OCI Cache is a native service that offers fully managed Valkey and Redis ecosystems. The service frees you from the routine management tasks of creating and managing the cluster, applying OS and security patches or handling node failures. OCI Cache is compatible with the interfaces of Valkey and Redis software engines so you can easily migrate existing applications from self-managed clusters to OCI Cache, thus allowing your teams to focus on the core business instead of operational overheads. Learn more about the OCI Cache here.
Our customers have large and complex applications that cater to their end customer needs. Such applications are designed to efficiently isolate data for each customer in their shared data stores, and they need to extend this isolation to data in cache as well. For example, application roles may be assigned based on departments within the organization (Finance, HR, Training etc), or roles may be assigned based on clients connecting to development, test, pre-production and production environments. And customers need a way to grant permissions like access to specific keyspaces or commands based on the roles.
To support our customers, we’re now introducing Valkey and Redis Access Control Lists (ACLs) in OCI Cache. This feature helps users and clients establish secure access to the cache through OCI Cache users with defined permissions.
Create OCI Cache Users
OCI Cache facilitates access control lists via OCI Cache users. You can create one or more users in the service with pre-defined permissions and associate them to one or more cache clusters. User authentication can be based on either passwords or IAM based tokens, and authorization is specified via access strings during user creation. Get started with just two simple steps to secure access to your cache
- Create one or more OCI Cache users
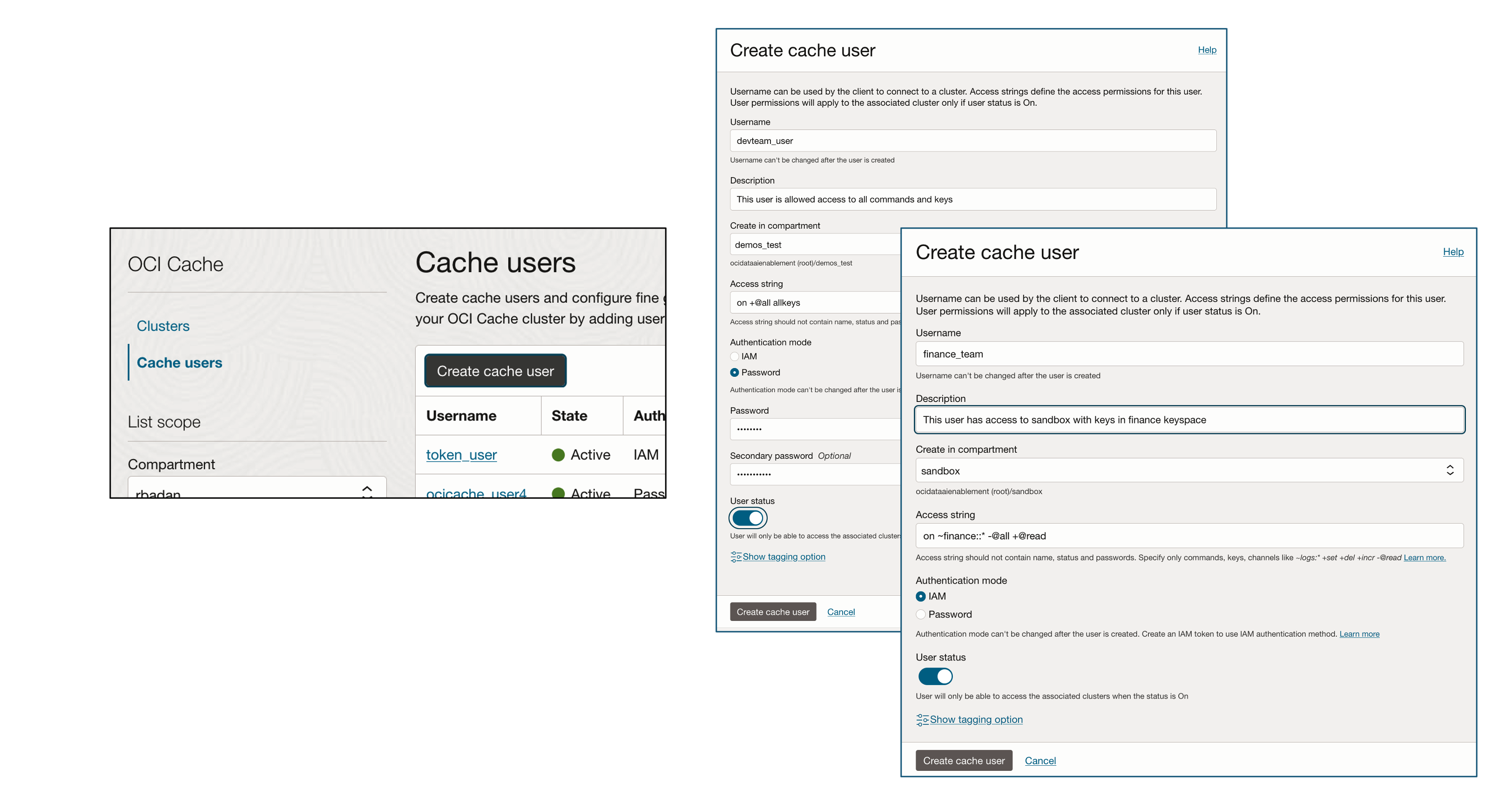
Figure 1: New Create Cache Users interface - Add the users to the cache cluster

Figure 2: Add users to your clusters interface
This way, access to the cache cluster is limited only to the users associated with the cluster, and access privileges are limited to their assigned permissions.
Users must be in Active state to connect to the associated clusters. If you want to temporarily disallow a user access to all associated clusters then set the status to Inactive by editing the Cache User and disabling the User status.
Authentication – passwords or IAM tokens
While creating a user you may choose password or IAM token to authenticate the user.
If you choose password authentication, you can set up to two passwords for a user. The second password is optional and is used during password rotation to seamlessly update the new password on the cluster nodes.
If you choose IAM based authentication, you will need
1. Set appropriate IAM policies to allow an IAM user to access the cache
2. Create an IAM token for the user every time they connect to the cache
See the section IAM Authentication for OCI Cache in the documentation for more details on how to generate and use IAM tokens. You cannot change authentication type after the user is created.
Authorization – Access Control Lists
OCI Cache allows you to grant users permissions to specific commands and/or keys in the cache with the help of access control strings.
Some examples of access string are
on +@all allkeys
Active user has access to all commands and keys
on +@read ~*
Active user has access to only read command
on ~hr_dept::* -@all +@read
Active user has access to read command for all keys with the prefix hr_dept
You can find details on ACL strings in the Valkey and Redis documentation.
default user
Every cluster created in OCI Cache will continue to have the default user, with full access (except certain admin commands) to the cache without any authentication needed. The OCI Cache users feature gives you the choice to override the default user’s permissions by creating a new user with the same name, default, and assigning updated permissions via an access control string to the new user. Additionally, you can secure this user with a password. When you associate the new default user with a cluster, the out-of-the-box default user is no longer effective.
Key Take Aways
OCI Cache now enables you to secure access to the cache by creating users and defining access control rules for them. This new feature not only improves security by adding authentication for clients and applications to connect to the cache but also helps ensure that data integrity is maintained by granting appropriate access permissions.
OCI Cache now provides you flexibility and control to align with your desired security posture and security controls – Private Endpoints with TLS enabled by default for secure network access, support for NSG to isolate clusters in VCNs and Authentication and Authorization including OCI IAM integration to provide fine grained access control for your applications accessing OCI Cache.
Get started today and sign up to our Always free OCI account

