Purpose of security
As the gatekeeper and the person responsible for protecting and securing all access to the data within your database, you should constantly be on top of all changes and improvements happening every day in this field. To be able to do this, first, you need to have a complete understanding of how to protect your data against all possible situations you could come across in your profession and keep an eye on all compliances and regulatory changes happening in your region.
Database security, and data protection, are always rigorously regulated. Although the law struggles to keep up with the constant changes of an evolving digital world, regulations call for specific standards from any business with an online element. Furthermore, users around the globe believe their privacy to be taken seriously, and modern entities must reflect this wish to succeed in today’s market. Therefore, in today’s world, every company must prioritize database security.
Compliance is also an essential part of any database security solution. This is because many of the regulations and laws provided for compliance focus on authentic problems faced by many global enterprises, which must be considered.
Database security is a crucial part of implementing IT security in an organization; sadly, it falls short most of the time because many regulations focus more on monitoring and measuring as opposed to real-time prevention of threats to the database and systems.
The Objective
When it comes to security compliance, taking as per example one of the most popular information security frameworks/standards like ISO-27001/002 that require proof of periodic security and data recoverability reviews/tests (as part of a disaster and recovery plan and continuity procedures, and internal audits), to ensure the confidentiality, integrity, and availability of our data are being applied.
So, why do not combine these two requirements by running a database disaster and recovery test using Oracle Data Guard (that would be part of your operating procedures for IT management) and checking at the same time the database for possible security deviations for access control (and much more) by using Oracle Database Security Assessment Tool (DBSAT)? This will allow your organization to kill two birds with one stone quickly and, in the process, document a review procedure that can be executed periodically as part of your compliance activities (generating audit logs as results for your internal audits).
The Database Security Assessment Tool (DBSAT) is an incredible free command line tool provided by Oracle Corporation as a utility to help you verify your database for common database security issues (including security policies and controls in place), as well as help to identify possible sensible data stored within the database. To be able to use it, you need to have a valid Oracle Support CSI and download it from My Oracle Support [Doc ID 2138254.1]
The DBSAT tool contains three modules:
- Collector
- Reporter
- Discoverer
Collector and Reporter work together to discover any risk areas and will produce reports regarding those risk areas – the Database Security Assessment report. The Discoverer is a stand-alone module used to locate and report on sensible data – and will produce the Database Sensitive Data Assessment report. Plus, DBSAT includes a few companion utilities (Reporter JSON output format
), they are:
- DBSAT Extract – Python program that enables you to extract findings by their identities
- DBSAT Diff – Python program that enables you to compare two reports and find the differences
Note: You can download the above DBSAT companion modules from the same My Oracle Support document you used to download the DBSAT tool [Doc ID 2138254.1].
The Environment
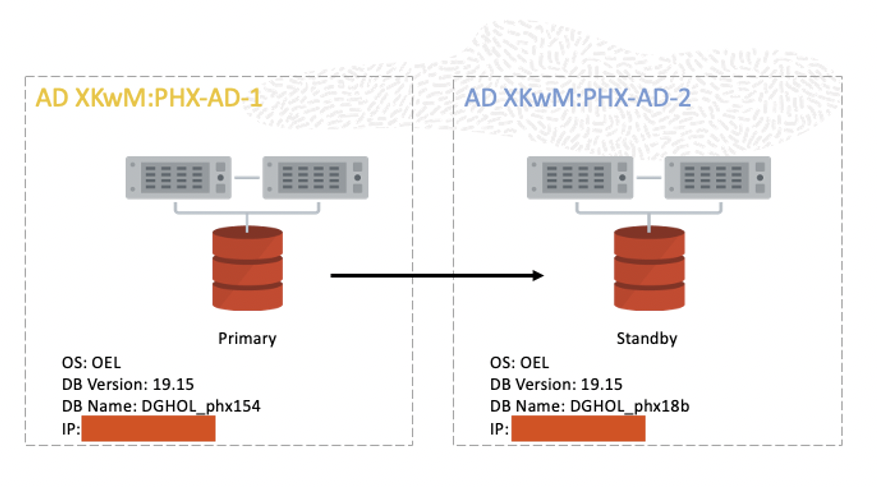
For this example, we will use the free practice environment available within the “Protect your data with Oracle Active Data Guard” workshop at Oracle LiveLabs, which can be found here. It comprises two instances across two Availability Domains (AD), with one instance with the primary role and another with the standby role.
Prerequisites
After enrolling in the LiveLabs “Protect your data with Oracle Active Data Guard”, please follow the lab instructions to establish connectivity to the OCI environment.
Note that DBSAT is only certified to run on the following operating systems:
- Solaris x64 and Solaris SPARC64
- Linux x86-64
- Windows x64
- HP-UX IA (64-bit)
- IBM AIX (64-bit) & Linux on zSeries (64-bit)
You can run the DBSAT tool on any Oracle Database 10.2.0.5 or later, and it can be used on-premises or in Cloud environments. DBSAT can also be run against Oracle Base Database Service (PaaS/DBaaS) and Autonomous Databases (ADWC or ATP).
The zip, unzip, and Python software must be installed on the server. You can easily install them by issuing the below command:
# yum install -y zip unzip python
Also, you can easily verify if you have Python installed (2.6 or later is required) on the server by issuing the following command at OS level:
# python -v
Python
2.6.6
Finally, you can verify if zip and unzip are installed on your server by issuing the following commands.
# zip -v
Copyright (c) 1990-2008 Info-ZIP – Type ‘zip “-L”‘ for software license.
This is Zip 3.0 (July 5th 2008), by Info-ZIP. Currently maintained by E. Gordon. Please send bug reports to the authors using the web page at www.info-zip.org; see README for details.
…
# unzip -v
UnZip 6.00 of 20 April 2009, by Info-ZIP.
Maintained by C. Spieler. Send
bug reports using http://www.info-zip.org/zip-bug.html; see README for details.
Latest sources and executables are at ftp://ftp.info-zip.org/pub/infozip/ ;
see ftp://ftp.info-zip.org/pub/infozip/UnZip.html for other sites.
Compiled with gcc 4.4.7 20120313 (Red Hat 4.4.7-17) for Unix (Linux ELF) on Jan 10 2017.
…
For running the discoverer module, you will need at least Java 1.8 JDK installed and running on your environment, and the JAVA_HOME environment variable needs to be set.
You can check if java is running on your environment by issuing the following command:
# java -version java version “1.8.0_181” Java(TM) SE Runtime Environment (build 1.8.0_181-b12) Java HotSpot(TM) 64-Bit Server VM (build 25.181-b12, mixed mode) # whereis java java: /usr/bin/java # export JAVA_HOME=/usr/bin/java
DBSAT Installation
Download DBSAT from here.
The installation of DBSAT is a very simple process:
- Log in to the database server you wish to use DBSAT
- Create the DBSAT directory – $ mkdir -p /home/oracle/dbsat
- Download the dbsat.zip file and copy it to the database server and unzip it – $ unzip dbsat.zip –d /home/oracle/dbsat
- And you are ready to go
Collector Prerequisites
The installation of DBSAT is a straightforward process. To collect all data, the Oracle DBSAT Collector must be run on the server containing the database because it executes some operating system commands to collect process and file system information that cannot be obtained from the database. In addition, the Oracle DBSAT Collector must be run as an OS user with read permissions on files and directories under ORACLE_HOME to collect and process file system data using OS commands.
The Oracle DBSAT Collector collects most of its data by querying database views. Therefore, it must connect to the database as a user with sufficient privileges to select from these views. Therefore, grant the DBSAT user the following privileges:
- CREATE SESSION
- READ or SELECT on SYS.REGISTRY$HISTORY
- Role SELECT_CATALOG_ROLE
- Role DV_SECANALYST (if Database Vault is enabled or if Database Vault Operations Control is enabled)
- Role AUDIT_VIEWER (12c and later)
- Role CAPTURE_ADMIN (12c and later)
- READ or SELECT on SYS.DBA_USERS_WITH_DEFPWD (11g and later)
Note: If you plan to run only the Collector component, you can assign only the following privileges:
- CREATE SESSION
- Role SELECT_CATALOG_ROLE
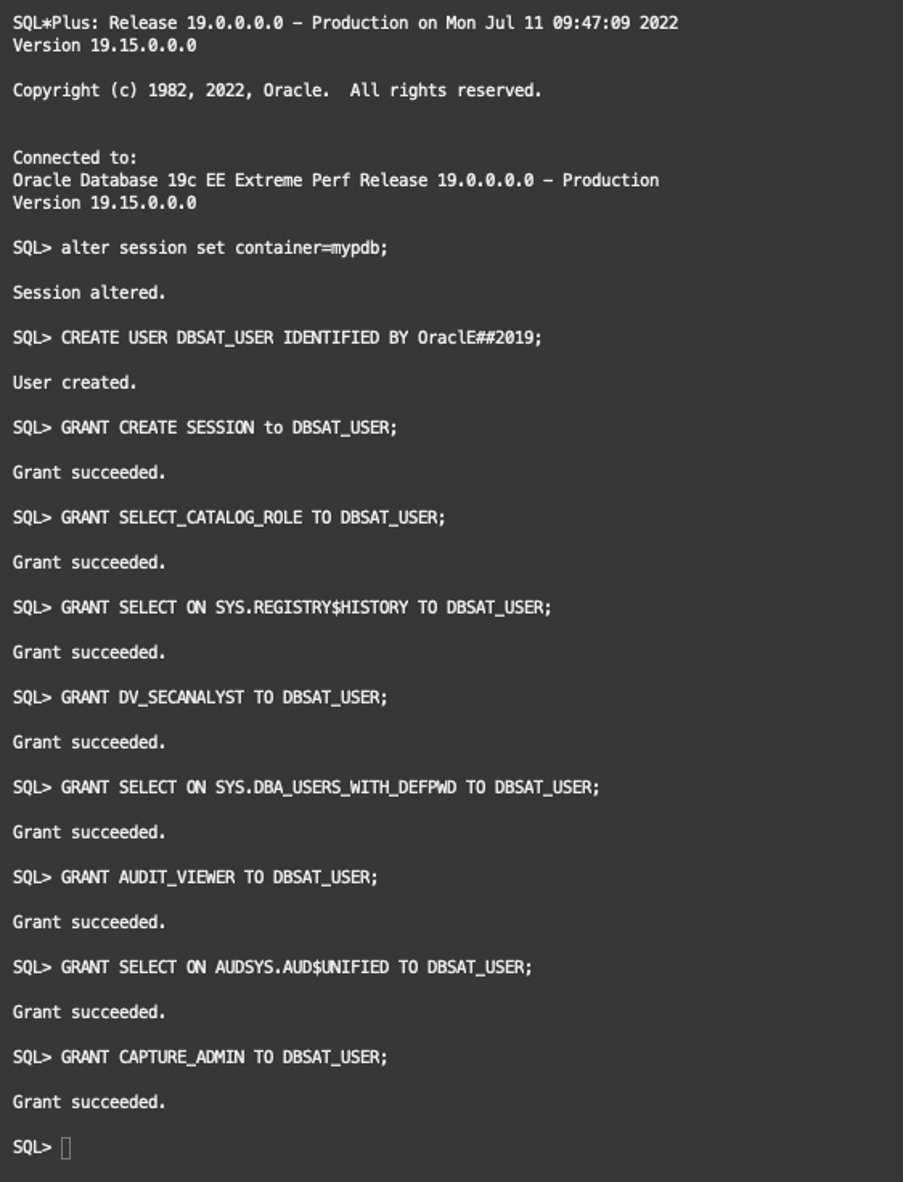
To successfully collect database vault information in a database vault-protected environment, you must connect as a non-SYS user with the DV_SECANALYST role. So, for this, we will connect to the pdb (pluggable database) called “mypdb” and create a user called “DBSAT_USER” with all required privileges to be able to run DBSAT later.
Important: If Database Vault is enabled, please connect as DV_ACCTMGR to run the commands below.
SQL> ALTER SESSION SET CONTAINER=mypdb; (If connected to the CDB)
SQL> CREATE USER DBSAT_USER IDENTIFIED BY OraclE##2019;
SQL> GRANT CREATE SESSION to DBSAT_USER;
SQL> GRANT SELECT_CATALOG_ROLE TO DBSAT_USER;
SQL> GRANT SELECT ON SYS.REGISTRY$HISTORY TO DBSAT_USER;
SQL> GRANT DV_SECANALYST TO DBSAT_USER; (If Database Vault is enabled)
SQL> GRANT SELECT ON SYS.DBA_USERS_WITH_DEFPWD TO DBSAT_USER; (if 11G or later)
SQL> GRANT AUDIT_VIEWER TO DBSAT_USER; (if 12c or later)
SQL> GRANT SELECT ON AUDSYS.AUD$UNIFIED TO DBSAT_USER; (if 12c or later)
SQL> GRANT CAPTURE_ADMIN TO DBSAT_USER; (if 12c or later)
Now that we have our environment created and ready to go, in the next part of this tutorial, we will use this environment to play with DBSAT and Active Dataguard to achieve our security and availability goals. So be tuned for our next blog post!
Want to learn more?
Check these amazing content about Oracle MAA and MSA available for you:
- Oracle Maximum Availability Architecture (MAA) Main Page – https://bit.ly/3ysinDY
- Database Security Main Page – https://bit.ly/3NSJWw3
- Cyber Security Blog – https://bit.ly/3yPVZpG
- Cyber Security Technical Paper – https://bit.ly/3akX1Ao
- Securing the Oracle Database – a technical primer (free 4th edition) – https://bit.ly/3bUYQVa
- DB Security – DBSAT Workshop Free Lab – https://apexapps.oracle.com/pls/apex/r/dbpm/livelabs/view-workshop?wid=699&clear=RR,180&session=15375272388130
- Security Free Labs – https://bit.ly/3NLjCDW
- Disaster and Recovery Free Labs – https://bit.ly/3yms6vK
