Announcing OCI Private DNS Response Logging
Domain Name System (DNS) is an often overlooked, but critical component of any successful cloud deployment. Oracle Cloud Infrastructure (OCI) is excited to announce that today we are launching Private DNS Response Logging.
DNS query responses help manage the complexity of networking by replacing IP addresses with more familiar names, such as www.oracle.com. As resources in your OCI environment make queries to the Virtual Cloud Network (VCN) DNS resolver endpoints, this feature helps by recording the queries and responses received along with some associated telemetry data.
Why do we need DNS response logging?
When application issues occur, DNS is often one of the first things that should be investigated. Whether DNS gets incorrectly blamed or quickly overlooked, proper DNS investigation can prove essential in effective troubleshooting. If you’ve heard the phrase “pictures or it didn’t happen”, OCI is now providing you with “pictures of your DNS” to provide visibility into DNS resolution for your cloud resources.
To get this level of visibility in the past, you may have had to enable DNS client logging on the instances or possibly open a ticket with Oracle Support to get access to the DNS logs. Unfortunately, those solutions could be incomplete or time-consuming. This new DNS response logging feature will help with investigation of DNS query responses to help identify issues and potentially decrease time to resolution.
Use cases
There are many reasons why you might want to have DNS response log data, such as threat hunting, security monitoring, troubleshooting, audit and compliance, utilization and statistical monitoring to name a few. Two of the most common use cases would be security and troubleshooting.
DNS logs for security threat hunting
One common use of DNS log analysis is in security threat hunting. DNS response logs can be used in conjunction with DNS threat data to help identify indicators of compromise (IOCs). DNS logging can help identify some security issues, such as:
- Finding man-in-the-middle (MITM) or DNS response hijacking
- Identifying DNS tunneling to hide Command and Control (C2) communications
- Tracking indications of C2 communications using dynamic resolution with malware autogenerated domain names
- Looking for DNS activity indicating communications with risky domains or deceptive domains used in phishing attacks
DNS logs in troubleshooting
Whether DNS is the actual problem or not, DNS should get early consideration in troubleshooting application performance and stability. It’s not uncommon to have an issue that looks like a network outage that is, instead, the result of DNS resolver misconfiguration or lengthy DNS query response times. For example, if an application is dependent on a server referenced as “api.sourcedata.com” and the “sourcedata.com” domain servers are experiencing problems, it might look like there’s a network issue. A quick review of DNS response logs might show that all responses for that domain return NXDOMAIN (or Non-Existent Domain). That being the case, network troubleshooting may stop, as the target of the troubleshooting will now move to the DNS responses from that domain.
How to work with Private DNS Response Logs
Key capabilities
Enabling private DNS response logs will allow you to capture and inspect records related to DNS queries made through the private DNS resolver configured within a Virtual Cloud Network (VCN) in your OCI tenancy. This allows you to browse and search through DNS responses based on any data in the record, such as error codes, response codes, latency, etc.
Enabling Private DNS Response Logging in the OCI Console
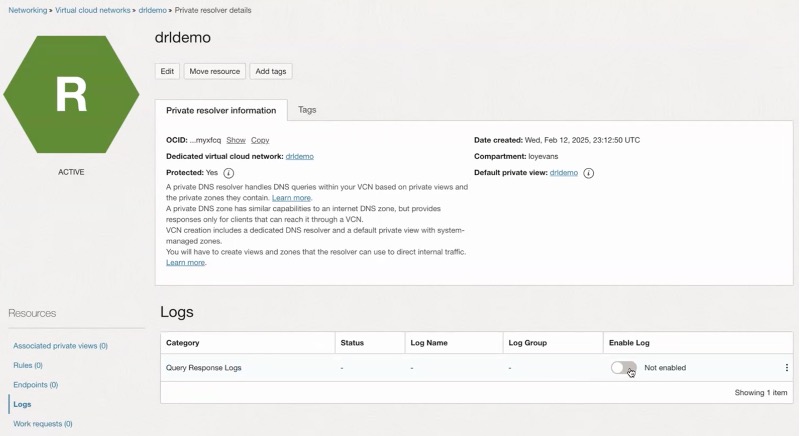
To enable DNS response logs, navigate to virtual cloud networks in the console and select the VCN where you want to enable DNS response logging. Once you are on the VCN details page, click the DNS Resolver, which is down at the bottom of the details pane.
Once you are on the DNS Resolver page, in the Resources section, click on Logs. Here you will see an entry for Query Response Logs. The entry will have a toggle switch that is set to “Not enabled” by default.
Click the “Enable Log” toggle switch. Next you will see a pop up allowing you to fill in the details of the log settings, then click Enable log. Shortly after you will see that the logs have been activated. As this enablement is a toggle, you can also disable the logging for that resolver at any time.
Exploring the DNS response logs
After the logs have been enabled, you can start looking through the data. In the console, navigate to Observability & Management -> Logging -> Logs. You will see a list of logs, including the DNS response logs. Click on the logs to begin log exploration.
The initial Explore Log screen will allow you to look at the logs in a histogram representation that you can sort through based on newest or oldest, and you can filter by time. Default settings show logs for the most recent 5 minutes in a list of DNS responses that can be expanded to view each record’s data.
The following example was a DNS query from an instance with the IP address of 10.100.0.59 (source field) that requested “isc.org” (qname field) and received a response with four A records, “151.101.66.271, 151.101.194.217, 151.101.130.217 and 151.101.2.217” (answer field) with a response latency of 95 milliseconds (latency field).
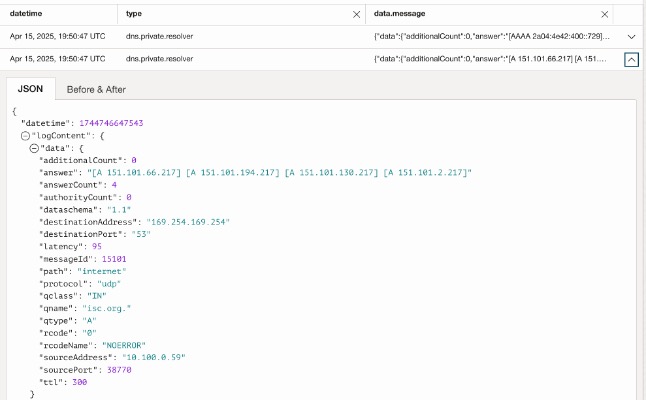
If you want to do a more advanced investigation, click on Actions -> Explore with Log Search. Log search allows you to filter down to specific elements of the data that you are looking for. For example, you can search for specific domains, fully qualified domain names, response codes (like NXDOMAIN), error codes, or even queries like “show me responses where latency is > 100” (note that latency is expressed in # of milliseconds it took to receive the response).
Learn more
To learn more, please see the OCI documentation on private DNS logging.
All OCI logging facilities can be connected to Service Connector Hub and OCI Logging Analytics. Check out these blogs on for more information about how these could be used with DNS response logging:
