With this new feature, all the necessary information are specified in the domain custom resource YAML file. There is no need to have a separate Kubernetes Job. WebLogic Kubernetes Operator will optionally create the persistent volume and claim, then create the WebLogic domain on the persistent volume, if needed, prior to starting the servers.
Preparation for infrastructure
- Gather database wallet and connection information
- Create file system storage objects for persistent storage
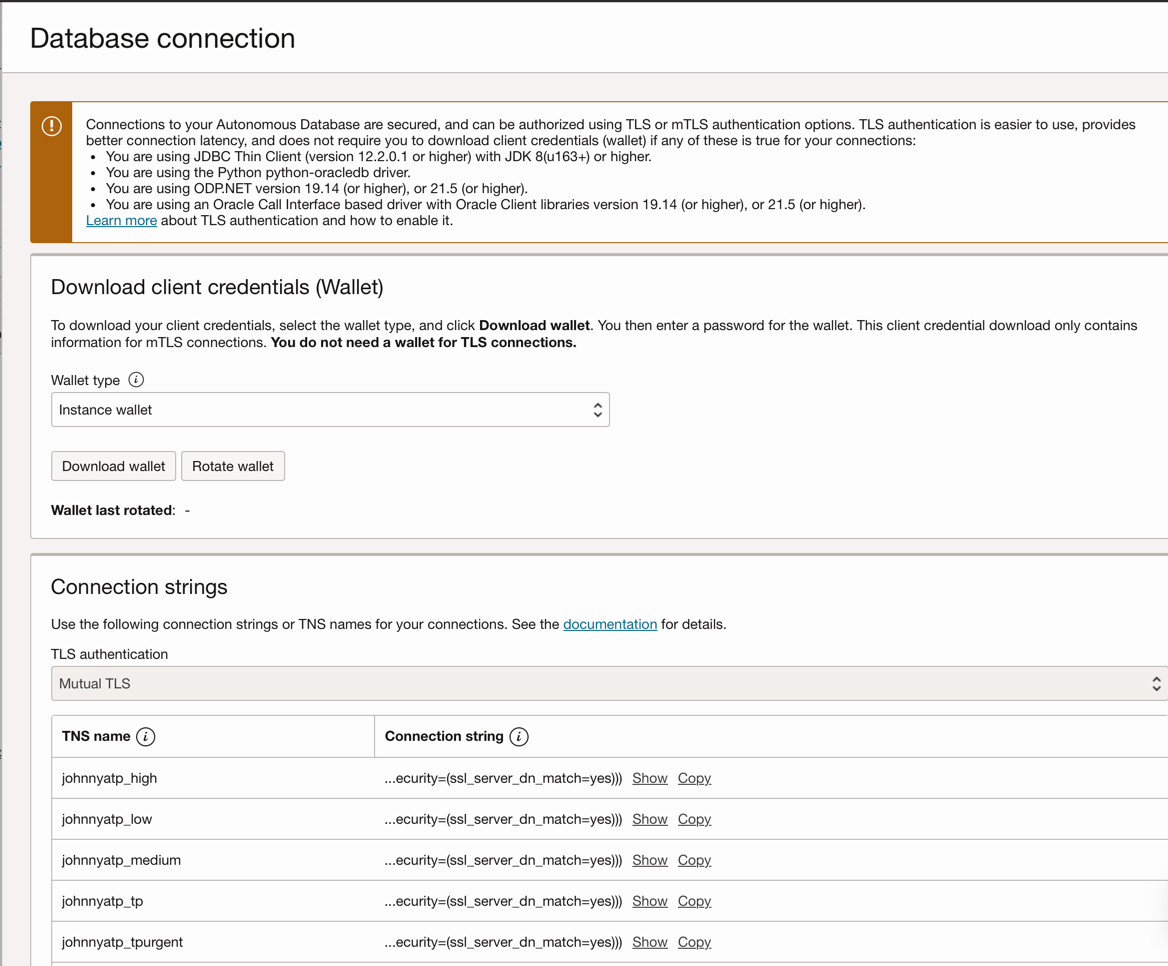
First, we download the database wallet required to access the ATP database, login to the OCI cloud console and navigate to the ATP database instance, click the “Database connection” tab and follow the instruction to download the wallet, also make a note of the database TNS name to use.
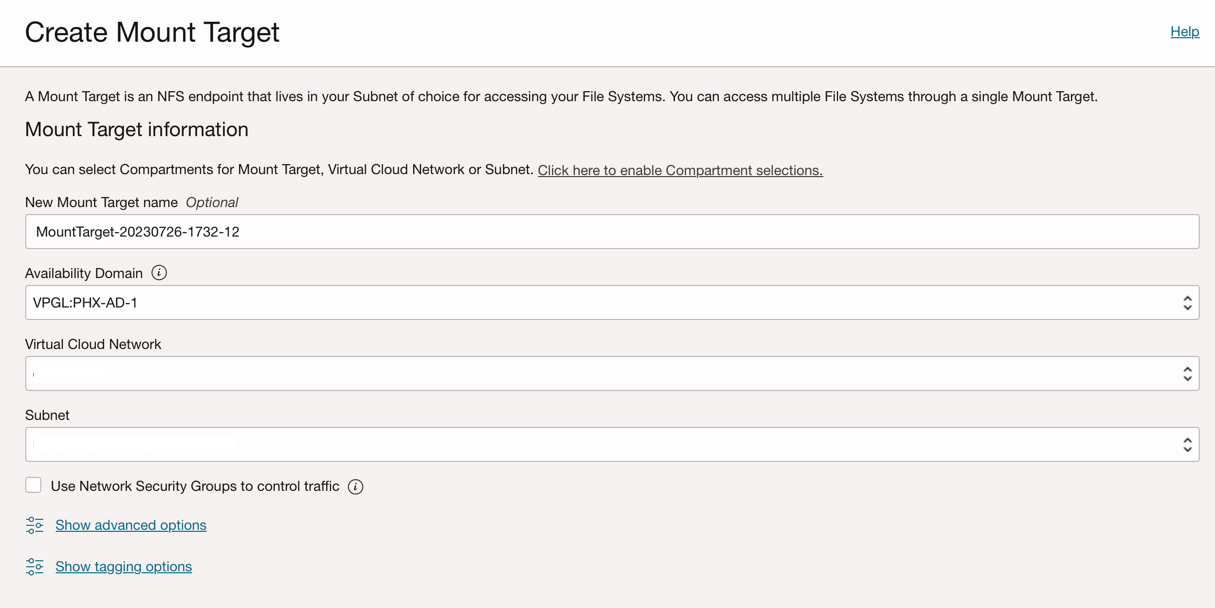
- Create a Mount Target
- Create a Storage class
- Create a persistent volume claim that use the Storage class
Note: Both OKE cluster and Mount Target must use the same Virtual Cloud Network, otherwise it will not work.
This step usually requires administrative privileges; work with your administrator if you do not have the required privileges. See Setting up file storage in OKE
For example, login to the cloud console, navigate to Storage -> Mount Target, use the same Virtual Cloud Network as the OKE cluster to create a Mount Target. Once the mount target is successfully created, make a note of the OCID of the Mount Target.

apiVersion: storage.k8s.io/v1
metadata:
name: wko-domain-in-pv-sc-new
namespace: sample-domain1-ns
provisioner: fss.csi.oraclecloud.com
parameters:
availabilityDomain: PHX-AD-1
mountTargetOcid: <your mount target OCID saved earlier>
exportPath: /mynew-fs07202023
kind: PersistentVolumeClaim
metadata:
name: wko-domain-inpv-pvc-new
namespace: sample-domain1-ns
spec:
accessModes:
– ReadWriteMany
storageClassName: “wko-domain-in-pv-sc-new”
resources:
requests:
storage: 10Gi
NAME STATUS VOLUME CAPACITY ACCESS MODES STORAGECLASS AGE
wko-domain-inpv-pvc-new Bound csi-fss-0bb79… 10Gi RWX wko-domain-in-pv-sc-new 10m
Once the status is in Bound state, this means the storage has been successfully allocated, we can delete this PersistentVolumeClaim, we will let the Operator to create the claim later.
Preparing domain resources
Now, we have the basic infrastructure to suport creating a JRF domain on persistent volume in your cluster, next we will proceed to create the domain resources. The Operator creates the WebLogic domain using the WebLogic Deploy Tooling Documentation.
In this section, we will:
- Create the WDT models to describe JRF domain, we will only setup the topology, but other resources and application deployment can also be setup.
- Create a domain creation image hosting the WDT models and the WebLogic Deploy Tool installation.
- Create domain resource YAML to deploy the JRF domain.
First, create an empty directory and copy the ATP database wallet into a separate directory
cp <wallet zip file> -d $HOME/models/rcu
AdminUserName: ‘@@SECRET:__weblogic- credentials__:username@@’
AdminPassword: ‘@@SECRET:__weblogic- credentials__:password@@’
RCUDbInfo:
databaseType: ATP
#
# RCU prefix
#
rcu_prefix: ‘@@SECRET:rcu-schema-secret: rcu_prefix@@’
#
# RCU schema password to be used for creating RCU schema
#
rcu_schema_password: ‘@@SECRET:rcu-schema-secret: schema_password@@’
#
# RCU database dba user name and password, required since we are going to let the Operator create the RCU schema
#
rcu_admin_password: ‘@@SECRET:rcu-schema-secret: dba_password@@’
rcu_db_user: ‘@@SECRET:rcu-schema-secret: dba_user@@’
#
# TNS name to be used for the ATP database
#
tns.alias: ‘@@SECRET:rcu-schema-secret: tns_alias@@’
#
# We are going to use the single signon wallet
#
javax.net.ssl.keyStoreType: SSO
javax.net.ssl.trustStoreType: SSO
javax.net.ssl.keyStore: cwallet.sso
javax.net.ssl.trustStore: cwallet.sso
topology:
Name: ‘sample-domain1’
AdminServerName: “admin-server”
Cluster:
‘cluster-1’:
Server:
‘admin-server’:
ListenPort: 7001
‘managed-server1’:
ListenPort: 8100
Cluster: ‘cluster-1’
‘managed-server2’:
ListenPort: 8100
Cluster: ‘cluster-1’
–from-literal=rcu_prefix=<rcu prefix you choose> \
–from-literal=schema_password=<rcu schema password you choose for the rcu schemas to be created> \
–from-literal=dba_password=<dba user password – supplied when creating the ATP instance> \
–from-literal=dba_user=<dba user name – supplied when creating the ATP instance> \
–from-literal=tns_alias=<found it in the database connection page>
unzip weblogic-deploy.zip -d $HOME/weblogic-deploy
cd $HOME/weblogic-deploy/bin
Next, use the WebLogic Image Tool (download) to create a domain creation image. The domain creation image contains the WebLogic Deploy Tooling installation and models for the domain; the Operator use this image to create the WebLogic domain.
unzip imagetool.zip -d $HOME/imagetool
cd $HOME/imagetool/bin
./imagetoo.sh cache addInstaller –type wdt –version latest –path <path of the WDT installer>
./imagetool.sh createAuxImage –tag <image name and tag> \
–wdtVersion latest
docker push <image name and tags>
- Click on Middleware
- Click on fmw-infrastructure_cpu
- Accept the license
- Get the docker image tag information. For example: container-registry.oracle.com/middleware/fmw-infrastructure_cpu:<latest tag>
- Create the Persistent Volume Claim.
initializeDomainOnPV:
persistentVolumeClaim:
metadata:
name: wko-domain-inpv-pvc-op
spec:
storageClassName: “wko-domain-in-pv-sc-new”
resources:
requests:
storage: 10Gi
- Create the RCU schema
initializeDomainOnPV:
…
domain:
# DomainAndRCU – operator will create the RCU schema for us.
# Domain – operator will use the RCU schema created manually by other means.
createIfNotExists: DomainAndRCU - Create the WebLogic JRF domain
domainCreationImages:
# TODO: change the name to match yours
– image: <domain creation image tag>
imagePullPolicy: Always
domainType: JRF
opss:
walletPasswordSecret: sample-domain1-opss-wallet-password-secret
# TODO: change to match the image you want to use
# How to mount the persistent storage , we are using the pvc
# Make sure the domainHome is under the mountPath
# and we will reuse the same PersistentVolumeClaim name further down.
# Domain – operator will use the RCU schema created manually by other means.
# TODO: change the name to match yours
# This is referenced by domain.spec.webLogicCredentialsSecret in the domain resource YAML
kubectl -n sample-domain1-ns create secret generic sample-domain1-weblogic-credentials –from-literal=password=<weblogic administrator password> \
–from-literal=username=<weblogic administrtor user name>
# passphrase to use when operator exporting the opss wallet. This is the passphrase used to encrypt a special key used for domain recovery when the
# domain home is corrupted and cannot be recovered, so that it can reuse the existing RCU schema in the database
# This is referenced by domain.spec.configuration.initializeDomainOnPV.domain.opss.wallePasswordSecret in the domain resource YAML
kubectl -n sample-domain1-ns create secret generic sample-domain1-opss-wallet-password-secret \
–from-literal=walletPassword=<passphrase to be used when exporting encryption wallet key>
# docker registry image pull secrets. This is the image pull secret for the base weblogic image, you will need to login to container-registry.oracle.com and navigate to # # the image page and accept the license first
# This is referenced by domain.spec.imagePullSecret in the domain resource YAML
kubectl create secret docker-registry ocr-regcred –docker-server=container-registry.oracle.com \
–docker-username= \
–docker-password= \
–docker-email= \
-n sample-domain1-ns
# This is the image pull secret for domain creation image
# This is referenced by domain.spec.imagePullSecret in the domain resource YAML
kubectl create secret docker-registry ocir-regcred \
–docker-server= \
–docker-username= \
–docker-password= \
–docker-email= \
-n sample-domain1-ns
NAME READY STATUS RESTARTS AGE
sample-domain1-admin-server 1/1 Running 0 72m
sample-domain1-managed-server1 1/1 Running 0 70m
sample-domain1-managed-server2 1/1 Running 0 70m
cd /share/logs/sample-domain1
ls
Post actions:
Set up other ways to access the domain for other daily operations. Use other tools such as WebLogic Console, WLST, and FMW Control console to make changes to the domain instead of changing the domain creation image, any subsequent updates to the domain creation image are ignored.
Back up the persistent volume, Oracle Cloud Infrastructure provides high reliability for the persistent storage, make sure the domain home is always backed up by taking snapshots of the file system, replicating to a different region, or backing up to the premise storage.
Follow the steps outlined in Best practices immediately, it outlined the steps to safe guide the recovery of a domain home directory in case of disaster.
We have created a JRF domain on PV in OKE cluster. For more information, visit Domain on PV documentation for details.
