NOTE:
WebLogic Server can be configured to use as a SAML Identity Provider (IDP) or SAML Service Provider (SP).
When WebLogic Server is configured as an Identity Provider, it does not support SAML Single Logout.
However, support for SAML SLO was added to WebLogic Server when configured as a Service Provider via enhancement requests 35673222 and 34556989.
These fixes are now a part of WLS Oct 2023 PSU and later.
Step 1:
Apply October 2023 PSU/SPB or later
Step 2:
Say, WebLogic Service Provider is configured on AdminServer.
Login to console -> AdminServer -> Federation Services -> SAML2.0 Service Provider
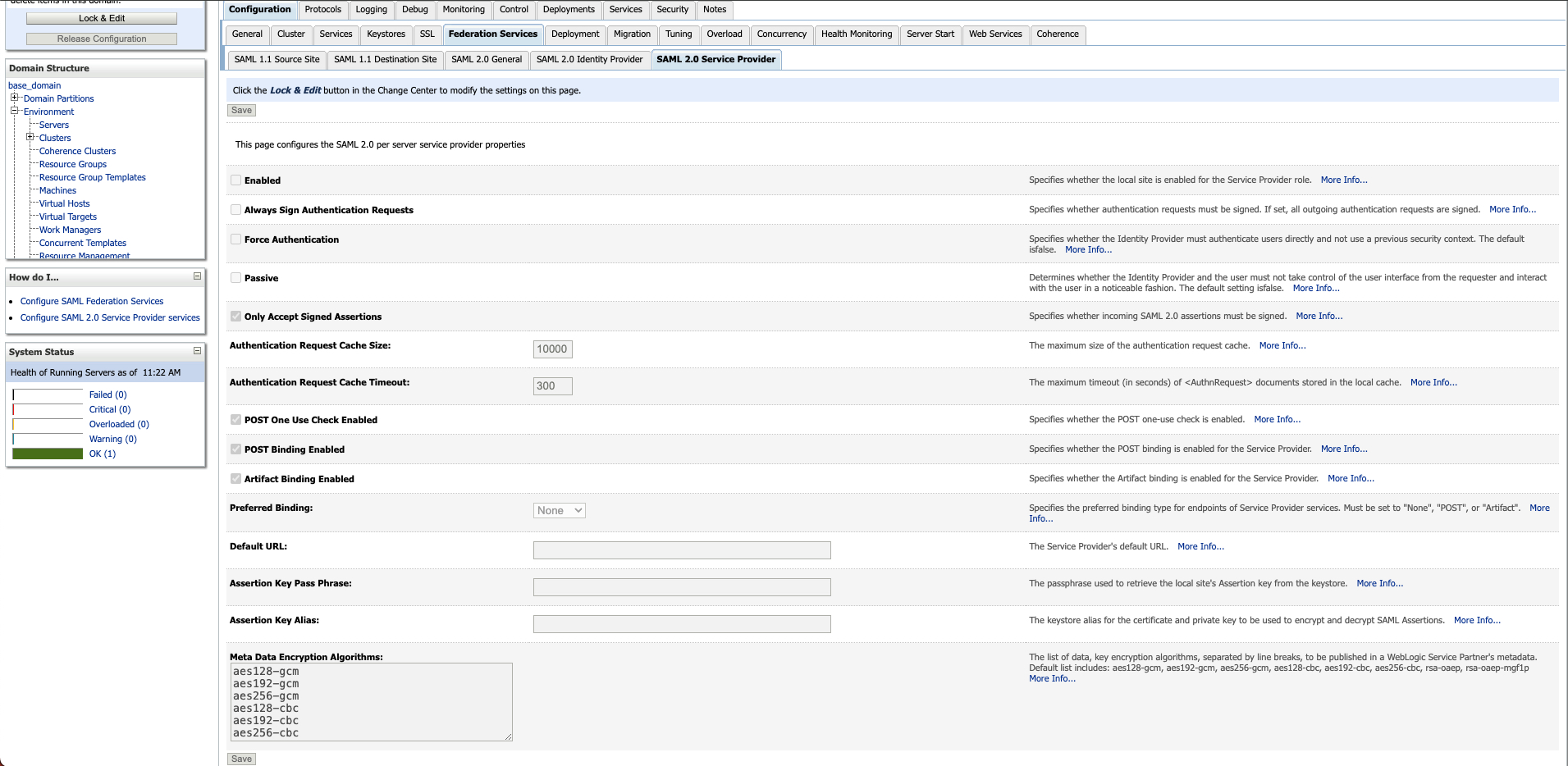
You should see 4 new fields here related to SLO after applyig the Oct 2023 PSU:
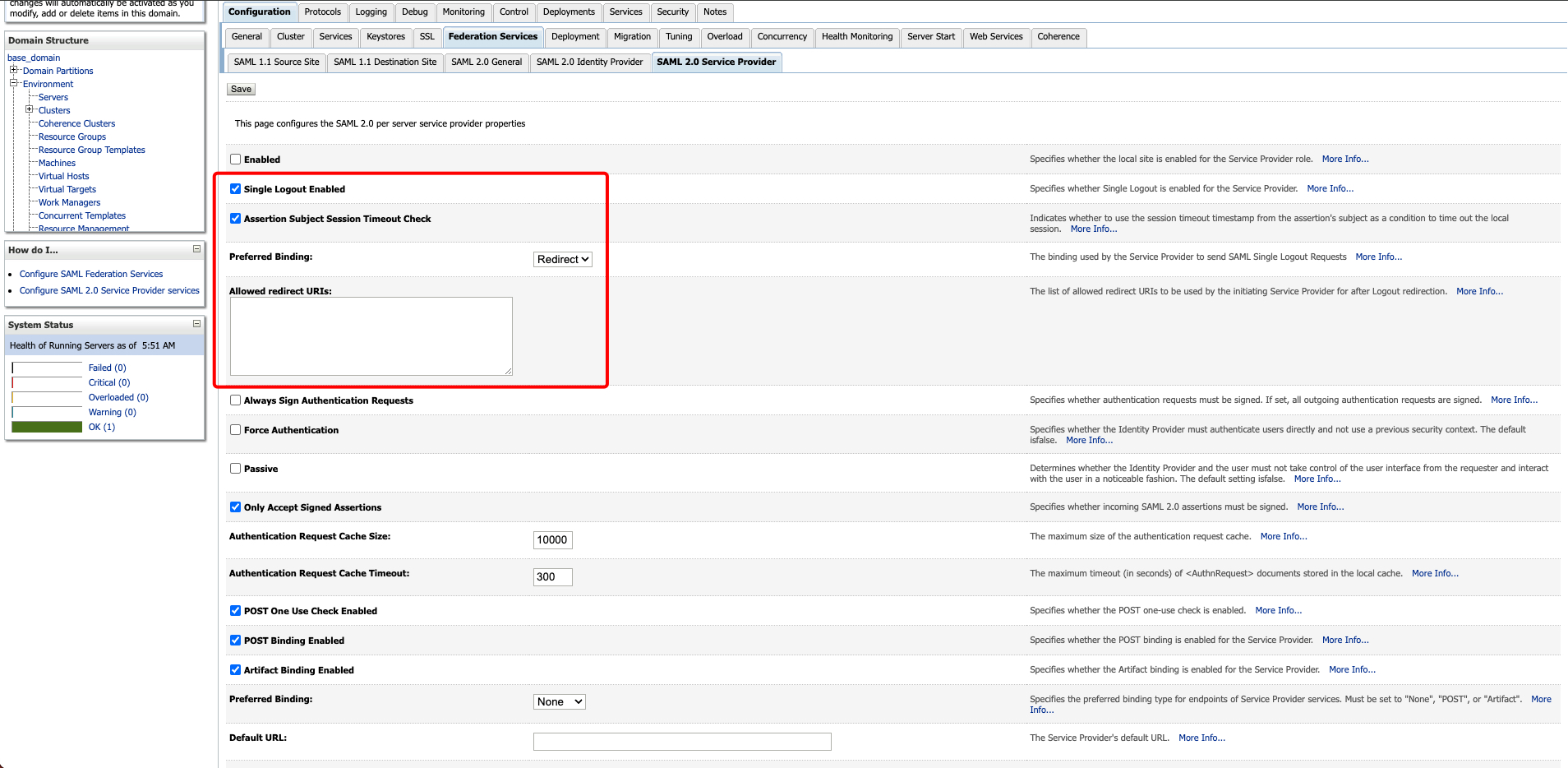
1. Single Logout Enabled
2. Assertion Subject Session Timeout Check
3. Preferred Binding
4. Allowed redirect URIs
Screenshots of WebLogic console after applying October 2023 PSU/SPB or above : (Notice the additional SLO related fields)
Screenshots of WebLogic console before applying October 2023 PSU/SPB:
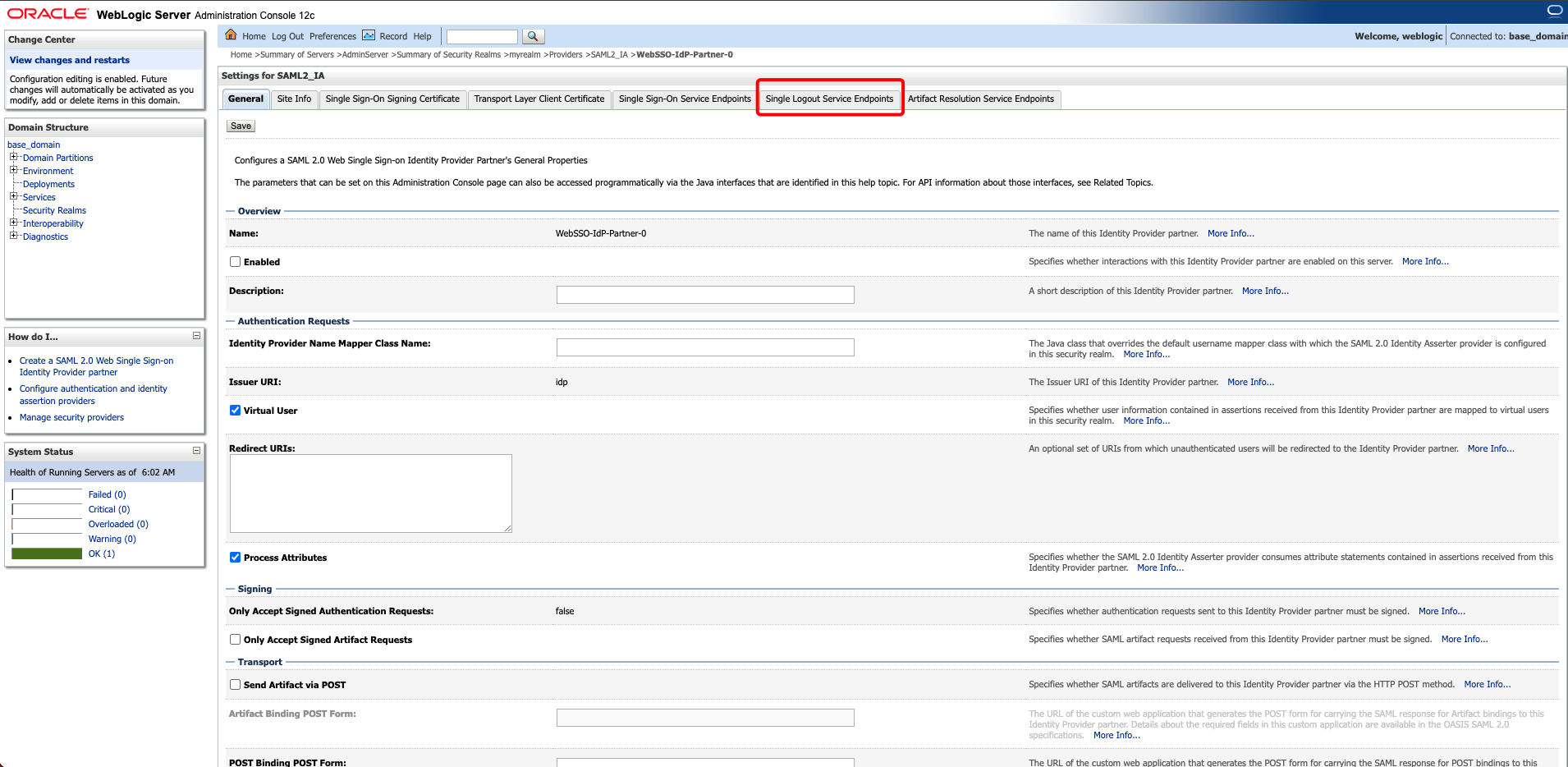
You will also notice a new tab ‘Single Logout Service Endpoints’ that displays the WebSSO IdP partner’s SLO endpoints in IDP partner tab :
Security Realms -> myrealm -> Providers -> <SAML2_IA> -> Management tab.
Screenshots of WebLogic console after applying October 2023 PSU/SPB or above :
Screenshots of WebLogic console before applying October 2023 PSU/SPB:
<Additional Info>
“SAML Single Logout (SLO) complements SAML Single Sign On by logging users out of all of the applications in their current SSO session at once. SAML SLO decreases the number of connections that remain active but unused, therefore reducing the opportunity for unauthorized access.”
“SAML SLO is enabled by default on WebLogic Server instances that act as Service Providers but you can choose to disable it if you want users to log out of each application separately.”
Note:
When WebLogic Server is configured as an Identity Provider, it does not support SAML Single Logout.
