A new year often comes with resolutions to do things better – get in shape, learn a new language, improve your database’s security. By spring, many resolutions have been forgotten – we haven’t visited the gym in months, we stopped improving our language skills right around the “hello, how are you” stage, and we are back to securing our databases the same way we did last year, the year before, or the year before that. When it comes to database security, we cannot continue with old habits – it’s a risky world with ever-evolving threats and databases hold our most critical asset, our sensitive data.
Before we can even begin work securing our databases, it’s important to know exactly where we stand. In this blog post, we’ll show you how to assess where you are by following four steps:
- Assess the security configuration of your databases
- Identify sensitive and privileged user accounts
- Locate PII and other sensitive data in your database
- Continuously monitor for and receive notifications of configuration drift
These steps can be performed in minutes and, once you know where you stand, you will be in a much better place to develop a plan to improve data security. Let’s get started.
Assessing Configuration Settings
By checking and maintaining proper security configurations, you can help minimize the risk to your database, your data, and ultimately your organization. Everything we do should help reduce the attack surface area and help reduce the organization’s risk. It’s vital to check the configuration of your database to identify whether you:
- Have misconfigured systems as the result of development or testing activities
- Have missed installing the latest security patch or the upgrade
- Have gaps compared to the company, industry, and regulatory standards
Oracle offers two tools you can use to help quickly verify your database configuration settings: Oracle Database Security Assessment Tool (DBSAT) and Oracle Data Safe.
DBSAT is a command-line utility that requires no formal installation or configuration; all you need to do is to unzip the archive, run the collection module, and generate a report. DBSAT can check dozens of security-relevant configuration settings for your OS, audit settings, encryption, and database initialization parameters, and compare them to some of Oracle’s recommendations as well as some GDPR, STIG, and CIS standards. DBSAT can help you identify whether you have applied critical security patches, such as the latest release update, to the database. Oracle customers can download the latest version of DBSAT from MyOracleSupport at no additional cost – look for note 2138254.1.
Oracle Data Safe provides security assessment capabilities with a cloud-based solution hosted on Oracle Cloud Infrastructure (OCI). Like DBSAT, Data Safe delivers some of Oracle’s configuration recommendations mapped to some of the technical requirements commonly associated with GDPR, STIG, and CIS. Data Safe can go a step further and allow you to see results across your entire Oracle database fleet, including Oracle Autonomous Database, Oracle Database Cloud Service, and on-premises databases. Data Safe is included for customers using the Oracle Cloud database services and is available as a subscription for those who want to assess their on-premises databases or databases running in third-party clouds like AWS or Azure.
With both DBSAT and Data Safe, you receive easy-to-understand prioritized reports of findings, mapping to various configuration standards, and recommendations on how to mitigate the related technical risks.
Identifying sensitive accounts
Like verifying configuration settings, it’s important to review users and privileges to understand:
- Do you have user accounts that could be particularly damaging if compromised?
- Are you following a “least privilege” approach to user account management?
- Do you have third-party or industry regulations that require periodic privilege review?
Reviewing users and privileges enable you to create a baseline for who has access to data and what privileges they have. Once you have a baseline, you can begin reducing or consolidating privileges to minimize the attack surface area and reduce the overall risk to the organization.
DBSAT collects information about users, roles, and privileges, and can tell you which system and data access privileges have been granted to whom and how. For example, were they granted to the public? To database users? Or your custom bespoke applications? Their risks can be much higher if they were granted privileges with admin options or through the container database.
Data Safe takes it a step further by enabling categorizing users based on some risk severity assessments and giving you a dashboard to quickly identify highly privileged users with access to database operations or sensitive data. Data Safe allows you to schedule regular user assessments and compare results to see what has changed.
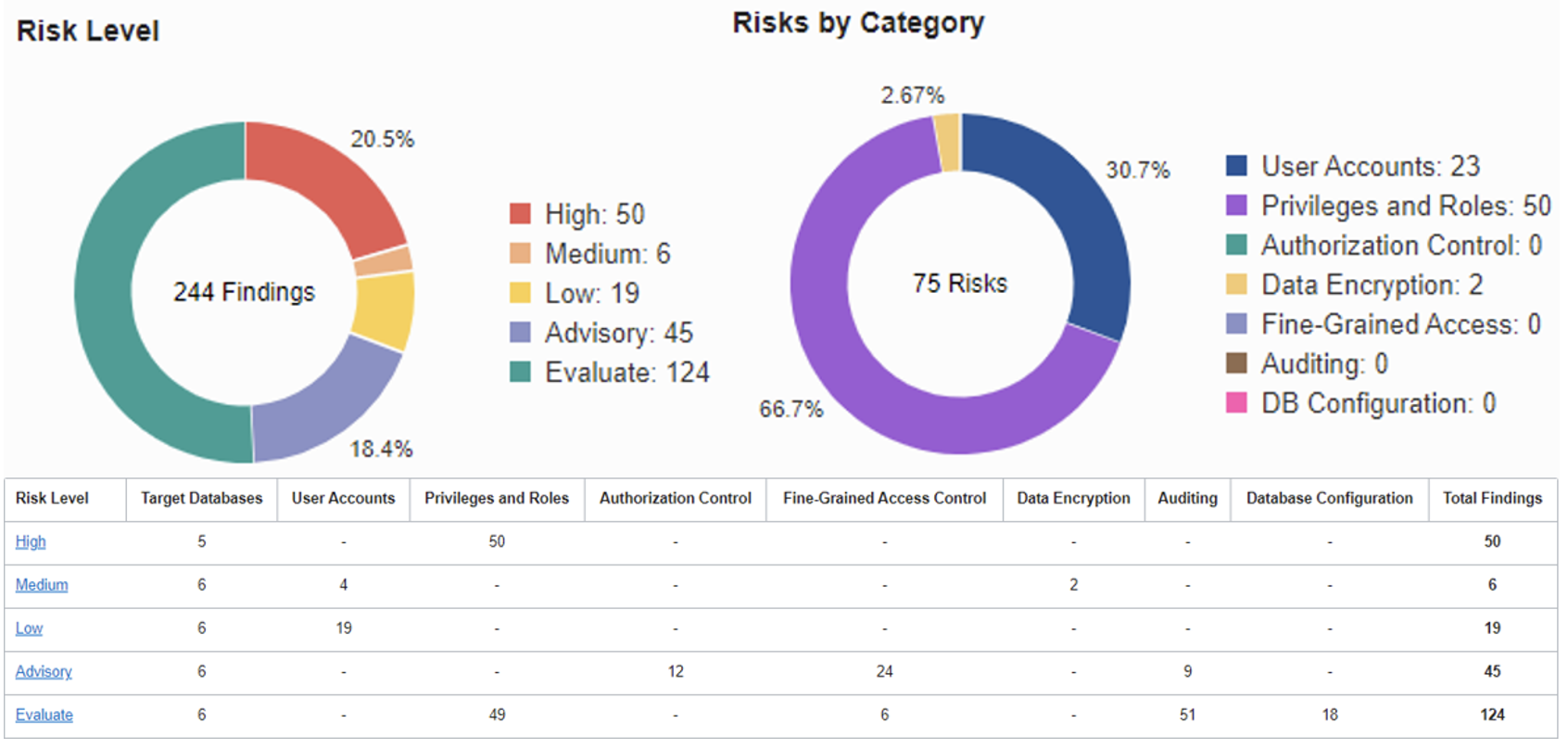
Users tend to collect more privileges than are needed, leading to a much higher risk if they get compromised. Privilege Analysis, a feature included with Oracle Database Enterprise Edition, helps you capture which privileges were used by a user, and which were not. This can be extremely helpful for periodic privilege reviews and enables your organization to reduce risk by removing unused (unnecessary) privileges from database accounts. Data Safe takes it a step further by enabling categorizing users based on some risk severity assessments and giving you a dashboard to quickly identify highly privileged users with access to database operations or sensitive data. Data Safe allows you to schedule regular user assessments and compare results to see what has changed.
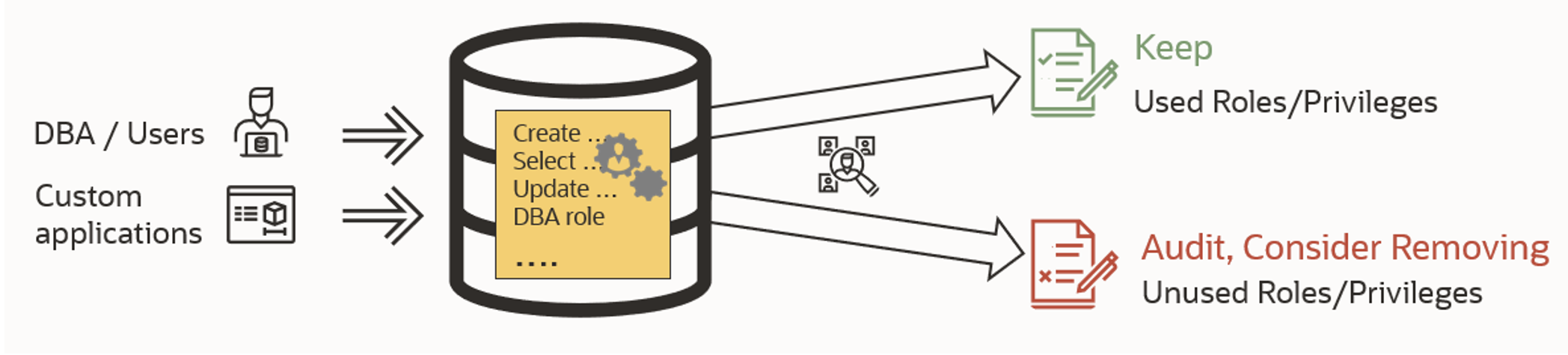
Identifying sensitive data
Sensitive data discovery allows an organization to know what type of sensitive data they have, along with its quantity and location. This helps them perform two critical tasks:
- Identify the risk to the organization if the data is exposed or lost
- Decide how to mitigate, transfer, or accept the risks associated with different types of data
DBSAT includes a separate module specifically designed for searching for sensitive data such as social identifiers, credit cards, phone numbers, and more. It can examine the column names and comments on a schema-by-schema basis looking for some patterns that may indicate sensitive data. DBSAT also helps give you a rough idea of how much sensitive data you have in the database along with its category using table statistics. Row count can be helpful to know so you can decide whether to focus on the small bits of sensitive data or the databases with large amounts of sensitive data. The DBSAT pattern matching file is customizable, so your organization can include patterns for column names or comments you know contain sensitive data. DBSAT supports patterns in multiple languages such as English, French, Portuguese, and Spanish.
Application Data Modeling in Oracle Enterprise Manager (EM) 13c can also examine the column names, column comments, and the first 100 rows of the data to help suggest whether a particular column contains sensitive information. Like DBSAT, EM 13c has an out-of-the-box library of some sensitive type pattern matching that is also extensible, but EM does not tell you how many rows of sensitive data exist. EM also requires you to create an Application Data Model (ADM) before discovering sensitive data. The ADM is needed if you’re going to mask data.
Oracle Data Safe can examine column names, column comments, and column data and then helps give you an estimate of how much sensitive data exists in your database along with its type, table, and column. Data Safe has over 125 built-in sensitive data types, supports patterns in different languages, and is extensible to meet your organization’s needs. When Data Safe discovers potentially sensitive data, it can also build a Sensitive Data Model (SDM), which you can leverage to mask the data for test and development. Data Safe recently added a new “Fleet View” for the sensitive types of data across all your Autonomous Databases, Database Cloud Services, and On-Premises databases.
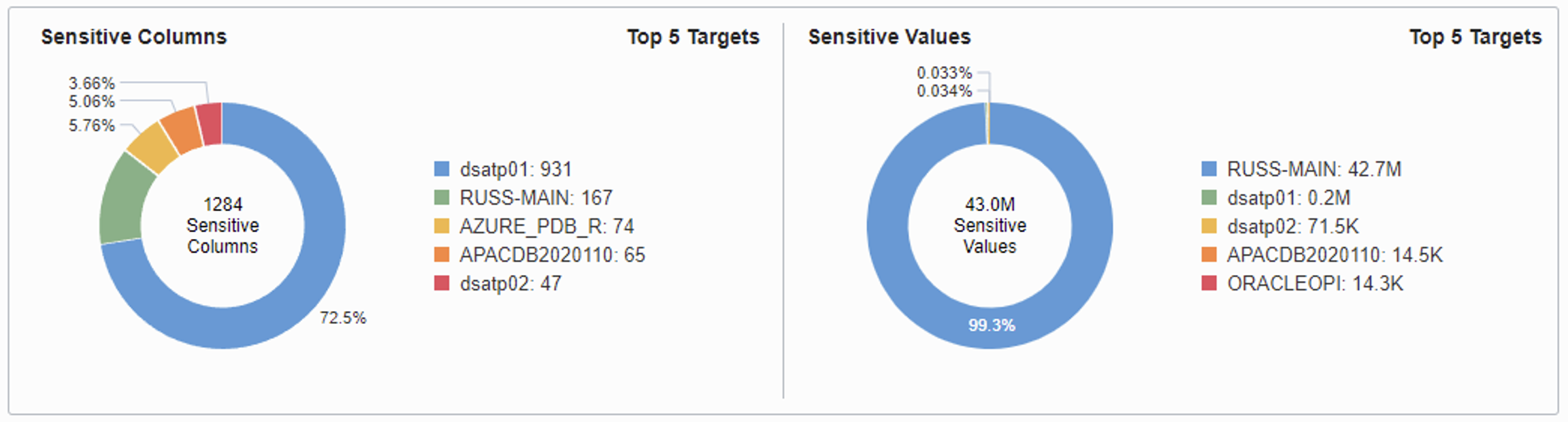
Detecting configuration drift
Once you have established your desired security configurations, essential user privileges, and have identified the data you need to protect, you want to ensure that there is no drift and that your databases continue to operate securely. Security misconfigurations might arise for several reasons:
- An administrator temporarily changes a security control to debug a production application and forgets to change it back
- An application is moved from a test or development environment to production without the requisite hardening
- A bad actor changes some security controls as part of a broader reconnaissance or with the intent of exploiting the change later
- An application patch changes some parameters without your knowledge
Helping prevent these incidents from going undetected is where Data Safe shines, by providing drift detection and notification of deviations from a specified security baseline. Data Safe can automatically run user and security assessments and compare new assessments against your baseline. For example, the screenshot below shows there have been changes in several categories at various risk levels, including modifications to user accounts, privileges/roles, fine-grained access control, and auditing. Data Safe can notify you of deviations for user and security baselines with the OCI Notification services.
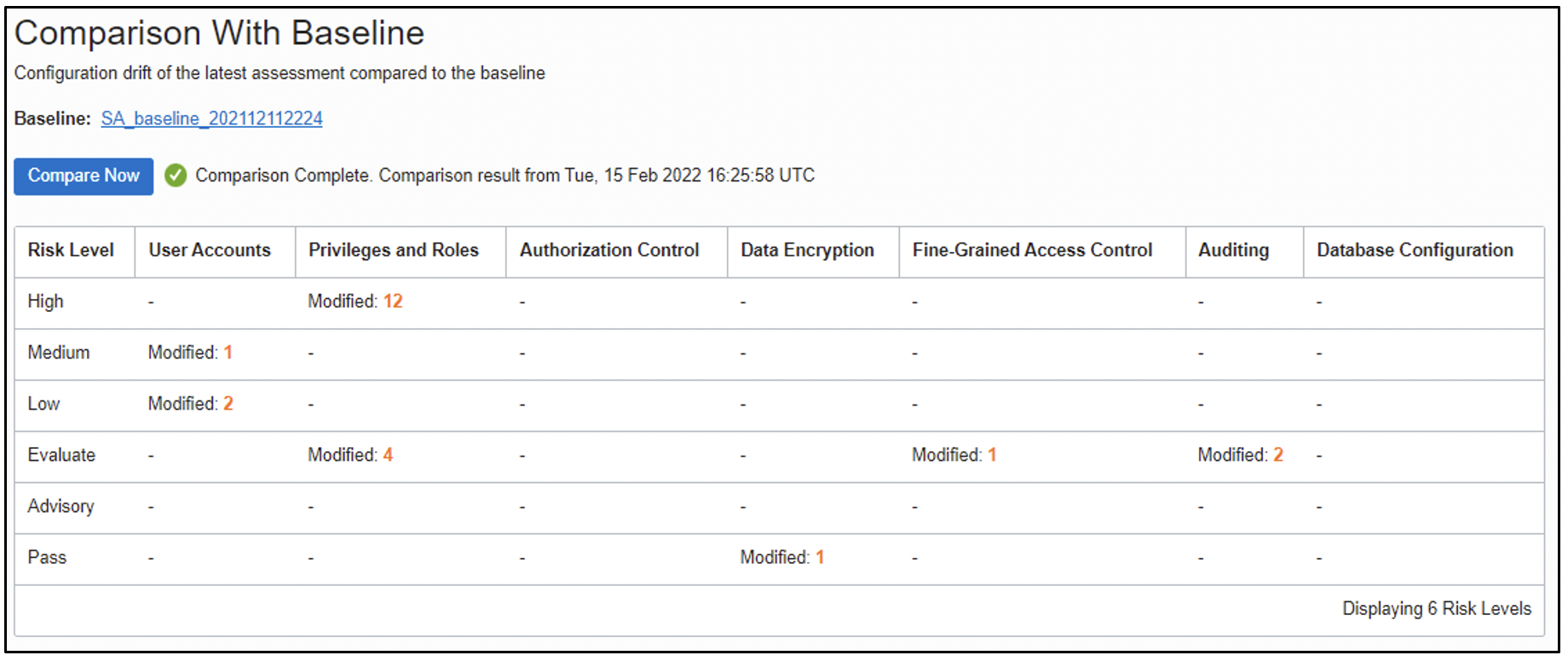
Now is the time to get started
Databases operate in highly demanding environments, managing data that is the lifeblood of your organization. Fortunately, taking the first step to securing them is easy with the tools we’ve talked about here. Now is the time to break bad habits from the past years. Assess your current database security, create a plan to improve the weak areas, and set baselines to monitor for drifts. Starting is supposed to be the most difficult part, but if you start now, you will be well on your way to a secure database before you know it. Visit www.oracle.com/security/database-security to learn more.