If you’ve ever added FRA-Project42-RCK21-DKR to a title of a compute instance running Docker in Frankfurt, to help remind yourself of its purpose, then you’ll understand the value of tagging. And if you’ve every had to try to determine whether various cloud resources, each tagged with “finance” “fianance” “fnce” or “fin” belonged to – and perhaps were billable to – the finance department, you’ll be familiar with some of tagging’s limitations.
I’m Martin Sleeman the Product Manager for Oracle Cloud Infrastructure Tagging, and in this post I’ll describe and demonstrate how Oracle Cloud Infrastructure tagging capabilities can help you address these challenges.
For those new to tagging, basic tags enable you to attach arbitrary, free-form metadata to cloud resources, like compute instances. The labels that tags provide can help you organize and control resources. For example, you can add tags to describe the business organizations that are responsible for a resource, or operational metadata needed to manage your resources effectively.
While other public cloud tagging implementations support free-form tags, that approach provides no structure. Oracle’s Cloud Infrastructure supports free-from tags, but our solution goes further. We recommend the use of our new Defined Tags, which eliminate many of the drawbacks of free-form approaches. Defined Tags support a schema to help you control tagging, ensure consistency, and prevent tag spam. You can even use tags to script bulk actions on your resources, to automate and simplify tasks.
Let’s explore how you create Defined Tags, scripting with tags, and the control they provide.
Namespaces and Tag Definitions
With Defined Tags, you can define the names of the tag keys to prevent “tag spam” (when users mistag resources by, for example, misspelling the keys). Defined Tags must have a Tag Key Definition which consists of the Tag Key and a Description. Tag Key Definitions are contained in a tag namespace, which groups defined tags for ease of administration. You can also set policy to restrict user access to tag namespaces. This ensures users without authorization don’t tag resources, change resource tags, or mistag resources.
It is easy to create a Tag Namespace and Tag Definitions. To create a Tag namespace in the Oracle Cloud Infrastructure portal, simply:- Click on Identity
- Select Tag Namespaces
- Then click on the “Create Namespace Definition” button
- Give the new Namespace a name and description
Now that you have a namespace you can add Defined Tag Key Definitions to it.
To create a Defined Tag simply:
- Click on Identity
- Select the Tag Namespace you wish to add the Tag Key Definition to
- Click “Create Tag Key Definition”
- Type in the Tag Key (it must not contain spaces or dots)
- Type in a description
Now that you have a Defined Tag you can apply it easily to existing resource and also apply it when creating new resources.
To apply a defined tag to a resource simply find the resource you wish to apply the tag(s) to and then click the “Apply Tag(s)” button.
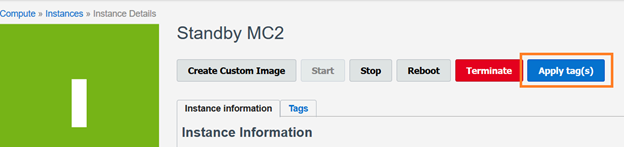
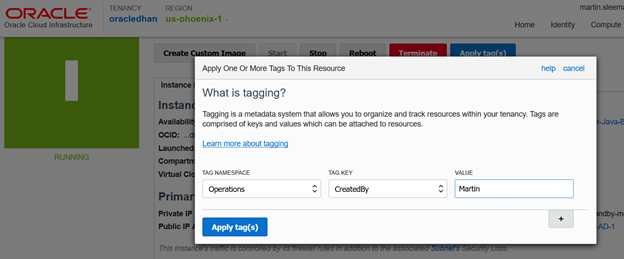
From there Select the Namespace from a drop down list, the Tag Key from a drop down list and then type in a value.
Tag Scripting
Tags also enable you to enhance your Oracle Cloud Infrastructure scripts to target only resources with particular tags. Let’s say Alice is using a “needs_backup” tag whose if any major updates have occurred to the block volume. She runs a script which examines the “needs_backup” tag for all her block volumes. When it encounters a block volume that has the needs_backup tag, it kicks off a backup of that block volume. Because “needs_backup” is a Defined Tag, it can easily be applied in a consistent fashion as new resources are created, and be protected from unintentional – or deliberate – changes by unauthorized users, which helps ensure those backups get done.
Here’s a python snippet to give you an idea of how this type of script could be written using our REST APIs:
# the name of the key to search for
filter_key = 'needs_backup'
# walking through the responses from the call to list compute instances
for compute_dict in response.json():
if filter_key in str(compute_dict['definedTags']):
print('Back that one up!')
# calls a user defined function to backup the volume
backup_volume(compute_dict)
We plan to add tagging support to our SDKs so look for a new blog post detailing the new and interesting things you can do with tags in the soon to be released SDK.
Controlling Access to Tags
You can also help ensure tag reliability by restricting access to Tag Namespaces. For example, you can have a set of Operational tags that anyone can use and apply to resources, and a separate set of sensitive tags from the finance team which you want to ensure are only applied and changed by a handful of authorized individuals. Defined Tags support this scenario by enabling you to set access control on a Tag Namespace. In this example you would create a namespace called Operations and give everyone access to that Namespace. You would also create a “Finance” namespace, but since that namespace is sensitive you would only give access to the trusted set of users. You would create Defined Tags, such as CostCenter and Project in the Finance namespace. Now you can rest assured that only a trusted group of users can apply and change those Finance tags.
These examples just scratch the surface of how you can enhance scripting and management of cloud resources with Defined Tags.
Oracle Cloud Infrastructure Tagging enables you to apply schema to tags, reduce Tag Spam, control access to tags, and empower your scripts, to ease the management and reporting of cloud resources. And only Defined Tags address the limitations of free-form tagging and provide the structure enterprises need to manage cloud resources at scale.
So, start tagging your resources today! If you need more information check out our documentation pages here.
Martin Sleeman (Principal Product Manager) Oracle Cloud Infrastructure
