![]()
This blog describes how to set up Kerberos Single Sign-on (SSO) for Oracle Analytics Server (OAS) with Oracle HTTP Server (OHS).
The way you configure Kerberos SSO for OAS is different to Oracle Business Intelligence Enterprise Edition (OBIEE). With OAS, you mustn’t modify or customize binary files such as .ear files and domain home configuration files. This solution uses OHS running on Oracle Enterprise Linux 8 or Red Hat Enterprise Linux 8 with the mod_auth_gssapi authentication module.
Prerequisites
- Oracle Analytics Server (version 5.9.0 or higher).
- Microsoft Active Directory configured as an authentication provider for OAS.
- OAS configured with an Oracle WebLogic Server identity asserter, such as OAMIdentityAsserter.
- Oracle HTTP Server 12.2.1.4 running as a web server for OAS on a separate or the same host as OAS.
- OHS server with Kerberos client and workstation libraries installed.
- Windows clients joined to the same Active Directory domain.
- Client browser configured for Integrated Windows Authentication.
Authentication Flow
This sequence diagram shows the Kerberos SSO authentication procedure, as well as all communication between the Kerberos client, a browser, and the Oracle WebLogic Server on which OAS is deployed.
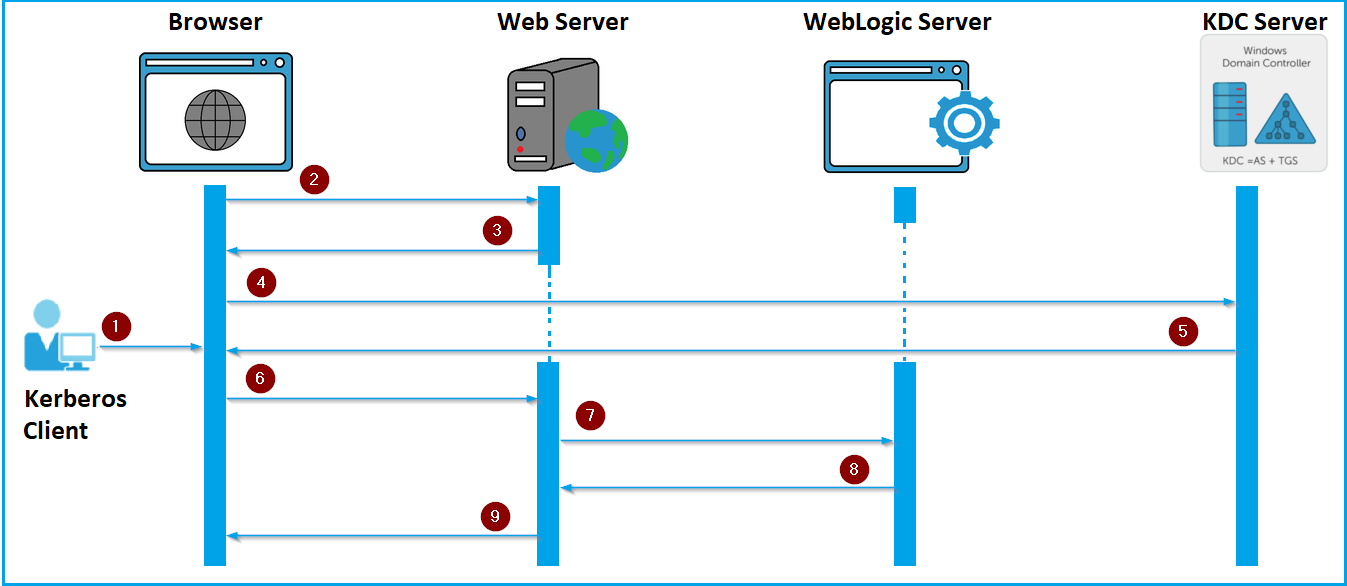
Note: Detailed communication between the Kerberos client, the browser, and the Key Distribution Center (KDC) server isn’t covered in this sequence diagram.
- The user logs in to the Active Directory domain’s Windows client and launches a browser.
- OAS is accessed using the web server (OHS) URL in the browser (/dv or /analytics).
- The web server (OHS) with the mod_auth_gssapi module issues a challenge to the user with a 401 unauthorized message.
- The browser sends an authentication request to the Key Distribution Center’s (KDC) Authentication Service (AS).
- The Key Distribution Center’s (KDC) Ticket Granting Service (TGS) responds with a ticket and a session key.
- The browser provides to the web server the ticket and session key (negotiate token) obtained from the Key Distribution Center (KDC).
- The web server extracts the user ID from the negotiate token and delivers it in an HTTP header such as OAM_REMOTE_USER using the mod_auth_gssapi module.
- Oracle WebLogic Server, where OAS is deployed, uses Oracle Access Manager Identity Asserter (OAMIdentityAsserter) to retrieve the user ID from the HTTP header. If the user exists, OAS grants the user the application roles and grants access to the requested resource (/dv or /analytics).
- The web server provides the user with the requested resource.
![]()
Considerations
Oracle recommends that you utilize the reference implementation for custom SSO, which is supplied as a docker-based solution for OAS and uses Kerberos or SAML 2.0. A web tier and a WebLogic asserter are used in this approach.
See SAML 2.0 and Kerberos Single Sign-On Configuration for Oracle Analytics Server (Doc ID 2761678.1).
See Configuring Oracle Analytics Server for Kerberos Single Sign-On (SSO) (Doc ID 2707401.1).
If you’re unable to use the reference environment in (Doc ID 2761678.1) and open-source software such as Apache HTTP Server in (Doc ID 2707401.1), use this manual approach for Kerberos SSO.
OAM_REMOTE_USER, iv-user, and SM_USER are the supported headers available in the OAMIdentityAsserter.
Oracle advises that you block direct access for all end users to the Oracle WebLogic managed server hosting OAS (bi_serverN) at port 9502 on the network to avoid unauthorized access.
End users must utilize the OHS server to access the OAS URL.
Specific resources are intentionally left unprotected by the mod_auth_gssapi module. These resources are accessible through the OAS basic authentication mechanism (user ID and password) and are intended for use by tools that are unable to use Kerberos SSO.
When configuring mod_auth_gssapi for OHS, the mod_auth_gssapi isn’t loaded in OHS due to the mismatch of the libcrypto.so.1.1 library version of OHS binaries.
You must use the Operating System libraries instead of the OHS libraries. More information is provided in the My Oracle Support Note.
Approach
Using this method, you install an OHS server as a web server before the OAS WebLogic managed server (bi_serverN) on port 9502.
OHS performs Kerberos-based SSO authentication and sends the authenticated user’s user ID to OAS in an HTTP header such as OAM_REMOTE_USER.
The OAS WebLogic server retrieves the authenticated user ID from the HTTP header and verifies that the user ID exists.
If the user ID exists in Active Directory, the user is granted access to the requested resource through OAS application roles.
Configuration Instructions
Refer to the My Oracle Support knowledge document ID 2941776.1 Configuring Oracle Analytics Server for Kerberos Single Sign-On (SSO) using Oracle HTTP Server and GSSAPI Module (Doc ID 2941776.1) for instructions on how to configure Kerberos SSO for OAS using OHS.
Call to Action
This article has shown you how to configure Kerberos SSO for OAS using the OHS server. To handle Kerberos SSO, OHS uses the mod_auth_gssapi module.
Other SSO techniques for OAS are encouraged. The recommended approach for SSO is to configure OAS with SAML 2.0 and Kerberos (Doc ID 2761678.1).
![]()
