Network Visualizer:
An Oracle virtual network is composed of virtual cloud networks (VCNs), subnets, gateways, and other resources. These entities are related and connected through routing that’s often complex. These resources can also have complex relationships with other Oracle Cloud Infrastructure (OCI) services.
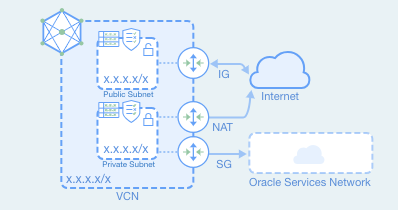
Having a concise picture of these entities and their relationships is essential for understanding the design and operation of a virtual network. The Network Visualizer provides a diagram of the implemented topology of all VCNs in a selected region and tenancy.
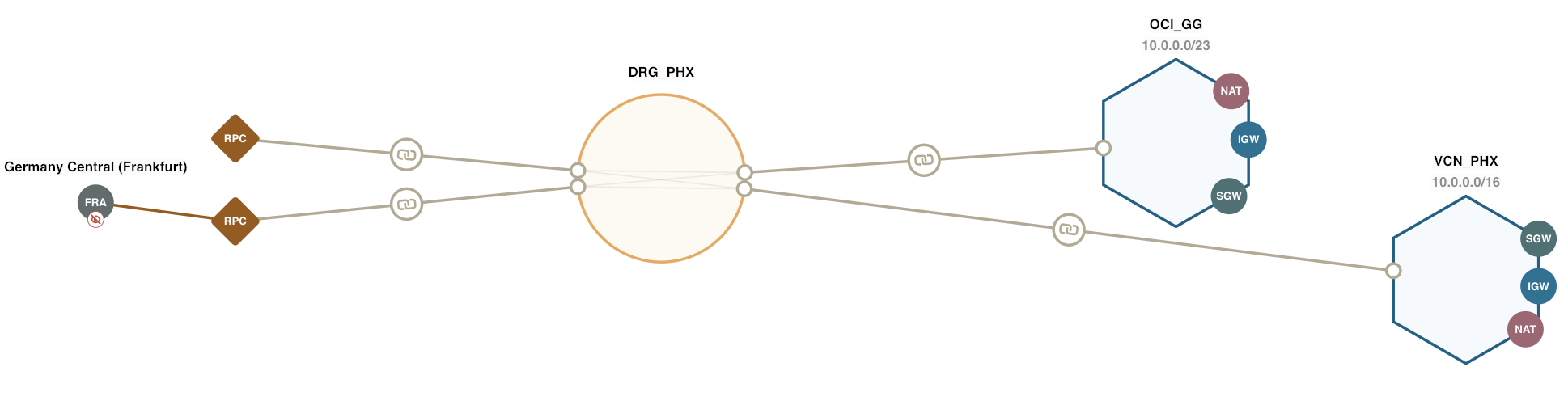
Network Path Analyzer (NPA)
Network Path Analyzer (NPA) is a diagnostic tool provided by OCI to help users troubleshoot and optimize network paths within their cloud environments. This tool is particularly useful for identifying potential network issues.
NPA carefully examines routing and security configurations and identifies the potential network path your defined traffic traverses, along with information about virtual networking entities in the path. In addition to the path information, the output of these checks includes how routing rules and network access lists (security lists, NSGs, and so on) allow or deny traffic. The sources and destinations could be within OCI, or across OCI and on-premises, or OCI and internet.
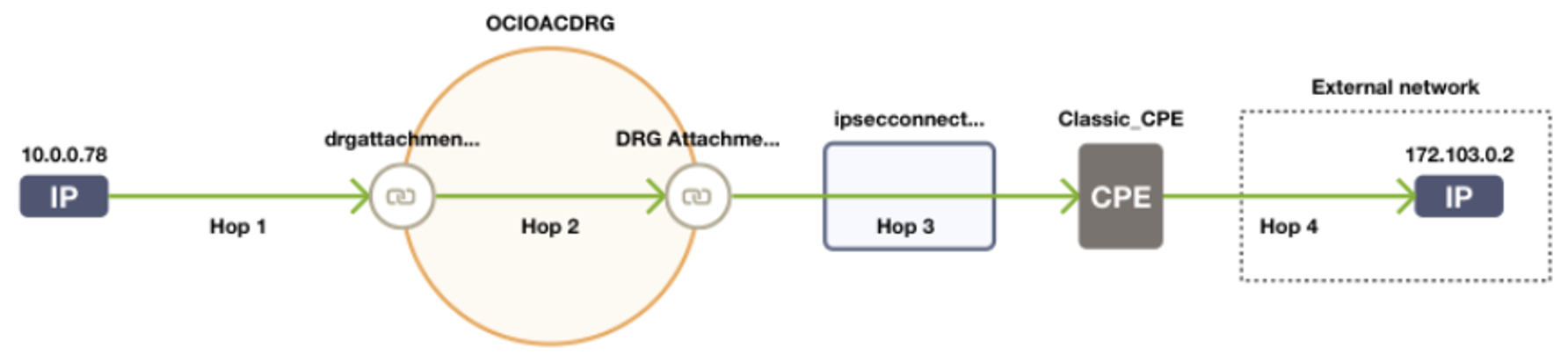
Using NPA, you can:
- Troubleshoot routing and security misconfigurations that are causing connectivity issues between OCI GoldenGate and your source/target
- Validate that the logical network paths match the intended route
- Verify that the virtual network connectivity setup works as expected before starting data replication using OCI GoldenGate.
How to use Network Path Analyzer?
- Network Path Analyzer is directly available under Networking on the Oracle Cloud Console. You only need to create and run a path analysis. An API is available for you to programmatically create, manage, and run your path analyses.
- When creating a path analysis, specify
- OCI GoldenGate Ingress IP as source and IP address of the GoldenGate source/ target as destination
- TCP as network protocol
- the source and the destination ports
Note: Select “This IP address is an on-premises endpoint” option when you enter an on-premises IP address as a source or destination. OCI GoldenGate Ingress IP to be used within the NPA test depends on the Traffic Routing Method of connection,
- Shared endpoint” then connection’s traffic originates from the assigned deployment’s Ingress IPs
- “Dedicated endpoint” then connection has its own dedicated private endpoint in the selected subnet with its own Ingress IPs. The traffic of this connection originates from these two IP addresses.
Here are a couple of scenarios depicting how to use Network Path Analyzer to troubleshoot connectivity issues related to OCI GoldenGate:
Scenarios:
- OCI GoldenGate Replication for ADB Source/Target
- ADB Source/Target in different VCN (allowing access to specific VCN & IPs)
- ADB Source/Target access restricted to Private access only
- ADB Source/Target traffic not opened i.e., ingress rule
- OCI GoldenGate Replication for OCI Base Database service:
- connectivity issues due to missing egress/ingress rules
- connectivity issues due to missing Service Gateway/ NAT Gateway
Scenario A: An OCI GoldenGate deployment can’t communicate with the Autonomous Database.
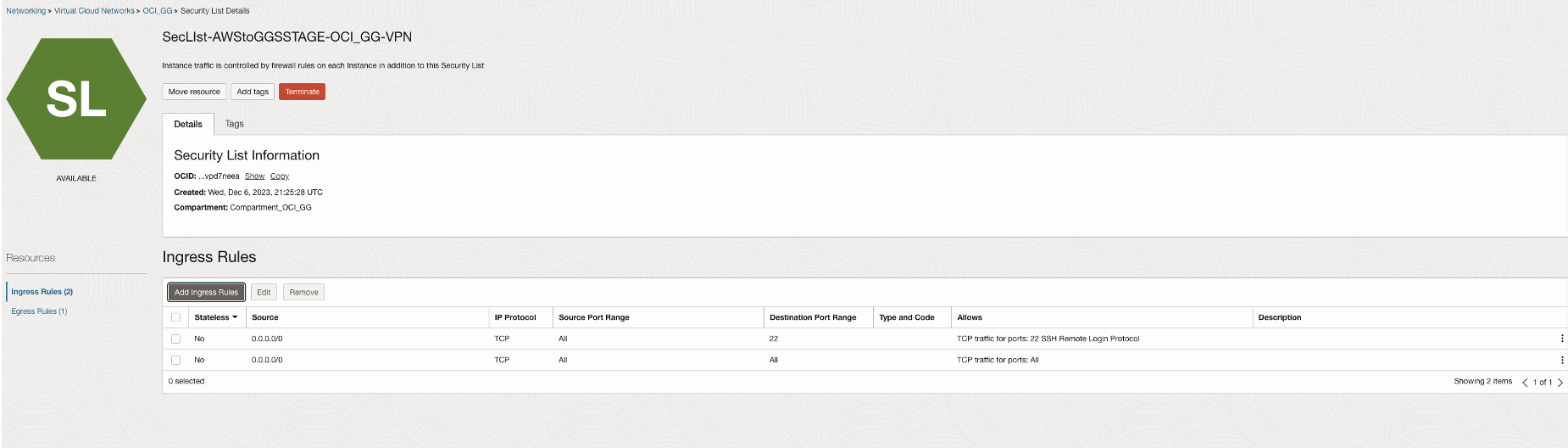
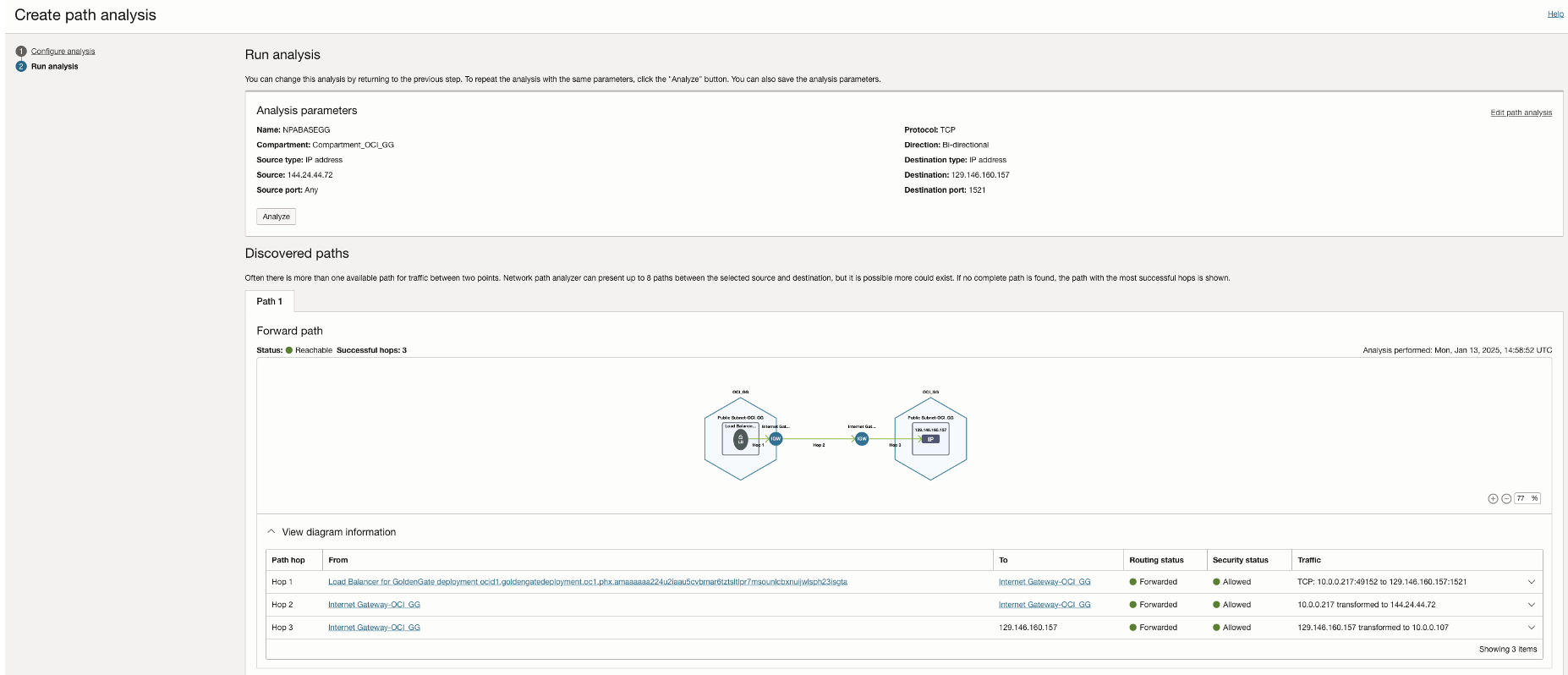
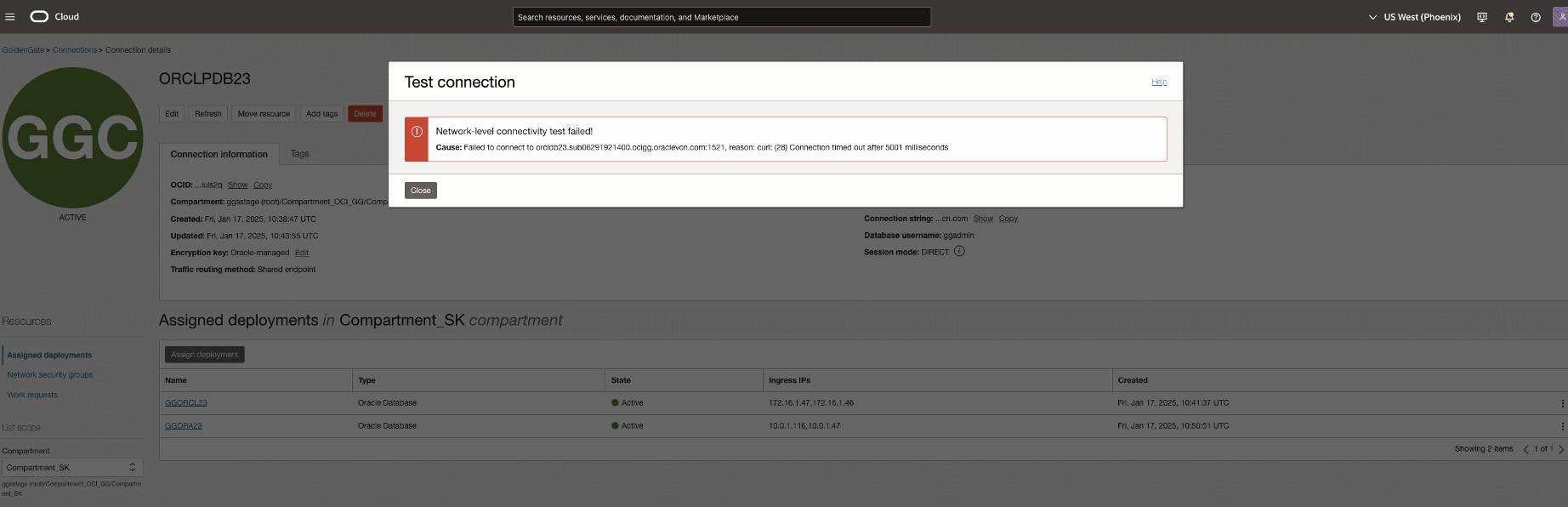
In this scenario, the ADB source/target database is in a different VCN than the OCI GoldenGate deployment. Network Path Analyzer reveals that the routing connectivity is available between the two tiers, but the security list of the ADB subnet is missing the ingress policy to allow traffic from the OCI GoldenGate deployment to the destination port 1522. The NPA test results show that the routing status is successful, but the security status shows up as Denied.
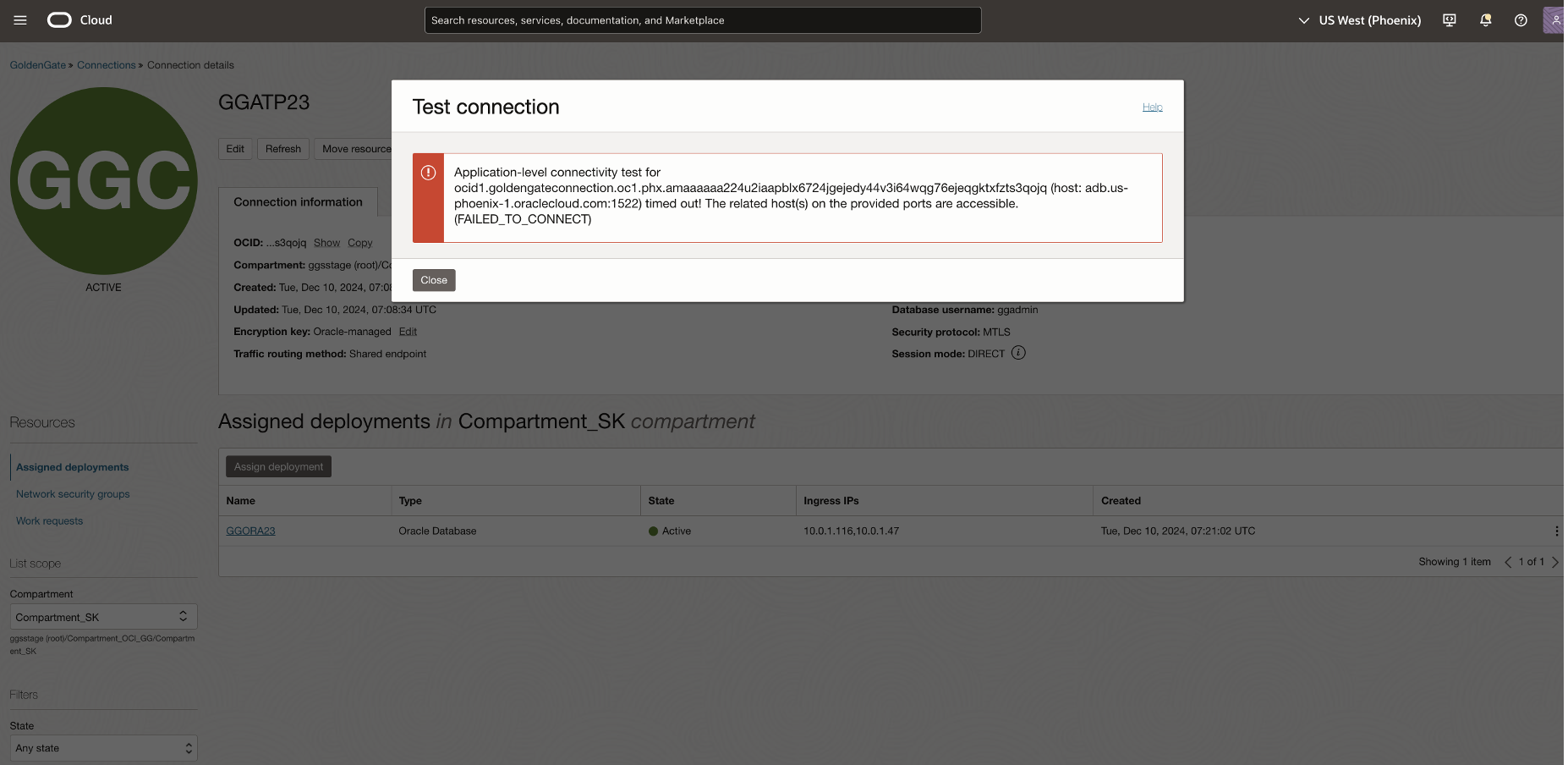
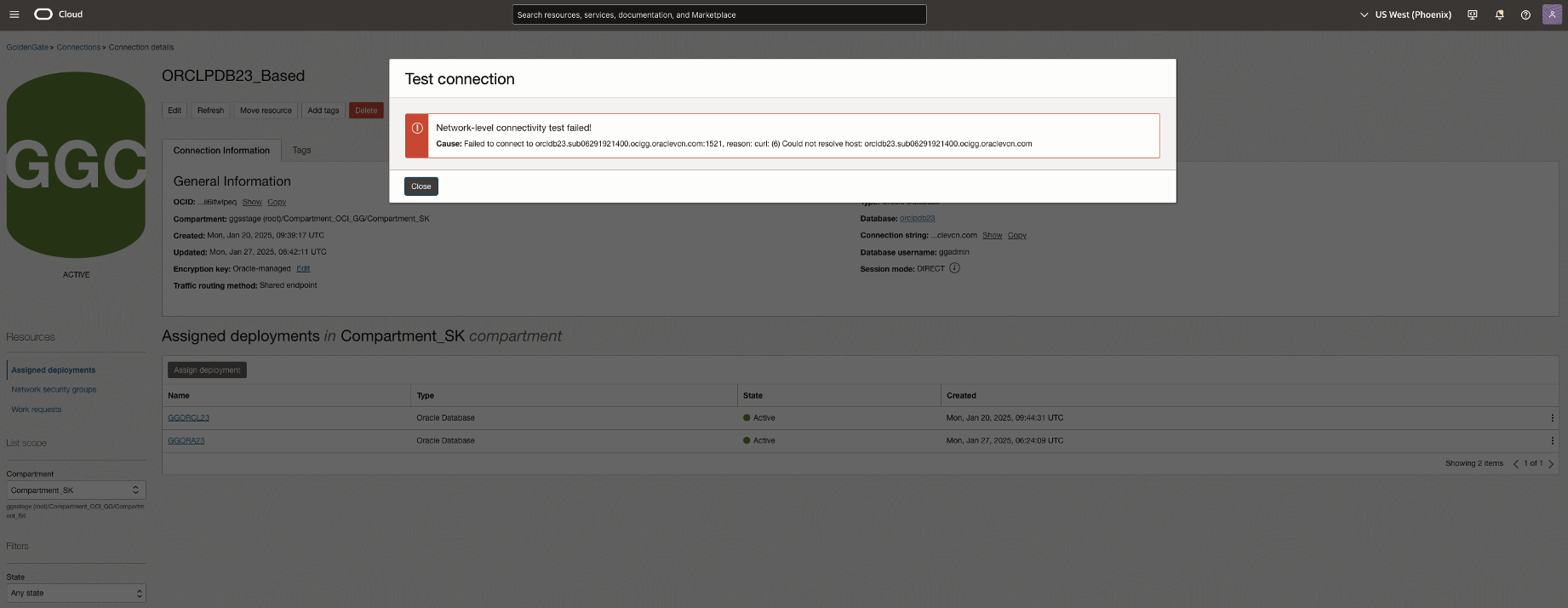
Test connection from OCI GoldenGate to the ADB fails with the below error

Run an NPA test to analyse each hop between between OCI GoldenGate and Source/Target endpoint
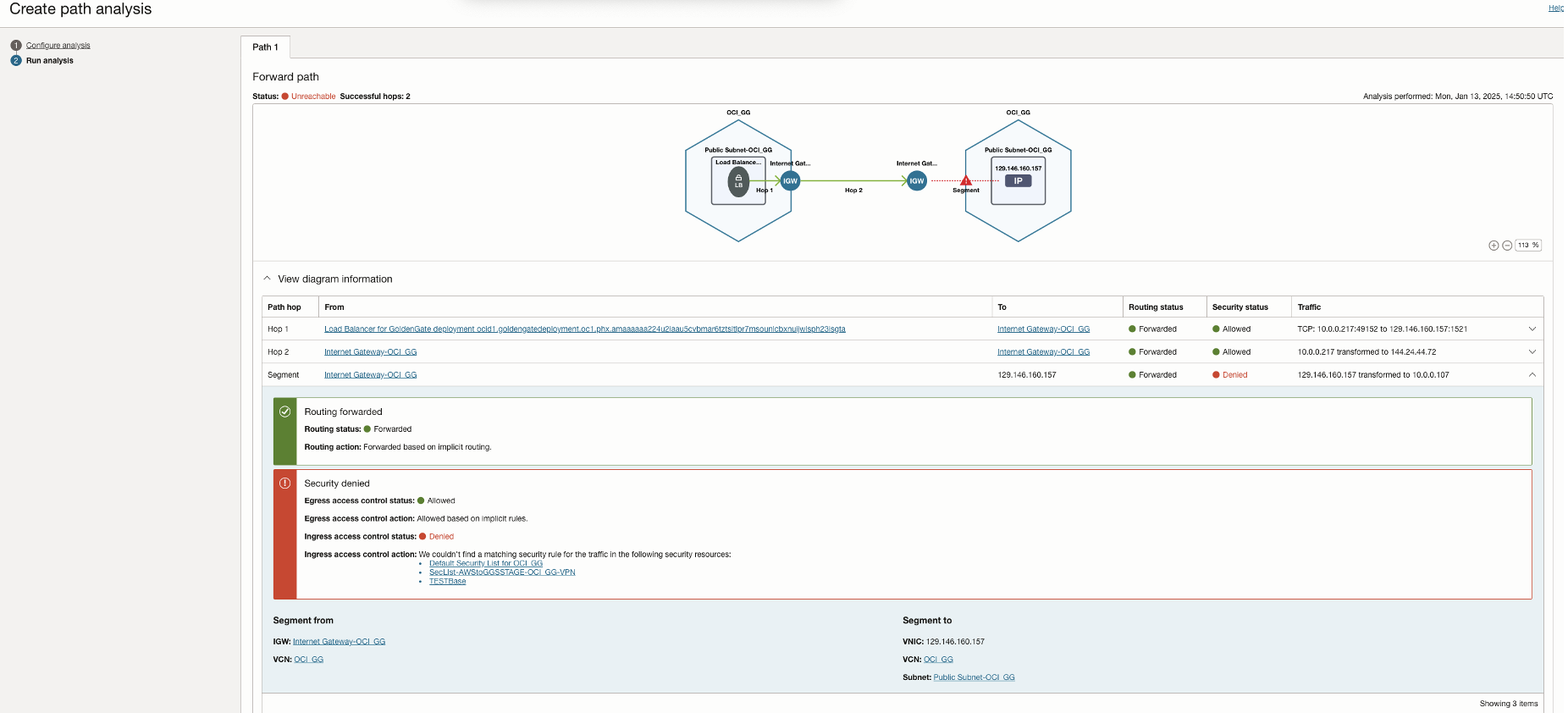

Note: NPA considers the union of all the security rules configured within NSG and Subnet Security Lists attached at the subnet level. We can go ahead and add the required ingress rule in the security list to allow traffic.
We can go ahead and add the required ingress rule in the security list to allow traffic.
Once the changes are made, rerun the NPA test.
Scenario B : ADB Source/Target in different VCN (allowing access to specific VCN & IP addresses)
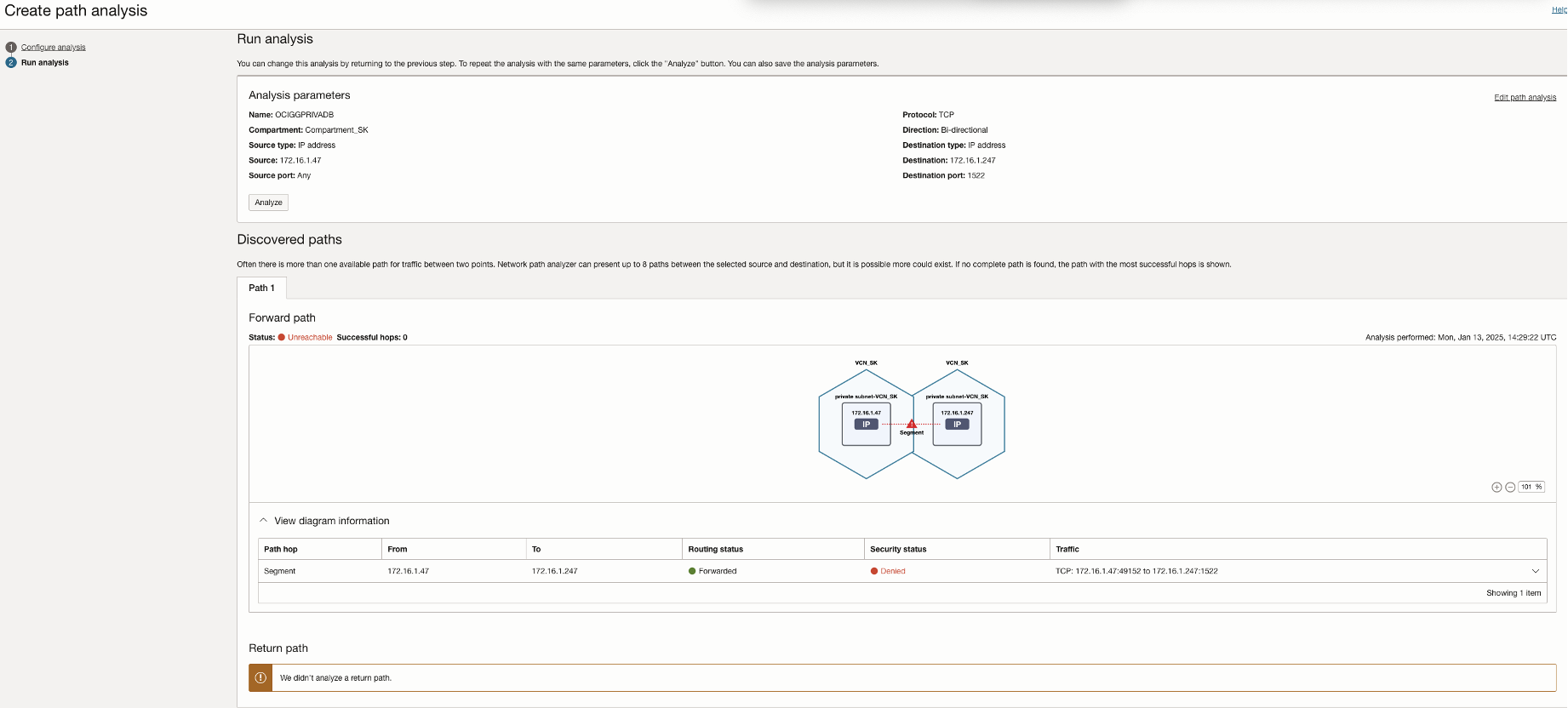
In this scenario, the ADB source/target database allows access only from specific listed VCN and IP addresses. Network Path Analyzer reveals that the routing connectivity is available between the two tiers, but the Access control list of the ADB is missing the access control rule to allow traffic from the OCI GoldenGate deployment to ADB. As shown in the NPA test results, the routing status is successful, but the security status shows up as Denied.
Add the appropriate security rule to allow connections from OCI GoldenGate. For example, you can add OCI GoldenGate deployment Ingress IP to the access control list.
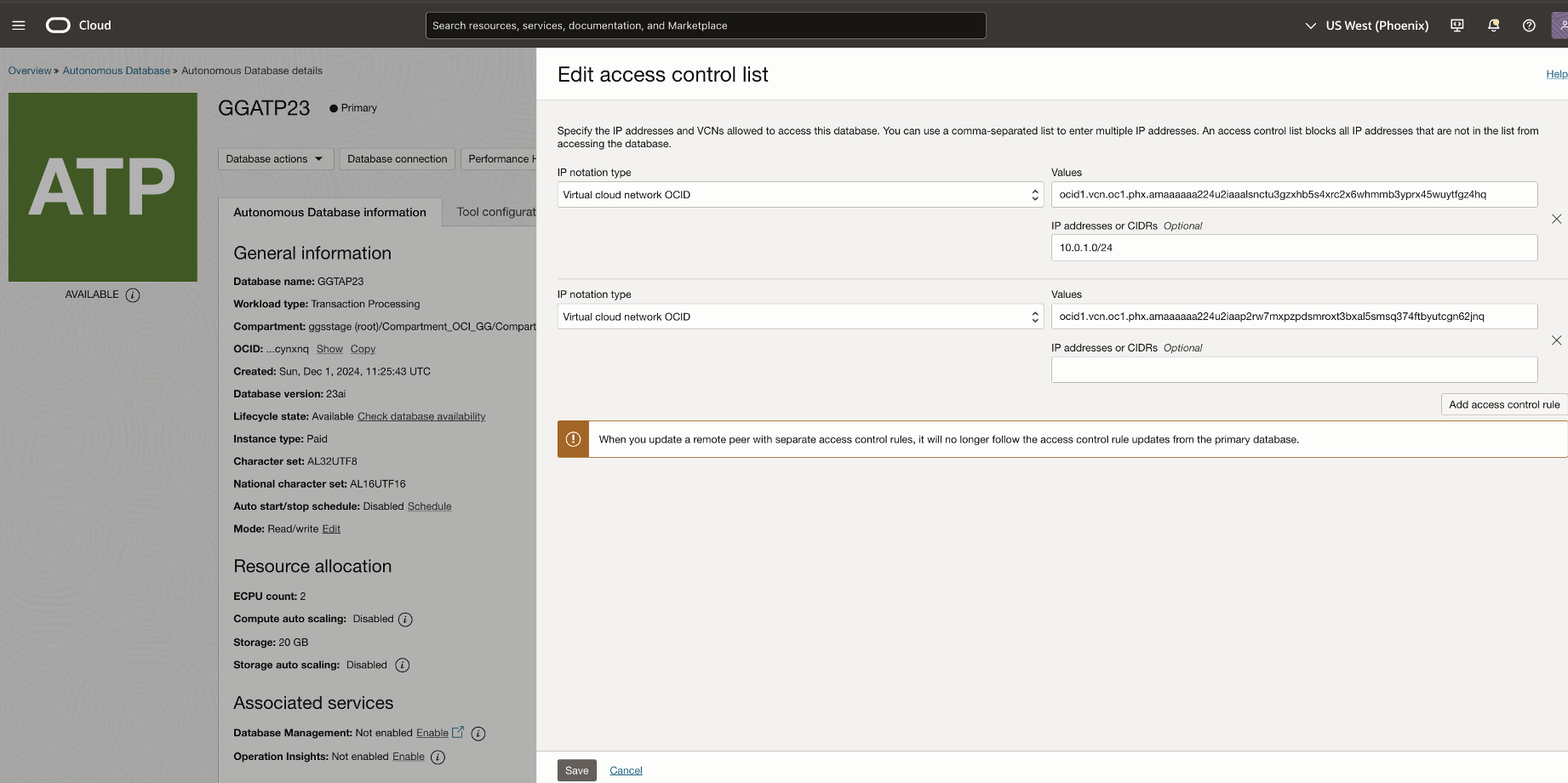
Once the changes are made, run the NPA test again.
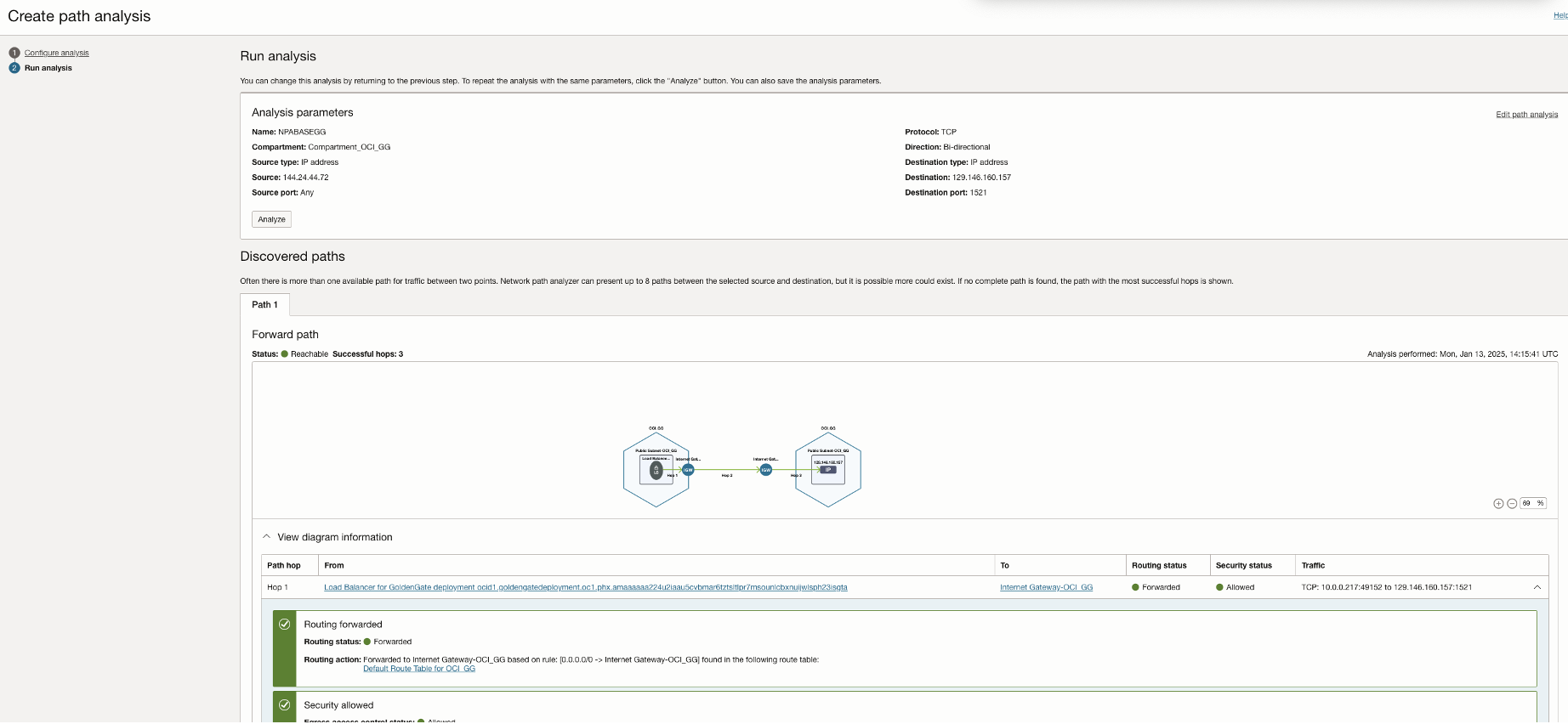
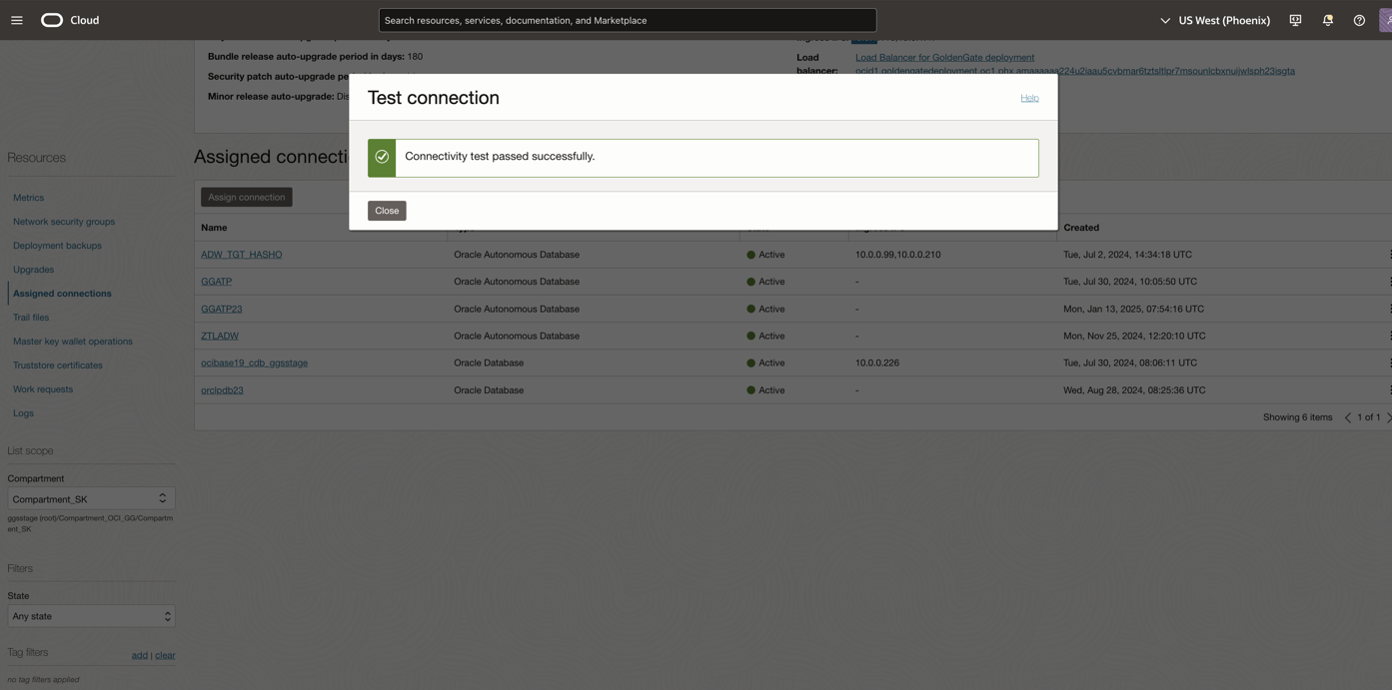
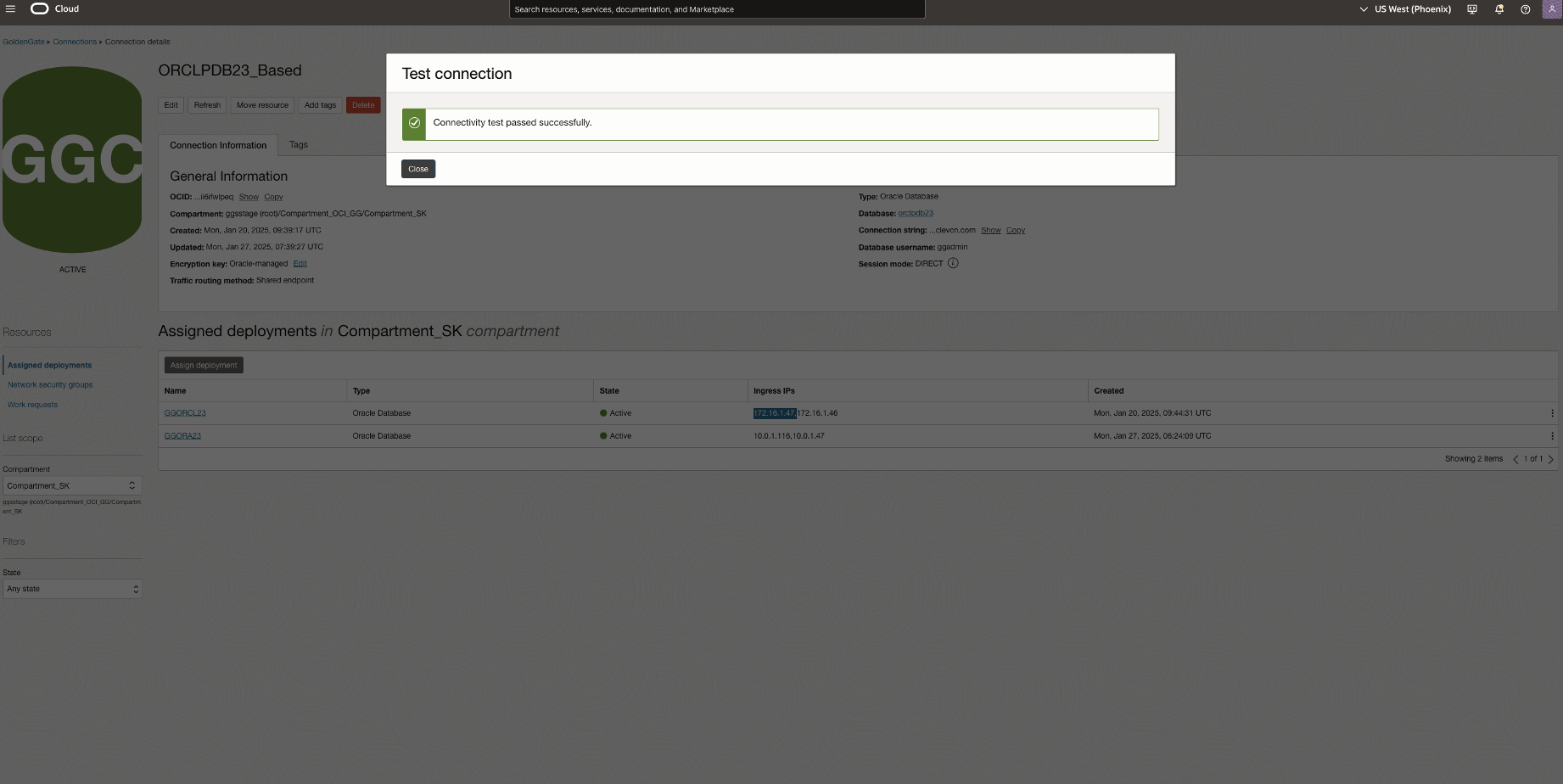
Also, perform test connection from OCI GoldenGate.
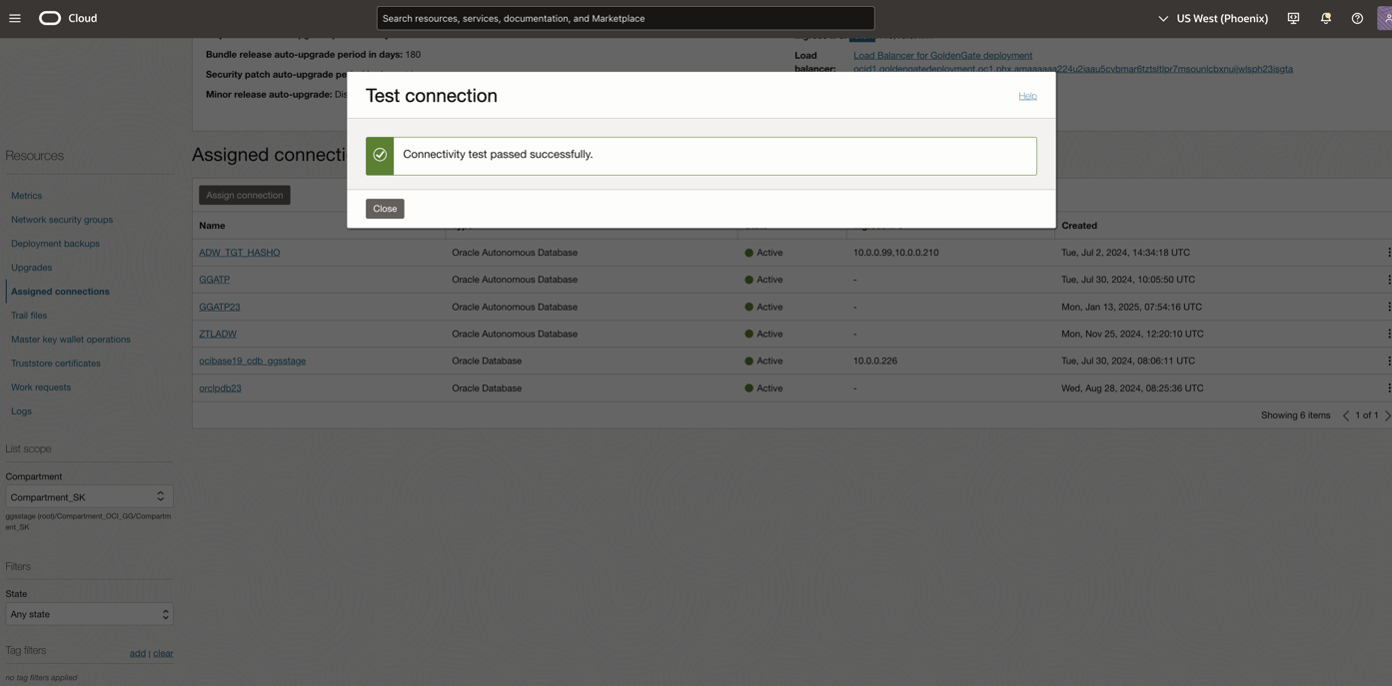
Scenario C : ADB Source/Target access restricted to Private access only
An OCI GoldenGate deployment can’t communicate with the Autonomous Database configured with Private Access only (Network Access option) within the same VCN.
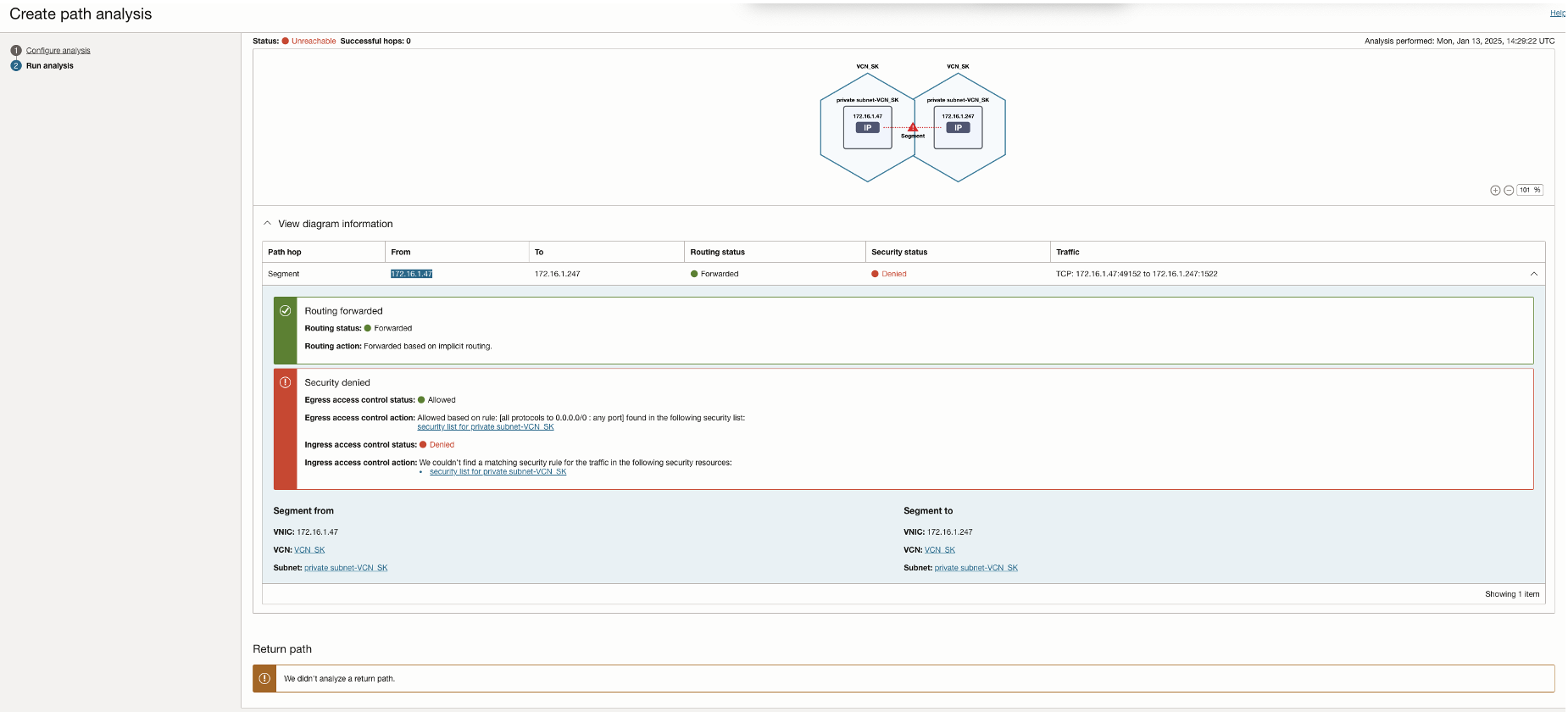
In this scenario, the ADB source/target database allows access only from specific private IP addresses defined in the subnet security list. Network Path Analyzer reveals that the routing connectivity is available between the two tiers, but the Access control list of the ADB is missing the access control rule to allow traffic from the OCI GoldenGate deployment private ip to ADB. The NPA test results show that the routing status is successful, but the security status shows up as Denied.
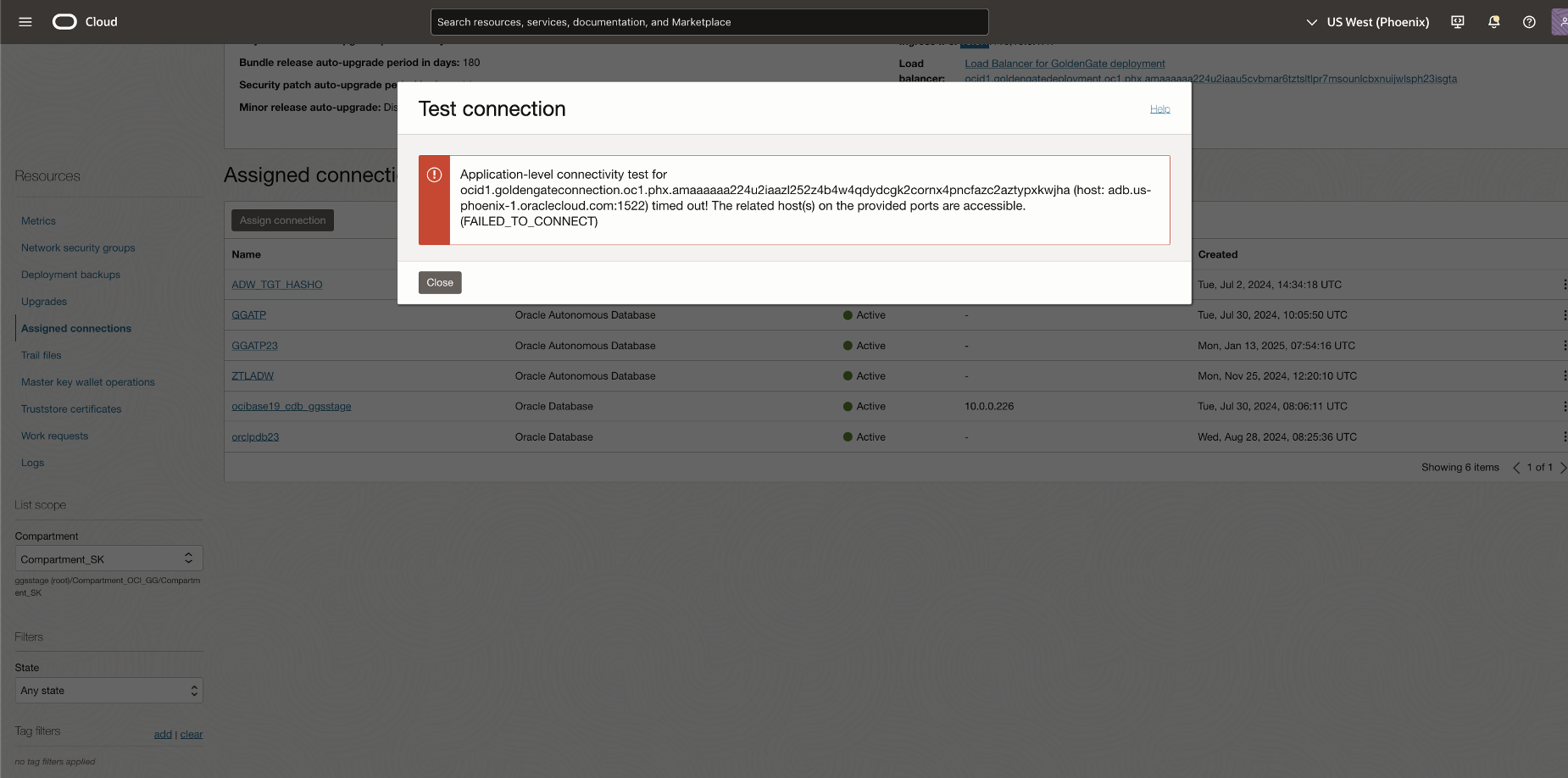
NPA test results show the Security status as Denied even though the routing status is Forwarded.
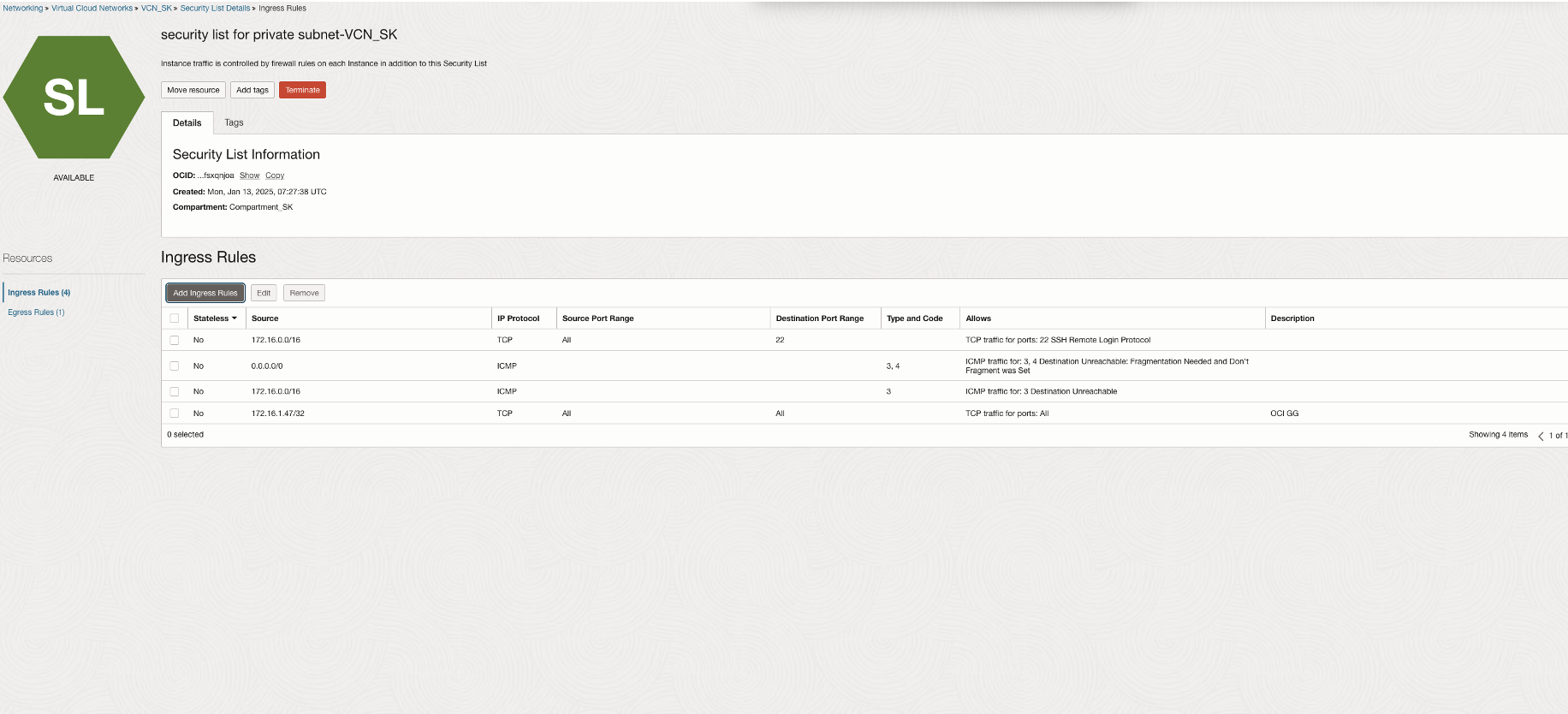
To allow connections from OCI GoldenGate, we add the deployment Ingress IP to the security list.
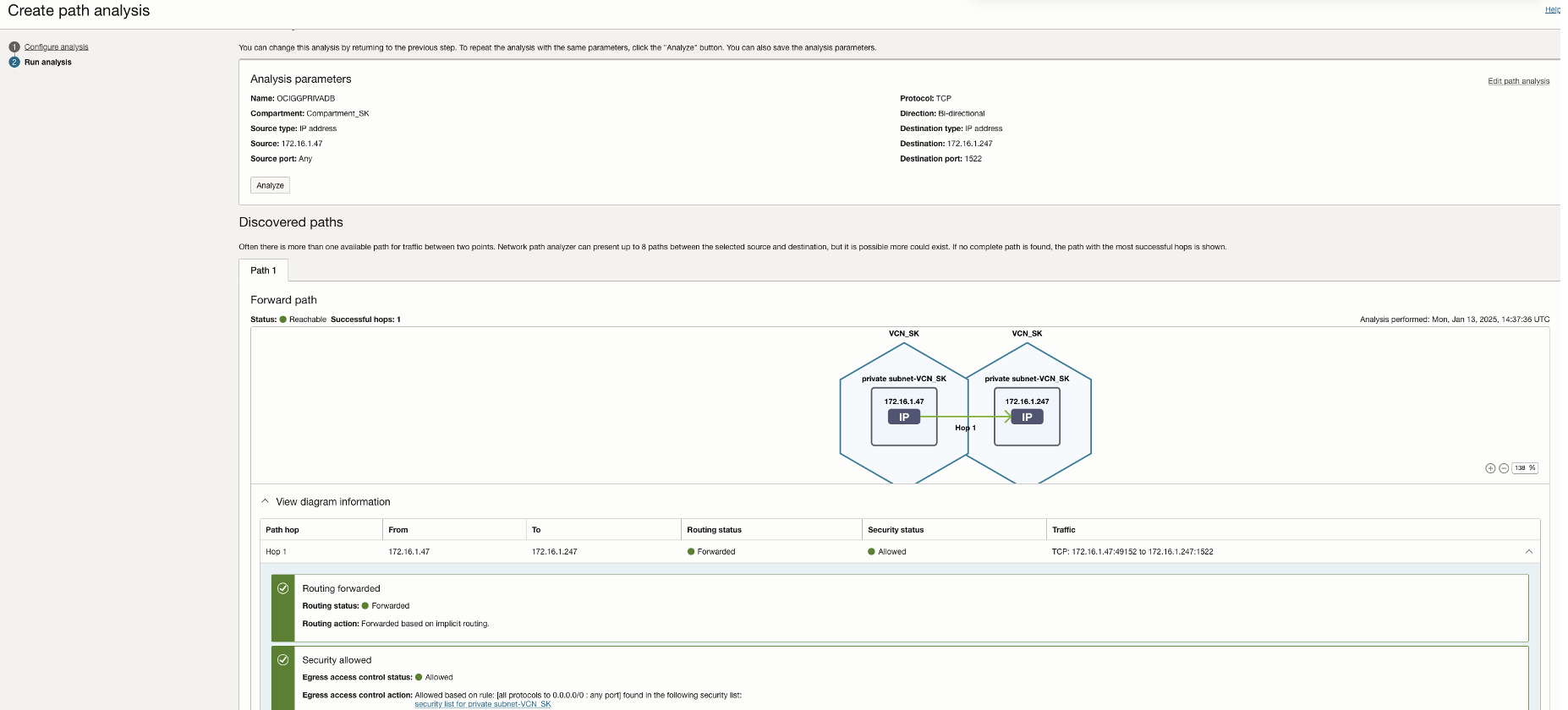
Next, run the NPA test and test connection again to confirm.
Scenario D: OCI GoldenGate to Oracle Base Database Service with missing egress/ingress rules to allow OCI GoldenGate connections.
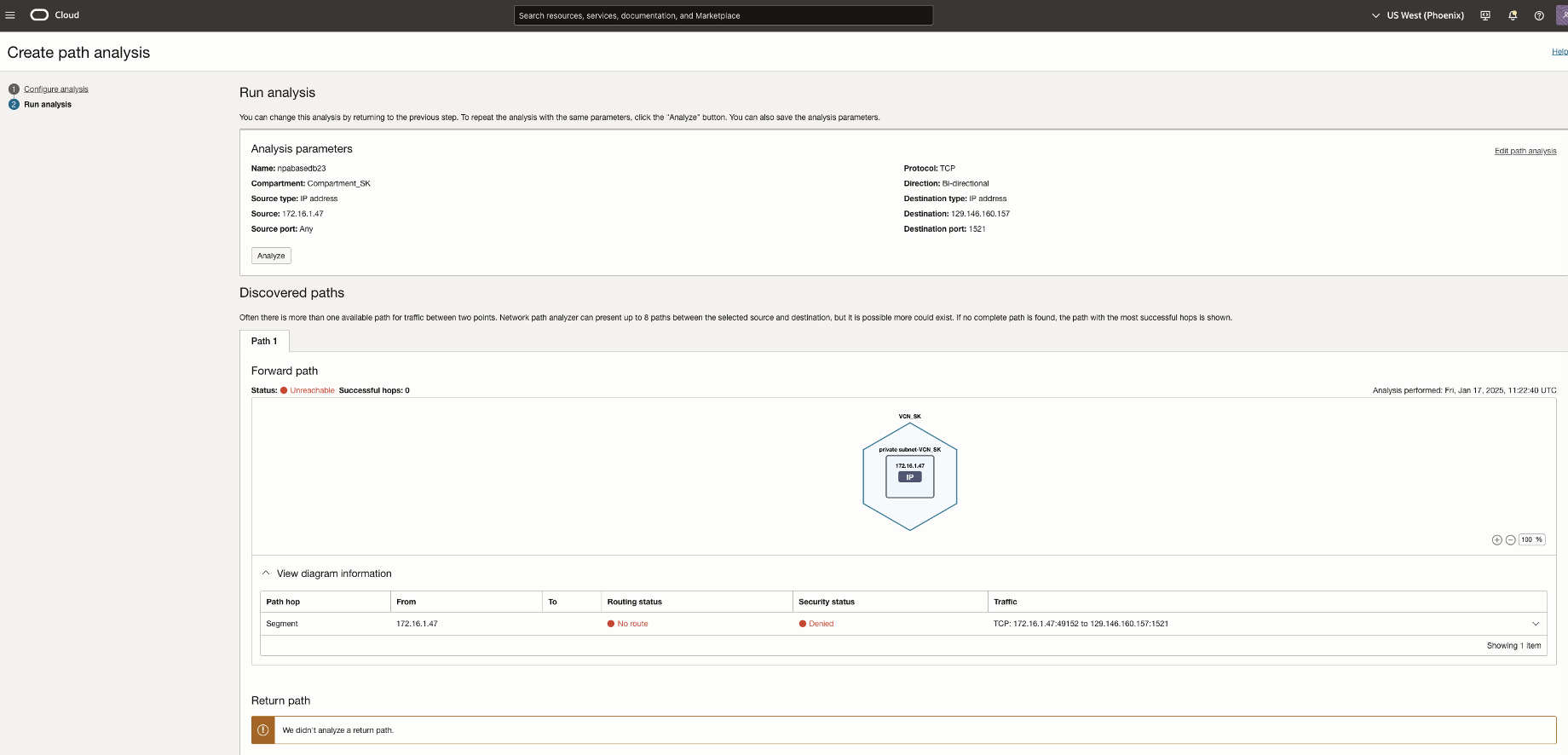
In this scenario, Network Path Analyzer reveals that the routing connectivity as well as security rule is missing, thus not allowing inbound traffic from the OCI GoldenGate deployment. As shown in the NPA test results, the routing status and security status show up as no route and denied respectively.
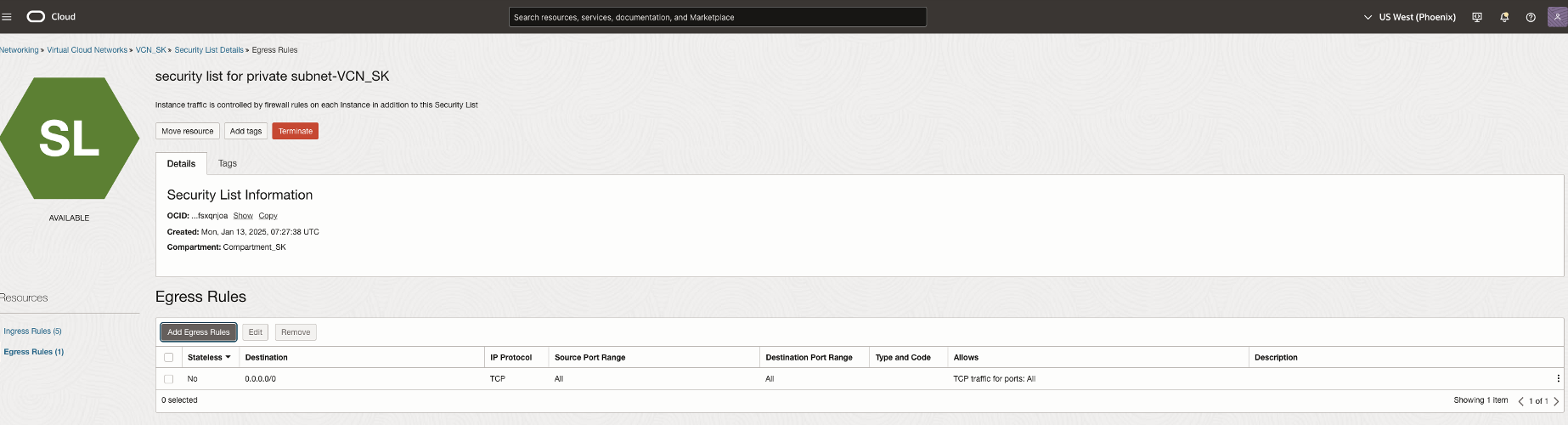
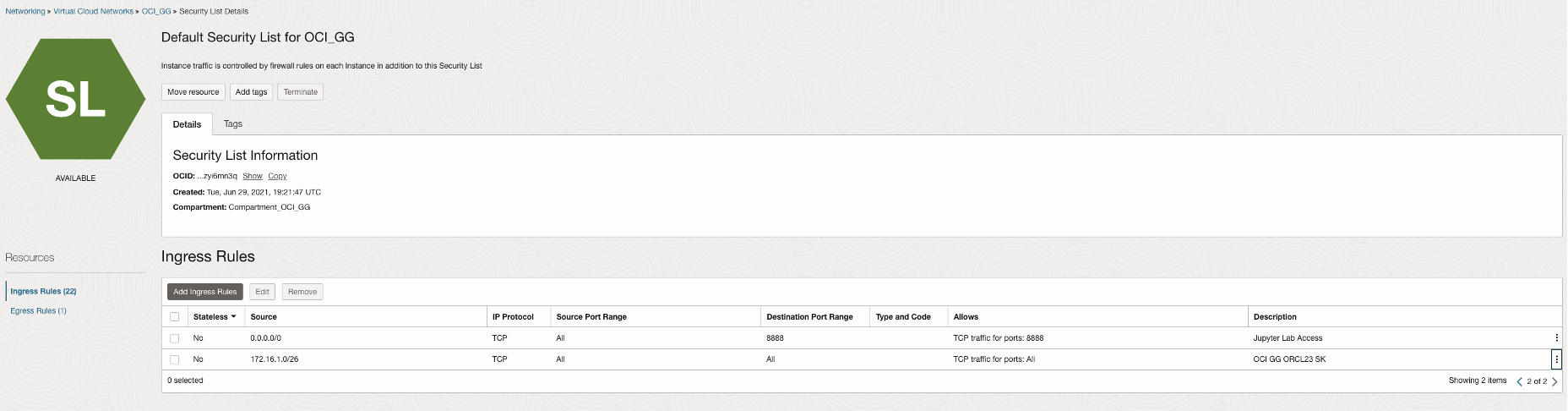
To allow outbound connections from OCI GoldenGate, we add the follow egress rule to the subnet security list.
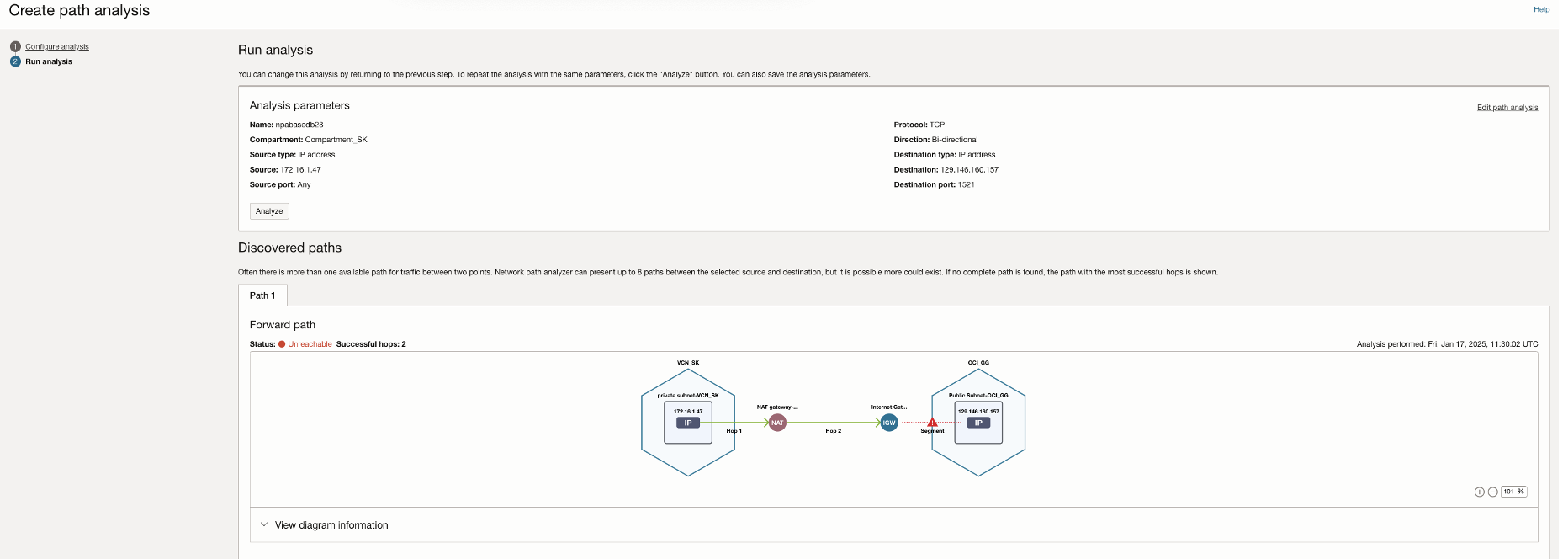
Running the NPA test again shows that the routing connectivity is available between the two tiers, but the Access control list of the Base database service is missing the ingress rule to allow traffic from the OCI GoldenGate deployment. Thus, Routing is successful with the result as Forwarded, but it returns denied under security status.
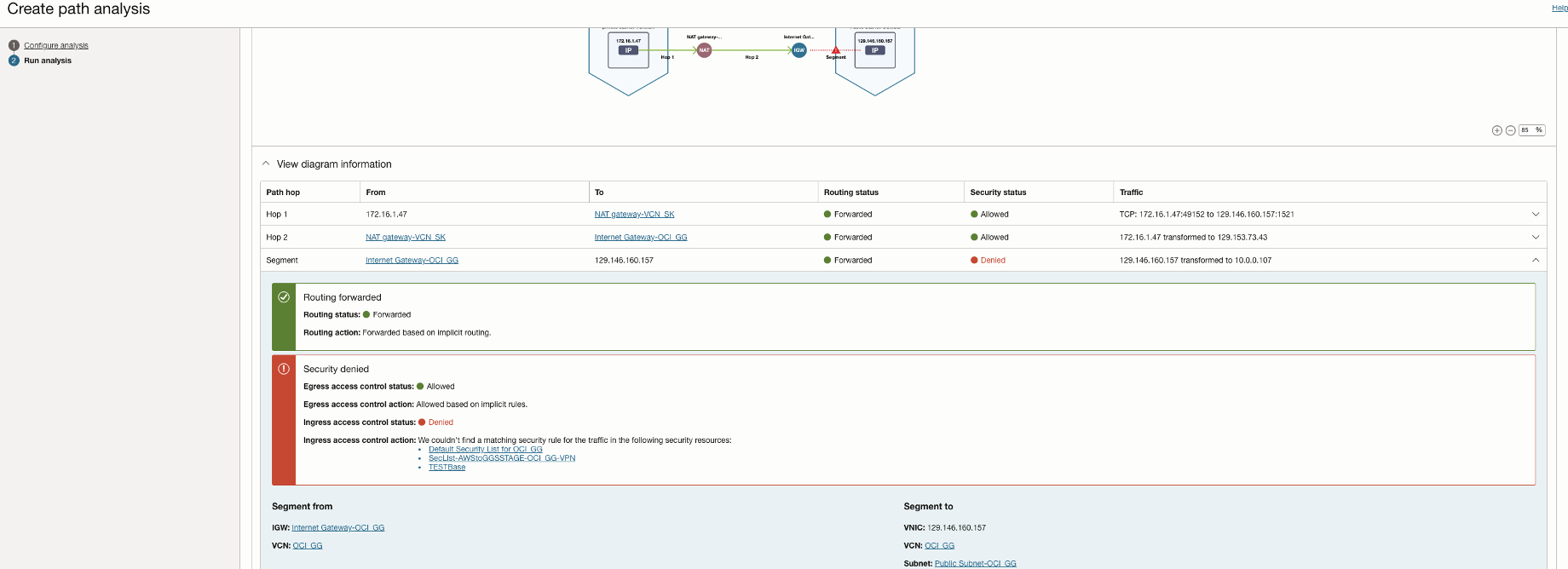
Now adding the appropriate ingress rule to the subnet security list i.e. adding OCI GoldenGate ingress ip address to the allow list.
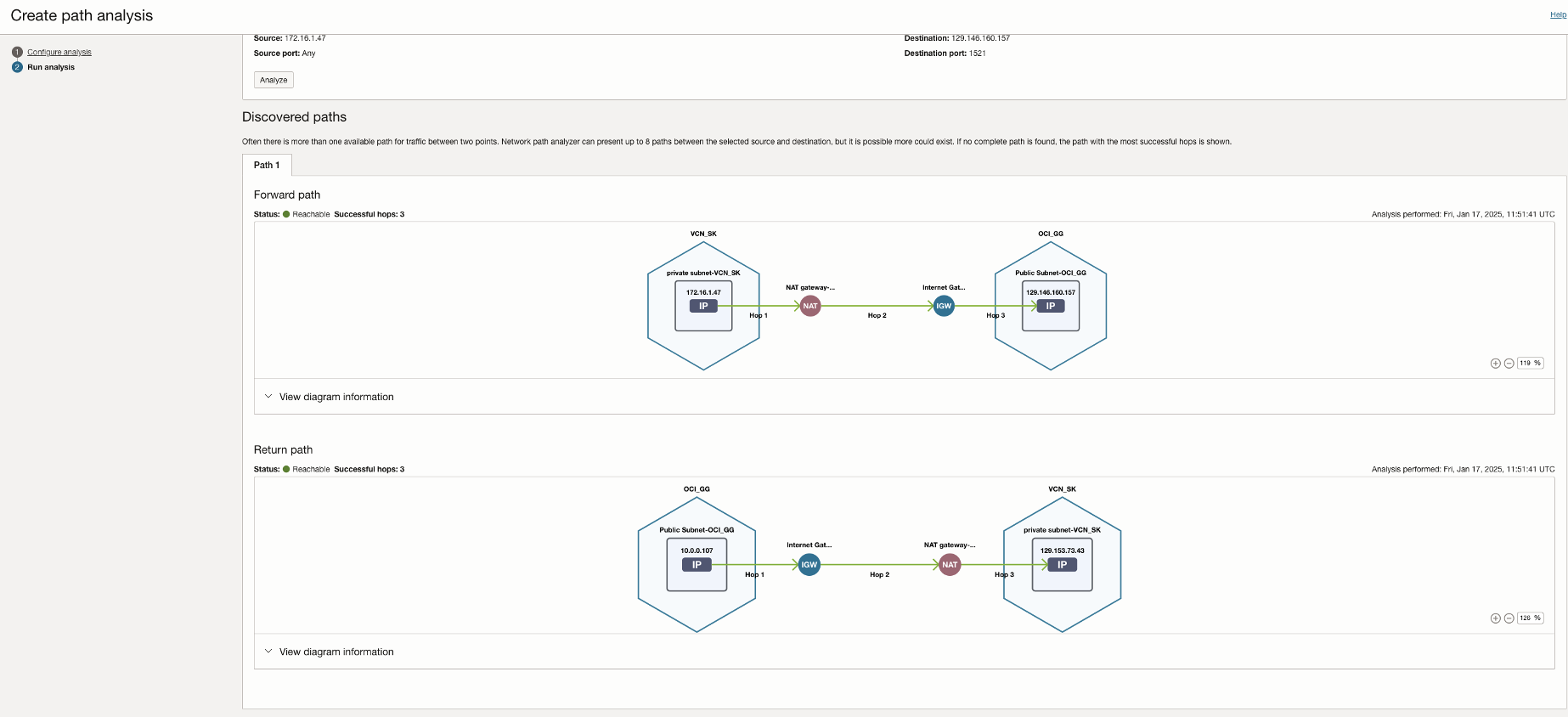
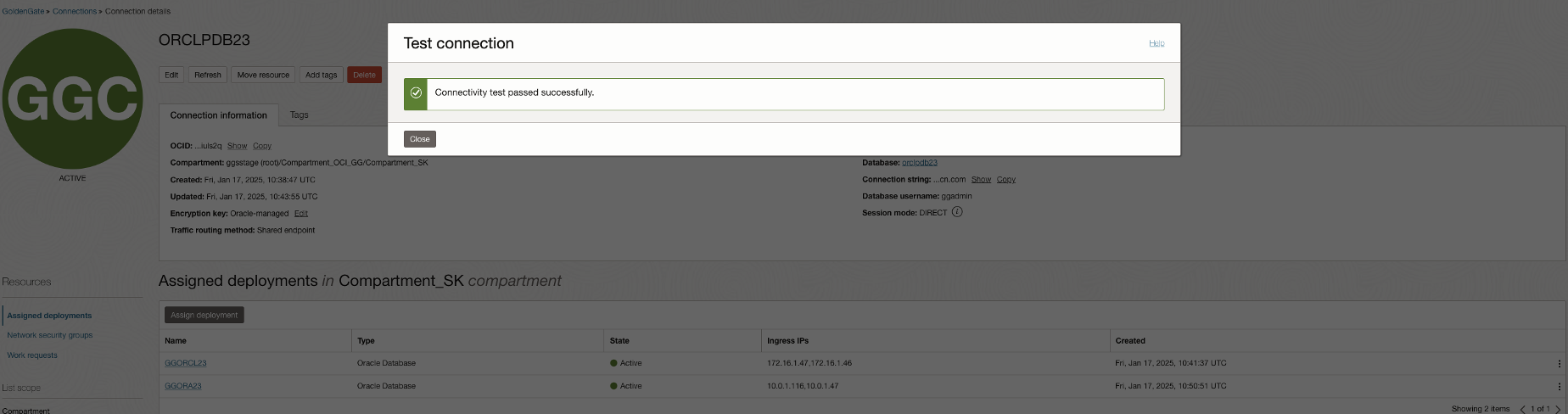
Finally, run the NPA test and test connection again to confirm.
Scenario E : OCI GoldenGate to Oracle Base Database Service with missing NAT Gateway to allow OCI GoldenGate connections to a public endpoint.
In this scenario, Network Path Analyzer reveals that the routing connectivity as well as routing rule is missing, thus not allowing traffic from the OCI GoldenGate deployment. As shown in the NPA test results, the routing status shows up as no route.
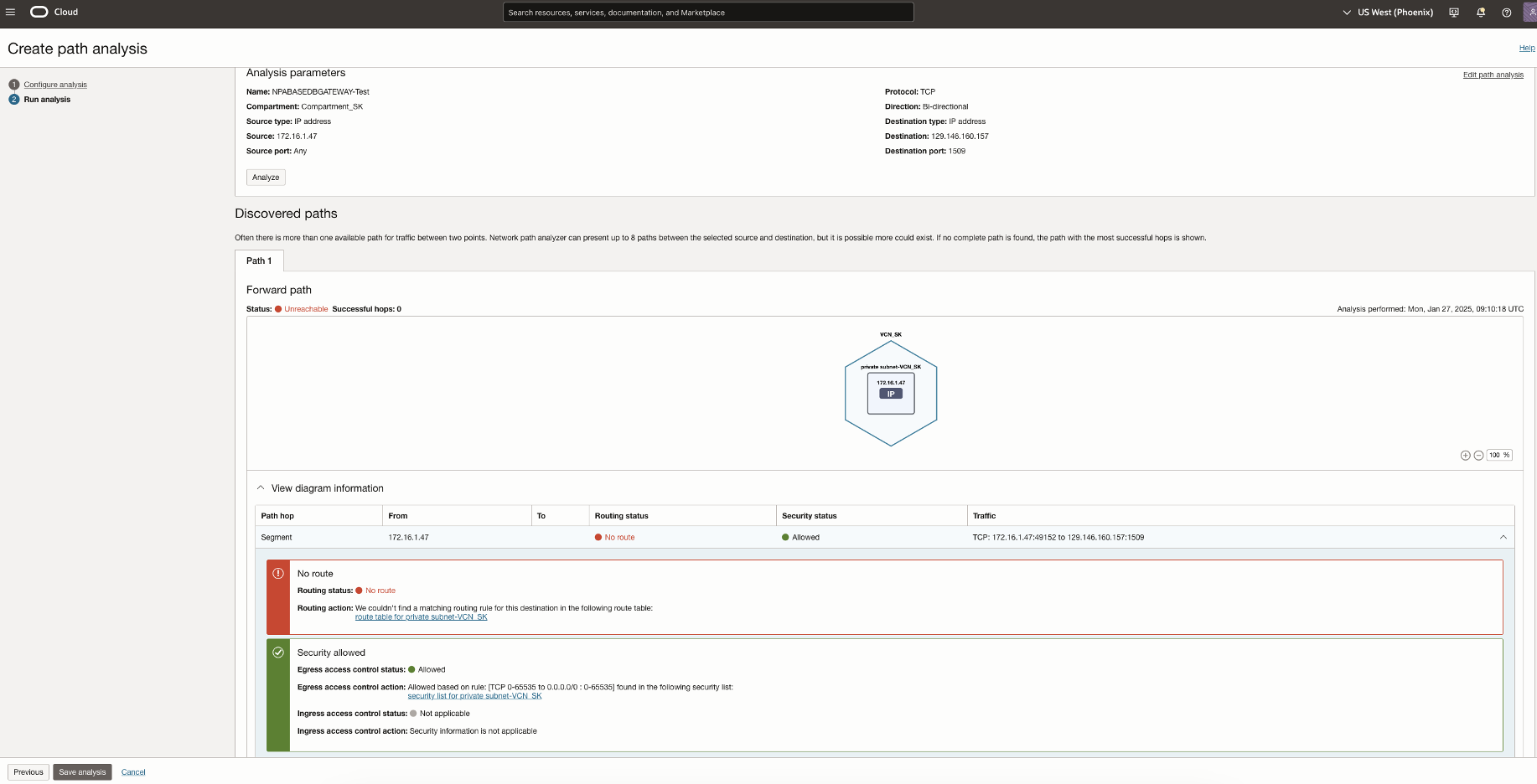
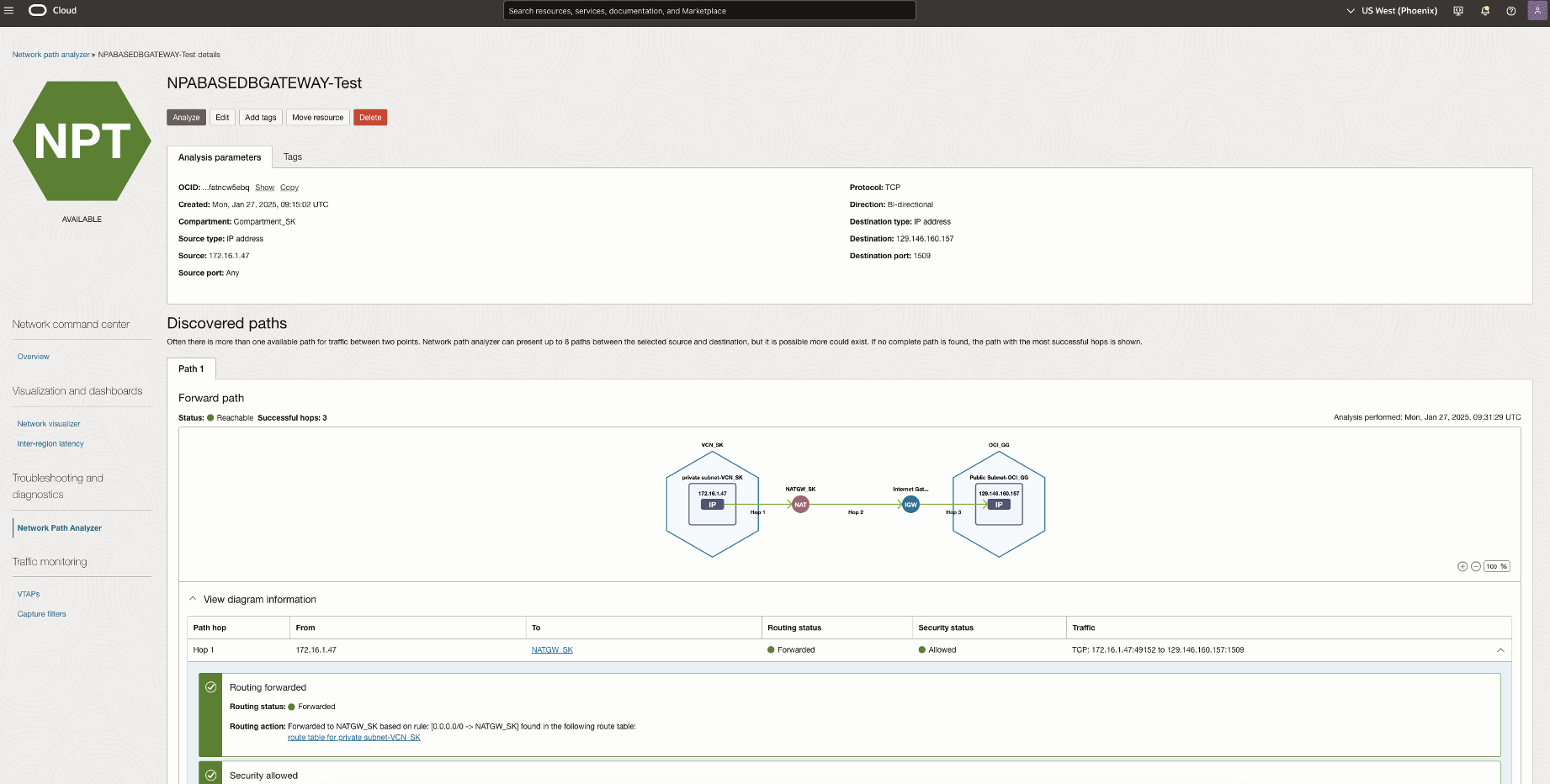
To allow outbound connections and access from OCI GoldenGate to public endpoints, ensure you have a NAT gateway or other access to the internet if necessary. To allow access to all Services in Oracle Services Network only, then a Service Gateway should be sufficient.
In conclusion, when armed with the right tools, troubleshooting network issues in Oracle OCI GoldenGate becomes much more manageable. The Network Visualizer provides a comprehensive, end-to-end view of your network topology, enabling you to visualize and understand the complex relationships between components. This holistic approach helps identify potential network bottlenecks or misconfigurations that could impact replication. On the other hand, the Network Path Analyzer is invaluable for pinpointing issues at each network hop between GoldenGate and the source/target systems. Together, these tools equip you to proactively identify and address network issues, ensuring your Oracle GoldenGate environment runs smoothly, efficiently, and without interruptions.
