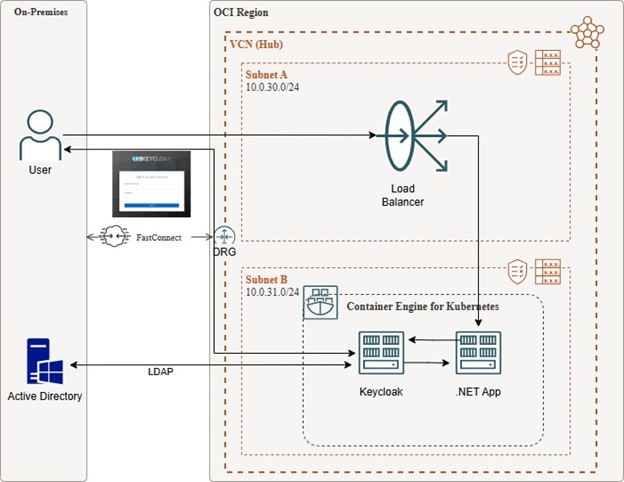
Introduction
Did you know you can deploy .NET applications in Oracle Cloud Infrastructure Kubernetes Engine? And even more, you can use your on-premises Active Directory!
What is Keycloak?
Keycloak is an open-source identity and access management solution for modern applications and services, built on top of industry security standard protocols. It provides user federation, strong authentication, user management, fine-grained authorization, and more.
How can we use Keycloak to authenticate users with on-premises Active Directory on our .NET applications on OKE?
Keycloak acts as a bridge between modern cloud applications and traditional enterprise identity systems like Active Directory.
By configuring Keycloak as an OpenID Connect (OIDC) identity provider and linking it to your on-premises AD via LDAP federation, your .NET applications running in OKE can delegate authentication to Keycloak — which securely validates credentials against AD.
With only small changes to your existing .NET applications, you can seamlessly integrate with Keycloak and reuse your existing AD users in the cloud without rewriting your authentication logic from scratch.
Even better, this setup also lays the groundwork for the future modernization of your authentication strategy. Once your apps use Keycloak, you can easily add support for multi-factor authentication (MFA), social logins, or other identity providers — all without changing your application code again.
Example application
To demonstrate this integration, I’ve created a small .NET web application that authenticates users via Keycloak. The application prompts for a username and password and, once authenticated, retrieves and displays the user’s Active Directory group memberships. These groups could then be used to apply different roles or permissions inside the application.
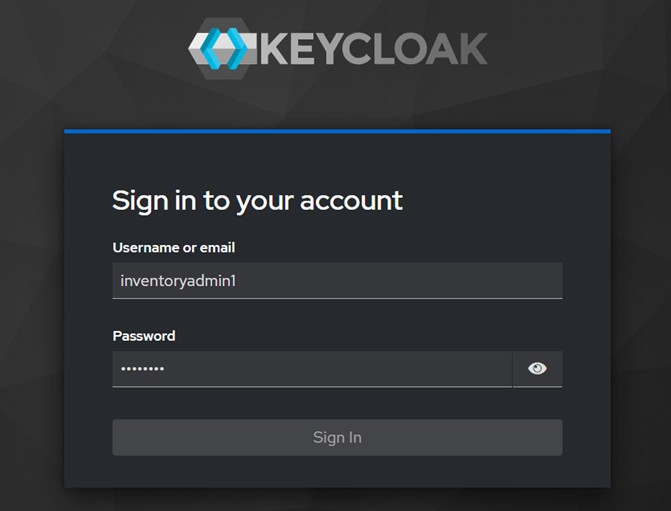
When an unauthenticated user accesses the application, they are redirected to the Keycloak login page, which can be fully customized to match your organization’s branding and design guidelines:
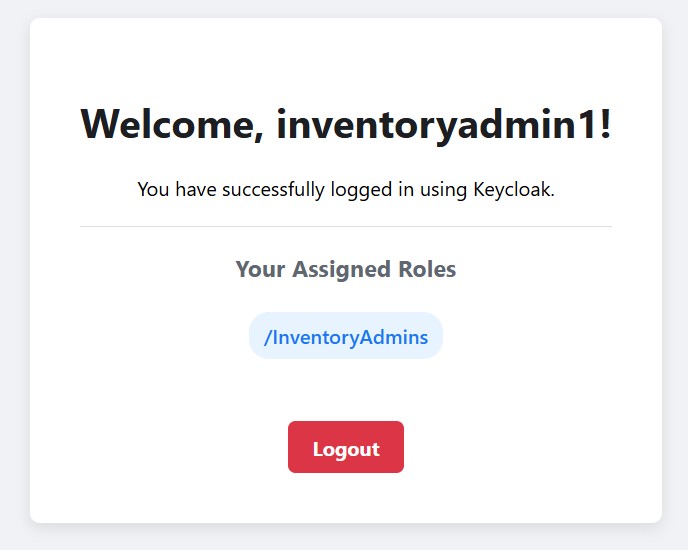
After a successful login, the application receives the user’s profile and group membership information from Keycloak, allowing it to control access and behavior accordingly:
Conclusion
By leveraging Keycloak as a federated identity broker, you can migrate your existing .NET applications to Oracle Kubernetes Engine (OKE) with minimal changes, while still using your on-premises Active Directory for authentication.
This approach not only simplifies the transition to the cloud but also modernizes your authentication strategy. Once integrated with Keycloak, your applications can easily adopt MFA, SSO, and future identity providers without additional code changes.
Useful Links
Oracle Cloud Infrastructure Kubernetes Engine Overview
Keycloak Server Admin – Lightweight Directory Access Protocol (LDAP) and Active Directory
