In this post, we teach you how to set enforcements across your organization using a new feature: Oracle Cloud Infrastructure (OCI) Organization Governance Rules service. This feature enables you to set enforcements across your organization to ensure that tenancies comply with the guardrails you have set. These enforcements include the following capabilities:
- Set a resource quota to limit or disable certain services
- Set an allowable list of regions as permitted by your compliance standards
- Share a tag namespace for consistent tagging
- Define a tag default to ensure that all resources are tagged
You can target each rule that the parent tenancy to one or more child tenancies. When set, they’re locked, so users within the child tenancy aren’t permitted to modify the rule.
Example use case
Let’s look at a typical structure of an organization.
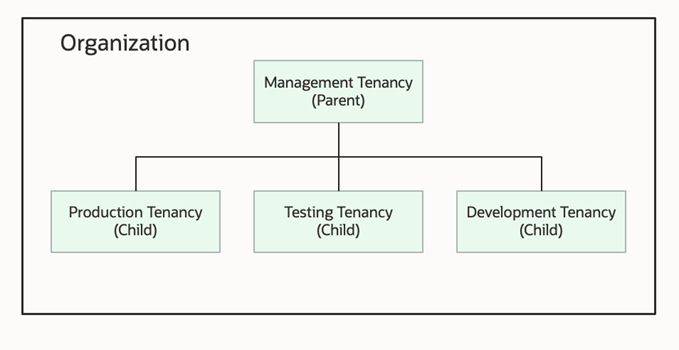
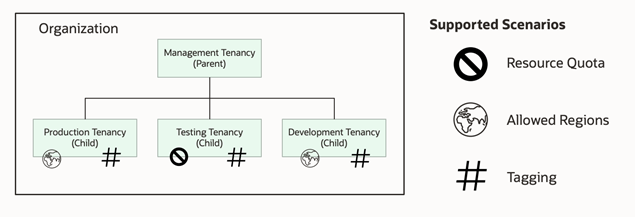
In this organization, I have a tenancy for each of my environments—production, development, and testing—and want to set guardrails for each of my tenancies. For example, I want to restrict the use of Resource Manager, allow only the US regions for my production and development tenancies, and share a tag namespace across all tenancies. So, I start by defining my governance rules, resulting in the following structure:
Setting a resource quota governance rule
For my resource quota rule, I create a simple rule, give it a name, provide a description, and select resource quota as my type. Using the quota policy builder, I can specify which policy is pushed to the targeted tenancy in the quota statement. After writing this quota, Governance Rules pushes the quota to the child and locks it so that the child tenancy can’t modify the quota. For this scenario, I want to ensure that my child tenancies don’t use Resource Manager. So, I write a quota that limits the number of Resource Manager jobs and stacks to prevent the use of this service.
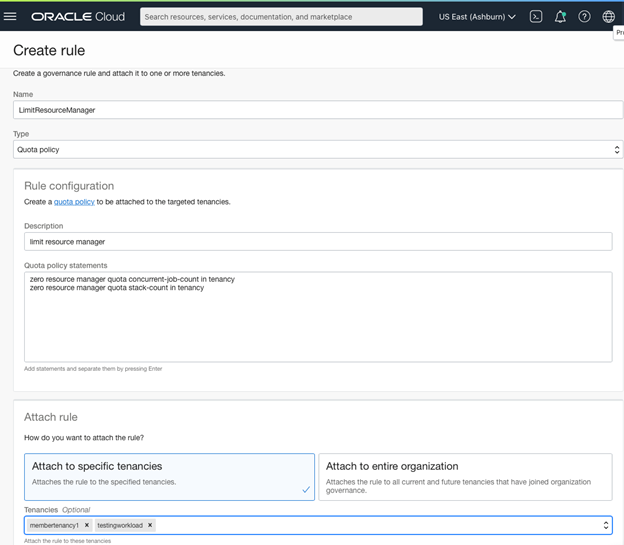
After I specify the rule, I can apply it to the testing tenancy. Governance rules create the quota within the targeted tenancy and lock it. So, when a user logs into the testing tenancy, they can view the quota statement but not modify it. This quota prevents the user from exceeding the resource manager stack and concurrent job count specified in the governance rule.
For a full list of quotas, see the quota service page. This service list and its resource types grow over time.
Setting an allowed region Governance rule
I have a compliance regulation that only allows production data residing in the US regions. So, I want to ensure that my production and testing tenancies can only subscribe to the US regions. In this list and apply the rule to the production and testing tenancies.
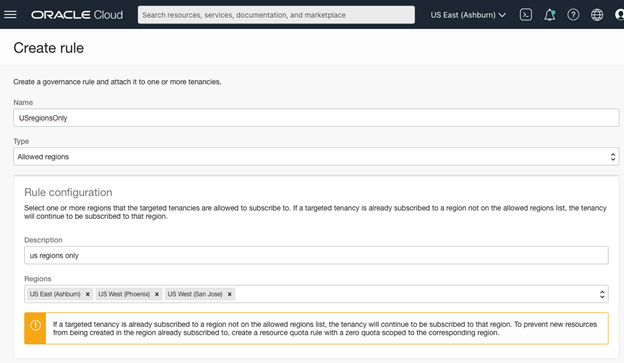
You can modify this rule at any time and propagate those changes throughout the targeted tenancies. So, if you want to add another region, you can modify the governance rule, add the region, and the service updates the list on the targeted tenancy. With the restrictions imposed by this rule, child tenancies are only allowed to subscribe to regions that the parent tenancy is subscribed to.
Setting a tag governance rule
The last rule you want to create shares a centralized tag across your organization. You can centrally manage this tag and have it viewable and usable by child tenancies, without needing to manage it for each tenancy.
First, have the tag namespace created. Then, using governance rules, select the tag namespace type and the specific namespace that you want to propagate throughout the targeted tenancies. Because you want it to apply to all tenancies that exist and new tenancies added to the organization, select Entire Organization as the target.
Governance rules create the tag namespace throughout each tenancy. When the child tenancy creates a resource, they can use the tag provided by the organization admin.

Applying governance rules
Whether you have a structured multitenancy organization or are starting to expand, you can apply governance rules at any time in the process. After creating these, you can view the rules, and select how you would like to apply them. You can either target specific tenancies or an entire organization. When applying to specific tenancies, only these tenancies have the rule applied. This list only includes tenancies that have opted into governance rules. If you apply to an entire organization, all tenancies including ones that join the organization have the rules apply. Choose the option that’s right for you.
When you add a tenancy to an organization, either by inviting an existing or creating a tenancy, you can a governance rule. If the rule applies to the entire organization, you see it added by default. You can add other rules and see how the rules apply to other tenancies to find the right type of restrictions you want to add to your new tenancy.
FAQs
1. When child tenancies leave the organization, such as the parent unsubscribing from Pay As You Go (PAYG), are any governance rules removed automatically from the child PAYG tenancy? Or do the rules remain but are unlocked?
When a child leaves the organization, the rules are detached from the child. The governed resource is unlocked from the child.
2. Is it true that not even the PAYG child cloud account administrator can remove these governance rules on the child level?
Correct. Those governed resources are locked and can’t be unlocked.
3. What if the PAYG or child tenancy admin has already set up quota rules, which are less restrictive than what the parent has set. Does the new parent setting override the child quota policy, or does it error out? How does that look in the Console?
Both quotas apply, which means that the most restrictive quota is enforced.
4. Regarding “Enforce a set of allowable regions, so that data resides only in specific regions”: Can this setting can only be applied to regions that the child is already subscribed to, or if the parent is subscribed to Ashburn, Phoenix, or London regions, while the child is subscribed to Ashburn or Phoenix, to prevent the child to add London as a future region? If the lock is on London set by the parent, the child can’t add the region, and if the child was already subscribed to London, they can only see the region, not select it, in the Console if locked.
The rules set an allowable set of regions. So, if the rule is created to allow Ashburn and Phoenix, it doesn’t allow for any other regions, including London. If the child is already subscribed to London, the rule doesn’t unsubscribe the child from London. You can resource quotas to prevent services from being enabled in London. It doesn’t impact existing workloads that are already in the region.
Conclusion
This blog post is the second in a series to help guide you through governance rules. Stay tuned for updates on the product. To learn more about organizations, refer to our public documentation.
Blog Post: Use Organizations to centrally manage costs: Part 1 of 3
Blog Post: Structure your OCI organization into groups for cost optimization and reporting: Part 3 of 3