Check Point’s CloudGuard AppSec analyzes web transactions with a set of Artificial Intelligence engines that operate in unison to protect against sophisticated attacks. This blog provides an overview of CloudGuard AppSec and how you can use it to secure your web applications running on Oracle Kubernetes Engine.
Solution overview
CloudGuard AppSec has the following primary components:
-
Web application protection (Advanced WAF)
-
API security
-
Anti-bot protection
-
Intrusion prevention
Web application protection
The first component of AppSec, the WAF, runs a two-stage request analysis.
The first stage is fast, and usually 95% of the requests are determined as non-suspicious. The suspicious requests go to a second stage, in which they undergo a deeper analysis that uses three patent-pending AI engines: User reputation scoring, application awareness scoring, and indicator scoring.
This three-score combination, with the addition of pattern learning, leads to an accurate decision that includes the following benefits:
-
Superior false-positive rate than traditional WAF. Decisions are based on matches to signatures.
-
Blocks different attack scenarios that aren’t blocked with a signature-only approach
-
Reduction in administration time because you don’t need to constantly tune the engine, create exceptions, disable signatures, and more.
API security
Frequently, software developers don’t include verification of API input in their code. The AppSec API security component provides two protection models: Positive and negative. Administrators can enable one or both.
The positive model delivers preemptive protection for possible API vulnerabilities through a schema validation procedure. API schemas in OpenAPI, such as Swagger, are uploaded to AppSec. Incoming API requests are validated against these schemas to block all invalid API requests.
The negative model uses the WAF and automatically detects and blocks malicious payloads in the API.
Anti-bot protection
AppSec anti-not protection component performs the following procedure:
-
Inject scripts into web application pages, such as login pages.
-
Collect data about input patterns and canalize key stroke sequences, mouse moves, and finger touches. Bots don’t use such patterns. If a bot artificially creates such patterns, AppSec identifies them.
-
Decide if the input is entered by a human or by an automatic script, such as a bot, and block this activity.
Intrusion prevention (IPS)
IPS provides traditional signature-based protections for over 2800 web-based common vulnerabilities and exposures (CVEs).
Integration architecture
One method of integrating CloudGuard AppSec deploys a nano agent Docker that attaches to an NGINX Kubernetes ingress Docker and provides all the CloudGuard AppSec features with the following steps. For all deployment methods, see the full documentation.
-
Configure your web application and API assets with the configuration wizard on Check Point’s Infinity Portal.
-
Enforce policy and install nano agents.

Figure 1: Integration architecture
Deployment use case
To understand the solution better, we’re deploying a web application on an Oracle Kubernetes Engine (OKE) cluster and using CloudGuard AppSec to protect it.
Prerequisites
-
A Check Point Infinity Portal account. If you don’t have an account, create one. Contact Check Point for subscriptions.
-
An Oracle Cloud Infrastructure (OCI) account. If you don’t have an account, you can sign up for an Oracle Cloud Free Tier account. You need the required permissions to manage and deploy resources.
-
A working Oracle Kubernetes Engine cluster: The web application can run anywhere within OCI. This use-case focuses on securing a web application running on Kubernetes cluster.
Topology
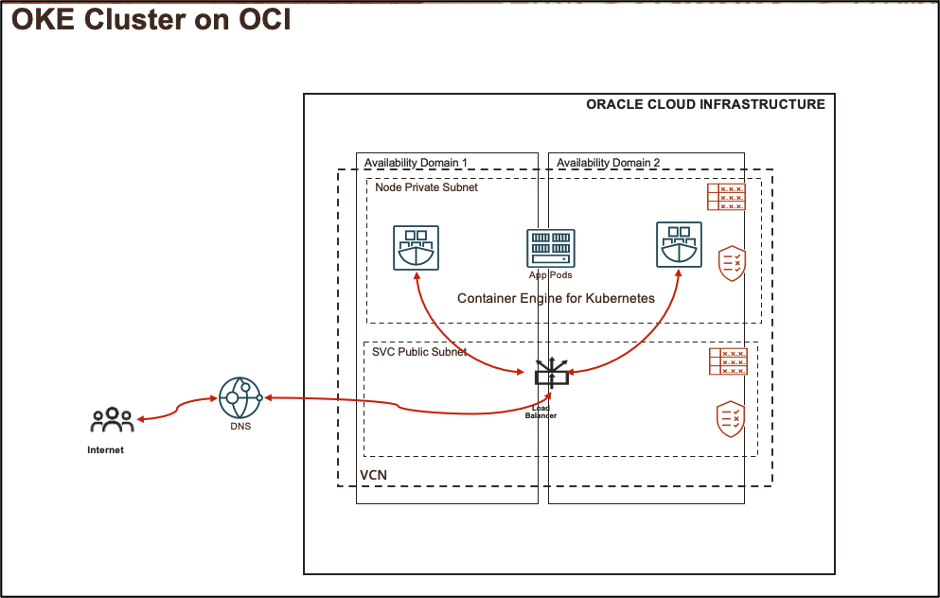
Figure 2: Use case topology
Configuration
You can follow this section, which gives you an overview on what you need to deploy and secure your application.
Ensure that you can connect to OKE cluster nodes from your local machine. Create a Kubernetes profile on the CloudGuard AppSec Console the following information:
-
Enter a user-friendly name.
-
Add an optional tag name.
-
Choose the sub type as application security
Note the Helm chart command, which we use to deploy an NGINX ingress controller with nano agent pods.
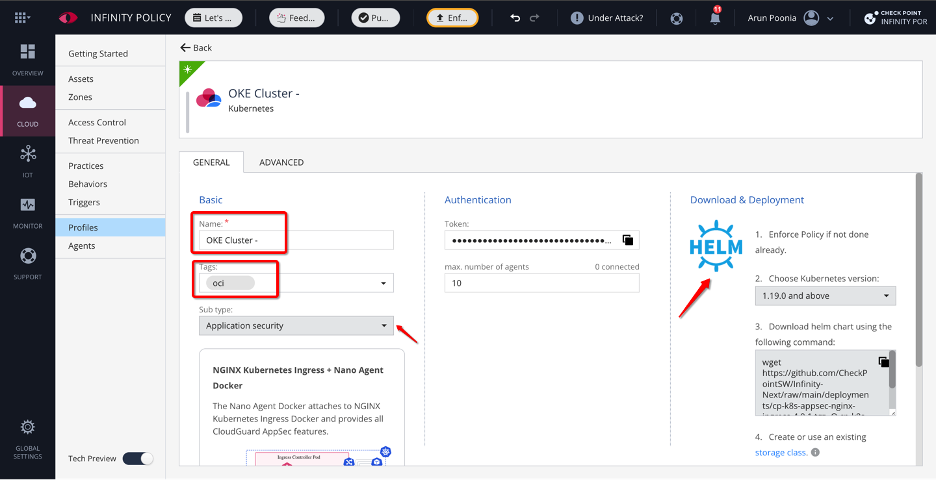
Figure 3: Adding an OKE bluster on CloudGuard AppSec configuration wizard
Run kubectl or Helm commands from your local environment that can access the OKE cluster. Create a namespace using the following command:
kubctel create namespace validate-app-sec
Deploy the NGINX Reverse Proxy pod with Helm chart instructions within the newly created namespace and verify.
helm install cp-k8s-appsec-nginx-ingress-4.0.1.tgz --name-template cp-appsec \\n--set appsec.agentToken="cp-us-XXXXXXXXXX" \\n--set appsec.persistence.storageClass="oci-bv" --namespace validate-app-sec
(k8s-env) ➜ ✗ kubectl get pods -A | grep appsec
validate-app-sec cp-appsec-cpappsec-ingress-nginx-controller-866f9b9c6b-4mxhg 2/2 Running 0 25d
(k8s-env) ➜ ✗
Install the Juice Shop application on your cluster using the Helm chart and verify. Juice Shop is an automated and scalable open source solution that can integrate various security vulnerability scanners with a simple and lightweight interface.
helm install my-juice-shop securecodebox/juice-shop --version 3.6.0 -n validate-app-sec
(k8s-env) ✗ kubectl get pods -A | grep juice
validate-app-sec my-juice-shop-7b9f7658df-2wb7g 1/1 Running 0 25d
(k8s-env) ✗
Save the following file to deploy ingress controller using NGINX class: file_name.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations:
name: ingress-wildcard-host
namespace: validate-app-sec
spec:
ingressClassName: nginx
rules:
- host: juice.oke.example
http:
paths:
- backend:
service:
name: my-juice-shop
port:
number: 3000
path: /
pathType: Prefix
Apply the changes using the following command and verify:
kubectl apply -f your_file_name.yaml(k8s-env) ✗ kubectl get ingress -A
NAMESPACE NAME CLASS HOSTS ADDRESS PORTS AGE
validate-app-sec ingress-wildcard-host nginx juice.oke.example 129.158.45.236 80 25d
(k8s-env) ✗
Ensure that the ingress controller was created successfully and that you can access the application locally using http://juice.oke.example. Create a local host entry to simulate DNS resolution.
Add an asset pointing to your application within the Infinity Policy console using the following parameters:
-
Enter a user-friendly name.
-
Select the Kubernetes profile created earlier.
-
Enter the web application’s URL pointing to http://juice.oke.example.
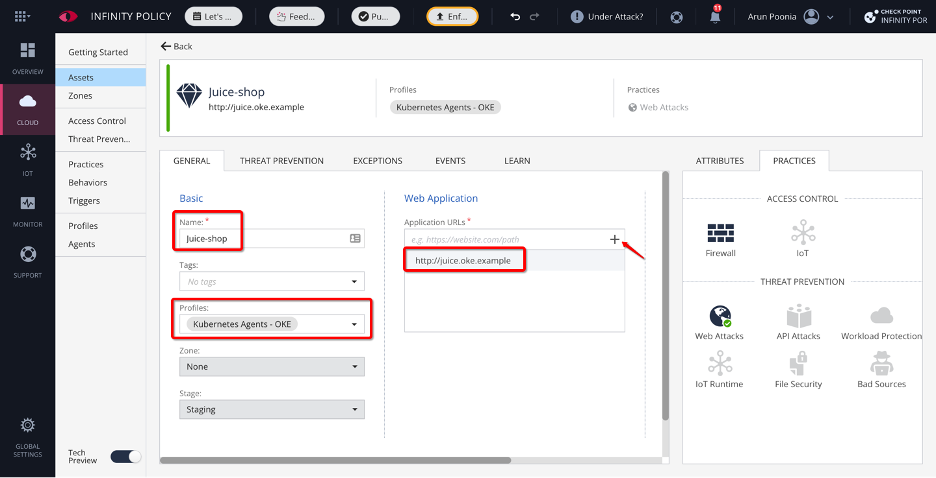
Figure 4: Add application URL as an asset
Navigate to your asset and select the Threat Prevention tab as shown in the following graphic and select one of the following options. Then, enforce and publish your changes.
-
Learn/Detect: This option allows the Check Point AppSec solution to ingest new datasets to ML and AI engines and improve the automated protection.
-
Prevent: You can start with prevention and learn in the process or change to protect when the Check Point AppSec has learned enough. Preventing attacks is the main goal of security solutions.
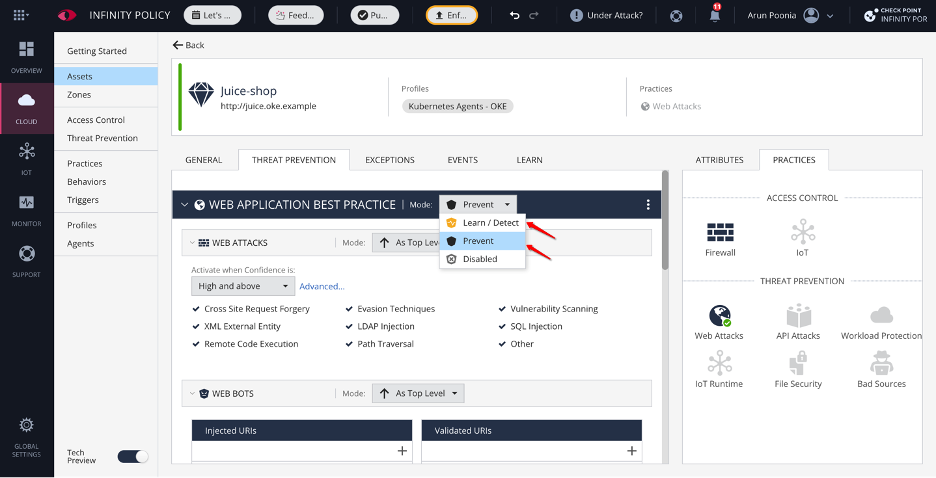
Figure 5: Select appropriate profile to learn and protect application traffic
Validation
After publishing your changes, CloudGuard AppSec starts monitoring your application traffic. We’ve enabled the Protect profile, so for test purposes, we use SQL Injection to see how it behaves.
SQL injection is a common vulnerability where an attacker injects malicious SQL code into the SQL query running on the server-side. SQL query running on the server side takes the client’s input as a parameter. An attacker can modify the query in a way that exposes, modifies, or destroys the data in the database.
The Juice Shop isn’t properly validating user inputs, leaving the possibility of SQL injection attack.
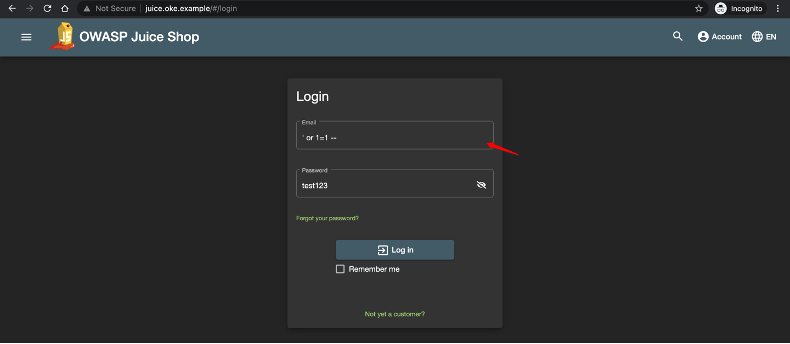
Figure 6: Application login with SQL injection
When you log in, it prevents you from logging to Juice Shop and generates an incident ID.
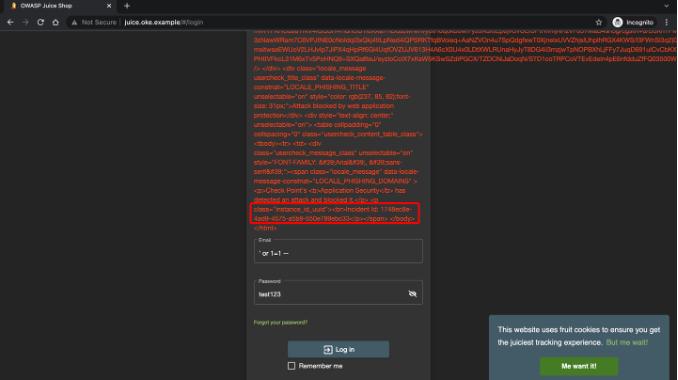
Figure 7: Incident ID
You can see this incident ID within CloudGuard AppSecurity Monitor on the AppSec dashboard, as shown in the following figure:
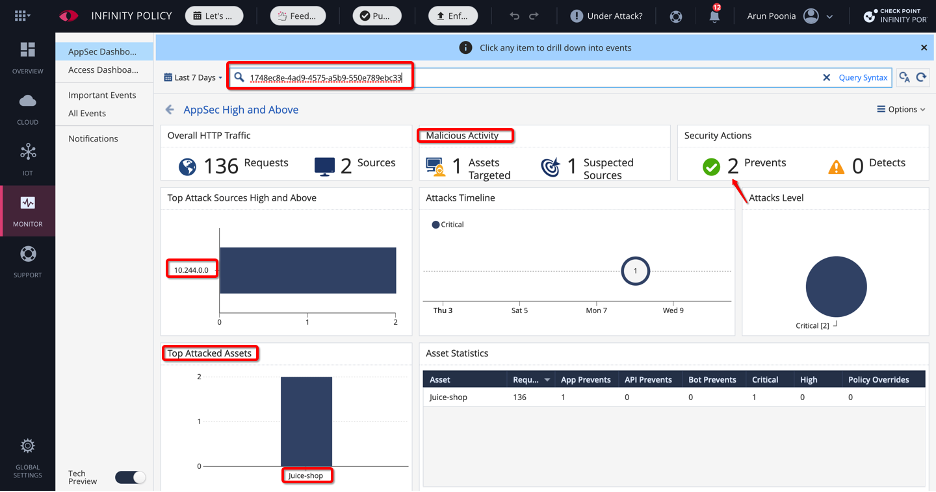
Figure 8: AppSec dashboard
Similarly, you can search incident id within all events:
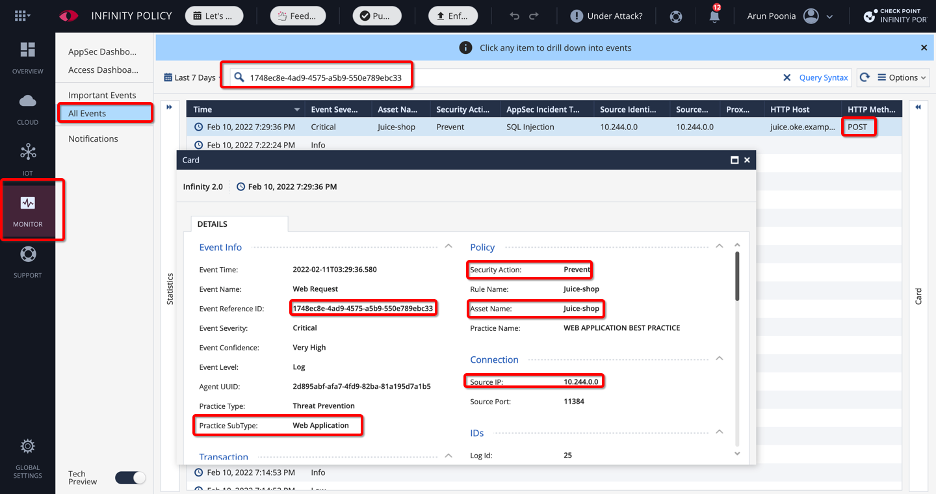
Figure 9: Monitor application threat
Conclusion
This post highlights the Check Point CloudGuard AppSec solution, which enables web application-level security for end customers. It shows how you can monitor and protect web applications running on Oracle Kubernetes Engine cluster nodes.
Ready to learn more about the Check Point CloudGuard AppSec Solution for Oracle Cloud Infrastructure? Check out the documentation today!


