Rule sets for your access control list (ACL) on your load balancer listener allow you to control your traffic because they permit or deny access to the load balancer. This permission reduces undesired requests sent from the load balancer to your backend systems.
This blog gives a brief introduction of ACLs and provides two use cases: Allow or deny public classless inter-domain routes (CIDRs) and allow or deny private CIDRs. Then, it instructs you on how to configure ACL rule sets on your load balancer.
Access control lists
ACLs act as a firewall to control the traffic going through your load balancer. The access control rule is based on the source IP. The rule permits access to application resources based on user-specified source IP address or address range. ACL rule sets are similar to pattern-matching and are used to verify certain conditions and perform an action, such as blocking traffic. If you don’t specify any ACLs, the default allows all traffic and forwards it to your load balancer backends.
Use cases
ACL rule sets restrict access from your specified IPs, range of your subnet, your own public addresses, or your on-premise network. The following use cases illustrate how a rule set can be used with your load balancer.
Allow or deny public CIDRs
This use case demonstrates that you can restrict access to application resources, based on a client’s source IP address range. An access control rule is applied at an HTTP or HTTPS listener. In Oracle Cloud Infrastructure (OCI), the default allows until you add a rule; then it becomes default deny. For example, if you configure access control rules as IP range 206.223.27.0/24, the listener denies all the traffic outside this range.
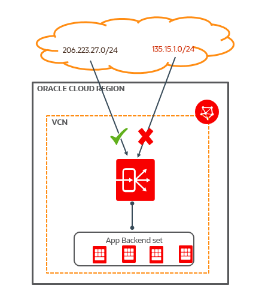
Allow or deny private CIDRs
You can also use restricted access for specialized applications or locations or departments inside the customer’s network. If you have an accounting system for a global company, you can allow each country’s Finance and Accounting team to access the VCN identified in the rule set and block the rest of the team from access.
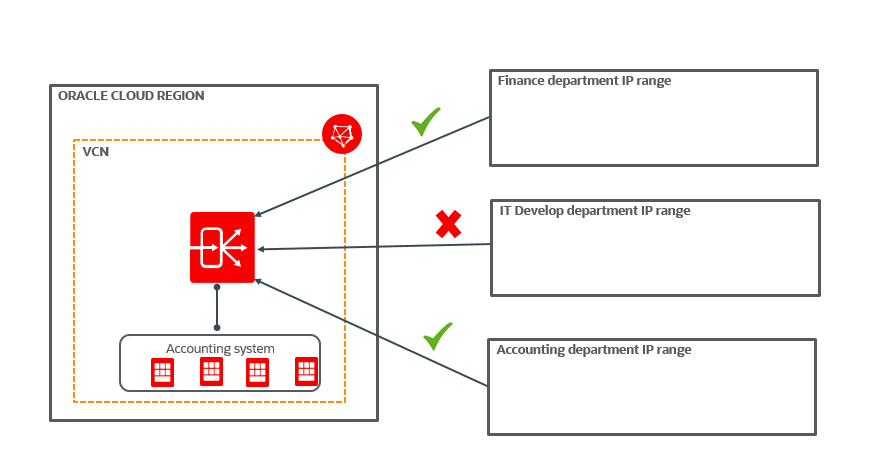 How to create an access control rule
How to create an access control rule
-
Click details of your load balancer. In Resources, click Rule Sets.
-
Click Create Rule Set and enter the name of the rule set.
-
Check the “Specify access control rules” box and enter an IP CIDR block.
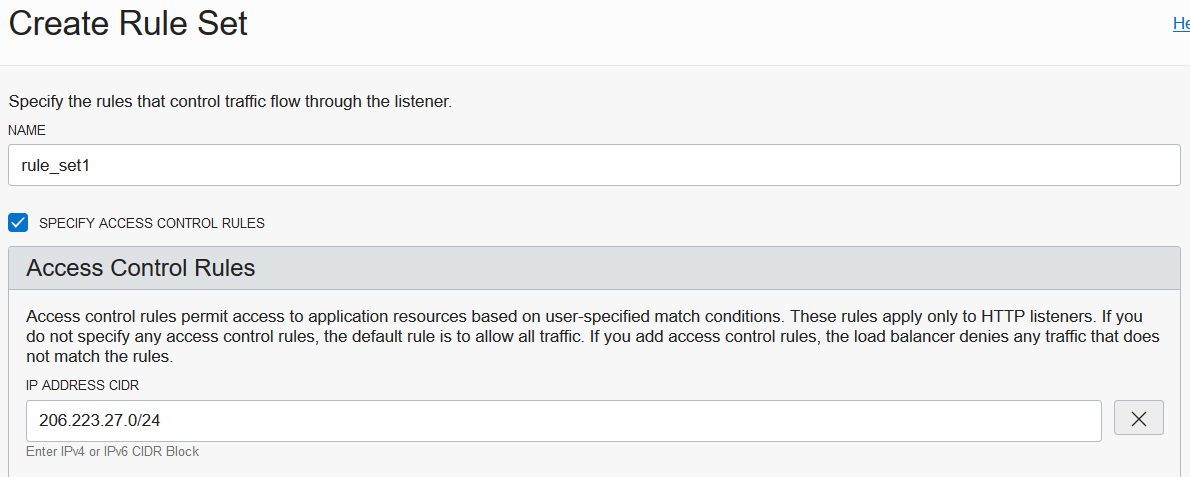
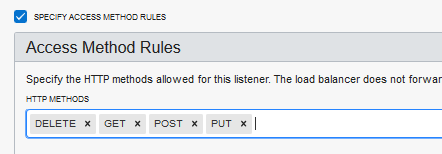
You can also configure a rule set to allow certain HTTP method at a per HTTP listener level. If a user sends a request to the listener using an HTTP method not on your allowlist, the load balancer returns an HTTP 405 Not Allowed error code. Consider adding only methods that your application is designed to receive to your allowlist. For example, if you don’t want to receive POST requests, don’t add POST to the rule set.
Creating access method rules
The method is optional. Select one or more methods if you need them.
-
Click the details of load balancer. In Resources, click Rule Sets.
-
Click Create Rule Set and enter the name of the rule set. Then check the “Specify access method rules” box and select the method.
Conclusion
Access control rule sets are available to use in the Oracle Cloud Infrastructure Console, API, CLI, and in Terraform for your automation needs. You can use rule sets to help prevent security risks and reduce unwanted network traffic from your load balancer to your backend servers. To learn more, see the Rules Sets documentation.