Introduction
Confidential computing refers to a combination of hardware and software security features built into the CPU virtualization environment that protect data while it is being processed (data in use). It enables sensitive workloads to run within securely isolated spaces known as Trusted Execution Environments (TEEs). These TEEs use embedded encryption keys and attestation mechanisms designed to ensure that only authorized application code can access protected data. Even users with administrative privileges cannot access the contents of a TEE, keeping in-use data secure from unauthorized access.
The Oracle Cloud Infrastructure (OCI) Confidential Computing solution is available on OCI VM instances powered by second-generation and third-generation AMD EPYC processors. OCI Confidential Computing-enabled VMs use AMD Secure Encrypted Virtualization (SEV) technology, while OCI Confidential Computing bare metal instances use AMD Transparent Secure Memory Encryption (TSME) technology. Currently, OCI Confidential Computing supports different shapes including E4 Flex VMs, while bare metal configurations support E5 series CPUs. In this blog, we will focus on E4 Flex VMs only to measure performance impact of enabling OCI Confidential Computing.
OCI Confidential Computing:
- Enhances security by creating Trusted Execution Environments (TEEs) that are isolated from applications, other virtual machines on the same bare metal host, the hypervisor, and other OCI tenants.
- Requires no change to the application to enable Confidential VMs.
- Provides high performance with the strong security standards. Many applications experience little to no performance impact with OCI Confidential Computing enabled.
This blog shares the outcome of a benchmarking study focused on evaluating the impact of enabling OCI Confidential Computing on OCI VMs. As cloud adoption increases for sensitive and regulated workloads, security expectations have shifted from not only protecting data at rest and in transit but also protecting data in use. OCI Confidential Computing, powered by AMD SEV, delivers hardware-enforced memory encryption and runtime isolation. While these features offer robust security, they bring additional protection layers between the workload and the hardware.
There is a common concern that adding a security layer often comes with performance penalties such as latency, memory and CPU overhead. Encryption and isolation mechanisms typically involve extra memory translation steps or access control checks that can impact I/O throughput, memory bandwidth, and instruction execution.
To understand the practical effects of these trade-offs, this study compared two identical OCI VMs – one with OCI Confidential Computing enabled, the other one standard. The study focused on a variety of representative workloads including CPU benchmarks, memory stress tests, disk I/O, in-memory data access and relational database transactions. We used most common open-source benchmarking tools to measure workload benchmarks.
The objective is to capture measurable differences if any occurs in performance and to understand if increased security in environment maintain efficiency for real world cloud applications and use cases.
Benchmarking Infrastructure Setup
To assess the performance impact accurately and fairly, we have provisioned two identical virtual machine instances, configured with the same number of OCPUs and memory in the same region with details show in table below.
- Standard VM – without OCI Confidential Computing enabled
- Confidential VM – with OCI Confidential Computing enabled (AMD-SEV)
| VM Name and Type |
Shape |
OS |
Region |
OCPU |
Memory |
| confcomputeno – OCI Confidential Computing Disabled |
VM.Standard.E4.Flex |
OL8 |
FRA |
4 |
16 |
| confcomputeyes – OCI Confidential Computing Enabled |
VM.Standard.E4.Flex |
OL8 |
FRA |
4 |
16 |
The following images show Instance Information and Security Configuration of VMs for OCI console.
Workloads Tested
We used a set of standardized and representative benchmarking tools across different workload types as shown in the table below:
| Workload Type |
Tool Used |
Description |
| Web Server |
wrk2 |
HTTP load testing tool simulating web traffic |
| In-Memory Database |
redis-benchmark |
Measures GET/SET performance |
| Relational Database |
pgbench |
PostgreSQL transactional throughput benchmark |
| CPU/Memory |
sysbench |
Prime number calculations |
| Disk I/O |
fio |
Random write performance simulation |
Web Server Benchmark with NGINX and wrk2
To evaluate the impact of enabling Confidential Computing on web server performance, we conducted HTTP benchmarking using the wrk2 tool on nginx web server. Nginx, known for its high performance and flexibility, is used in a variety of customer scenarios. Primarily, it acts as a web server, reverse proxy, and load balancer, but also excels in content caching, API gateways, and microservices architectures. OCI VMs in both cases run NGINX configured to serve static content using default settings. The table below shows the detail of wrk2 test parameters
| Parameter |
Value |
| Load Generator |
wrk2 |
| Target Server |
nginx (default config) |
| Test Duration |
60 seconds |
| Threads |
4 |
| Connections |
100 |
| Request Rate |
2000 requests/sec |
| File Served |
index.html (static) |
After executing the given commands, we have got the results from both VMs as given in the table and chart with imported data set below.
| Metric |
Standard VM |
Confidential VM |
| Requests/sec |
1998.70 |
1998.69 |
| Avg Latency |
774.50 µs |
775.01 µs |
| Max Latency |
2.46 ms |
3.53 ms |
| Transfer/sec |
7.98 MB |
7.98 MB |
| Total Requests |
119,924 |
119,924 |
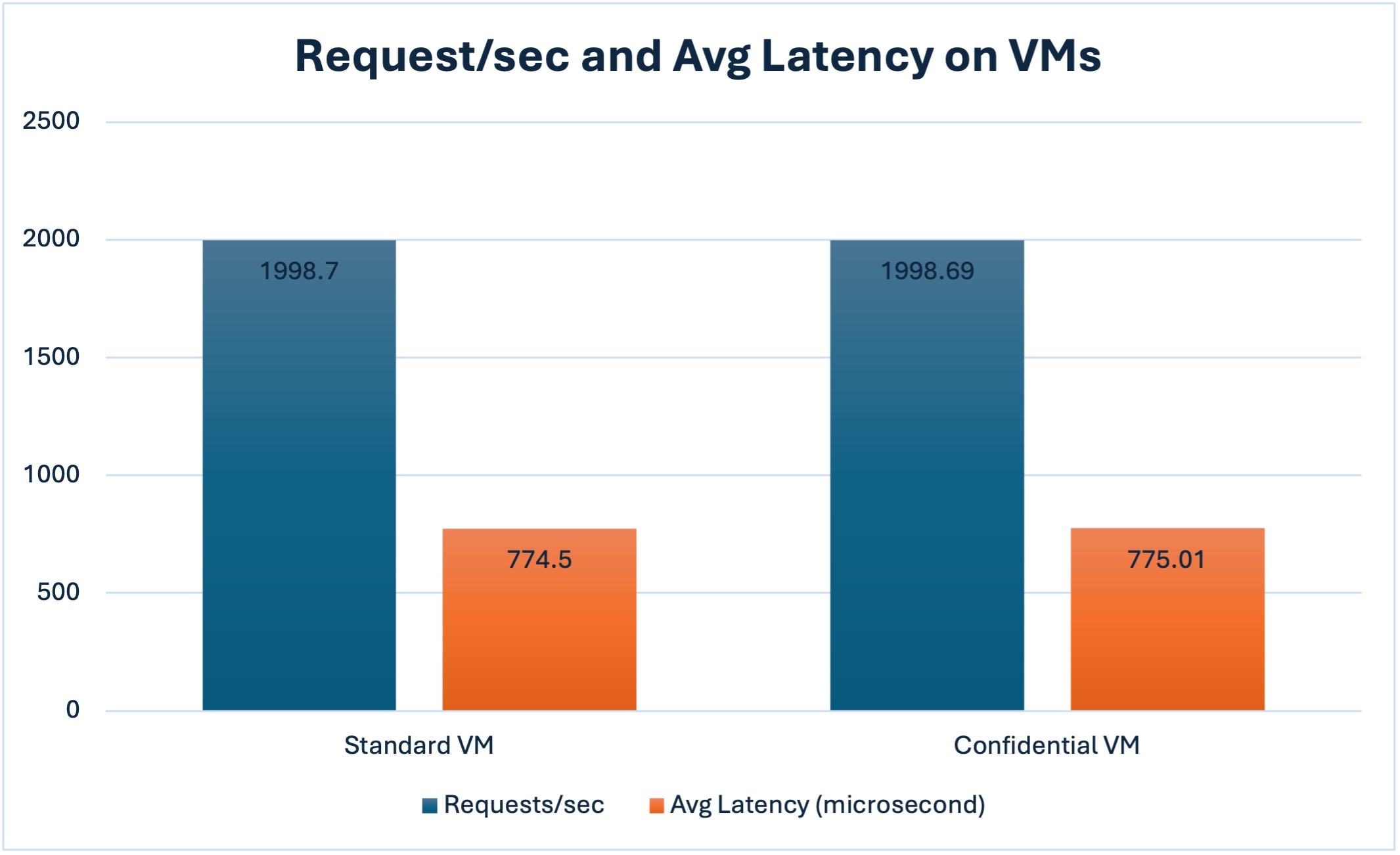
- Throughput is nearly identical. Both VMs sustained ~2000 requests/sec.
- Average latency remained well below 1 ms.
- Max latency increased slightly on the Confidential Computing-enabled VM, which is expected due to enabled security overhead.
- Total request volume and transfer rate remained consistent across tests.
- These results confirm the suitability of Confidential VMs for serving high-volume web workloads with minimal overhead and added security posture.
Redis Memory Benchmark
We used the built-in Redis-benchmark tool to measure Redis performance on both a Standard VM and a Confidential VM on OCI. Redis is a high-performance, in-memory data store designed to manage key-value data efficiently. It excels in scenarios where low-latency access is critical, such as real-time analytics, caching, and message brokering. By keeping data in memory rather than relying on disk storage, Redis enables rapid read and write operations, making it a good choice for applications that demand quick data retrieval and real-time responsiveness.
The goal was to evaluate whether enabling OCI Confidential Computing impacts in-memory database performance. The table below shows the detail of Redis-benchmark test parameters which we used to measure throughput and latency.
| Parameter | Value |
|---|---|
| Tool |
redis-benchmark |
| Total Requests |
100,000 |
| Concurrency |
50 parallel clients |
The table below shows the detail of Redis benchmark test parameters. We have reached the results below after redis benchmark test on both VMs.
| Metric | Standard VM | Confidential VM |
|---|---|---|
| SET Throughput |
68,119.89 req/sec |
66,755.67 req/sec |
| GET Throughput |
68,073.52 req/sec |
66,225.16 req/sec |
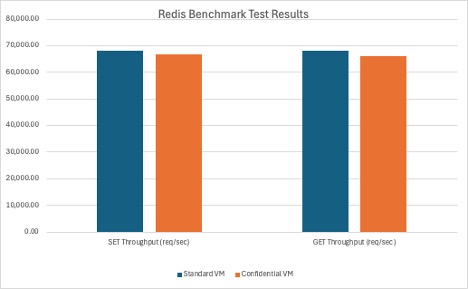
- The Standard VM performed ~2–3% better in both SET and GET throughput, which is within the margin of normal variation for Redis workloads.
- p99 latency remained excellent and nearly identical on both VMs.
- While encryption is active in Confidential VMs, the performance impact remains negligible even for high-throughput, in-memory workloads like Redis.
- The slight difference in throughput does not compromise usability, especially given the enhanced security of OCI Confidential Computing.
Sysbench Benchmark
We used Sysbench to test CPU processing power and memory throughput on Oracle Cloud Infrastructure Flex VMs. Sysbench is a modular, cross-platform benchmarking tool designed to evaluate the performance of various system components such as CPU, memory, disk I/O, threads, and database performance. It is particularly helpful in performance testing and system tuning efforts, especially in pre-deployment stages of VMs on cloud platforms. Customers often use Sysbench in their environments like cloud vs on premises VM testing, capacity planning, and tuning infrastructure to match workload demands before going into production. It provides both quick insights and repeatable load patterns for deeper analysis. Our goal was to check whether OCI Confidential Computing affects performance due to memory encryption and runtime isolation. We used a set of parameter definition as we list in the table below.
| Parameter | Value |
|---|---|
| Tool |
Sysbench 1.1.0 (built from source) |
| CPU Test |
–threads=4 –cpu-max-prime=20000 |
| Memory Test |
–memory-total-size=1G –threads=4 |
Here are the results after conducting given tests on both VMs.
| Subsystem | Metric | Standard VM | Confidential VM |
|---|---|---|---|
| CPU |
Events/sec |
5706.40 |
5720.66 |
| CPU |
Avg Latency (ms) |
0.70 |
0.70 |
| Memory |
Ops/sec |
13.84M |
13.38M |
| Memory |
Throughput (MiB/sec) |
13,516.37 |
13,062.04 |
| Memory |
Max Latency (ms) |
0.02 |
0.02 |
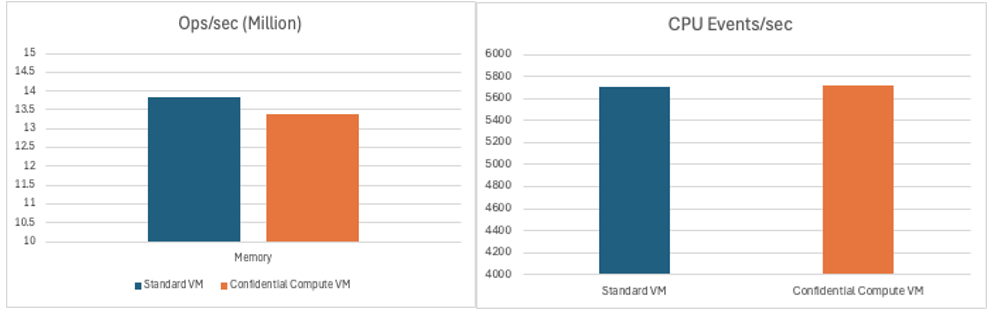
- Both VMs performed equally well in raw compute power. No noticeable difference in latency or speed.
- The Standard VM had a slight edge in memory speed, but both delivered excellent performance.
- OCI Confidential Computing enables secure execution without comprising practical performance which is ideal for sensitive workloads in security manner.
FIO Random Write Benchmark
We used the FIO (Flexible I/O Tester) tool to benchmark random write IOPS performance on OCI VMs. FIO can simulate a wide range of I/O patterns, including sequential and random reads/writes, across different block sizes and job concurrency levels. It has been widely used by customers to evaluate how a VM or storage volume performs under specific I/O stress. Many customers and storage providers use FIO officially to choose right sizing of disk spaces and disk types. It helps to validate HDD, SSD, NVMe or block storage performance before deployment. Our test compared a Standard VM with a Confidential VM, both using a 1GiB test file on the block volume. We used FIO parameters which are given below:
| Parameter | Value |
|---|---|
| Tool |
fio 3.19 |
| Mode |
Random write (–rw=randwrite) |
| Block size |
4 KiB |
| Total file size |
1 GiB |
| Number of jobs |
4 |
| Runtime |
60 seconds |
| IO Engine |
psync |
| Volume type |
Block volume |
| Directory |
/mnt/testdisk |
After execution of test commands, we got the results from both VM as shown below:
| Metric | Standard VM | Confidential VM |
|---|---|---|
| Write IOPS |
12,600 |
12,500 |
| Bandwidth (MiB/s) |
49.3 |
48.6 |
| Avg Latency (µs) |
127.1 |
148.8 |
| p99 Latency (µs) |
~11 |
~12 |
| Max Latency (µs) (99.99th) |
~38,500 |
~42,700 |
| CPU Usage (sys %) |
1.68% |
1.63% |
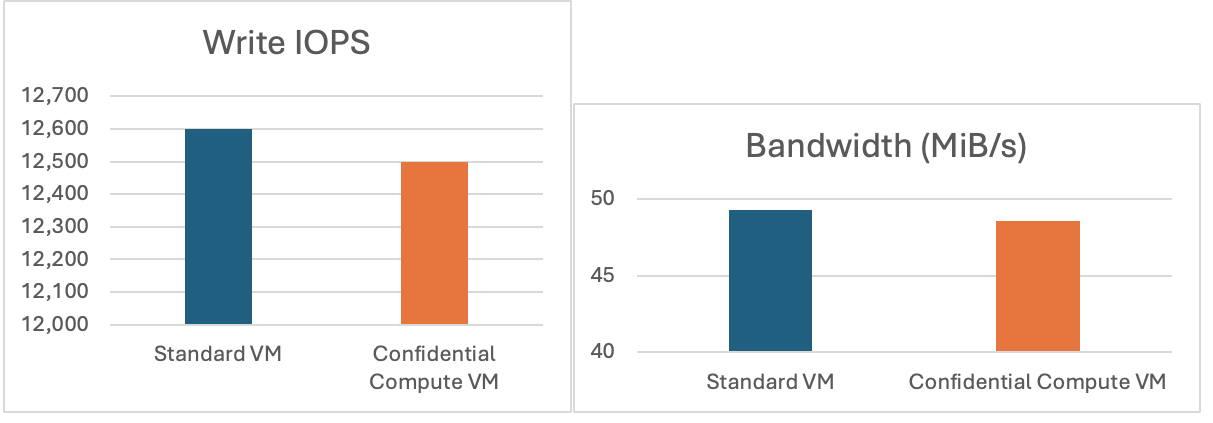
- Both VMs show very similar IOPS and bandwidth. The Standard VM is just a bit faster, but the difference is not large.
- The average and 99.99th percentile latency are slightly higher on the Confidential VM, but this is expected due to memory encryption overhead.
- CPU usage and context switches are also very close, showing both systems are working under similar loads.
- The small latency increase is expected and acceptable for most real-world applications, especially given the extra security benefits.
PostgreSQL pgbench Benchmark
We performed PostgreSQL benchmarking using the pgbench tool to evaluate the performance impact of enabling Confidential Computing on OCI Flex VM shapes. Pgbench is an official benchmarking test tool for PostgreSQL which is a powerful, open source, relational database system. It is being used across various industries including financial systems, analytic platforms, web and mobile applications. It runs the same sequence of SQL commands over and over, possibly in multiple concurrent database sessions, and then calculates the average transaction rate (transactions per second) and latency. In our study, two identical VMs were tested, one Standard VM and one with OCI Confidential Computing enabled, using the same PostgreSQL configuration and load conditions. The table below shows the parameters used during the tests.
| Parameter | Value |
|---|---|
| Tool |
pgbench (PostgreSQL built-in) |
| Scaling factor |
50 |
| Clients |
10 |
| Threads |
4 |
| Duration |
60 & 120 seconds |
| Query mode |
Simple |
| Database |
Pgbenchdb |
We have received results from test cases conducted over different durations, as shown in the table below.
| Duration | Metric | Standard VM | Confidential VM |
|---|---|---|---|
| 120s |
TPS |
3234.2 |
3076.6 |
| 120s |
Latency (avg) |
3.092 ms |
3.250 ms |
| 60s |
TPS |
3393.5 |
3116.3 |
| 60s |
Latency (avg) |
2.947 ms |
3.209 ms |
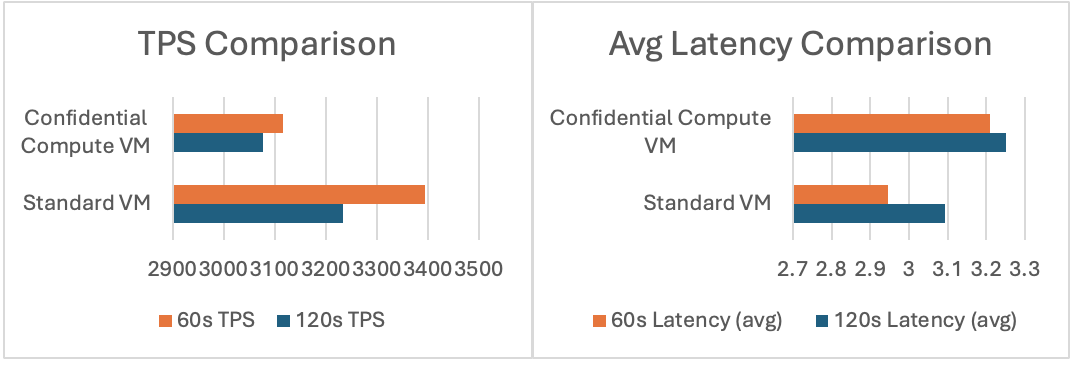
- The Standard VM outperformed the Confidential VM by approximately 7% in terms of transactions per second. This is the biggest gap in all tests wide.
- Average latency was slightly lower on the Standard VM, showing marginally faster response times.
- Both VMs demonstrated consistent behavior across the 60s and 120s test durations.
- The Confidential VM showed a small but consistent overhead in both throughput and latency.
- The performance difference is minor and unlikely to impact most real-world database applications.
Conclusion
After conducting comprehensive benchmarking across five distinct workload categories including nginx (web server), Redis (in-memory cache), Sysbench (CPU/memory), FIO (disk I/O), and pgbench (PostgreSQL OLTP), we conclude that OCI Confidential Computing VMs deliver:
| Test Type | Metric | Standard VM | Confidential VM | Difference / Notes |
|---|---|---|---|---|
| Web Server |
Throughput (RPS) |
1998.70 |
1998.69 |
Identical performance |
| Redis |
SET / GET Throughput |
68,119 / 68,073 |
66,755 / 66,225 |
~2–3% lower on Confidential VM |
| Sysbench CPU |
Events/sec |
5,706 |
5,720 |
Nearly identical |
| Sysbench Memory |
MiB/sec / Ops/sec |
13,516 / 13.84M |
13,062 / 13.38M |
~3–4% lower on Confidential VM |
| FIO Disk |
Write Throughput (MiB/s) |
49.3 |
48.6 |
~1–2% lower on Confidential VM |
| pgBench |
TPS (avg across runs) |
~3,314 |
~3,096 |
~6.6% lower TPS on Confidential VM |
- Web server and CPU performance were identical between Standard and Confidential VMs. This confirms that CPU bound, and stateless workloads incur no overhead from memory encryption or AMD SEV isolation.
- Redis benchmark, representative of high-throughput, low-latency in-memory operations, showed sub-3% variance in throughput. The performance delta can be tolerated and demonstrates that encrypted memory access is efficiently handled by the AMD EPYC architecture.
- Memory and Disk (Sysbench & FIO) results showed a slight decrease in throughput on Confidential VMs. This is likely attributable to the added encryption and address translation layers introduced by AMD-SEV. Additionally, latency remained low and negligible, confirming that OCI Confidential Computing can handle memory intensive workloads with minimal performance cost.
- pgbench PostgreSQL test was the most sensitive test, with a ~6–7% lower TPS under OCI Confidential Computing. This suggests that in write heavy transactional databases, memory encryption may introduce slight overhead under sustained concurrency. However, the performance remained stable and reliable, even with AMD SEV features are on board.
OCI Confidential Computing on OCI E4 Flex shapes delivers near-parity performance compared to Standard VMs across compute, memory, storage, and application-layer tests. Despite running with full memory encryption and runtime isolation via AMD SEV, the VMs maintain consistently high throughput and low latency. This demonstrates that OCI Confidential Computing is production ready and suitable for security sensitive workloads without compromising on performance.
Explore More
- Confidential Computing page on OCI: https://docs.oracle.com/en-us/iaas/Content/Compute/References/confidential_compute.htm
- A-Team Chronicles on Confidential Computing: https://www.ateam-oracle.com/post/ciso-perspectives-confidential-compute-protecting-data-inprocess
- Confidential Computing allows customers to enable confidential virtual machines (VMs) with the help of AMD Infinity Guard features
- Klaudia Warner blog page on Confidential Computing: https://blogs.oracle.com/cloud-infrastructure/post/protect-data-in-use-with-confidential-computing
- AMD Memory Encryption White Paper – https://www.amd.com/content/dam/amd/en/documents/epyc-business-docs/white-papers/memory-encryption-white-paper.pdf
- AMD SEV Developer Central – https://www.amd.com/en/developer/sev.html
- AMD EPYC – Google Cloud Performance Brief – https://www.amd.com/content/dam/amd/en/documents/epyc-business-docs/performance-briefs/confidential-computing-performance-sev-snp-google-n2d-instances.pdf