why is spear phishing so effective?
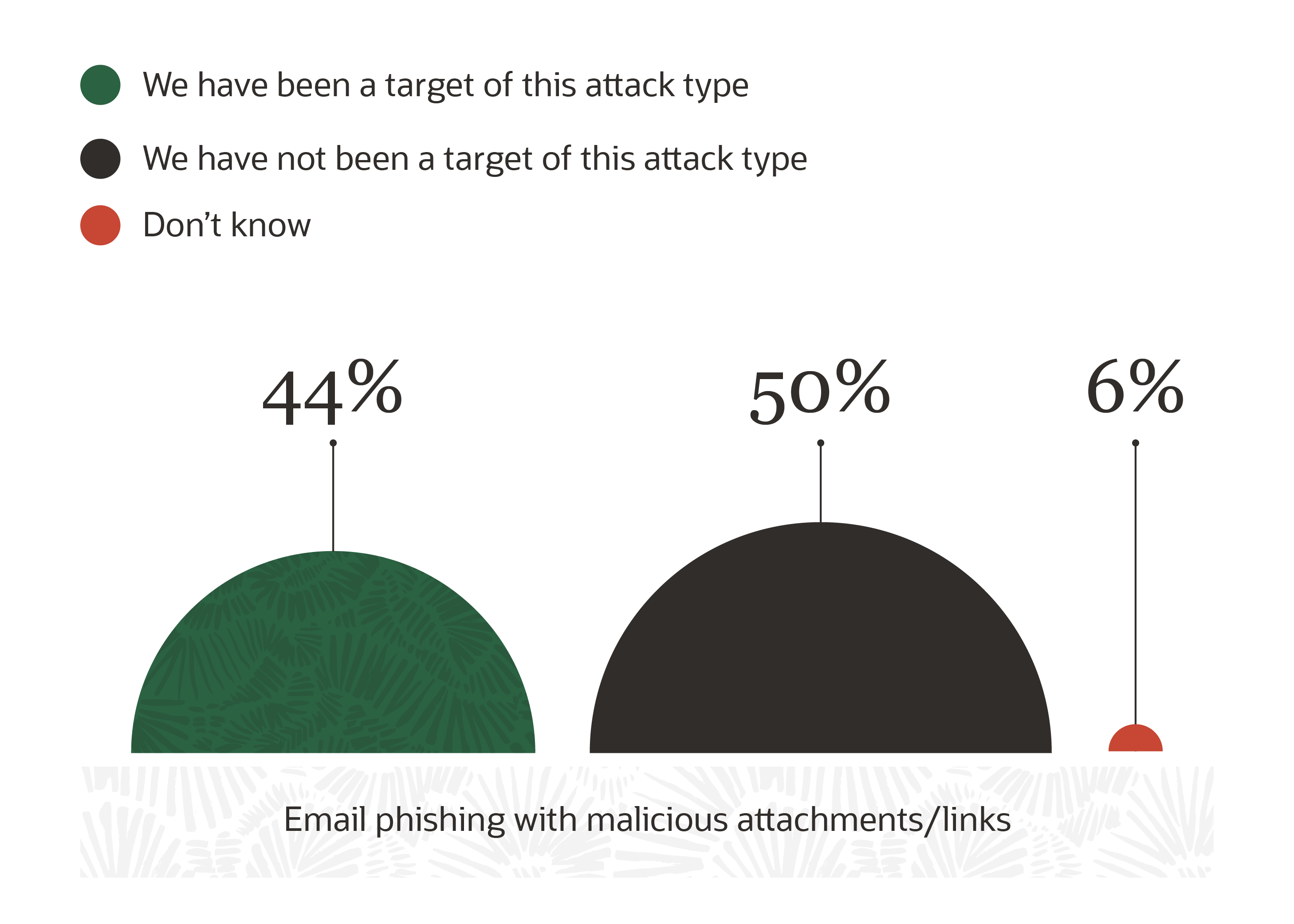
According to the Oracle and KPMG Cloud Threat Report, 44% of organizations surveyed have been the target of an email phishing attack in the last 24 months.
- Authority – Attackers often target high level executives or members of an organization with privileged account access. 59% of participants in the Oracle and KPMG Cloud Threat Report also reported members of their organization with privileged cloud accounts were compromised by targeted phishing attacks, known as spear phishing. By successfully impersonating a privileged user, attackers have access to more information and a network of employees to send requests to further the reach of the attack. Through social network platforms like LinkedIn, attackers can find out who you work with and craft an email based on the types of subjects your role would normally react to. It’s highly tempting for employees to respond to a senior executive’s request asking them to update a time sheet, or a project status by clicking on a link. This is what makes phishing so successful. The masquerading as a legitimate employee plays on our human vulnerabilities.
- Haste makes waste – We are all busy; working, balancing family and friends, calling a plumber to fix a leaky faucet. Our minds are full and the last thing we are thinking about is the validity of a request to transfer funds from our CFO. Many of these attacks are successful because the vast majority of our email is viewed on a smartphone which provides less up-front information on the sender, making it easier to fool the victim.
- Creating a sense of urgency – Attackers push the victim to complete the request faster, they don’t always notice the small discrepancies, like a fake login page for their CRM system setup by the attacker to capture credentials. Attackers go after our natural reactions and send notes threatening to cut off access to critical applications if the person doesn’t login and complete an action within the next few hours.
These challenges have been amplified by the pandemic as we no longer work next to others in the office who might have also received the strange email request.
What are some actions we can take to protect our organizations and ourselves?
- Improve employee training and processes – This is especially important with increased remote workers a need to operate securely. Here is a list of CISA Cybersecurity resources.
- Adopt a security-first mindset – This change comes from the top, as leaders must commit to focus on security across every aspect of the business. This includes centralizing identity siloes, managing down shadow IT, and making processes user friendly and secure. Learn how CISOs can impact change within their organizations.
- Select a security-first cloud provider – Protect your most valuable data in the cloud and on-premises with Oracle’s security-first approach. Oracle has decades of experience securing data and applications; Oracle Cloud Infrastructure delivers a more secure cloud to our customers, building trust and protecting their most valuable data. Learn more about Oracle Security, Oracle Cloud Infrastructure Security, and Oracle Database Security.
- Take a modern identity and access management approach – As more flexible work environments have emerged, the need for organizations to focus on securing the human perimeter is key to a modern and secure organization. Implementing multifactor authentication, effectively managing entitlements, and improving the ability to detect anomalous behavior, all help build defenses around your data and applications. Learn more about how Oracle Identity and Access Management can help secure your organization.
- Enforce strong identity governance – Ensure people within the organization only have access to the data that is necessary to complete their work tasks and follow the principle of least privilege. Completing certifications on an ongoing basis to keep unnecessary entitlements from accumulating throughout the organization. Read the KuppingerCole Leadership Compass for Identity Governance and Administration.
Spear phishing and other methods of cyberattacks aren’t going away and every organization is at risk of a breach of their valuable data. This month is a great time to start conversations within our organizations about putting security-first and following best practices to protect our most valuable assets. Visit these pages to help get the conversation started: Cybersecurity Awareness Month, Oracle and KPMG Cloud Threat Report, Oracle Security.