Welcome to the final post in this series about using Terraform to manage infrastructure in the Oracle Cloud. In the last post, we looked at how to use the OCI CLI in our GitHub Actions pipeline to execute our Terraform scripts via creating stacks and jobs with Resource Manager. In this post, we’ll simplify the concept and make it a bit more portable by using native Terraform in our GitHub Actions pipeline. You’ll lose a bit of the power and flexibility of Resource Manager, but if you’re just looking to simply build and maintain your infrastructure, this solution is perfectly great for you!
If you’ve missed the previous posts in this series, here is a list to catch up:
-
Infrastructure as Code in the Cloud: Introduction to Terraform for Developers
-
Infrastructure as Code in the Cloud: Installing Terraform and Running Your First Script
-
Infrastructure as Code in the Cloud: Getting Started with Resource Manager
-
Infrastructure as Code in the Cloud: Advanced Terraform on the Oracle Cloud with Resource Manager
Building Infrastructure From Your Pipeline
Just like in our last post, we’ll need some secret values so that we can execute our Terraform scripts from our CI/CD pipeline. Set some secrets for the following values from your tenancy.
Running With Terraform
Using the OCI CLI to build our Terraform scripts via Resource Manager is nice, but if you remember from our last post, it wasn’t exactly a quick process since we had to install the CLI and all of the Terraform script execution happened in our cloud tenancy instead of on the pipeline/build server. Let’s see if we can improve the build times (and reduce a bit of the build script complexity) by executing our scripts natively in the pipeline.
We’ll start by defining our pipeline as we did before in a file called build.yaml.
Note: Like before, we’ll use the same GitHub project, but again branched: https://github.com/recursivecodes/oci-resource-manager-demo/tree/github-actions-tf
We’ve defined our environment variables again, but this time we prefixed them with TF_VAR_ which, if you remember back to an earlier post in this series, is a special prefix that Terraform will pick up on and set our script variables accordingly. Next, checkout the code and configure the Hashicorp “setup-terraform” plugin which will install Terraform in our build environment.
That’s all the config we need. Now we can run our scripts directly via the Terraform CLI as we did earlier in this series when we ran them manually on our own machine. Add steps to initialize Terraform and validate our script(s):
Then run terraform plan and terraform apply.
Check in and push the build and once again the pipeline will be executed automatically.
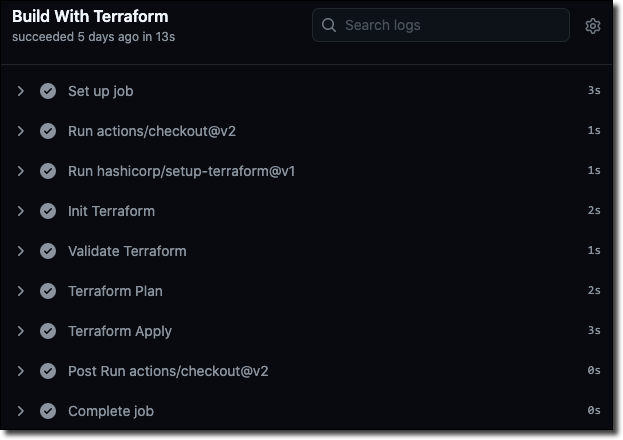
But this time, we get a much faster execution – from 3 minutes 17 seconds down to 13 total seconds.
Summary
In this post, we looked at executing our Terraform scripts to build our infrastructure in our CI/CD pipeline using the native Terraform CLI.
Series Summary
In this series, we have focused on Infrastructure as Code. From the very basic intro to Terraform for developers, to integrating our solution into our CI/CD pipeline we have dug deep into every aspect of automating our infrastructure and hopefully you have learned the basics and benefits of using using this solution in your cloud native applications. As always, please feel free to provide me your feedback and check me out on Twitter.
Photo by Pete Gontier on Unsplash
