Introduction
Multicloud is a cloud computing strategy that incorporates the best services from more than one public cloud provider to deploy a solution. This enables customers to meet diverse business requirements and ensure they are choosing the best cloud provider for each workload, based on capabilities, requirements, and performance.
With Oracle Cloud Infrastructure (OCI) being one of the leading cloud platforms, organizations often find themselves in the position of utilizing OCI services along with at least one other cloud provider to meet their business requirements.
But as organizations adopt multicloud strategies, the need to seamlessly integrate and manage resources across multiple cloud providers can become a challenge. One of the critical issues faced by enterprises in a multicloud environment, is managing Identity and Access Management (IAM) across multiple cloud platforms.
A multicloud IAM solution simplifies administration and plays a vital role in ensuring secure access to resources, controlling permissions and maintaining compliance. Oracle Cloud Lift Services has implemented solutions that address these challenges for various enterprise customers in multicloud environment setup.
OCI IAM
Along with various IaaS, PaaS, and SaaS services, OCI offers Identity as a Service (IDaaS), which provides Identity Governance (Joiner-leaver-Mover) and single sign-on (SSO) capabilities to customers (Service name is OCI-Identity-Domain/IDCS).
OCI-Identity-Domain supports various standards (SAML, OAuth, OIDC, SCIM etc.) to integrate with most of cloud providers (Microsoft Azure, Amazon AWS, Google Cloud, Alibaba, IBM Cloud, Tencent Cloud, OVHcloud, DigitalOcean etc.). This type of integration not only enhances operational efficiency and user experience, but also strengthens security in their multicloud architecture. Such integrations are already designed and implemented for various enterprise customers by Oracle Cloud Lift Services.
In this article, we will deep dive into key components of OCI integration with Azure Active Directory (AAD). This includes establishing trust relationships, enabling single sign-on, and synchronizing user identities and access policies. Additionally, we will discuss best practices, potential challenges, and strategies for ensuring security and compliance when managing IAM across OCI and Azure.
Architecture
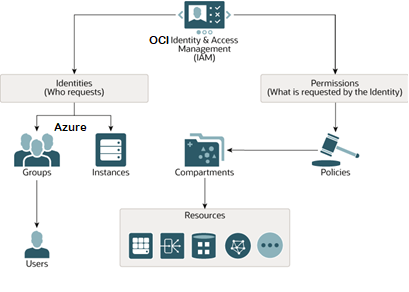
In this architecture, Azure serves as the authentication and authoritative source. So, the user’s identity management will take place from Azure to OCI via System for Cross-domain Identity Management (SCIM) mechanism, and users can access OCI resources using Azure credentials via federation setup. Once authentication is completed at Azure level, OCI may handle authorization via written policies/permissions.
This architecture supports the following components:
- Single Sign On (SSO): Single sign-on is an authentication scheme that allows a user to log in with a single ID to any of several related, yet independent, systems
- Federation: A feature that allows users to sign in to OCI resources using their Azure AD credentials.
- Security Assertion Markup Language (SAML): Is XML-based open-standard to setup federation trust between IdP(Azure) and SP(OCI-Identity-Domain)
- System for Cross-domain Identity Management (SCIM): SCIM protocol is used for Identity Federation
- Identity Federation: Is the management of identities in federation trust setup between IdP (Azure) and SP (OCI-Identity-Domain)
Before You Begin
Before you set up federation trust between Azure and OCI-Identity-Domain, please ensure the following:
- You have access to OCI-Identity-Domain with authorization to manage IdPs (Identity Domain Administrator or Security Administrator role)
- You have an Azure AD subscription and an admin/developer account, as well as having hands-on experience working with the Azure platform
- You know how to create an enterprise application in Azure and also add users to it
- You have a Unique identifier (UserName/Email/UPN etc) to map with SAML NameID attribute
Configuration Steps
To integrate these two platforms, follow these steps:
- Establish a trust relationship between OCI IAM and Azure AD
- Configure SSO between OCI and Azure AD
- Define access policies and roles
- Implement multi-cloud authentication
- Explore Just-in-time (JIT) provisioning
Testing Steps
For testing follow these steps:
- Login to Azure and create test account
- Set credentials for newly created account in Azure
- Assign this user to enterprise applications created in Azure for OCI
- Sync users from Azure to OCI-Identity-Domain
- Access OCI Login URL and select “Azure-IDP” option to login
- Provide user’s Azure credential and observe seamless login
Implementation considerations
1. For Synchronize users and groups from Azure to OCI, following are supported: –
- The application template from the Azure AD gallery- SCIM Based
- Just-in-Time (JIT) provisioning
2. Currently Azure application template has 40 min sync interval that can be eliminated with combining JIT with SCIM. It depends on what’s best suited for customer, they can co-exist but has some operational overhead as stated in configuration steps.
3. By default, Azure enterprise application provides attribute mapping of many attributes like Address, Passcode, City etc. those may not be required. It is better to remove them, as by keeping them additional validation is needed from both sides (OCI-Azure). Another beneficial consideration would be to add ‘isfederated‘ flag mapping in azure side, in order to distinguish local users from federated in OCI. Please refer to the testing steps regarding this.
Conclusion
Oracle’s OCI IAM and Azure AD are powerful identity management solutions that each offer robust features. However, some organizations desire an integrated approach that allows them to seamlessly manage user identities, access controls, and policies across both OCI and Azure. This is where the integration of OCI IAM with Azure becomes crucial. By establishing a bridge between these two cloud platforms, organizations can leverage the strengths of each platform while maintaining consistent IAM practices. This blog provided steps for Azure integration with OCI IAM, but the same is also applicable for other Cloud platforms.
Note:- Configurations and testing steps may vary depending on the version and capabilities of the respective platforms at the time of implementation. It’s always recommended to refer to the official documentation and guidelines provided by Oracle and Microsoft for the most up-to-date and accurate instructions.
