Introduction
Oracle Database@Google Cloud delivers Oracle Database services inside Google Cloud data centers and in the customer’s Google Cloud environment. The service integrates into Google Cloud Console and services. At launch, the service supported deploying Oracle Database resources connected to a Google Cloud Virtual Private Cloud (VPC) network in the same Google Cloud project.
With the Oracle Database (ODB) Network release, Oracle Database@Google Cloud service adds greater flexibility to the network configuration. The ODB Network creates a metadata construct around the Google Cloud VPC and replaces the VPC connection selection users previously made while provisioning Oracle Database resource in Google Cloud. The introduction of ODB Networks allows customers to deploy Oracle Databases in a Shared VPC.
These additional capabilities create a change in the resource provisioning workflows in the service, making it easier for organizations to split responsibilities between network and database administrators.
Shared VPC Support
With this release, Oracle Database@Google Cloud Network now supports Google Cloud’s Shared VPC capability, a popular network topology in Google Cloud.
Shared VPCs allow organizations to connect resources from multiple projects to a common Virtual Private Cloud (VPC) network in a Host project. Organization administrators can delegate management of applications to Service Project Administrators while maintaining centralized control over network resources. This simplifies the configuration and allows these resources to communicate securely and efficiently with each other using an internal IP address from the Shared VPC network.
Shared VPCs simplify networking configuration in Google Cloud. Service owners, like database users, use the network configuration defined by their network teams, instead of manually configuring the networks between different resources. It reduces the need to enable and configure VPC Peering and associated configurations.
ODB Networks
The ODB Network feature introduces a new step into the deployment workflow, where customer Network administrators configure and define the network configuration before Database administrators leverage them (through an Identity and Access Management (IAM) permissions) when deploying Oracle Database resources.
The network administrator starts by creating an ODB Network, then associates it with a standalone or Shared VPC. Next, they assign CIDR ranges for the client and backup subnets that the ODB network uses. The network administrator assigns “use” permissions on these networks to database administrators. Finally, database administrators provision Oracle Database instances, selecting from the pre-defined ODB networks that they have access to.
VPC Network Conversion to ODB Network
Before the launch of the new ODB Network feature, Google will automatically convert all existing VPC connections for Oracle Database resources to ODB Networks behind the scenes. There’s no action required on your part; your current experience with the Google Cloud Console, API, CLI, and Terraform will remain unchanged. Once the updated deployment workflow is live, your Oracle Database resources will start using the enhanced ODB Network seamlessly, ensuring a smooth transition and improved network management going forward.
Related Roles
IAM Roles for ODB Networks
This feature introduces additional roles in Google Cloud IAM that allow authorized users to manage ODB networks.
| Administrator (IAM role) | Purpose |
|---|---|
| Organization Admin (resourcemanager.organizationAdmin)
|
Organization Administrators have the resourcemanager.organizationAdmin role for the organization. They nominate Shared VPC administrators by granting them appropriate Google Cloud Project creation and deletion roles, and the Shared VPC Admin role for the organization. These admins can define organization-level policies, but specific folder and project actions require additional folder and project roles. |
| ODB Network Admin (roles/oracledatabase.odbNetworkAdmin, roles/oracledatabase.odbSubnetAdmin)
|
ODB Network Admins have the oracledatabase.odbnetworkAdmin roles for the Googe Cloud organization or one or more Folders. They create and manage ODB networks, ODB network subnets, and delegating access to some or all the ODB network subnets in a Shared VPC environment to Service Project Admins. An ODB Network Admin for a given host Project is typically the Project’s owner as well. |
| Service Project Admin (roles/oracledatabase.odbSubnetUser)
|
A Shared VPC Admin defines a Service Project Admin by granting an IAM principal the ODB Subnet User (roles/oracledatabase.odbSubnetUser) role to the host Project. Service Project Admins also maintain ownership and control over resources defined in the service projects. They may have additional IAM roles to service Projects, such as Project owner. |
Google Cloud Roles Required for Standalone VPC Network Deployment
Deploying Oracle Database@Google Cloud resources within a single Project and standalone VPC networks have multiple options for assigning permissions based on their IAM policies:
- Assign all administrative permissions to database administrators.
- Follow the least-privilege model and assign network-related roles to network administrators and assign database-related roles to the database administrators.
The following table lists the roles required depending on the roles and responsibilities of your users:
| Administrator (IAM role) | Roles Required with only Database Administrators | Roles Required with Separate Network and Database Administrators |
|---|---|---|
| Network Administrator | Not applicable | roles/oracledatabase.odbNetworkAdmin roles/oracledatabase.odbSubnetAdmin |
| Autonomous Database Administrator | roles/oracledatabase.odbNetworkAdmin roles/oracledatabase.odbSubnetAdmin roles/oracledatabase.autonomousDatabaseAdmin |
roles/oracledatabase.odbSubnetUser roles/oracledatabase.autonomousDatabaseAdmin |
| Exadata Database Administrator | roles/oracledatabase.odbNetworkAdmin roles/oracledatabase.odbSubnetAdmin roles/oracledatabase.cloudExadataInfrastructureAdmin roles/oracledatabase.cloudVmClusterAdmin |
roles/oracledatabase.odbSubnetUser roles/oracledatabase.cloudExadataInfrastructureAdmin roles/oracledatabase.cloudVmClusterAdmin |
Google Cloud roles required for Shared VPC network deployment
Deploying Shared VPC requires IAM roles granted in both the host and service projects used with Oracle Database@Google Cloud resources.
- Network administrators must have ODB Network and ODB Subnet Admin roles granted in the host project.
- Service project administrators are granted “ODB Network User” role to either the host project or select ODB Subnets.
The following table lists the roles required depending on the responsibilities of your environment’s users:
| Administrator (IAM role) | Roles assigned in host project | Roles assigned in service project |
|---|---|---|
| Network Administrator | roles/oracledatabase.odbNetworkAdmin roles/oracledatabase.odbSubnetAdmin |
None |
| Autonomous Database Administrator | roles/oracledatabase.odbSubnetUser | roles/oracledatabase.autonomousDatabaseAdmin |
| Exadata Database Administrator | roles/oracledatabase.odbSubnetUser | roles/oracledatabase.cloudExadataInfrastructureAdmin roles/oracledatabase.cloudVmClusterAdmin |
ODB Networks In Action
In the new provisioning workflow added to support this feature in Google Cloud, authorized users create ODB Networks by selecting the ODB Network option in the Console.
Note: The capabilities described here are also available to customers through Terraform, API, and `gcloud` CLI.
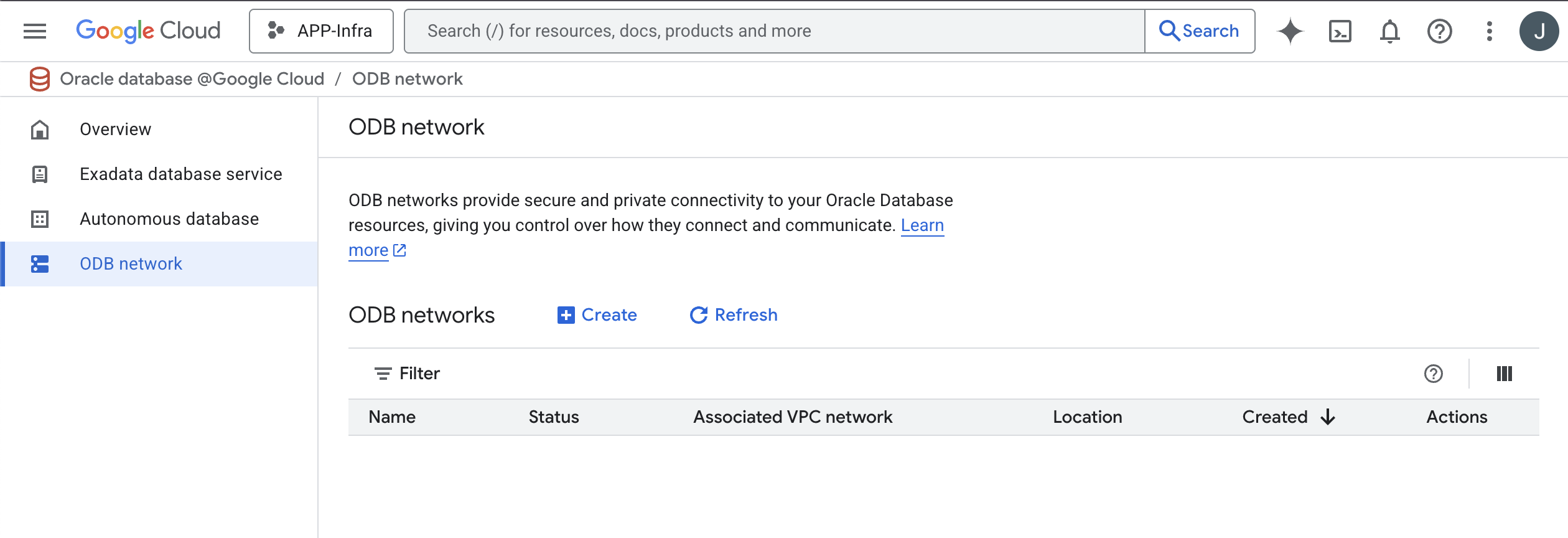
When creating a new ODB network, a network administrator associates the ODB network with an existing VPC in the selected Project and region.
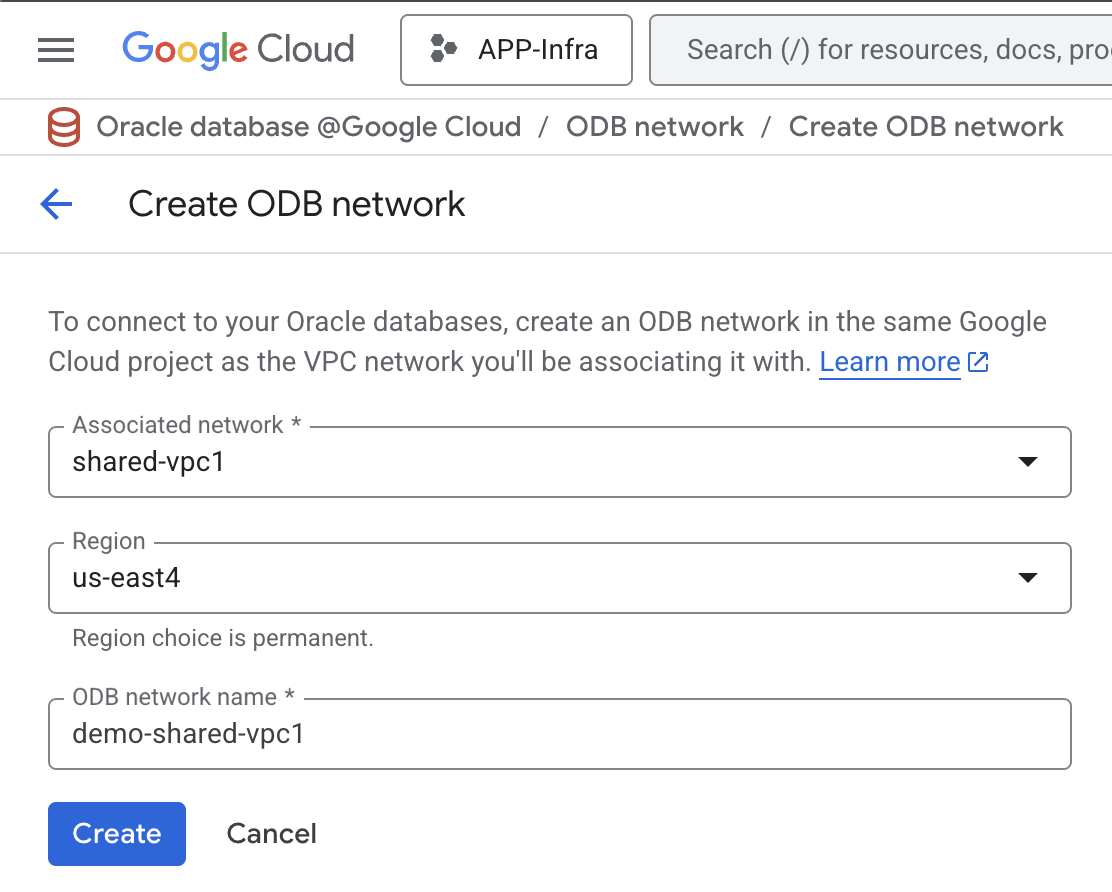
Network administrators can create up to 5 non-overlapping subnets in the ODB Network. The CIDR ranges used for ODB Subnets must not conflict with any existing CIDR ranges used by the selected VPC.
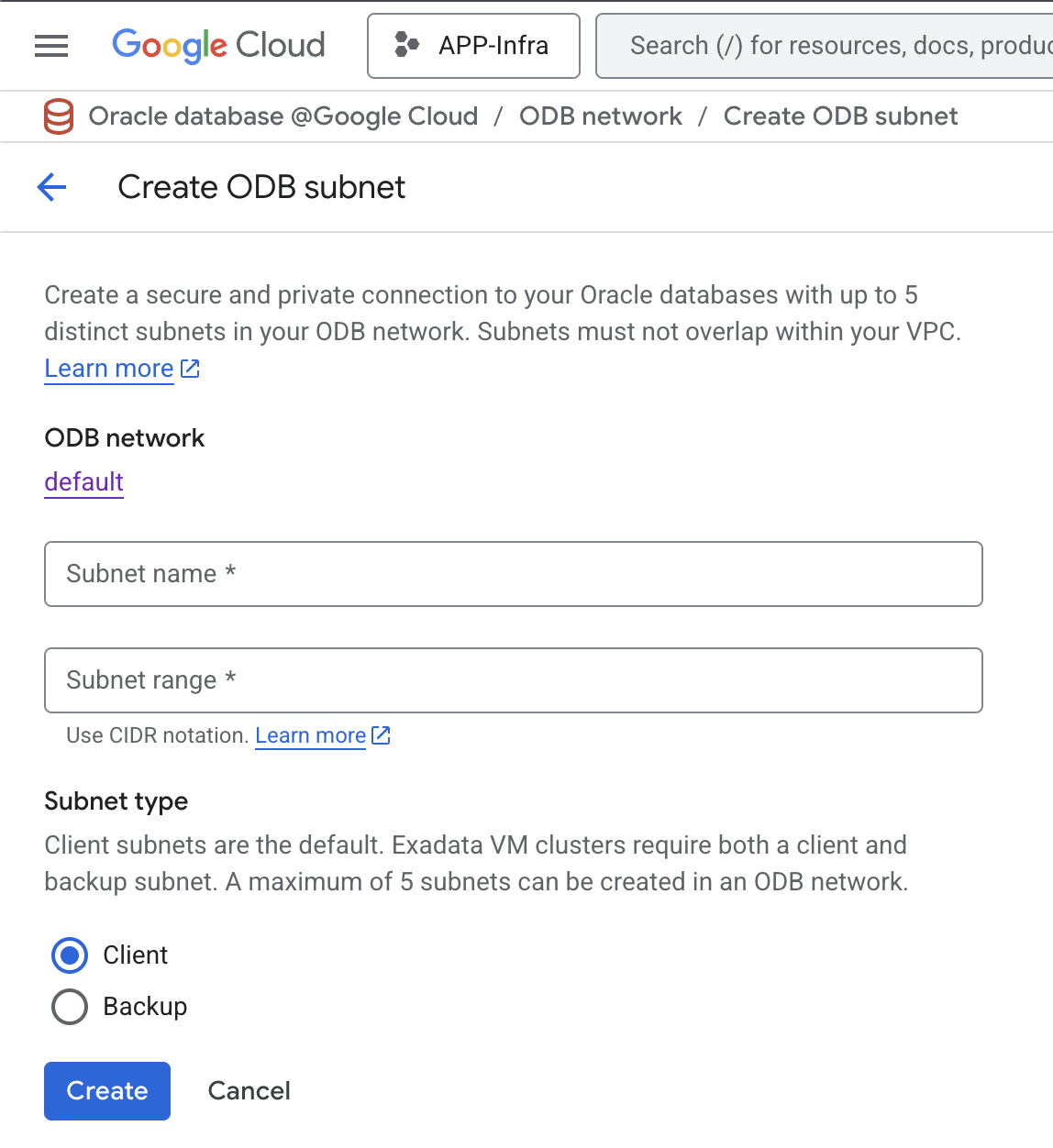
With the ODB network and ODB subnet in place, when a database administrator deploys an Oracle database instance, they select the ODB Network and ODB Subnet created for them during the provisioning process. For a Oracle Database instance provisioned in a Shared VPC, the database administrator uses the project picker to select the Host project (Network project) instead of the current project.
What This Means for Customers
With this feature update comes some changes to the Oracle Database@Google Cloud Console experience and provisioning workflows:
- Adds a new Console section for managing ODB Networks, allowing Network Administrators to create, manage, and delete ODB Networks.
- Removes the option to select a VPC when provisioning Oracle Database resources, replacing it with the ODB Network selection as described above.
Conclusion
With the Oracle Database@Google Cloud network release, customers can plan and manage independently network and database deployment. Oracle Databases can seamlessly integrate into Google cloud network topologies.
Resources
Oracle Database@Google Cloud
Learn about network topologies for Oracle Database@Google Cloud


