We’re pleased to announce that Oracle Functions service now supports the ability to sign and verify your container image and scan it for vulnerabilities. Signing ensures the use of trusted images free from unauthorized alterations, and scanning provides visibility into potential vulnerabilities inside images. Together, these features enhance the security posture of serverless applications.
Oracle Cloud Infrastructure (OCI) Functions is a serverless functions-as-a-service platform that lets you create, run, and scale business logic without managing any infrastructure. Functions are created using container images and run as Docker containers. Oracle Functions service is secure by design, so image security is of paramount importance to Functions.
Functions image signing
Container image signature verification is an important container security standard and best practice recommendation from OWASP, NIST, and several others. It ensures the authenticity and integrity of container images. Image signature verification ensures that the image used at runtime is the same image that was published and hasn’t been tampered with. So, it helps prevent potential man-in-the-middle attacks.
With image signing, Functions administrators define policies that mandate image signature verification. Developers can easily sign function images, and the Functions service enforces these policies and validates signatures during function creation, update, and invocation. This validation ensures that the function image deployed by the developer serves function invocation requests without any unauthorized modification
You can sign your function images in the OCI Registry using an asymmetric master encryption key from the OCI Vault. You can view image signatures in the OCI Registry and verify that the signatures haven’t changed, ensuring that the integrity of the image isn’t compromised.
You can enable signature verification at the Functions application level and select the master encryption key used to sign images. This signature verification policy allows the creation, update, or invocation of functions using images signed with this master encryption key only. The policy ensures that functions with unsigned images or images signed by a different encryption key can’t be created, updated, or invoked.
Functions image scanning
Functions images are stored inside repositories in the OCI Registry. You can now use the OCI Registry to enable scanning of function image repositories and view scan results. When repository scanning is enabled, the OCI Vulnerability Scanning service scans the function images pushed into the repository for security vulnerabilities published in the Common Vulnerabilities and Exposures (CVE) database. Repositories with scanning enabled are automatically rescanned when new vulnerabilities are added to the list of threats. In the scan results, you can see a list of potential vulnerabilities identified with the vulnerability description, risk level, and a link to the CVE database.
Usage
Functions image signing and scanning are optional but recommended steps in the function build and deployment process.
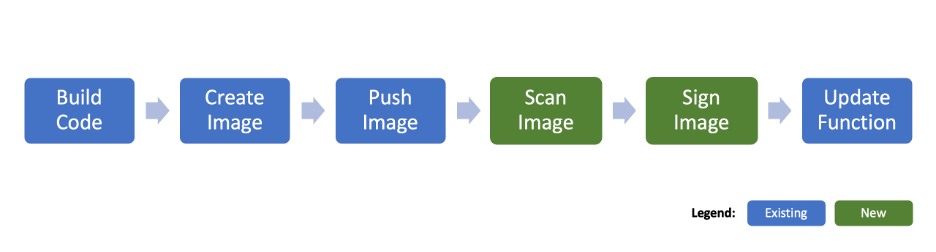
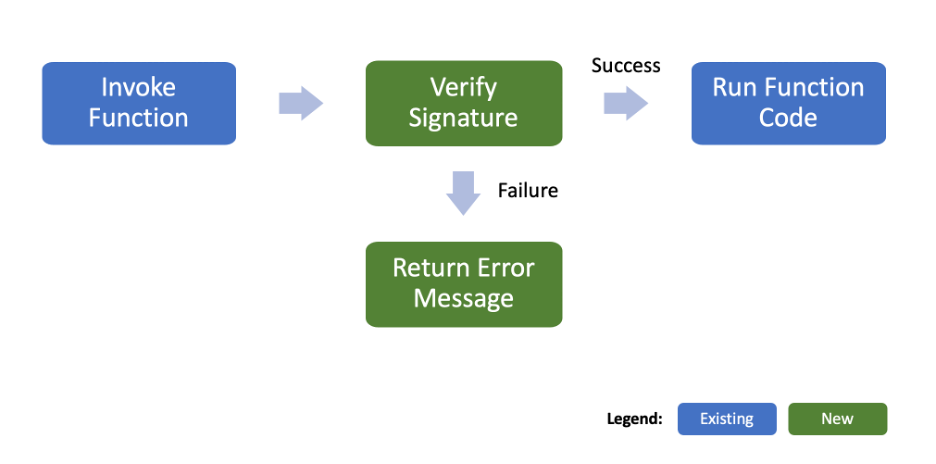
The Functions service enforces signatures during the function invocation stage.
Next steps
To learn more about these features, see Functions image signing and Functions image scanning.
To get started with Oracle Functions, see the Quick Start guide, samples repo, and documentation. If you haven’t tried Oracle Cloud Infrastructure yet, try it for free today.
