![]()
Introduction
An anonymous login allows the embedding of Oracle Analytics Server (OAS) classic reports or dashboards and data visualization (DV) workbooks into an external portal without user authentication.
Configuring anonymous login for OAS is only appropriate for public-hosted environments and embedding scenarios, and is not advised for general analytics.
Use case 1: If the external portal is a public website embedding OAS reports and workbooks, you can bypass OAS authentication using the anonymous login.
Use case 2: If an external portal utilizes the Go-URL method to access dashboards or reports from Oracle Business Intelligence Enterprise Edition (OBIEE), this is no longer supported from OBIEE version 12.2.1.3 onwards when lightweight SSO or SSO is enabled. In such cases, use the anonymous login for OAS.
Note: when the same SSO provider authenticates both the external portal and OAS, there is no requirement for anonymous login when embedding OAS reports and workbooks.
Approach
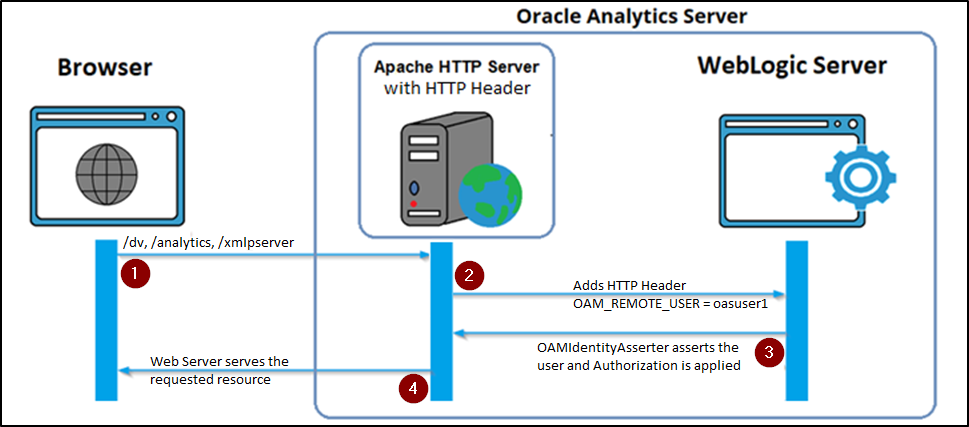
Notes:
- When embedding OAS reports in a public website and OAS and Apache HTTP servers are running on-premises protected by a firewall, configure a load balancer for OAS in the DMZ.
- When embedding OAS reports in a public website and OAS and Apache HTTP servers are running on Oracle Cloud, create the OAS server in a private subnet and the load balancer in a public subnet.
In a typical scenario with certified SSO providers for OAS like Oracle Access Manager and App Gateway, users accessing the OAS URL are redirected to the SSO Identity Provider for authentication. After a successful authentication, the SSO Identity Provider sends the username in the HTTP header to the OAS WebLogic server, where the WebLogic Identity Asserter asserts the username, applies the authorization, and grants access to the OAS application.
Anonymous login is a hybrid solution that involves a webserver, like Apache HTTP Server or Oracle HTTP Server, simulating the SSO Identity Provider authentication and sending a hard-coded username as the authenticated user in the HTTP header to the backend OAS WebLogic Server.
The OAS WebLogic Server is configured with a WebLogic Identity Asserter to assert the username sent in the HTTP Header. This example uses the OAMIdentityAsserter.
Once the user exists in the default embedded LDAP or an external LDAP, the user is allowed access to OAS per the user’s authorization.
Any external portal or user accessing OAS, either via embedding or a direct URL, is automatically logged in and can view the reports, dashboards, and workbooks.
Considerations
OAMIdentityAsserter supports any of these headers: OAM_REMOTE_USER, iv-user, and SM_USER.
With this solution, you need to restrict the privileges and permissions of the hard-coded user only to consume or view reports, and to deny permission to edit or create new OAS reports.
After the configuration, anonymous login is available for /analytics, /dv, and /xmlpserver.
Because this solution is based on sending a username in the HTTP header, any application, browser, tool, or load balancer can also simulate the hard-coded username in an HTTP header and access the OAS application. To manage the security implications, you should restrict access for all end users to the OAS WebLogic managed server (bi_serverN) on port 9502 or 9503.
For example, restrict access to the direct OAS URL like http://oas_server:9502/dv or https://oas_server:9503/dv. You can do it by blocking the 9502 and 9503 ports of the OAS servers in the network. You must also ensure only the webserver can access the OAS servers on ports 9502 and 9503.
The best practice is running a webserver on the OAS Server.
You will also need to suppress the use of the HTTP header in the browser, load balancer, and any external applications, to make sure only the webserver can add values in the HTTP header and send those to the backend OAS WebLogic server.
To more fully understand how to mitigate security issues, read the white paper, Anonymous Login for Oracle Analytics Server, or post questions in the Oracle Analytics community.
Protected, Public, and Excluded List of Resources for OAS
Specific resources are intentionally left unprotected. These resources are accessed through OAS basic authentication mechanisms (user ID and password) by tools that can’t use SSO.
Refer to OAS documentation, Updating the Protected, Public, and Excluded Resources for an Enterprise Deployment..
Configure Anonymous Login for Oracle Analytics Server using the below Whitepaper
Download the Whitepaper: Anonymous Login for Oracle Analytics Server.
![]()
Call to Action
When embedding OAS reports into public websites and applications, either configure the applications and OAS server with same SSO provider or use anonymous login to simulate SSO at OAS server.
While configuring Apache HTTP Server as a webserver for OAS, follow these blogs for more details: Configure Apache HTTP Server as a Webserver for Oracle Analytics Server and SSL Offloading at Webserver for Oracle Analytics Server on Oracle Cloud Marketplace.
If you are using the Oracle HTTP Server to implement the Anonymous Login for OAS Server, see Routing the Oracle HTTP Server requests to the Oracle Analytics Server.
