While we all understand that thorough security checks are a must before going to production, the reality is that doing so cannot slow down DevOps processes. Businesses should not – and cannot – be put in a position where they need to decide between development speed and security. But how can teams achieve continuous regulatory compliance in highly scalable and dynamic Kubernetes environments without interpreting performance?
Based on what we see from our worldwide customers, here are actionable suggestions to truly enable continuous compliance that is practical, thorough, and will not impede performance:
- Maintaining compliance with industry regulations such as HIPAA, PCI-DSS, GDPR, and other regulations demands more than a snapshot of security processes. In a modern DevOps pipeline, build processes will continue to introduce new code, open source code and libraries, and external containers at different stages. Multiple teams will be deploying containers into staging and/or production Kubernetes platforms. Running containers will typically be scaling up and down frequently – sometimes this will mean crossing into multiple regions and multiple clouds. Kubernetes environments are a live system requiring security checks are consistently executed. These environments need continuous compliance with audit alerts and blocking that can work in real time.
- Security must be automated. Manually running a compliance check or vulnerability scan isn’t a realistic strategy for continuous security and compliance. There are tools, such as an automated Kubernetes audit log analyzer, to help process logs and events, as well as new types of SIEM tools use machine learning technology to help identify any malicious threat patterns as quickly as possible. Additionally, next-generation container security solutions are built with automated and ongoing monitoring and protection.
- Deep visibility with application context correlation makes a huge difference, as suspicious activities will often happen as a kill chain. For example: an unknown process launches inside a database container; it accesses or writes the sensitive files; it connects back to an external IP address or a hidden attacker behind the proxy; it hides some sensitive data inside the network payload to steal; it may issue the man-in-the-middle (MiTM) attack to the Kubernetes API service from within the Kubernetes network. All these malicious behaviors can be a strong indication of an zero-day attack, an unknown threat, a cryptomining container, or an insider attack. To get a clear view of the malicious behavior, a Kubernetes security solution must be able to see multiple places of the kill chain, understand the content of network payloads, and inform action to remediate threats before they are harmful.
- Security solutions must cover the full stack of the container environment. Compliance checks are not only for containers; they must also cover the Kubernetes platform, service meshes being used (like Istio), any plugins, and the hosting VMs. All potential attack surfaces should be monitored continuously.
- Prevention is better than cure. By meeting compliance in your Kubernetes environments you have ensured better security. Whenever possible, use a zero-trust security model to lock down Kubernetes environments securely, instead of waiting to analyze logs and then responding reactively. For example, NeuVector’s behavior-based learning and protection is able to block network attacks even before they reach the application.
As one example of how to approach this, DLP (Data Loss Prevention) technology is one of the critical safeguards that many compliance regulations are now requiring:
SOC 2 Requirment
Data Loss Protection (DLP) solutions are to be utilized to identify, monitor and protect data in use, data in motion and data at rest through content inspection and with a centralized management framework.
PCI DSS Requirment
Data Loss Protection (DLP) is an information security strategy for ensuring that intneral network users do not intentionally or unintentionallyextract and send sensitive organizational data outside of defined areas, typically outside the organization. This is defined via a policy that identifies the sensistive data and provides restritions on its area of use.
GDPR Requirment
DLP is necessary for implementing the GDPR’s “ingegrety and confidentiallity” principle and achieving compliance with the regualtion. The GDPR States that processor must ensure that personal data is not uses for any other purpose outside the services it was intended for. They must also prevent from being uploaded to personal cloud services and BYOD. DLP Solutions can asily help meet this requirement thorugh data monitoring.
HIPAA Compliance
Healthcare and personal records mustn’t leave the health provider’s or associated companies’ premises uneless it is encrypted or transmitted to the secure, autorized channels. Data Loss Prevention soltions are a big help in that direction. DLP allows organiziations to monitor and control data movement. it can scan documents before they are transferred and block them in case they contain sensitive information, such as Health Insurance Numbers, Social Security Numbers, Addresses, etc.
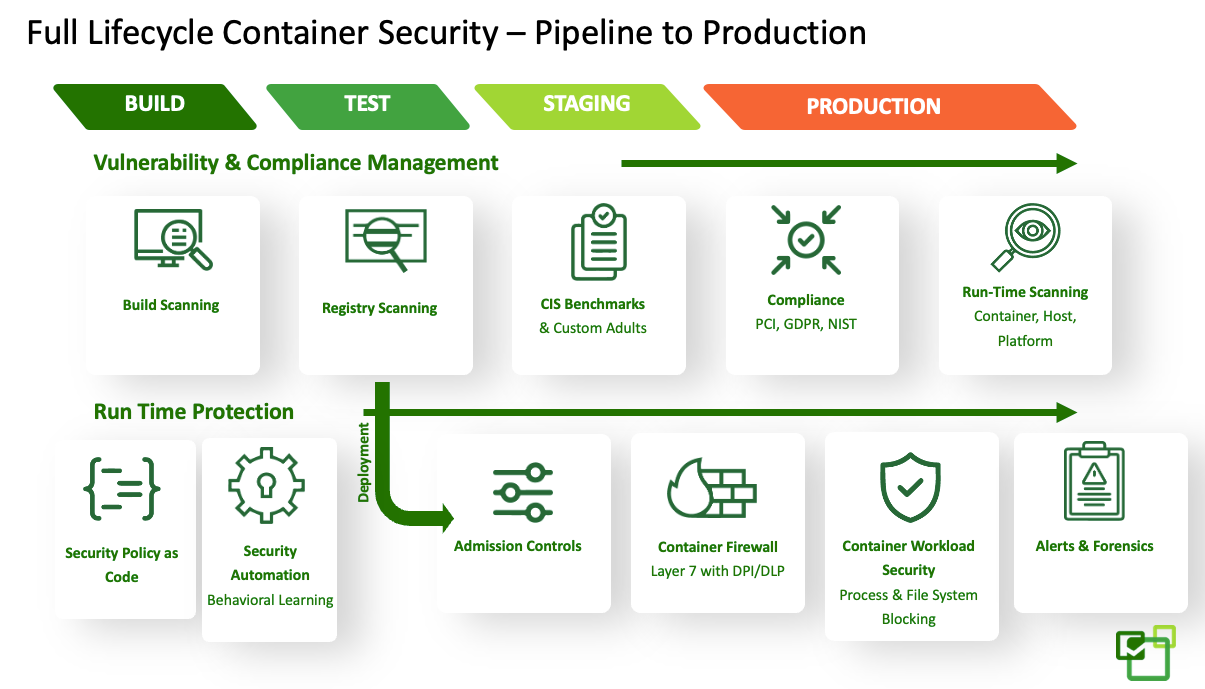
Another compliance auditing best practice is leveraging Kubernetes’ built-in capabilities. Kubernetes already supports auditing logs, and the Kubernetes API server is the central hub for all Kubernetes platform-related activities and events. It initiates, manages, and monitors all the resources in Kubernetes, making it is the best place for Kubernetes system log collecting. It’s a good practice here to collect all the activity logs and analyze these logs for symptoms of a compromised, abused, or misconfigured system. Doing so can also help identify non-compliant behavior at runtime, or investigate a specific operational or security problem. You can also trace back the events in logs to find the root cause and take actions to patch or set security policies.
To enable the Kubernetes auditing logs, an audit policy needs to be in place. The audit logs can be configured to be stored in persistent storage or sent over webhook. More details and examples can be found at: https://kubernetes.io/docs/tasks/debug-application-cluster/audit/.
But this is not enough. As headlines continue to show, the container applications themselves are the most attractive attack targets. The application behavior logs, network activities, file activities, and process activities all demand continuous compliance auditing. Modern Kubernetes security technologies like NeuVector are able to report these behavior logs and activities at runtime.
Leveraging the built-in Kubernetes Admission Control function can ensure that the platform and security tools like NeuVector are working together to actively prevent unauthorized and vulnerable deployments. This is another critical requirement of many compliance regulations.
Finally, understand that the host platform is the base of Kubernetes services. Today, most of the well-known Kubernetes hosting platforms are already being hardened and under regular compliance auditing. It is the cloud platform’s responsibility to keep the host system secure and compliant. For example, Oracle Cloud has guidance on its security and compliance structure:
(https://blogs.oracle.com/developers/5-best-practices-for-kubernetes-security)
Conclusion
You can confidently ensure security compliance and that Kubernetes services are production-ready. The DevOps CI/CD pipeline requires compliance auditing at all stages. The infrastructure and application layers tie together and must be compliant regardless of how they scale or when they run.
You can confidently to the validate complaince of your Kubernetes clusters cloud using this low-risk approach. Contact NeuVector (www.neuvector.com) to enable continuous compliance within your Kubernetes environment.
For more information, see the Oracle Container Engine for Kubernetes documentation. If you want to experience NeuVector on Container Engine for Kubernetes for yourself, sign up for an Oracle Cloud Infrastructure account and start testing today!
