In a single tenancy, Oracle Cloud Infrastructure (OCI) has the concept of compartments that let you divide resources into logical group for security isolation and access control. You can specify who in your organization can access what in which compartment using Identity and Access Management (IAM) policy. But in some situations, you need to grant permissions for an external entity (person or system) outside your OCI tenancy to access your resources, such as a third-party vendor to manage resources in your OCI tenancy.
If you’ve used Amazon Wed Services (AWS), you’re probably familiar with the command AssumeRole. With AssumeRole, you can delegate cross account access by allowing a user from another AWS account to assume an IAM role in your account and get permissions associated with the role.
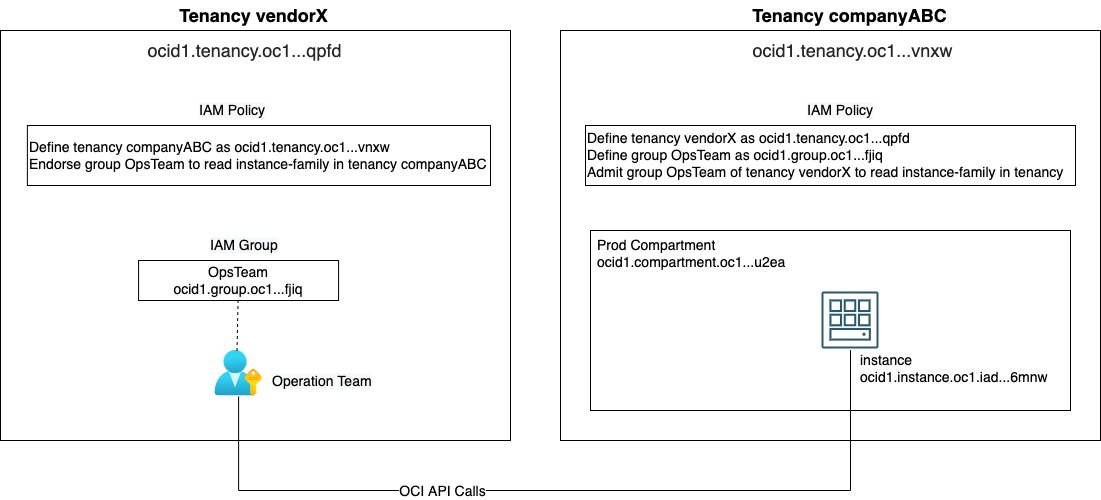
In OCI, we use a different approach to achieve the same result: cross-tenancy policies. OCI IAM policy uses the concept of admit and endorse. Let’s say you want to grant permission for the operation team in a third-party vendor tenancy (vendorX) to monitor Compute instances in your OCI tenancy (companyABC). Administrators of both tenancies need to create IAM policies, as depicted in the following diagram:
Configure IAM policies
In your OCI tenancy, use the following steps:
-
Obtain tenancy and IAM group OCIDs from your third-party vendor.
-
Use the define statement to assign alias for tenancy and IAM group for third-party vendor.
-
Use the admit statement to grant permission for IAM group in the third-party vendor’s tenancy.
Define group OpsTeam ocid1.group.oc1…..fjiq <OpsTeam unique OCID>
Admit group OpsTeam of tenancy vendorX to read instance-family in tenancy
In the third-party OCI tenancy, use the following steps.
-
Supply your tenancy OCID to third-party vendor.
-
Use the define statement to assign alias for the customer (companyABC) tenancy.
-
Use the endorse statement to control which group can access resources in the customer tenancy.
Endorse group OpsTeam to read instance-family in tenancy companyABC
Implementing the policies
The operation team in vendorX Tenancy can then cross the boundary and access resources in your tenancy by specifying either the compartment-id or unique OCID of the resource.
To list all the instances in prod compartment in companyABC tenancy, use the following command:
To get details of an instance in companyABC tenancy, use the following command:
Conclusion
With proper Endorse/Admit IAM policies defined, users can access resources in another tenancy using OCI CLI, SDK or API. The same IAM syntax applies to Instance Principles, a feature that allows instance to perform actions on service resources. Cross-tenancy policies must be defined under the root compartment on both sides. Not all Oracle Cloud Infrastructure services and API support cross-tenancy policies, so ensure you test the policies thoroughly to verify results.
For more information, see the following resources:
