In today’s dynamic cloud landscape, data protection extends beyond compliance. As encryption requirements evolve, there is growing interest in achieving granular control, operational resilience, and strategic autonomy throughout the encryption lifecycle. This is especially critical in highly regulated sectors, where data sovereignty is not just recommended; it’s essential.
To meet these needs, Oracle is pleased to announce the general availability of the Oracle External Key Management System (EKMS) for Oracle Fusion Cloud Services. With EKMS, you can securely store and manage your encryption keys outside Oracle Cloud, giving you full ownership and control throughout the encryption lifecycle.
Why This Matters: Achieving Unmatched Control in Cloud Encryption
Oracle EKMS transforms cloud data encryption by granting you complete ownership of your encryption keys, empowering you to tailor your strategies to your unique needs. Here’s what you gain:
- Direct Key Ownership: Manage, use, and govern your encryption keys independently, ensuring maximum flexibility and alignment with your policies.
- Immediate Data Control: Instantly disable or revoke your keys (crypto-shredding) for irreversible control over encrypted data access, supporting your compliance or operational requirements.
- Comprehensive Compliance: Natively support standards such as GDPR, HIPAA, and SWIFT, enabling you to meet regulatory requirements while retaining complete oversight.
With Oracle EKMS, you gain the freedom and agility to manage cloud data encryption entirely on your own terms.
What’s Included in This Release
This release introduces new capabilities that give you greater control over how your encryption keys are hosted, associated, and replicated, while ensuring a consistent experience across Fusion environments.
- Support for Externally Hosted Keys
- Integrates with Thales CipherTrust Cloud Key Management (CCKM), part of the Thales CipherTrust Manager suite, enabling you to leverage externally managed keys for greater ownership and operational flexibility.
- Key Association Options
- New Environments: Select an external key during Fusion environment provisioning.
- Existing Environments: Associate an external key after provisioning.
- Cross-Region Replication for External KMS (Disaster Recovery Support)
- Automatically replicate your external vaults and key references to a secondary region, supporting business continuity and enhancing data durability.
- All updates, including key creation, deletion, changes, and movement; in your primary vault are synchronized with the replica.
- Consistent Fusion User Experience
- EKMS offers the same intuitive workflows and behaviors as Virtual Vault and Private Vault solutions, ensuring a unified Bring Your Own Key (BYOK) and Hold Your Own Key (HYOK) management experience across all vault types.
What You Need to Know: Subscription & Responsibilities
Using EKMS for Fusion services involves specific subscription requirements and operational responsibilities to help ensure reliable encryption functionality and business continuity.
- A Break Glass subscription is required to manage encryption keys for your Oracle Fusion Cloud databases with EKMS. The service is billed separately through Oracle Universal Credits.
- You are responsible for the availability of your keys. If access to your keys is lost (due to disablement or network disruptions), key management operations; and therefore Fusion service availability, may be affected.
- While Oracle provides cross-region replication for vaults and key references, you are responsible for replicating externally managed keys that are hosted on-premises.
Deployment Overview: An Example
A typical configuration is as follows:
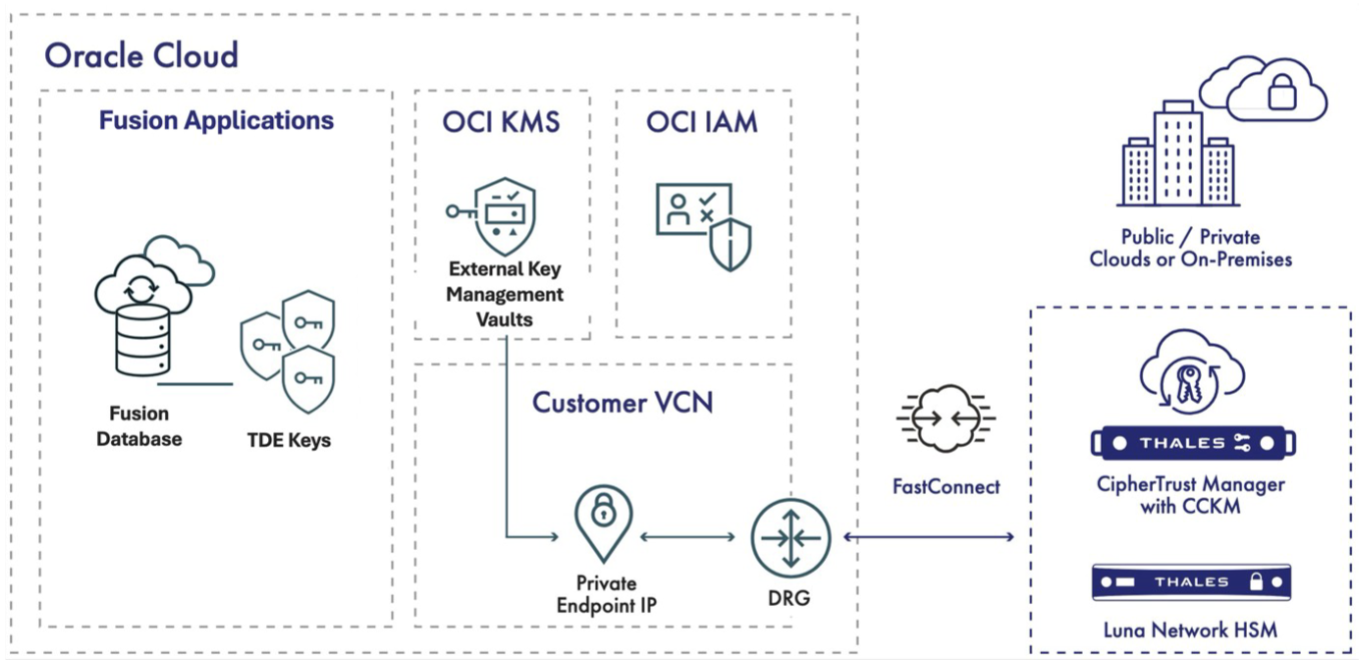
- Your transparent data encryption (TDE) master encryption key (MEK) is stored in your organization-controlled, on-premises key management system (KMS), such as Thales CipherTrust Manager or Luna Network HSM via CCKM.
- Your Fusion Databases use EKMS to perform TDE tasks.
- Cryptographic requests from your Fusion Applications flow securely through Oracle Cloud Infrastructure (OCI) EKMS and FastConnect or virtual cloud networks (VCN) to your KMS.
- Your third-party KMS performs the requested cryptographic operations and returns the result to your Fusion Applications via EKMS.
- For encryption, your TDE data encryption key (DEK) is encrypted with your MEK; for decryption, the process is reversed.
Prerequisites to Set Up Oracle EKMS
You can access Oracle EKMS through the Oracle Cloud Console, API, or command line interface (CLI). To get started, create your vault and master encryption keys (also known as key references); the actual key material is never stored in Oracle Cloud Infrastructure (OCI). The structure of vaults, master encryption keys, and data encryption keys remains consistent across applications using Oracle EKMS.
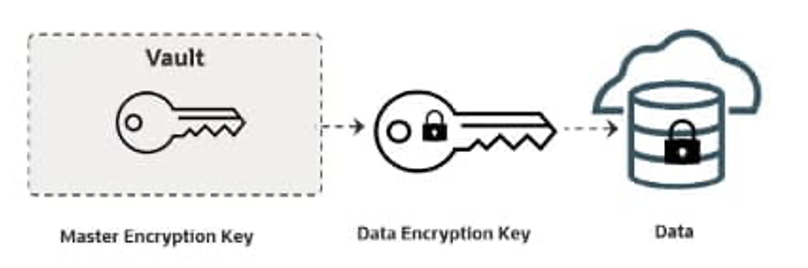
To create your vault and master encryption keys, follow these one-time configuration steps to enable secure connectivity and communication between External KMS and Thales CipherTrust Manager and CCKM.
Procure and provision Thales CipherTrust Cloud Key Management and OCI FastConnect
- Install Thales CipherTrust Cloud Key Management: Deploy CipherTrust Manager as a virtual appliance or on-premises server by following the official instructions.
- Provision OCI FastConnect: We recommend FastConnect with Colocation with Oracle. FastConnect with a Third-Party Provider is also supported. site-to-site VPN is possible but not recommended due to reliability concerns. For setup details, see the implementation examples.
Establish secure connectivity between OCI and Thales resources
To access Thales CipherTrust Cloud Key Management, you need to set up authentication and authorization. OCI EKMS uses the OAuth 2 protocol for authorization. To complete the setup, your administrators are responsible for:
- Set up OAuth 2.0 in your Identity Domains for authentication and authorization
- Set up Confidential Resource Application to represent Thales CipherTrust Manager
- Associate Confidential Client Application with Confidential Resource Application
- Register the identity provider with JSON Web Token (JWT) Issuer
- Configure Identity and Access Management IAM policies
For detailed steps, refer to the OCI EKMS Documentation.
How to Get Started
Create an External Vault and Key Reference in OCI EKMS
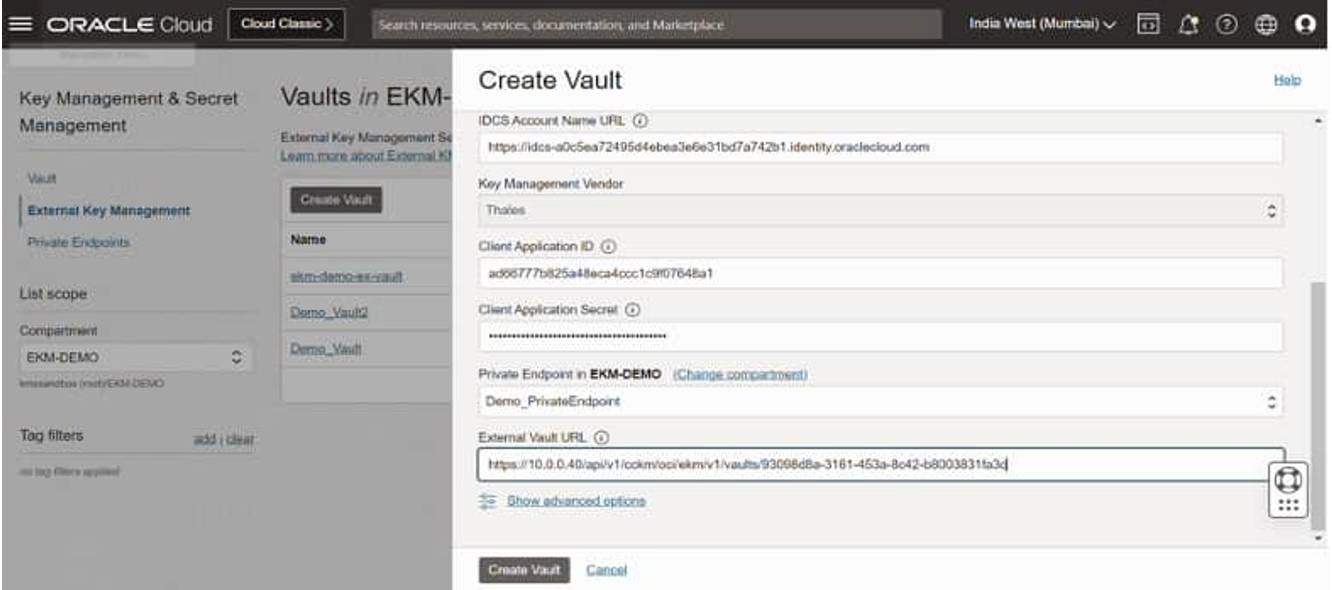
In Oracle Cloud Console, Nevigate to Identity & Security → Key Management & Secret Management → External Key Management
After completing all prerequisite configurations, create your External Key Management Vaults and Key References from the External Key Management page in the Oracle Cloud Console.

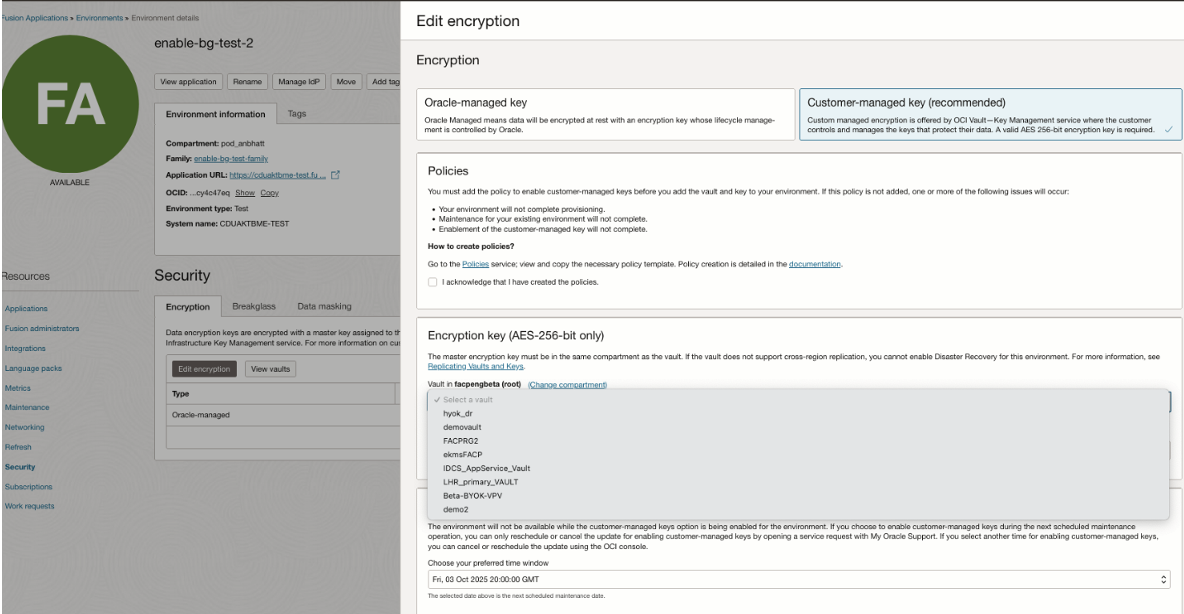
Add a Customer-Managed Key in EKMS to your Fusion Environment
In Oracle Cloud Console, Navigate to Fusion Applications → Environment → Edit Encryption
Adding customer-managed keys to your Fusion environments can be performed either during environment creation or after the environment has already been created.
Enable replication for the External Vault in Oracle EKMS
In Oracle Cloud Console, Nevigate to Identity & Security → Key Management & Secret Management → External Key Management → Vault Information → Actions → Replicate Vault
Refer to Creating a Vault Replica and Viewing a Vault Replica’s Keys for detailed instructions.
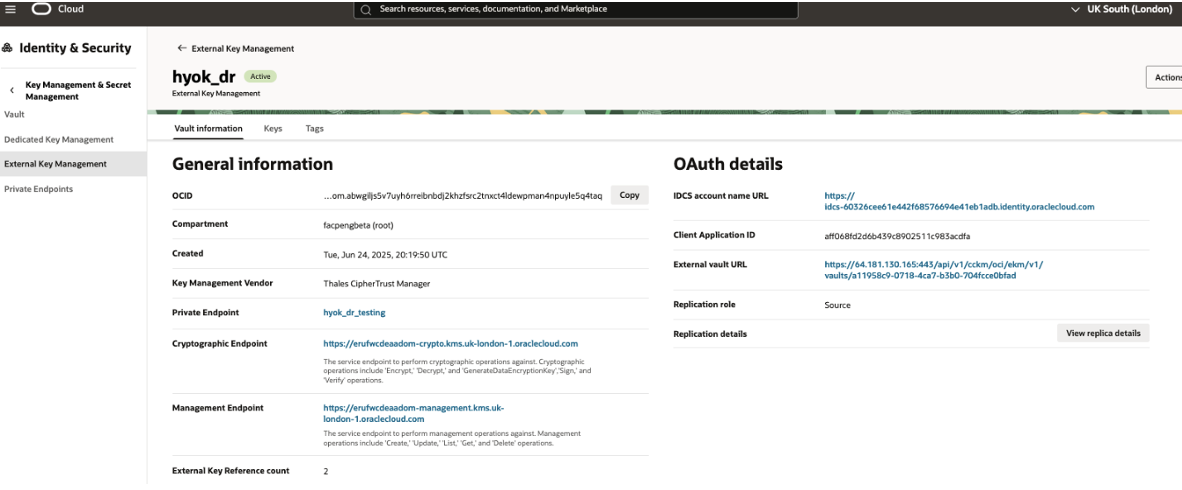
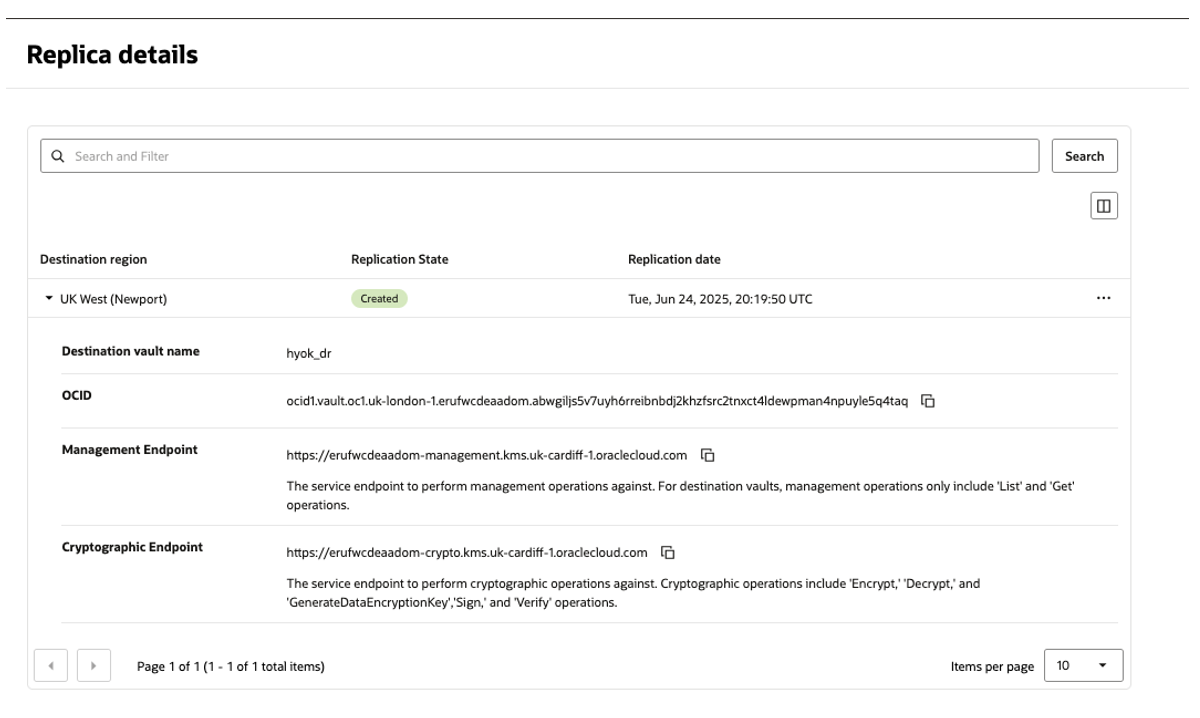
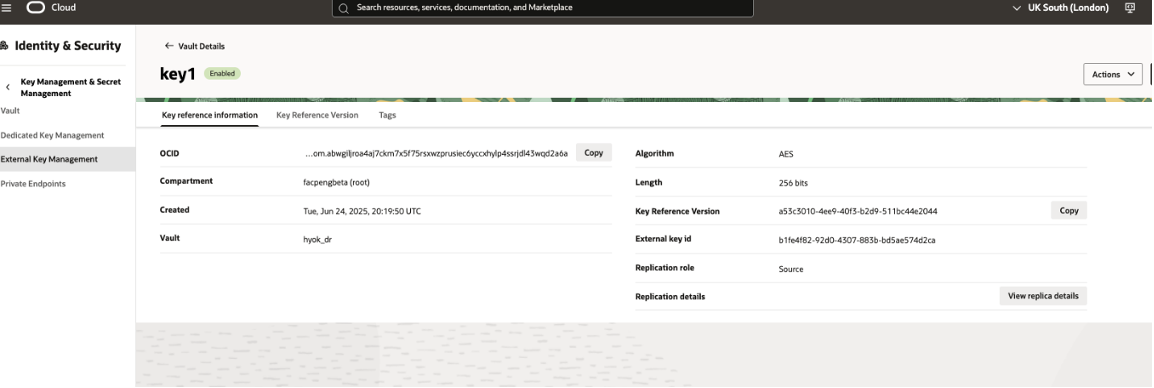
Register the Oracle External Vault in Thales CipherTrust Cloud Key Management
Before you begin, make sure your OCI tenancy and identity provider (IDP) are added to CipherTrust Cloud Key Manager (CCKM). For detailed steps, refer to the official instructions.
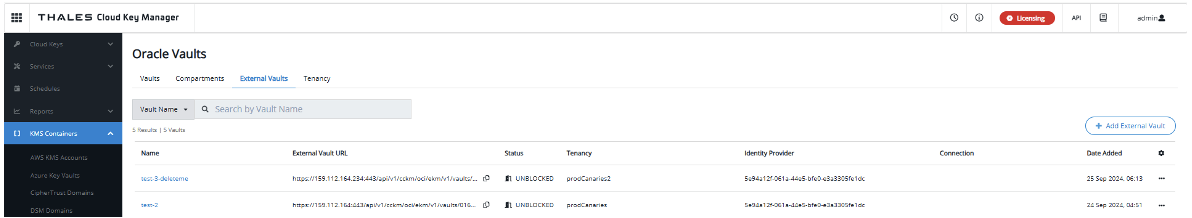
In Thales Cloud Key Manager, Navigate to Cloud Keys → Oracle → Add Key.
For detailed steps, refer to the instructions.
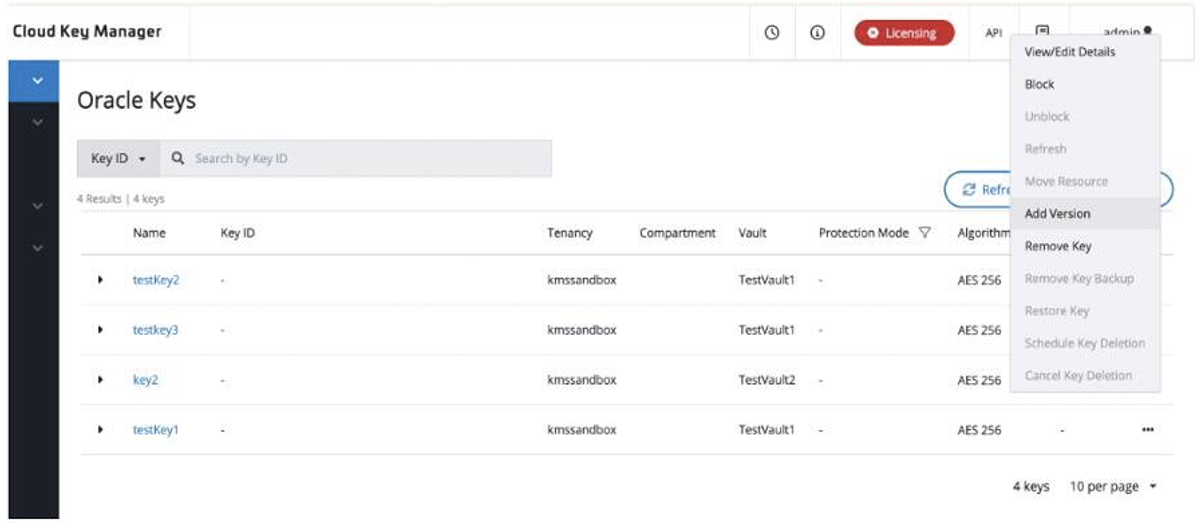
Rotating key references
To rotate the encryption key and the corresponding key reference, first rotate the key in Thales CipherTrust Cloud Key Management. Select Add Version to add a new external key version in Thales.
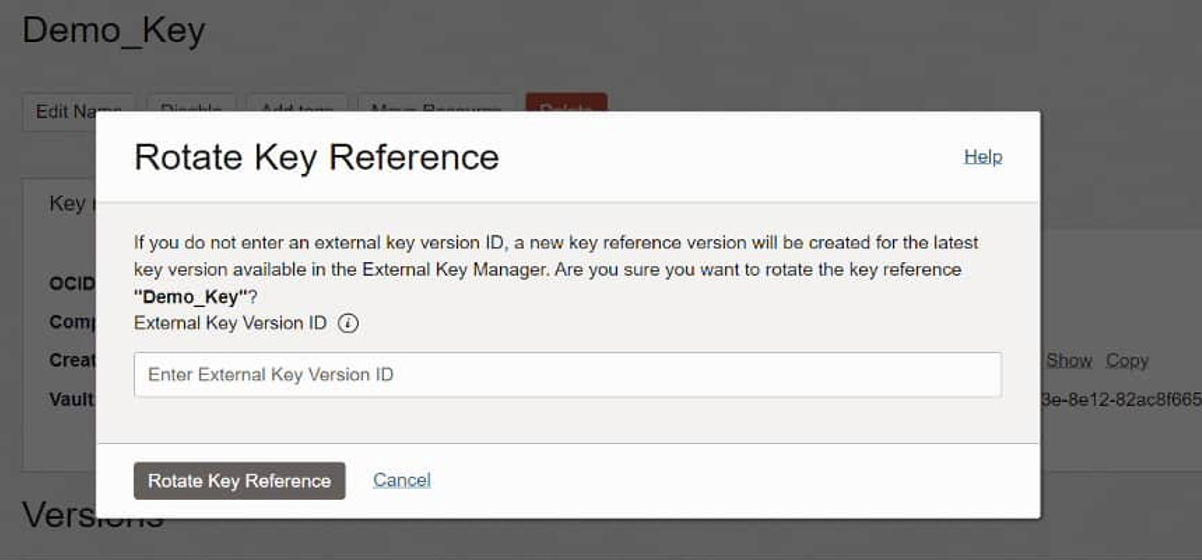
In Oracle Cloud Console, you also need to Rotate the Key Reference. Select Rotate Key Reference and enter the external key version ID from the previous step. If left blank, Oracle EKMS automatically uses the most recent Version in Thales.
Conclusion
We are witnessing a significant shift in expectations: you now require not only robust protection, but also direct control over your encryption keys. Oracle EKMS for Oracle Fusion Cloud Services delivers exactly that, combining Oracle’s cloud resilience with customer-controlled encryption management. This milestone advances your operational independence, supports a zero trust architecture, and ensures verifiable compliance.
By enabling you to bring and hold your own keys, Oracle Fusion Cloud Services reinforces a core principle: your data, your control.
Together, we can shape the future of cloud on your terms.
Learn More
• Break Glass for Oracle Applications Service Documentation
• Onboarding External KMS Guide


