As the next generation cloud provider, Oracle Cloud Infrastructure (OCI) is committed to help our customers achieve their goals using Oracle, partner, and open source technologies. OCI is also committed to helping our customers implement hybrid cloud environments. This post explains how you can achieve a simple integration between Oracle Cloud VMware Solution and native OCI services in different regions.
VMware Solution virtual machines to OCI native instances
To demonstrate the communication from an Oracle Cloud VMware Solution overlay (NSX-T) segment to native OCI instance in a different region, the setup uses the OCI Frankfurt region as the VMware Solution deployment region and London as the location of the native OCI virtual machine (VM) instance.
In the following graphic, the green dashed lines indicate source traffic flow: NSX-T overlay to native OCI virtual cloud network (VCN) or subnet. The blue dashed lines indicate return traffic.
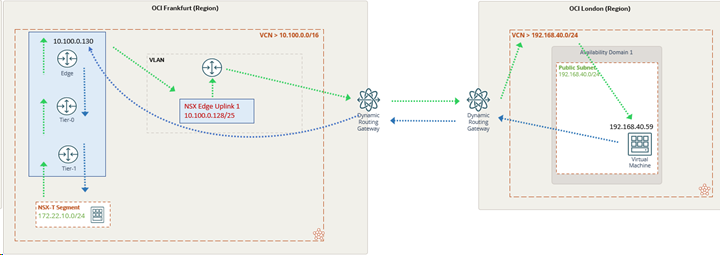
To establish communication, use the following high-level steps:
Here are the high-level steps to establish communication:
- Create a remote peering connection between dynamic routing gateways (DRGs) in Frankfurt and London.
- Use the Oracle Cloud VMware Solution console wizard to configure connectivity to your on-premises network.
- Verify network configuration.
In Frankfurt (region A), we begin with the following setup:
- VCN with CIDR 10.100.0.0/16.
- VMware Solution software-defined data center (SDDC) is deployed in this VCN.
- VMware Solution SDDC management IP CIDR is 10.100.3.128/26.
- NSX-T overlay segment is 172.22.10.0/24
In London (region B), we begin with the following setup:
- VCN and public subnet (both CIDR 192.168.40.0/24)
- Windows instance connected to public subnet with IP address 192.168.40.59
- DRG with VCN attachment
First, set up DRG remote peering from Frankfurt to London. For a detailed guide if this setup, see Peering VCNS in different regions through a DRG.
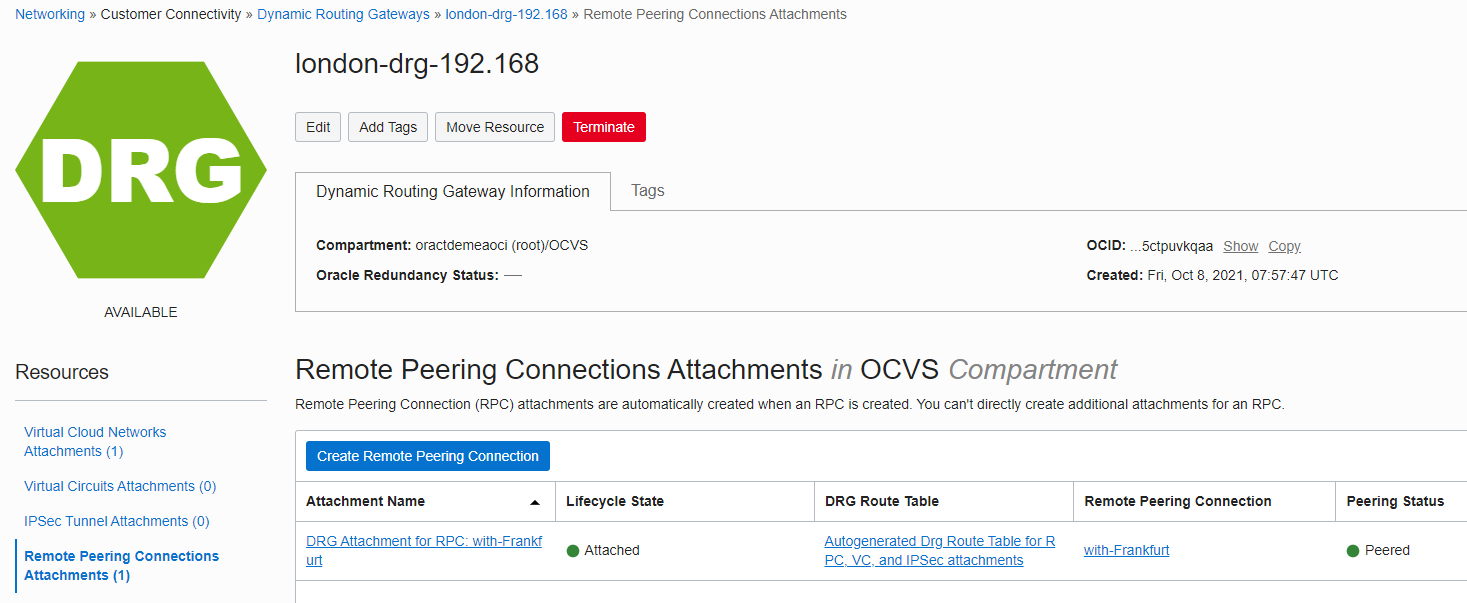
- Navigate to the DRG page in the Oracle Cloud Console in London and click Remote Peering Connection attachments.
- Click Create Remote Peering Connection and name (for example “with-Frankfurt”).
- When it’s in the attached state, click the link “with-Frankfurt” under the Remote Peering Connection column.
- Copy the OCID ID starting with ocid1.remotepeeringconnection.oci1.uk-london*
Now, we need to create the other end of the peering connection in Frankfurt. Navigate to the DRG in the Console, followed by Remote Peering Connection Attachments.
- Click Create Remote Peering Connection and enter a name (for example “with-London”).
- When it’s in attached state, click the link “with-London” under the column, Remote Peering Connection.
- Click the Establish Connection tab.
- Choose region as uk-london-1 and copy the ocid1.remotepeeringconnection.oci1.uk-london* ID
- In a few minutes, the status reports “Peered.” The same status is seen in the London region Console.
To view the routes learned from Frankfurt in London, we need to navigate to the DRG Console in London.
- Click the DRG Route tables, followed by Autogenerated DRG Route Table for VCN attachments.
- Click the tab, Get All Route Rules. Here, we see all the routes learned from Frankfurt.
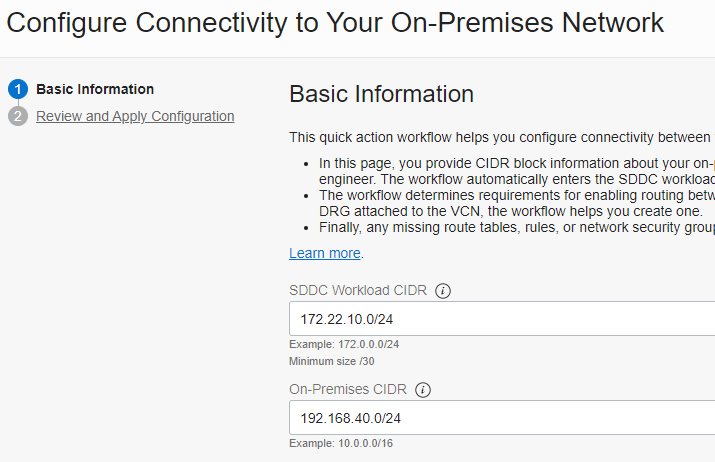
The second step is to set up connectivity from the NSX-T overlay network in Frankfurt to the OCI VCN in London.
- In the Console, in Frankfurt, navigate in the menu to Hybrid, VMware Solution, and OCVS SDDC.
- Click the tab, Configure Connectivity to Your On-Premises Network.
- Enter the SDDC workload CIDR as 172.22.10.0/24 (NSX-T overlay network).
- Enter the on-premises CIDR as 192.168.40.0/24 (London region native OCI VCN or subnet) and click Finish.
- It adds the required route table entries and the required network service gateway (NSG) rules.
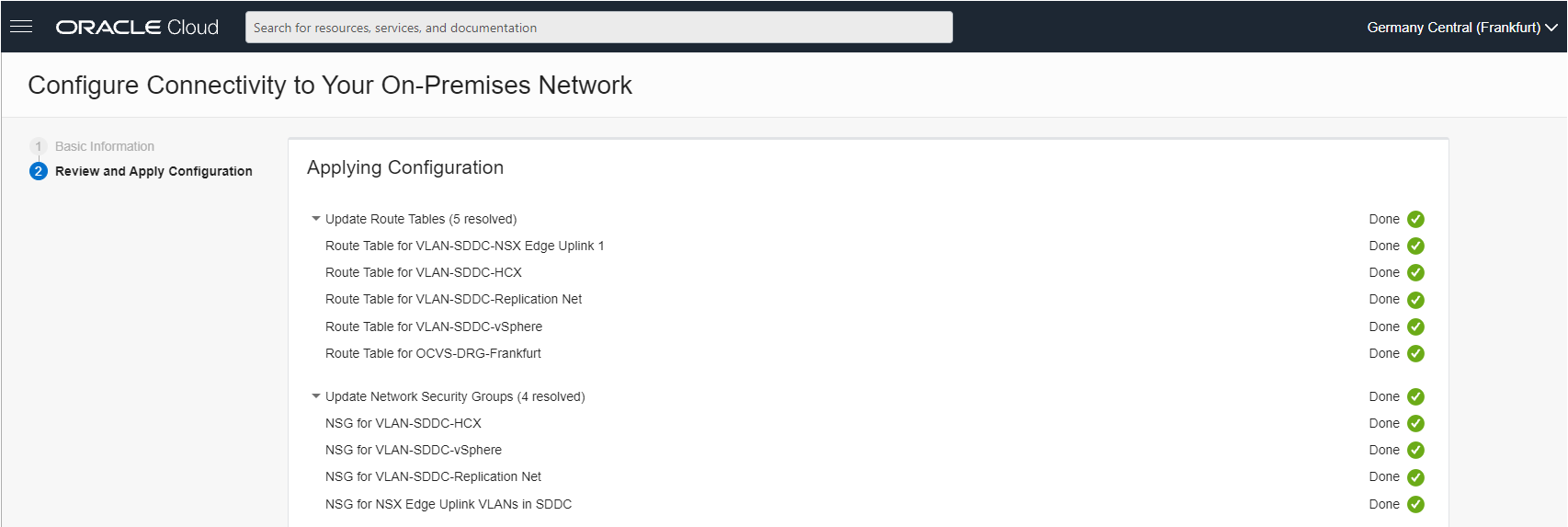
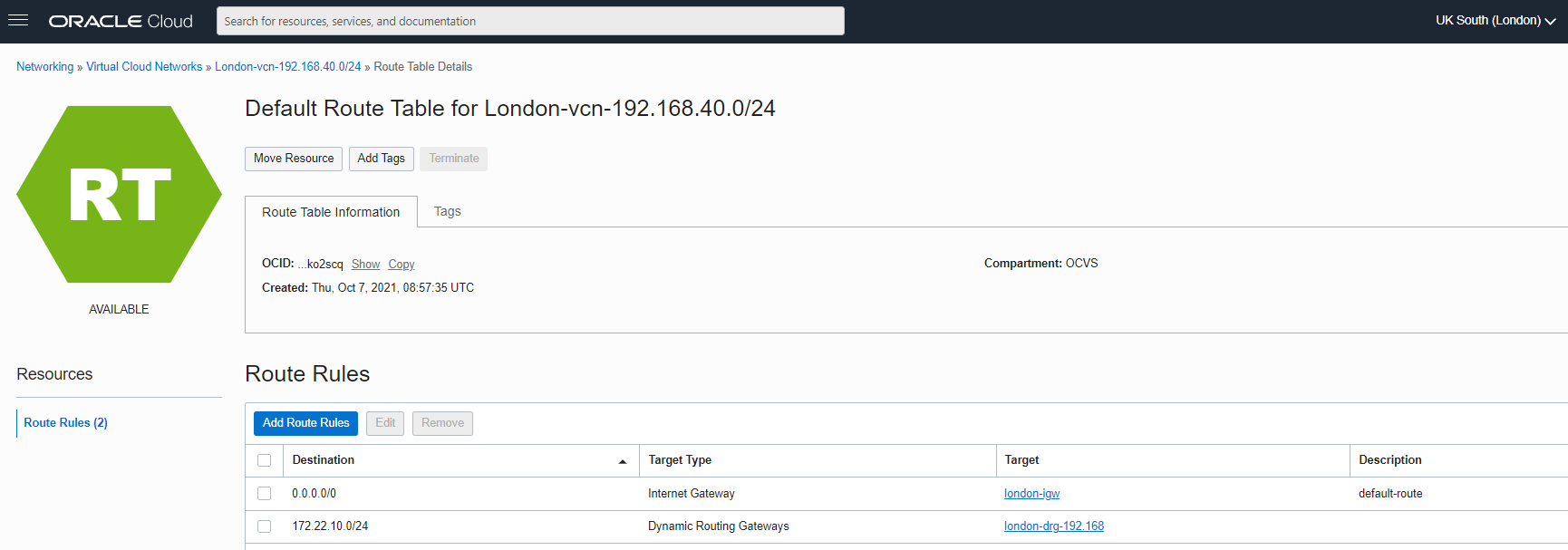
The third step is to verify the network configuration by verifying that security list and routing are in place.
- The routing table for the subnet in London (192.168.40.0/24) needs to send traffic to the DRG in London for traffic destined to the NSX-T overlay network in Frankfurt (172.22.10.0/24).
- A security list in the London subnet or an NSG associated with the instance in London needs to allow incoming and outgoing traffic from the NSX-T overlay segment in Frankfurt (172.22.10.0/24).
Conclusion
You now have bidirectional connectivity from the NSX-T overlay segment in Oracle Cloud VMware Solution Frankfurt to the native OCI subnet in London. The ability to communicate between different solutions and regions ensures your ability to innovate using all the resources available, without region and product limitations.
If you want to read more on this topic, the following links give you more insight about VMware on Oracle Cloud Infrastructure: