I’d like to share the exciting news that Autonomous Database on Shared Exadata Infrastructure (ADB-S) now supports customer-managed keys thanks to the integration with Oracle Cloud Infrastructure (OCI) Vault service. You can use OCI Vault to centrally manage the Transparent Data Encryption (TDE) master key of your ADB-S instance and be in full control of your key lifecycle operations such as key creation, rotation, deletion, and so on.
When you decide to use a customer-managed key, ADB-S generates and encrypts the TDE master key by using the key you created in OCI Vault. In other words, whenever ADB-S needs your TDE master key to decrypt the tablespace keys and datafiles, it needs to first access your key in OCI Vault to decrypt the TDE master key.
The benefits of customer-managed keys are not only limited to the master key lifecycle management. Customer-managed keys also allow you to store your keys in a highly available, managed service where they can be protected by hardware security modules (HSM) that meet Federal Information Processing Standards (FIPS) 140-2 Security Level 3 security certification.
In this post, we will go over how to use customer-managed keys in ADB-S. Here are the steps we will follow:
- Create a Vault and a Key in OCI Vault
- Create a Dynamic Group and a Policy
- Use Customer-Managed Keys During Provisioning or for an Existing Instance
- Rotate Your Key or Switch to an Oracle-Managed Key
Create a Vault and a Key in OCI Vault
Before we start using customer-managed keys in ADB-S, we first need to create a vault and a master encryption key in OCI Vault.
- In the OCI console, go to ‘Identity and Security‘ -> ‘Vault‘
- Create a vault
- Create a master encryption key with your choice of protection mode, key algorithm, and key length (Optionally, you can also import your own key)
Here’s how my vault looks after creating two master encryption keys:
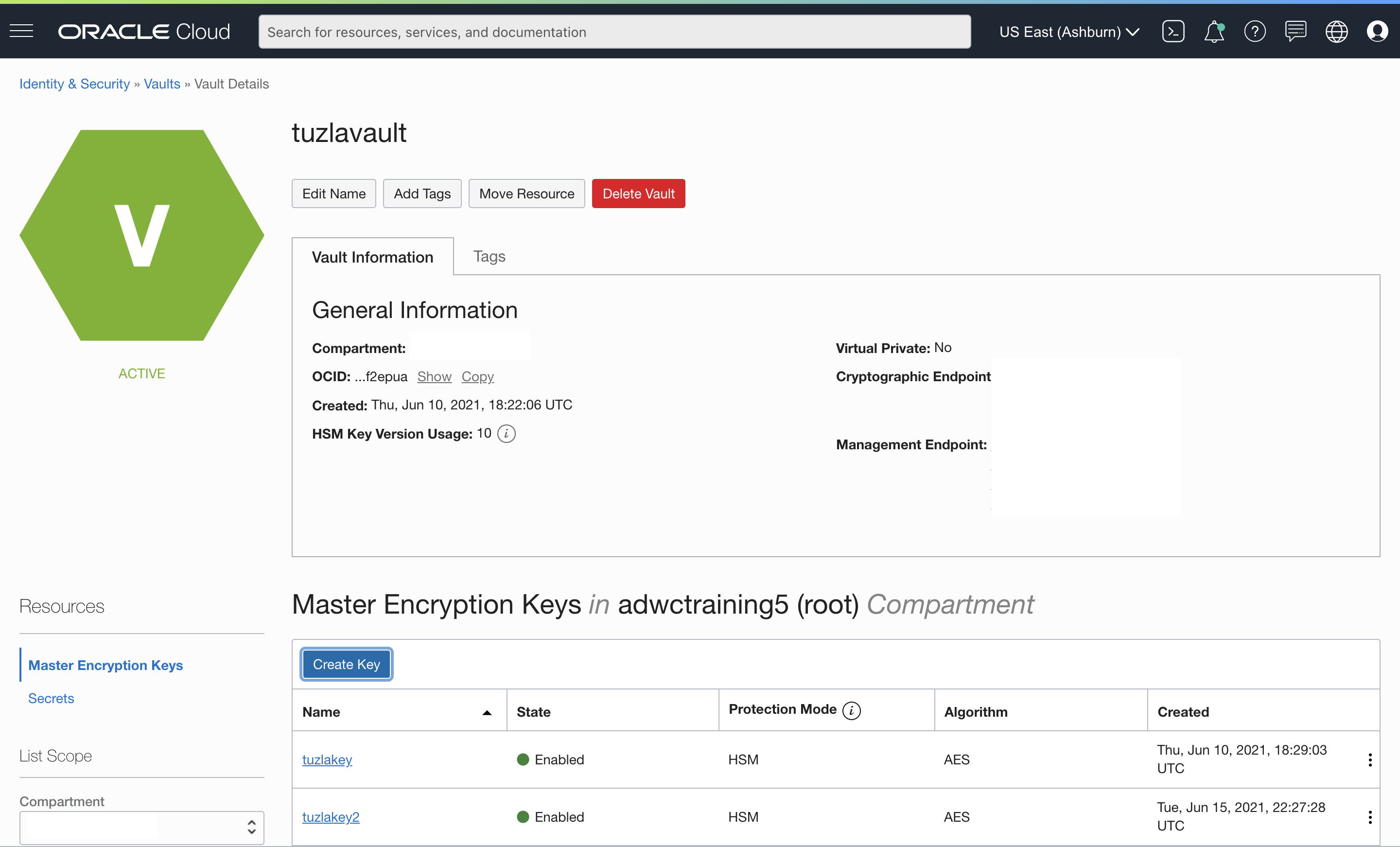
Create a Dynamic Group and a Policy
This step might sound familiar if you have already checked out my last post about OCI resource principal authentication. In that post, we covered how to access OCI Object Storage to load data using resource principal authentication, which requires us to first create a dynamic group and a policy in OCI Identity and Access Management (IAM). The same requirement applies here as well since ADB-S relies on resource principal authentication to access OCI Vault, where you store your master encryption keys. Therefore, we will create a dynamic group and a policy so that IAM knows our ADB-S resource has the necessary privilege to access the vault in our tenancy (or a given compartment of our tenancy).
- In the OCI console, go to ‘Identity and Security‘ -> ‘Dynamic Groups‘ -> ‘Create Dynamic Group‘
- Since we want to include all ADB-S instances under a given compartment to this dynamic group, we need to add the OCID of our compartment in the following rule:
resource.compartment.id = 'ocid1.autonomousdatabase.oc1.iad.osbgdthsnmakytsbnjpq7n37q'
In the example above, we created a dynamic group that includes all the resources under a given compartment. It’s also possible to narrow the scope of this dynamic group by adding a resource type or the OCIDs of specific ADB-S instances. However, when a dynamic group is restricted to a group of existing instances, it doesn’t include any new instances we might provision in the future. Since one of the goals of this post is to show how to use customer-managed keys during provisioning, we have created a dynamic group at the compartment level so that it can include both existing and any future ADB-S instances we provision.
The next step is to create a policy for our dynamic group so that those resources can access the vault and keys in our tenancy. Similar to dynamic group rules, policy statements can also be written to allow access to certain services and resources under a given compartment.
- In the OCI console, go to ‘Identity and Security’ -> ‘Policies‘ -> ‘Create Policy’
- Add your policy statement in plain text or use the Policy Builder.
Allow dynamic-group ctuzlaDG to use vaults in tenancy Allow dynamic-group ctuzlaDG to use keys in tenancy
Use Customer-Managed Keys During Provisioning or for an Existing Instance
Now that we have set up our vault, master encryption key, dynamic group, and policy, we can start using our own master encryption key in our ADB-S instances. In order to use a customer-managed key during provisioning:
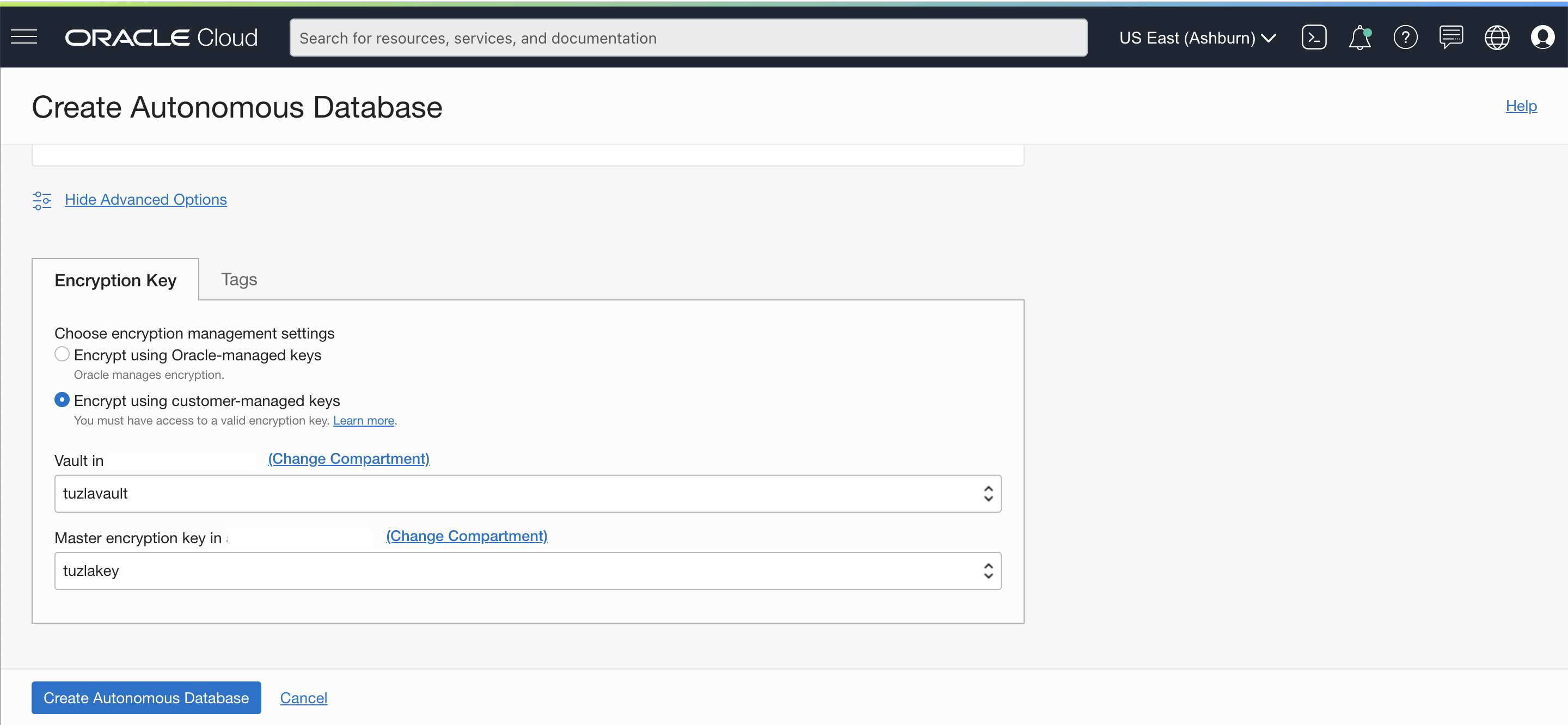
- Scroll all the way down on the ‘Create Autonomous Database’ page and click on ‘Show Advanced Options’
- Choose ‘Encrypt using customer-managed keys‘ option
- Select your vault and master encryption key from the dropdowns as shown in the screenshot below
- Click ‘Create Autonomous Database‘
In order to switch to a customer-managed key for an ADB-S instance that is currently using an Oracle managed key:
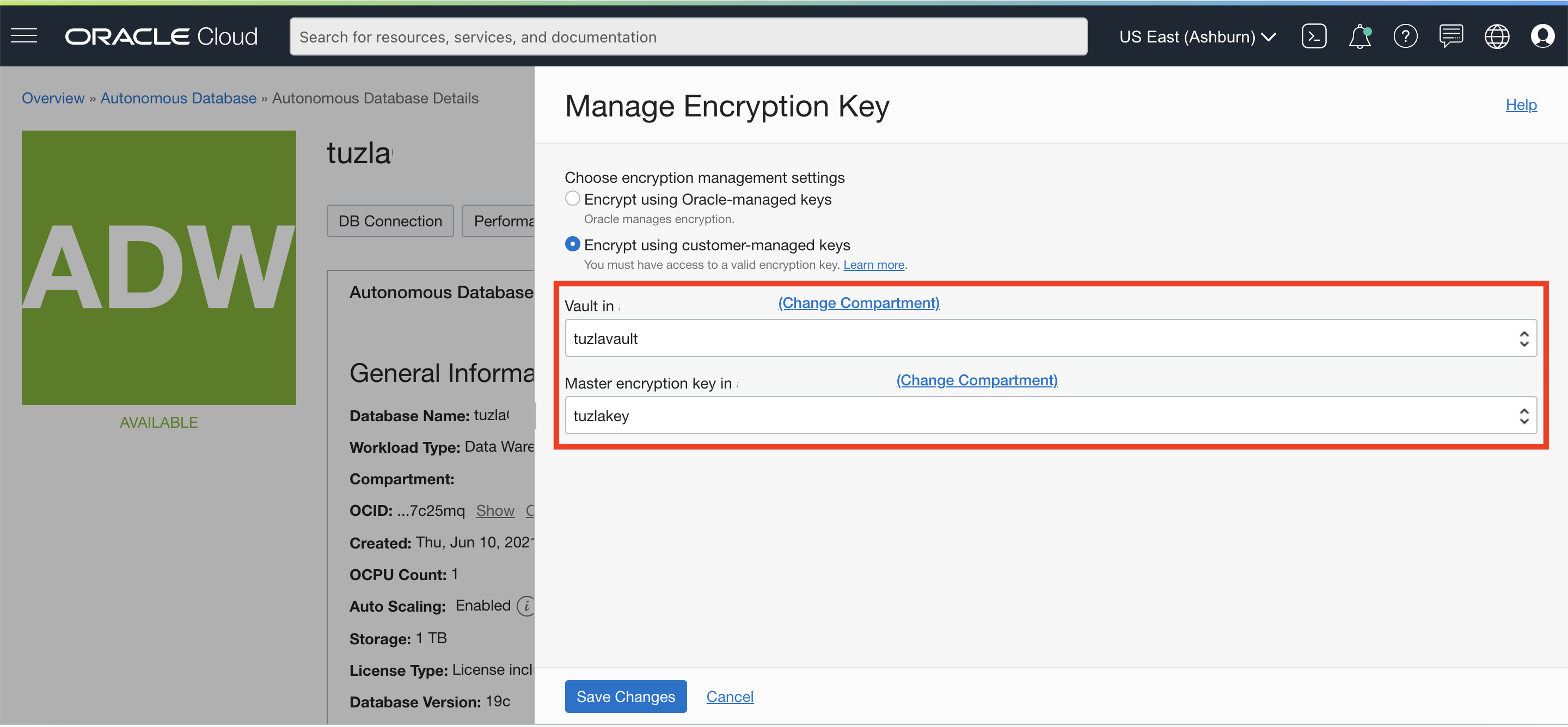
- Go to the ‘Autonomous Database Details‘ page
- Click ‘Manage Encryption Key‘ under ‘More Actions‘
- Choose ‘Encrypt using customer-managed keys‘ option
- Select your vault and master encryption key from the dropdowns as shown in the screenshot below
- Click ‘Save Changes‘
 Rotate Your Key or Switch to an Oracle-Managed Key
Rotate Your Key or Switch to an Oracle-Managed Key
Once we are using a customer-managed key in our ADB-S instance, we can rotate our key by following almost the same steps we covered previously. In order to rotate to a customer-managed key for an ADB-S instance:
- Go to the ‘Autonomous Database Details‘ page
- Click ‘Manage Encryption Key‘ under ‘More Actions‘
- Choose ‘Encrypt using customer-managed keys‘ option
- Select your vault and a different master encryption key than the one that is used currently
- Click ‘Save Changes‘
 Please note that OCI Vault also has a key rotation capability for the keys stored in your vault. Once you rotate your key via the OCI Vault UI (or REST API), a new key version is created. However, this operation has no meaning in terms of rotating the master encryption key of your ADB-S instance. In order to rotate the master encryption key used by your ADB-S instance, you need to create a new key in your vault and use that key in ADB-S ‘Manage Encryption Key‘ UI (or REST API).
Please note that OCI Vault also has a key rotation capability for the keys stored in your vault. Once you rotate your key via the OCI Vault UI (or REST API), a new key version is created. However, this operation has no meaning in terms of rotating the master encryption key of your ADB-S instance. In order to rotate the master encryption key used by your ADB-S instance, you need to create a new key in your vault and use that key in ADB-S ‘Manage Encryption Key‘ UI (or REST API).
Another important point worth mentioning about customer-managed keys is the ability to switch back to an Oracle-managed key at any time. In order to switch to an Oracle-managed key for an ADB-S instance:
- Click ‘Manage Encryption Key’ under ‘More Actions‘
- Choose ‘Encrypt using Oracle-managed keys‘ option
- Click ‘Save Changes‘
To summarize, ADB-S manages the TDE encryption keys of your instance by default. However, if you have to meet certain regulatory or compliance needs, or simply would like to be in full control of your master encryption keys, you can start using customer-managed keys in your ADB-S instance today. As we have covered in this post, the key lifecycle management is tightly integrated with OCI Vault, and those operations are only a few clicks away!
