We’re pleased to announce the general availability of two major enhancements for internet protocol security (IPSec) virtual private networks (VPNs) in Oracle Cloud Infrastructure (OCI) commercial regions: support for multiple encryption domains and VPN logging.
Support for multiple encryption domains allows customers to specify multiple pairs of source and destination CIDRs for encryption when using a policy-based IPSec VPN implementation with the Oracle Cloud Infrastructure VPN Connect service.
With VPN logging support, customers now have more visibility for their IPSec connections. Customers can use the Oracle Cloud Infrastructure Logging service to view log messages generated by the VPN service, such as during initial tunnel negotiation, to assist with verification and troubleshooting of any IPSec related issues.
Both enhancements are only available in regions where Oracle supports the VPN Connect v2 service.
Overview of policy-based VPNs
The IPSec protocol uses security associations (SAs) to decide how to encrypt or decrypt specific traffic. For each SA, a defined encryption domain maps interesting traffic based on a packet’s source and destination IP address. In other words, the source and destination IP addresses on both ends of the tunnel are encrypted and forwarded to the IPSec peer on the other side. The encryption domain must match on both sides to successfully negotiate an IPSec VPN tunnel.
Customers using legacy, policy-based VPN devices might not be able to use a route-based IPSec VPN with a single encryption domain. They might require multiple, discontiguous on-premises networks to forward interesting traffic across the VPN tunnel to resources in Oracle Cloud.
With the multiple encryption domain enhancement for policy-based VPN, customers can now define multiple on-premises and Oracle Cloud CIDRs in OCI to match a multiple encryption domain IPSec VPN configuration on their customer-premises equipment (CPE). This system provides customers with improved interoperability with policy-based VPNs and more flexibility in defining specific interesting traffic for their VPN tunnel. They don’t need to summarize their policy encryption domains into a less specific single entry or use a route-based VPN. For more information on this concept and how it pertains to OCI, see Supported Encryption Domain or Proxy ID.
Getting started
Verify that your current IPSec Connection is using the VPN Connect v2 service. This can be viewed by browsing to your current IPSec Connection within the OCI Console. For more information on the VPN Connect v2 service and regions where it is available, see Updated VPN Connect service.

If your current IPSec Connection is already using VPN Connect v2 you can enable both multiple encryption domain support and the VPN logging features. You can edit your existing tunnels in your IPSec Connection to use policy-based VPN by selecting the policy-based option. All your previously configured settings, such as pre-shared keys, IKE version, and Oracle VPN IP addresses, remain the same. You also need to configure IPSec on your CPE to match the new policy-based configuration.
If your current IPSec Connection is still using VPN Connect v1, first ensure that you’re in an OCI region where VPN Connect v2 is available. Once you’ve confirmed that VPN Connect v2 is available in your OCI region of choice, create a new IPSec Connection to use policy-based VPN. This new IPSec Connection will automatically use the VPN Connect v2 service. You will also have to reconfigure your pre-shared keys, IKE version, and other IPSec connection-related settings for this connection. Both tunnels in the IPSec Connection will also have new Oracle VPN IP addresses. Configure IPSec on your CPE to match the new policy-based configuration and update the IPSec peer IP address on your CPE to match the new Oracle VPN IP address for each tunnel.
Creating a policy-based IPSec VPN
-
Open the navigation menu in the OCI Console, go to Networking, and click VPN Connections.
-
Create an IPSec Connection. Click Show Advanced Options and select Policy Based Routing as the routing type for your tunnels.
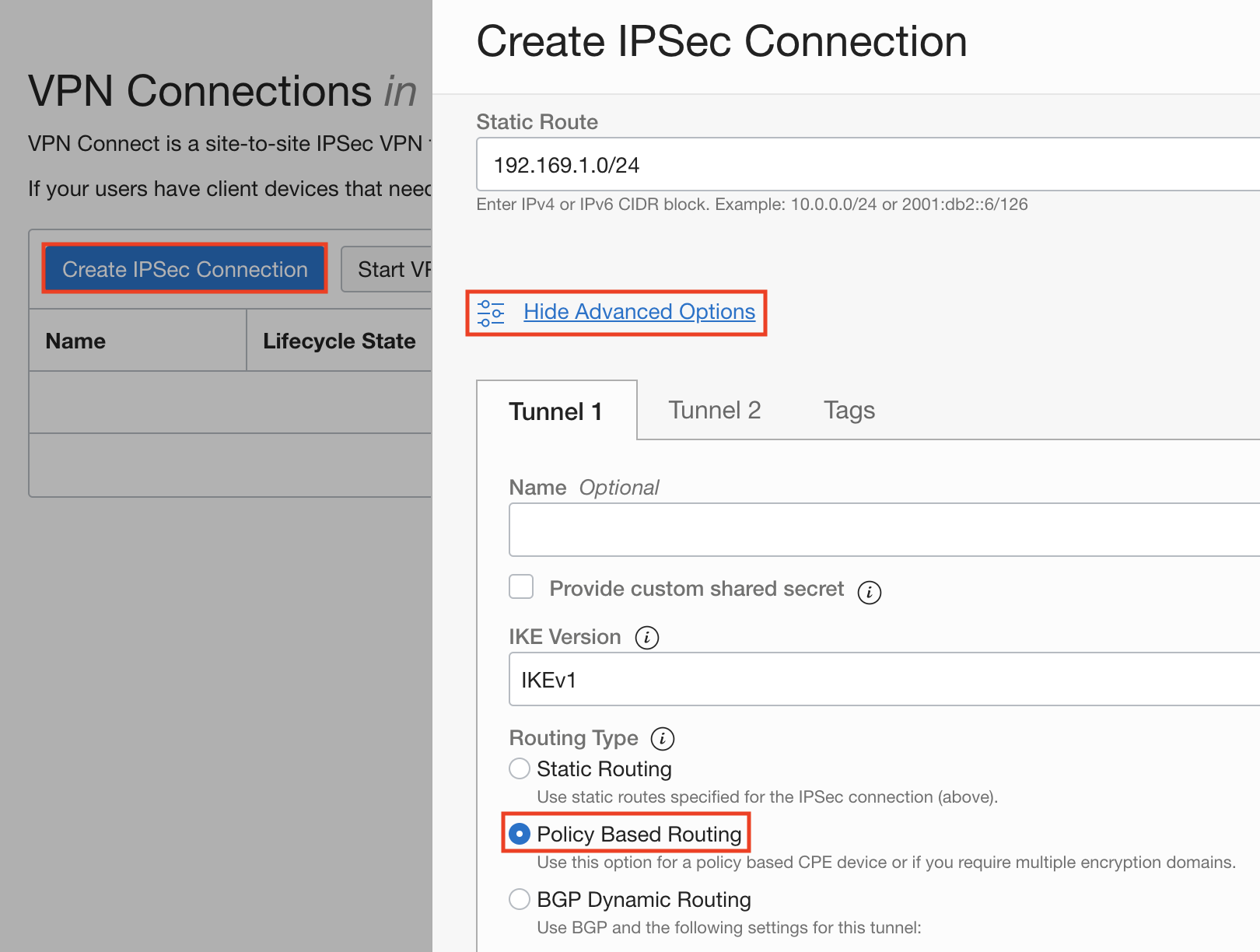
-
Input on-premises and Oracle Cloud CIDRs.
Under Associations input all on-premises and Oracle Cloud CIDRs that need to communicate over the VPN tunnel. You can provide multiple on-premises and Oracle Cloud CIDRs.

That’s it for configuring multiple encryption domains! After selecting all your other IPSec VPN options, you can click Create IPSec Connection. When the IPSec connection has been provisioned, configure your CPE. For more info on how to configure your CPE, see Verified CPE Devices for CPE configuration guides or use the CPE Configuration Helper tool.
Getting Started with VPN Logging
By using the Logging service you can configure, view, and manage your VPN logs.
- Open the navigation menu in the OCI Console, go to Logging, and click on Log Groups.
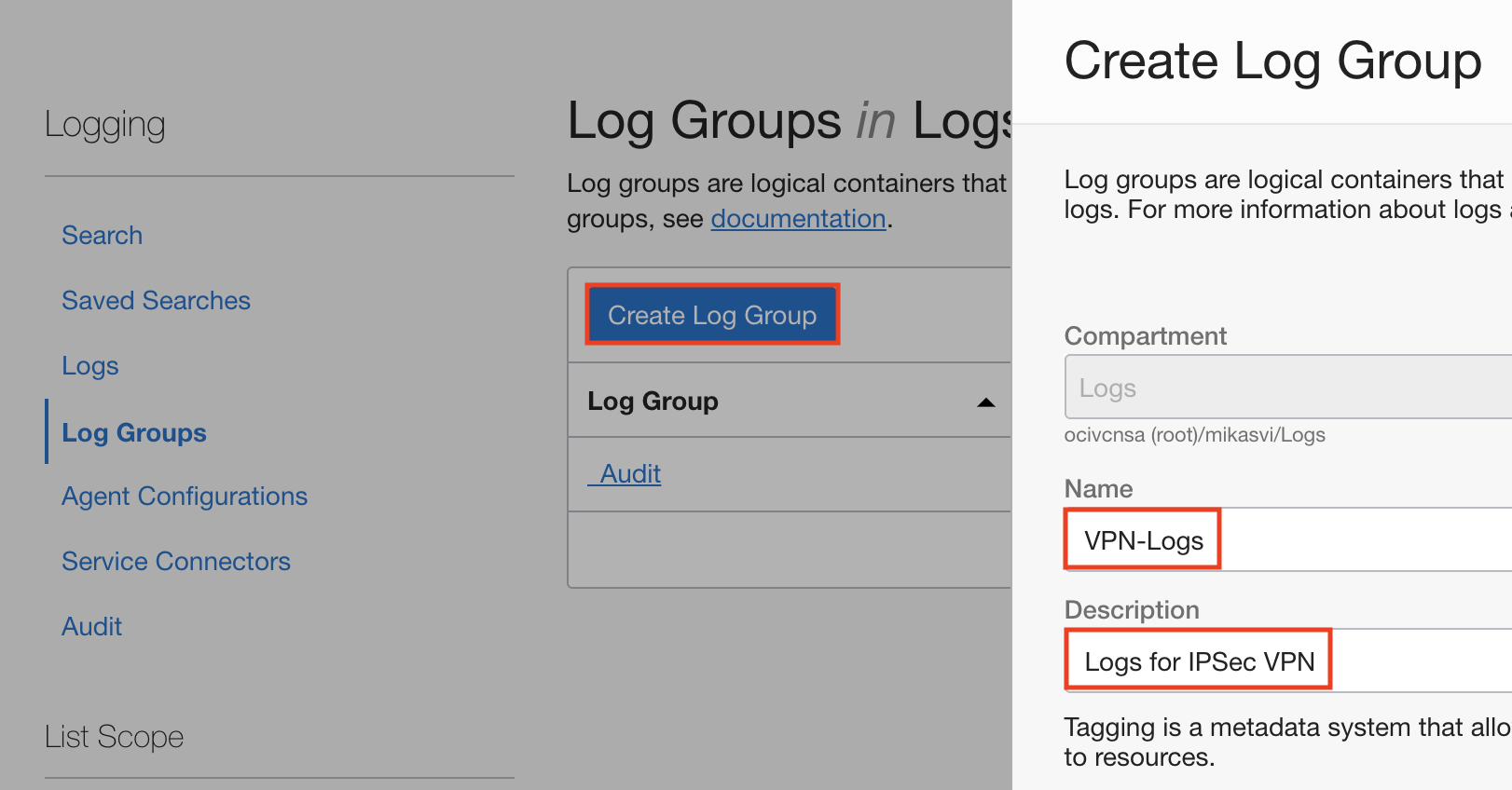
- Create a log group for your VPN logs.
Click Create Log Group. Input a name and description for your log group, then click Create.
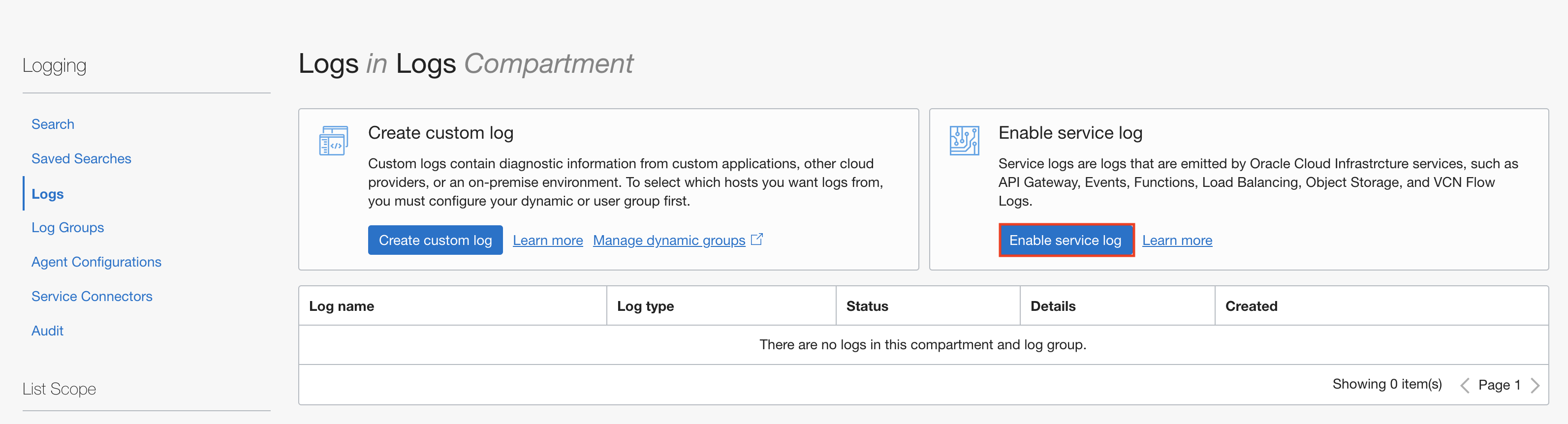
- Enable VPN logging for your IPSec Connections.
Under the Logs menu, click Enable service log.
Select the VPN Connect service, select the relevant IPSec connections under Service, IPSec Tunnel Logs for the Resource, and provide a name for your log. If you have multiple groups, you may need to expand Advanced Options to select the previously created log group.

That completes the VPN logging configuration. After a short time your logs will be available for viewing within the OCI Console.
You can also enable VPN logs for each IPSec connection by selecting the Logs tab under the relevant IPSec connection.

View VPN Logs
You can view and search through your VPN logs with the viewer provided by the Oracle Cloud Infrastructure Logging Service. To access your VPN logs, navigate to Logging and select Search. Here you will be able to view your IPSec connection logs for necessary information such as tunnel state and negotiation. For more information on how to filter these messages and the type of information provided, see Logging details for VPN Connect.

Conclusion
Thank you for your interest in the multiple encryption domain support for policy-based IPSec VPNs and VPN logging features in OCI. This blog details how both policy-based IPSec VPNs and VPN logging are configured in Oracle Cloud Infrastructure. We encourage you to read more about this feature in the available documentation and provide any product feedback that you have in the comments.
