As customers adopt growing number of cloud applications, there is a huge demand to deliver seamless user experience for the employees and other end users. One of the topics that keep coming up in this area is Single sign (SSO) and identity federation. In this article, we will review some of the basic concepts for SAML and try to understand key differences between SP initiated vs idP initiated SSO flows.
Oracle Cloud HCM supports federated SSO leveraging SAML 2.0 to enable secure cross-domain communication. The security administrator can configure SSO between Oracle Cloud HCM and SAML-compliant identity management system such as Oracle Identity Cloud (IDCS) or Microsoft Active Directory Federation Services etc. For purpose of this article, I am using Oracle IDCS as the idP and Oracle Cloud HCM -20C as the SP.
SAML Basics:
The Security Assertion Markup Language (SAML) was developed by the Security Services Technical Committee (SSTC) of the standards organization OASIS. It is a standard that defines a framework for exchanging security information between online business partners. This security information is expressed in the form of portable SAML assertions that applications working across security domain boundaries can trust.
Participants involved in a SAML Integration:
-
Service Provider (SP): Service providers provide services, resources etc to the end user. For e.g. Oracle Cloud HCM is the SP providing HCM services (self-service, payroll, compensation, benefits, talent, recruiting, etc…)
-
Identity Provider (idP): Identity providers provide identification & authentication to end users.
-
User\User Browser: Consumers or end users (employees, job applicants, vendors, etc)
Let’s review what SP vs idP initiated SSO flows mean….
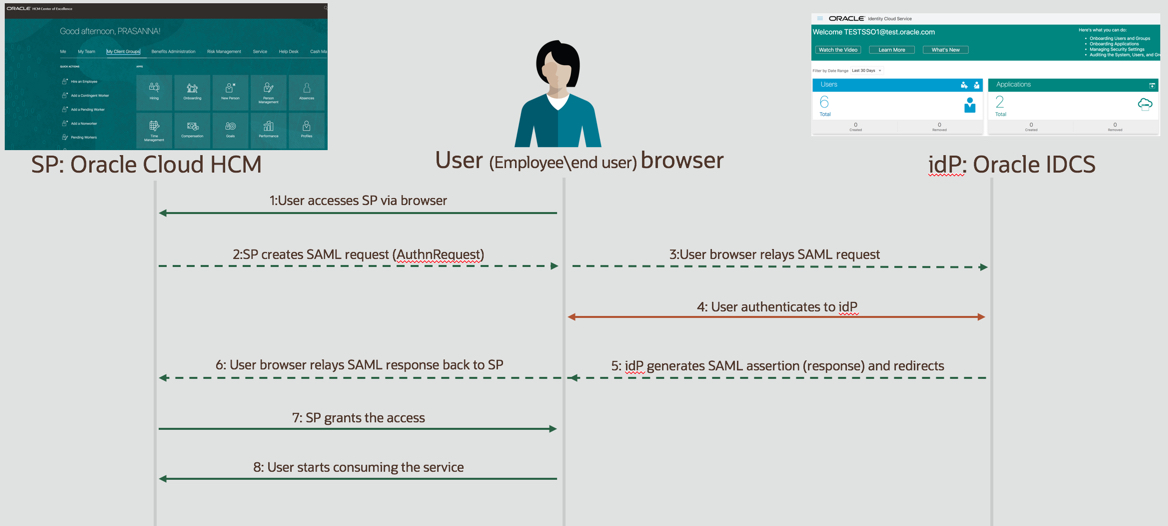
SP (Service Provider) Initiated SSO Flow
In this case the user will initiate the login process at SP (Oracle Cloud HCM) by typing the Oracle HCM URL in the browser. The SP (Oracle Cloud HCM) will redirect the user to the idP with the AuthnRequest\SAML request, hence the idP is well aware of SP who is initiating the SSO flow. This is critical because idP may be serving more than one Service providers and need to know who sent the request for redirection (post successful authentication).
For e.g. user begins the flow by typing the Oracle HCM URL like https://pod-dev1.login.us6.oraclecloud.com
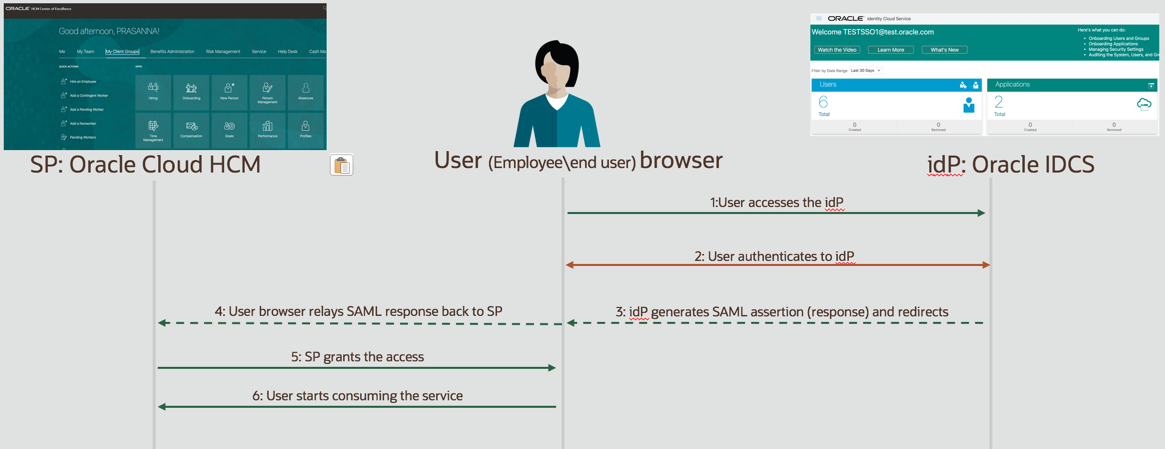
idP (Identity Provider) Initiated SSO Flow
In this case the user will initiate the login process at Idp (Oracle Identity Cloud) by typing a special URL configured in Oracle IDCS. Since idP may be serving more than one SP, idP needs to know the relay state\ where to redirect the user post successful authentication. The idP (Oracle IDCS) will send the SAML Response\Assertion to SP (Oracle Cloud HCM) which SP validates and allows the end user to access HCM Application. For e.g. the idP initiated sign in URL may look like
https://<idcs-instance>.identity.oraclecloud.com/sso/v1/app/launcher/<appId>?appName=<appname>
(This URL or method may vary based on your idP. For Oracle IDCS, the URL is generated for the App configured to setup the SSO)
Good luck with your implementation…
