Enterprises face data protection and privacy liability issues based on new General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA) regulations, which carry fines of up to $25M. Both regulations empower consumers with key data protection rights, including knowing how their data is being used, a right to access, and a right to opt-out of having their data sold to third parties. In light of these new protections, a staggering €500M has been fined since GDPR enforcement began in mid-2018. This problem is growing, and enterprises need a simple, automated solution.
Current Solutions
Today, several software management solutions have designed workflows to manage compliance, such as awareness, data mapping, consumer request fulfillment, cookie management, vendor risk, and incidence reports. These great tools help manage the requirement and avert fines. However, these processes typically require several people to manage the effort and are difficult to scale when customer requests and deletion rates grow exponentially. Fundamentally, the customer does not achieve real privacy and transparency, and the company is still liable for privacy breaches, regardless of compliance requirements.
A New Approach
For organizations to truly solve the privacy issue and achieve zero-liability, they must give full ownership and control of data to the customer and provide transparency of data activities. The following architecture allows you to own a storage allocation on a trusted platform to upload their data, and then share an encrypted link to the company. The business then uses this auth token to download a copy for their application, without any change to their current IT processes. In this three-step process, where you have the following capabilities:
-
Owning data and can upload, updated, delete encrypted data.
-
Sharing the authentication token to the company.
-
Allowing the company to download their data.
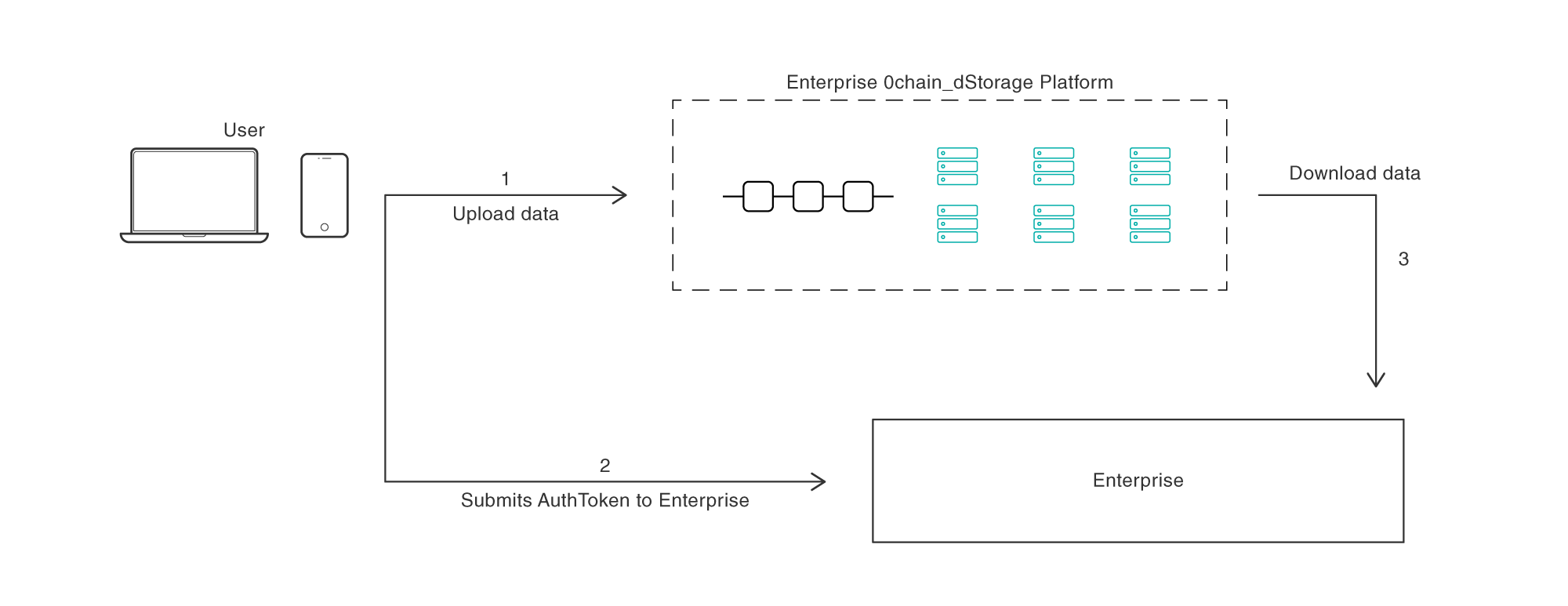
This simple three-step process is recorded and displayed transparently to customers, without the need for complex processes that can’t scale with customer requests for access and deletion of their data. The responsibility lies with the customer, and not the company.
Shifting Liability
With user ownership, control of data, and a transparent process of securely sharing it to the company, the onus of privacy protection lies with the customer. For the hacker, it’s difficult to attack a lot of customers, because they would need to steal keys individually.
With the liability shifted to you, organizations must ensure that the data is well protected, that all activities are recorded on the ledger, and prevent any potential for breach.
Preventing Breach
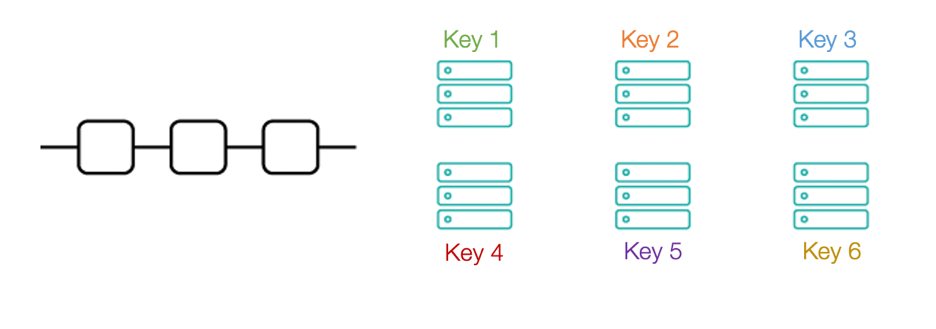
Copies are inherently vulnerable because a hacker needs to attack only the most vulnerable server to get access to all customer data. One approach to prevent this attack mode is to split the data into multiple servers with different keys. Now, the attacker needs all the keys to get access. The implementation of this architecture is fairly simple as the server access keys can be distributed among teams and individuals within the organization.
The Business Advantage
0Chain is deployable directly from Oracle Cloud Marketplace. It provides automation, liability and breach protection, immutability, transparency, and a trusted platform for the Oracle Cloud Infrastructure customers to not only abide by GDPR and CCPA regulations, but also use them to their business advantage. With 0Chain, organizations can brand themselves as a leader in privacy, gain higher usage, add revenue, and differentiate their products in the market.
You can deploy 0Chain on-premises, through cloud, or in hybrid environments. The user interface automatically creates a key and allocation and stores the key based on your password. So, only you can access you key and data. This key is registered on the platform’s blockchain and any action of uploading a new file (such as a post, image, or video), updating an existing file (such as user profile data), and deleting them are recorded on the ledger.
The files are automatically shared to the business through an auth token. So, only the business can decrypt and use it for their operations. Each time the company uses customer data, they need to make a note of the metadata on the blockchain, creating a transparent audit trail for you to instantly visualize it and have complete trust in the organization. The company can handle this process as a parallel batch operation offline, without the need to block existing inline data used by the company for their daily business activities.
Migrating customer data to this trusted platform requires a simple, phased approach. In the first phase, only new data is sent to the platform. In the second phase, older data is migrated. In subsequent phases, granular datasets can be implemented to have a higher level of precision permission settings that the company can offer the customer, perhaps with a fee to cover for development costs.
FAQ
-
How do you achieve zero liability?
Since you own and controls the data, the company is not liable. You provide explicit permission through signed transactions, which can’t be disputed since their action is recorded on the blockchain and is immutable—something that a company can’t go back and change in their database records. -
How do you make breach impossible?
Since the file is split into multiple servers, a hacker needs to have keys to all of them to gain access. This configurable feature, with each server split, makes it more difficult to get hold of the keys, as long as they’re distributed across individuals and teams. -
Does 0Chain replace the current privacy software tools?
No. 0Chain helps you protect your data better and shift liability back to you. It can handle billions of customer privacy requests and provides instant compliance reports from ledger transactions, using integrated search tool for specific files, users, and activities that anyone can access. Through these efforts, 0Chain provides an open, trusted compliance platform. -
How do you ensure that the enterprise aligns with your consented dataset?
Whenever a dataset is used by the enterprise, they send a signed transaction with the metadata of the content to record the activity. If the company misuses the dataset, you can mount a challenge based on the exposed data and the consent that’s recorded in the ledger.
Want to Know More?
To learn more, visit our website and trial our product for free through Oracle Cloud Marketplace.