This blog is part 1 of our multipart series on the Oracle Cloud Native SCCA Landing Zone solution.
U.S. Department of Defense (DoD) customers who deploy workloads to the cloud must follow the Cloud Computing Requirements Guide (CC SRG) and build an architecture that’s compliant with the Secure Cloud Computing Architecture (SCCA) Functional Requirements Document (FRD) established by the Defense Information Systems Agency (DISA). These documents define the application and security standards to deploy DoD workloads connected to DoD Non-classified Internet Protocol Router Network (NIPRNet) and Secret Internet Protocol Router Network (SIPRNet).
In this blog series, we examine the critical aspects of building an SCCA-compliant architecture. Let’s start by looking at the SCCA framework and how the Oracle Cloud Native SCCA Landing Zone solution helps DoD customers build secure and compliant architectures.
SCCA compliance is required to protect DoD networks inside the Department of Defense Information Network (DODIN), from systems hosted on a public cloud. Figure 1 shows the following main components of SCCA:
- The Virtual Data Center Security Stack (VDSS) contains the security tooling and configurations such as entry and exit security, routing, and firewall rules.
- The Virtual Datacenter Management Stack (VDMS) contains management tooling and configurations, such as backup, patching, and monitoring.
- Boundary Cloud Access Points (BCAPs) are connectivity points for all DoD traffic.
- A Trusted Cloud Credential Manager (TCCM) is a person or role that owns and maintains the cloud credential management plan.
These SCCA components and controls are verified by a DoD Authorizing Official (AO) and DISA cyber personnel before issuing an interim authorization to test (IATT) or authority to pperate (ATO). Mission owners may migrate their workloads to the cloud once IATT is complete and ATO is granted.
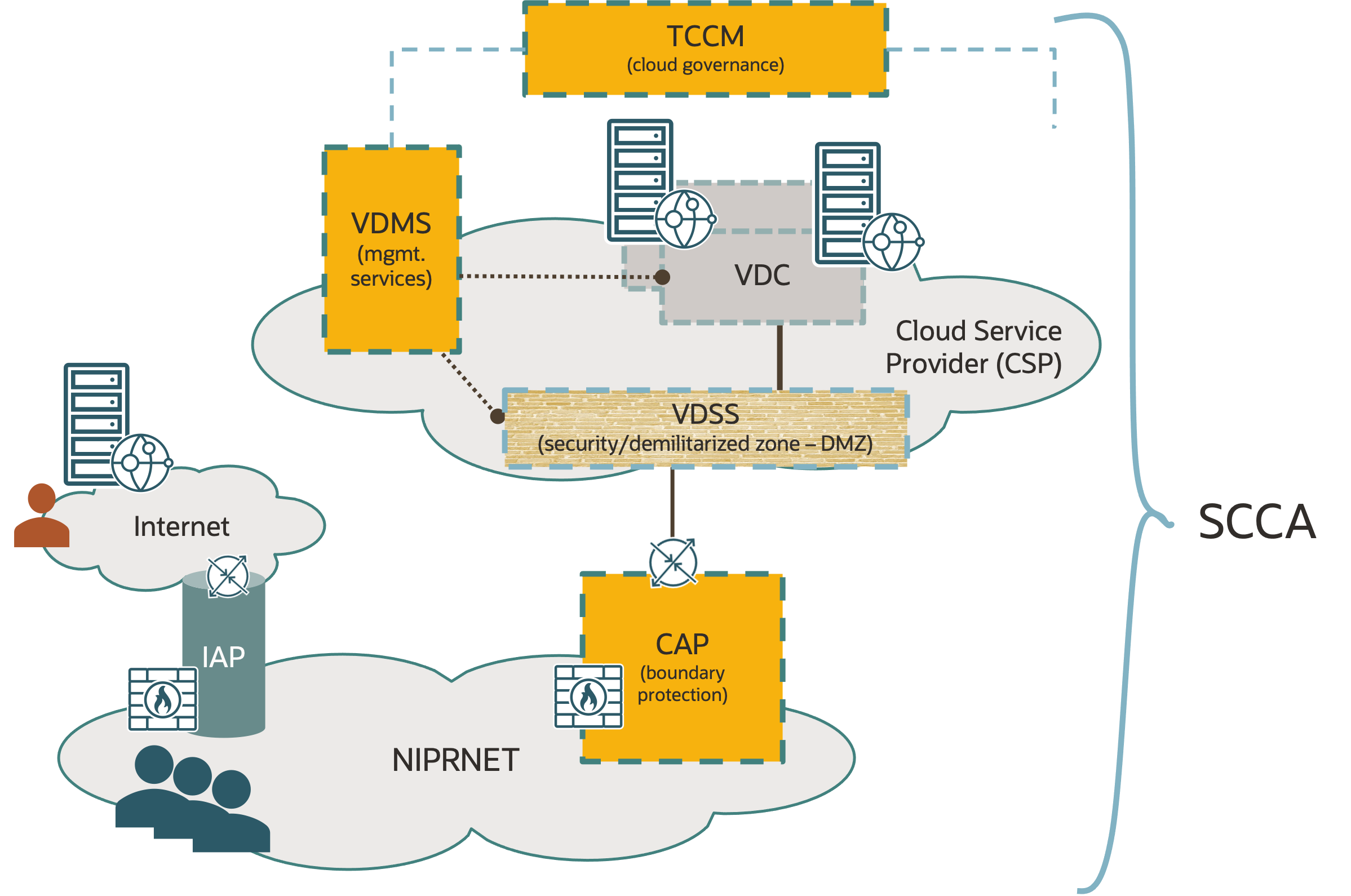
Figure 1: The four components of SCCA
Common challenges when meeting SCCA requirements
DoD mission owners have struggled to meet SCCA requirements in order to migrate to the cloud and modernize their workloads. DoD mission owners and their assigned systems integrators have invested significant time and money to build custom SCCA implementations. These custom implementations often require third-party software, which further increases the total cost to maintain SCCA compliance. Multiple DoD customers have asked us for an SCCA solution that is less labor-intensive and more cost-effective.
Onboard DoD workloads faster with consistent deployments each time
The Oracle Cloud Native SCCA Landing Zone automates the process of building a SCCA-compliant architecture using Terraform scripts to make it easy to build and deploy your DoD IL4 and IL5 workloads. The landing zone includes baseline configurations, rules, and templates delivered using an infrastructure-as-code (IaC) template. Customers can launch the templates from the Oracle Cloud Native SCCA Landing Zone, answer a few simple questions about their configuration, and have an architecture set up that same day. The landing zone configures identity domains, virtual cloud networks (VCNs), network firewalls, load balancers, vulnerability scanning, and more. Customers can find the landing zone via GitHub or in the Oracle Cloud Console.
Oracle helps customers satisfy and document required controls. We built our Cloud Native SCCA Landing Zone with integrated cloud native platform services to meet the SCCA controls that are the responsibility of the cloud service provider (CSP). We also provide tools, services, and guidance to meet the additional SCCA controls that are your responsibility as a DoD mission owner.
The DISA FRD has controls that can be logically distributed in different control areas as depicted in Figure 2. The Oracle Cloud Native SCCA Landing Zone meets the CSP portion of SCCA controls. The shared responsibility matrix provides guidance on your DoD mission owner responsibility, as documented in the SCCA Architecture Guide and SCCA Customer Responsibility Guide.
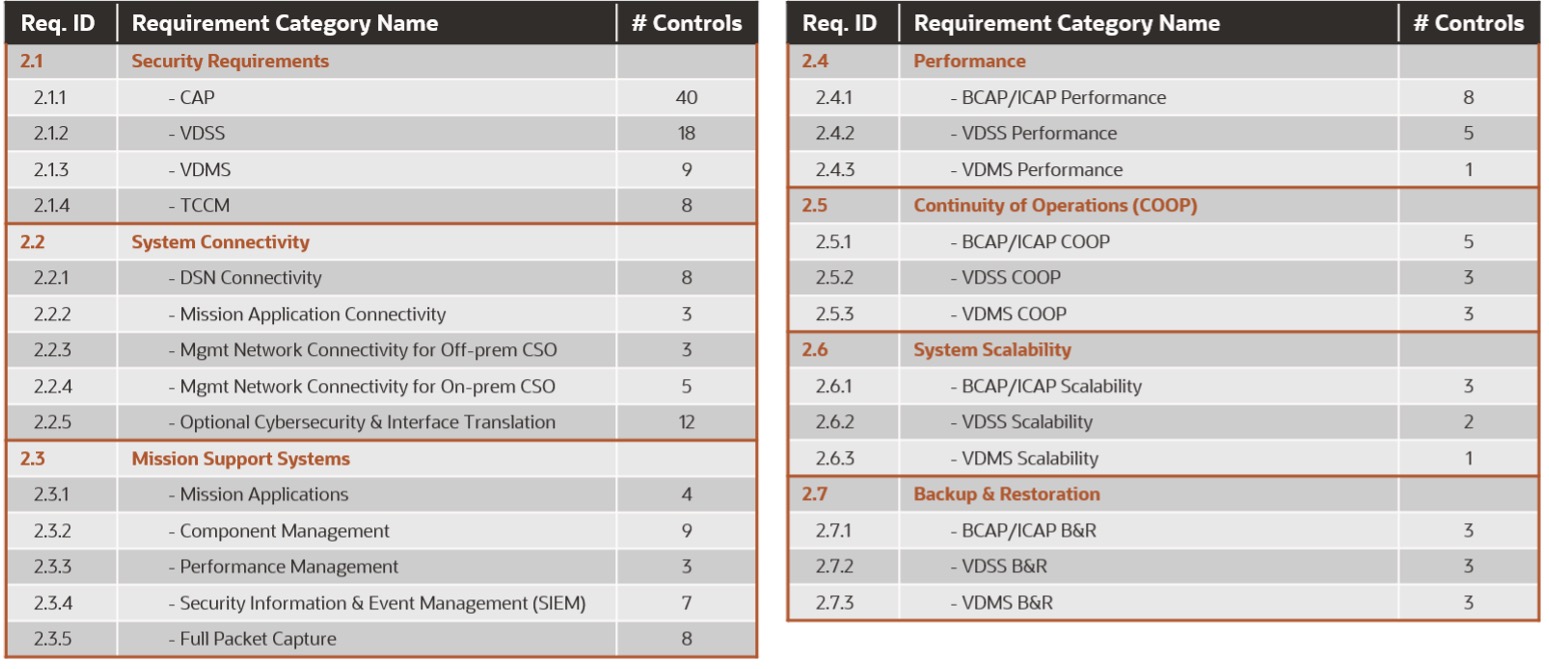
Figure 2: Key SCCA requirements in the DISA SCCA FRD
Accelerate time to deployment for mission critical workloads
The automation and guidance provided by the Oracle Cloud Native SCCA solution enables DoD mission owners to establish a compliant security architecture in just a few hours or days, instead of months. The Oracle Cloud Native SCCA Landing Zone script and associated technical documentation are provided at no separate or additional charge under a customer’s contract. Underlying consumable cloud services used to stand up the SCCA compliant architecture in a customer’s tenancy may be billable in accordance with the customer’s contract. Oracle provides upgrades, maintenance, and enhancements to all these services at no additional cost. The Oracle Cloud Native SCCA solution saves you a significant amount of time and money that can be better used to further your DoD mission.
Up next in our blog series, we will discuss best practices for migrating IL4 and IL5 workloads with the Oracle Cloud Native SCCA Solution.
For more information on the Oracle Cloud Native SCCA solution, please reach out to the DoD Product Management team.
Additional reference materials
Best practices for migrating IL4 and IL5 workloads with the Oracle Cloud Native SCCA Solution
SCCA Customer Responsibility Guide
Oracle Cloud Native SCCA Landing Zone on GitHub
Oracle Cloud Native SCCA Landing Zone Documentation
Oracle Cloud Native SCCA Landing Zone press release



