Part 4(4) : Database Artifacts Creation : This section will offer comprehensive instructions for creating all the necessary steps to provision a database, open ports, configure Network Security Group (NSG), and assign them to the GG deployment.
1.Provision database.
Now, we need to provision the source database (ATP).
Compartment : dev-database-som-cmp
Private Subnet : som-pvt-sn-dev-database
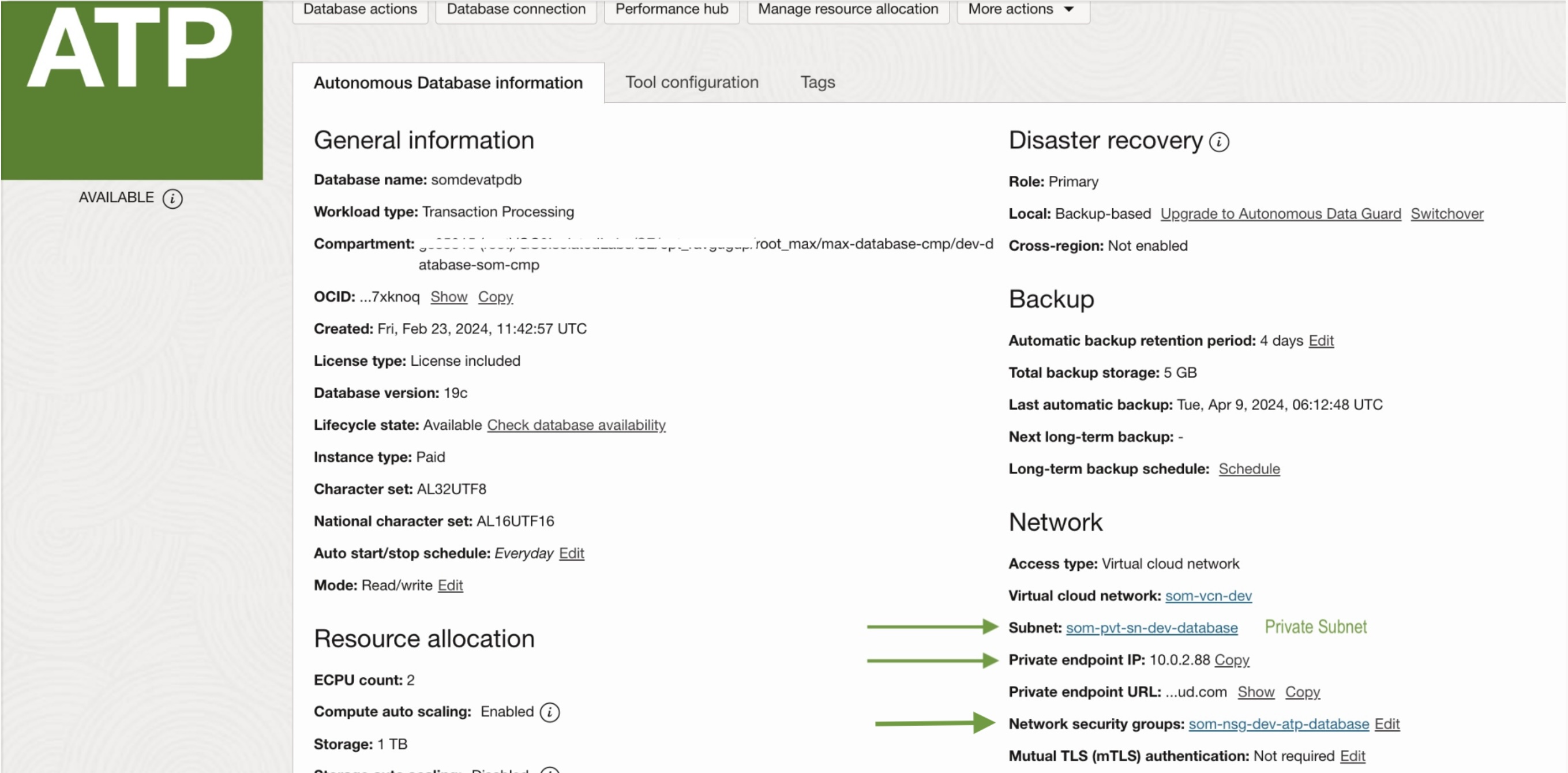
Once the deployment is created, it will be assigned one private IP address.
2. Access Database
To access the Database, currently located within a private subnet, the same route as before will be taken, utilizing the Bastion service.
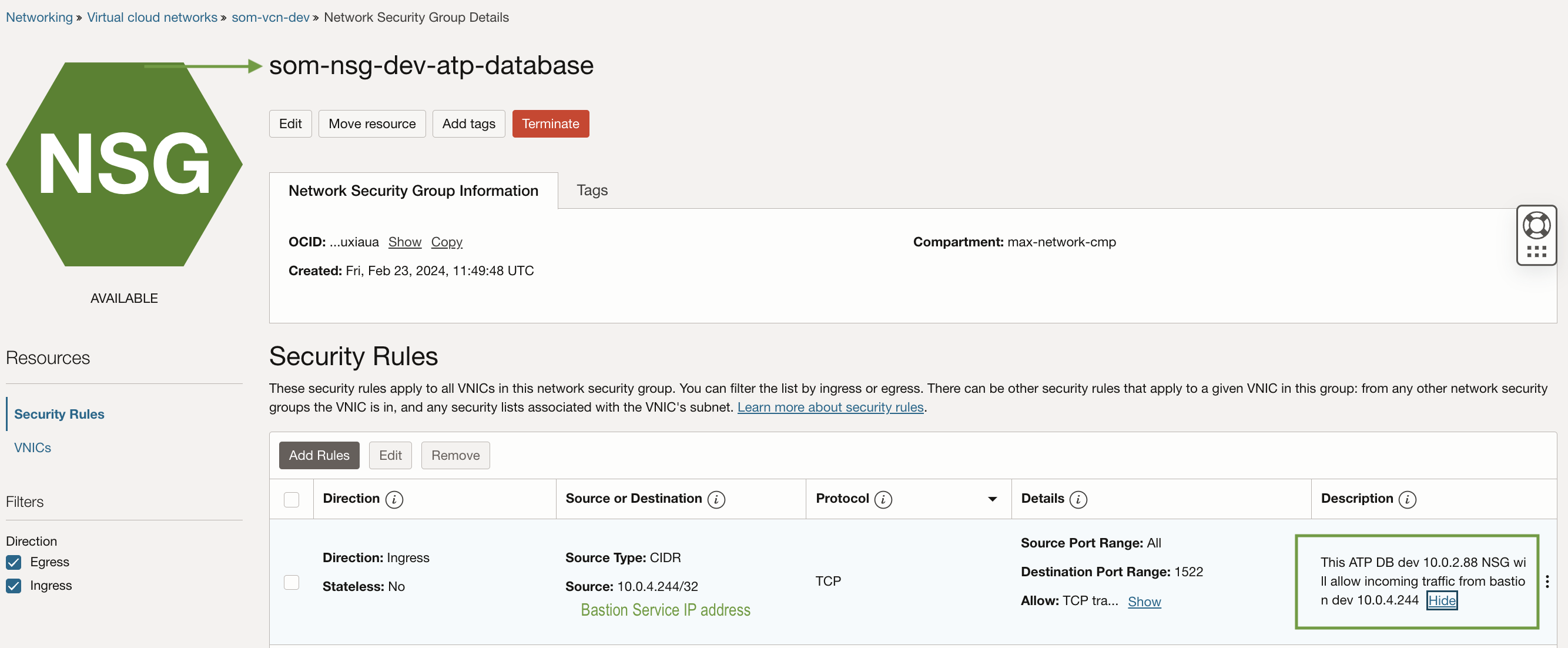
a) Ingress rule for ATP databse
Create the NSG ‘som-nsg-dev-atp-database’ and include an ingress rule allowing traffic from the Bastion service.
Now, the “som-nsg-dev-atp-database” needs to be added to the ATP network security group. You can find “Network Security Groups” under the Network segment.
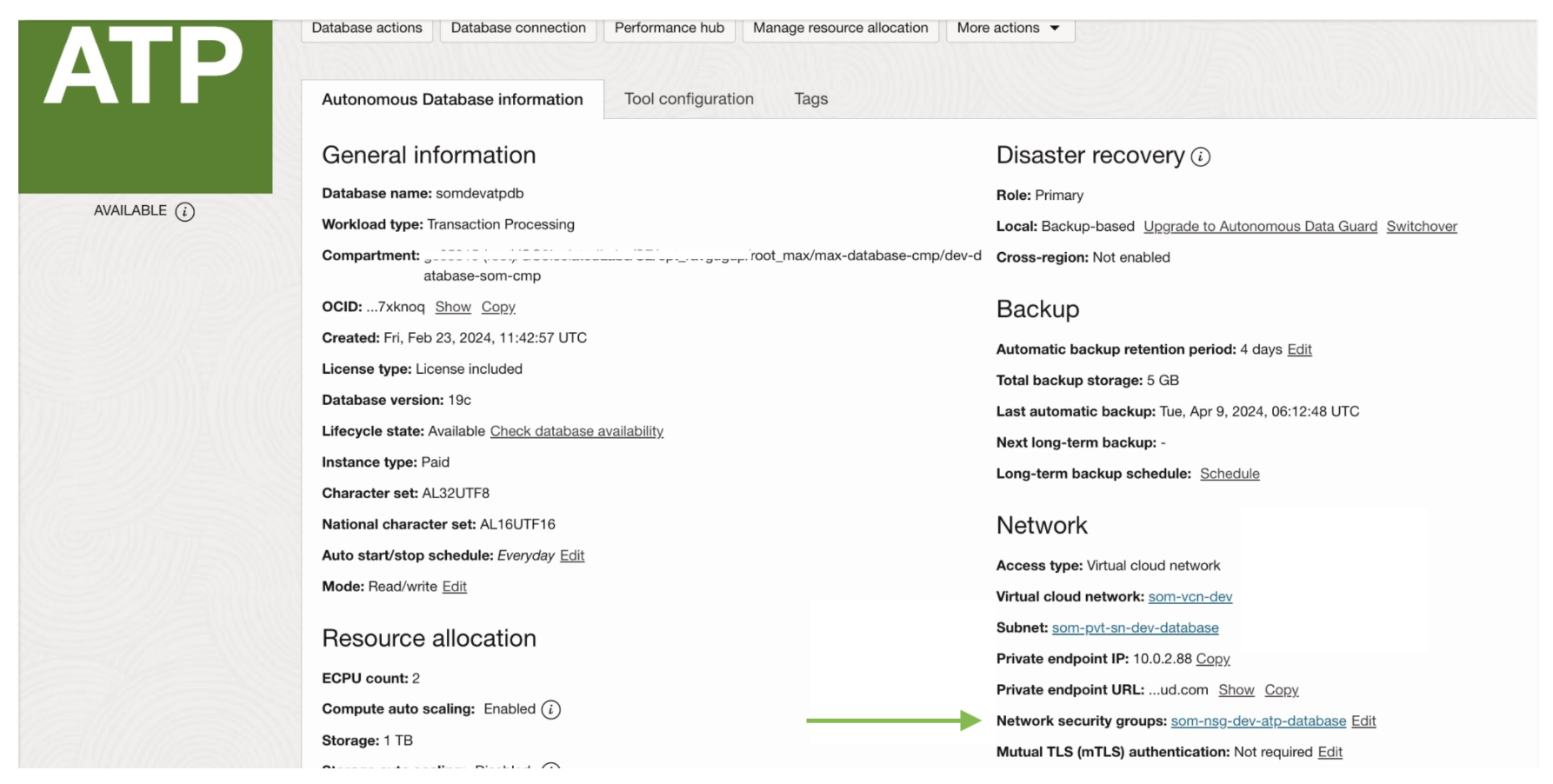
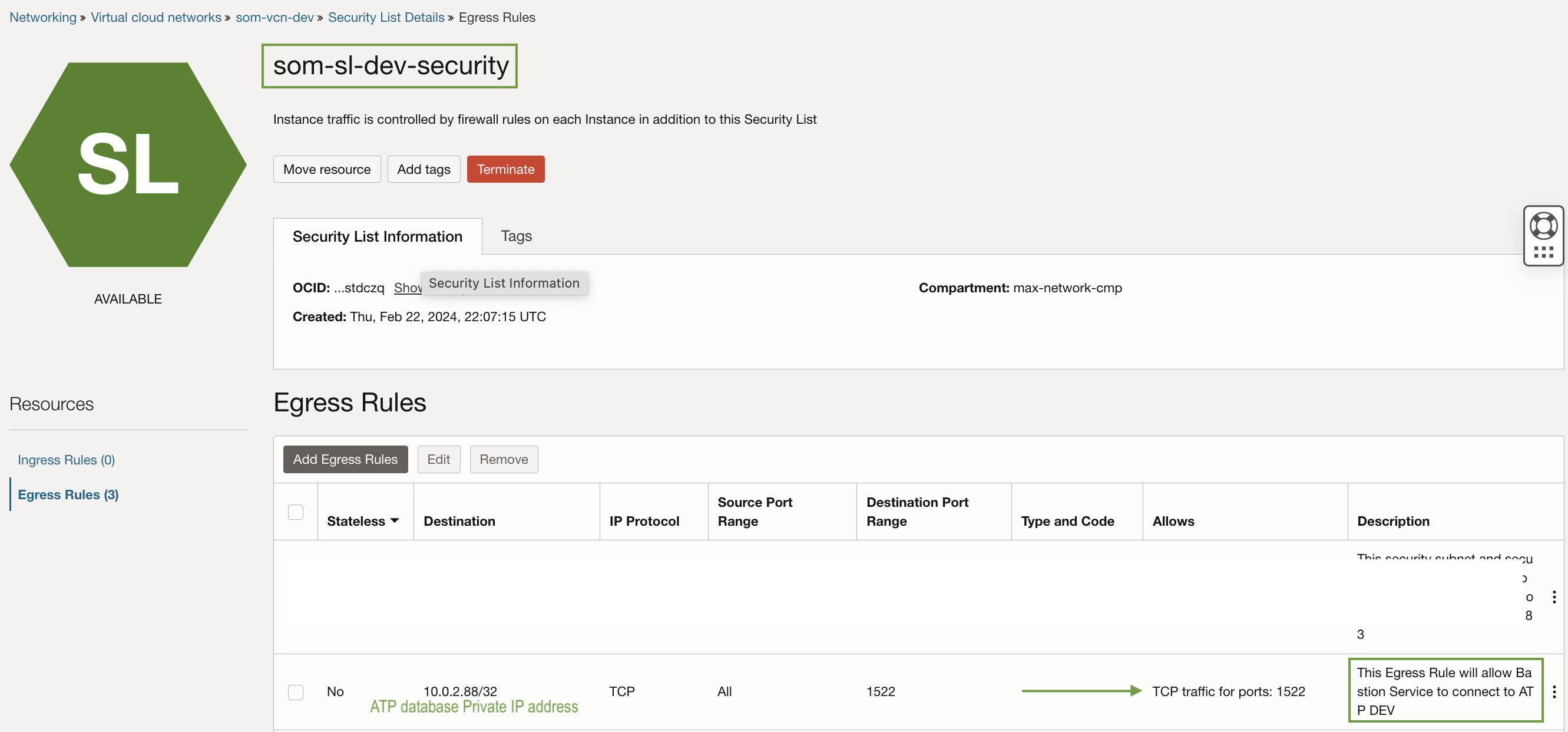
b) Egress rule for ATP database.
Create an Egress rule in the Security List ‘som-sl-dev-security’ to allow all traffic from the Bastion service to the ATP database.
c) Access ATP database
• Download the ATP wallet and make changes in the “tnsnames.ora” file.

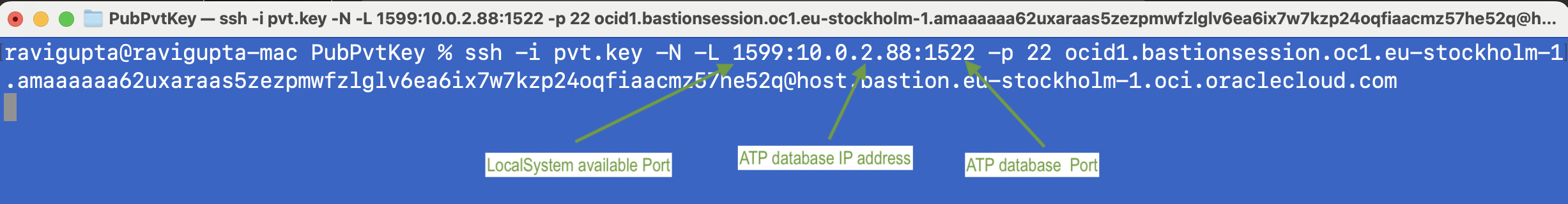
• Create a Bastion session with the ATP private IP address and port 1522. Copy the SSH command and modify the port as saved in the tnsnames.ora file.
• Connect SQL Developer to the ATP database.
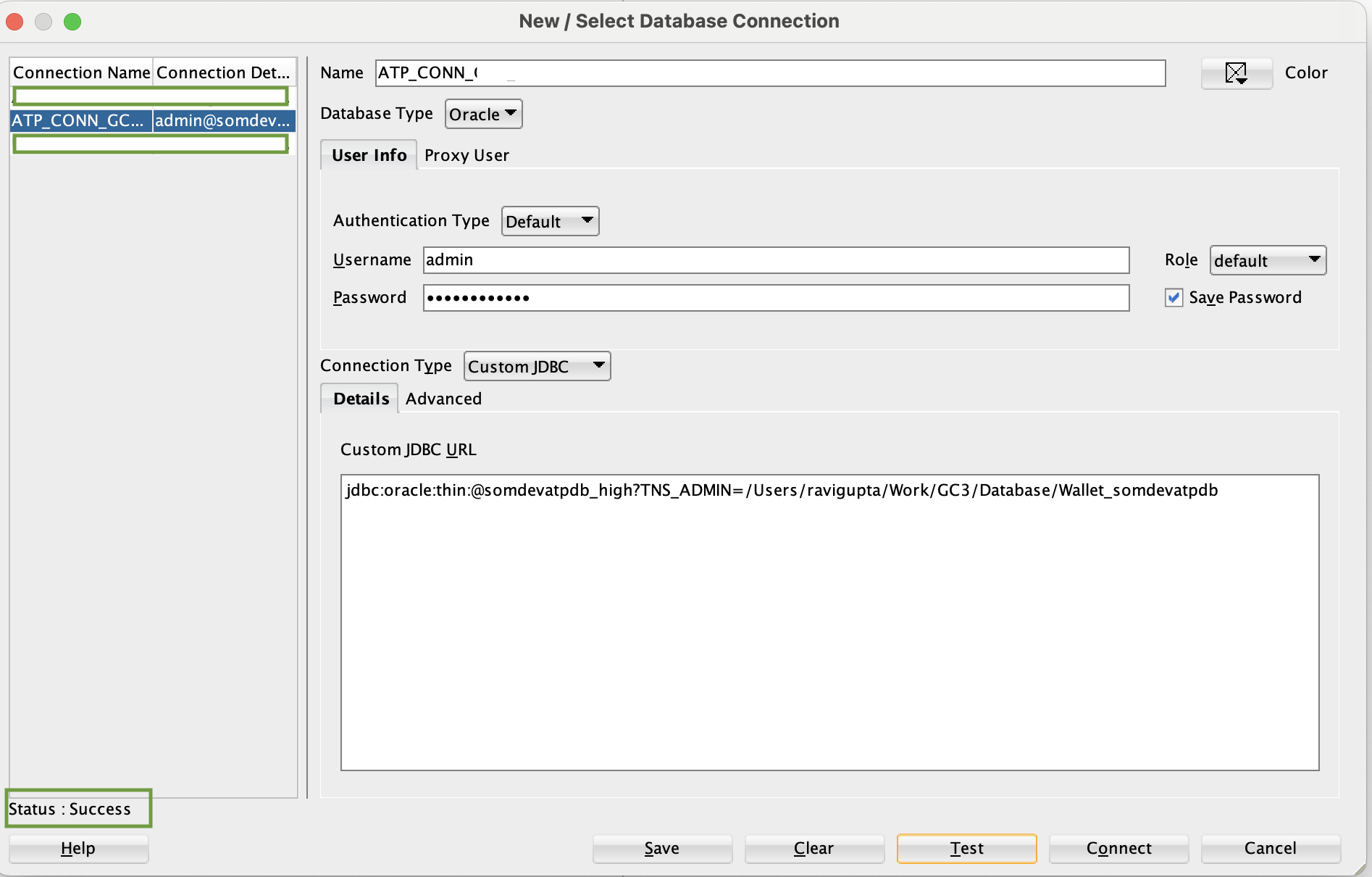
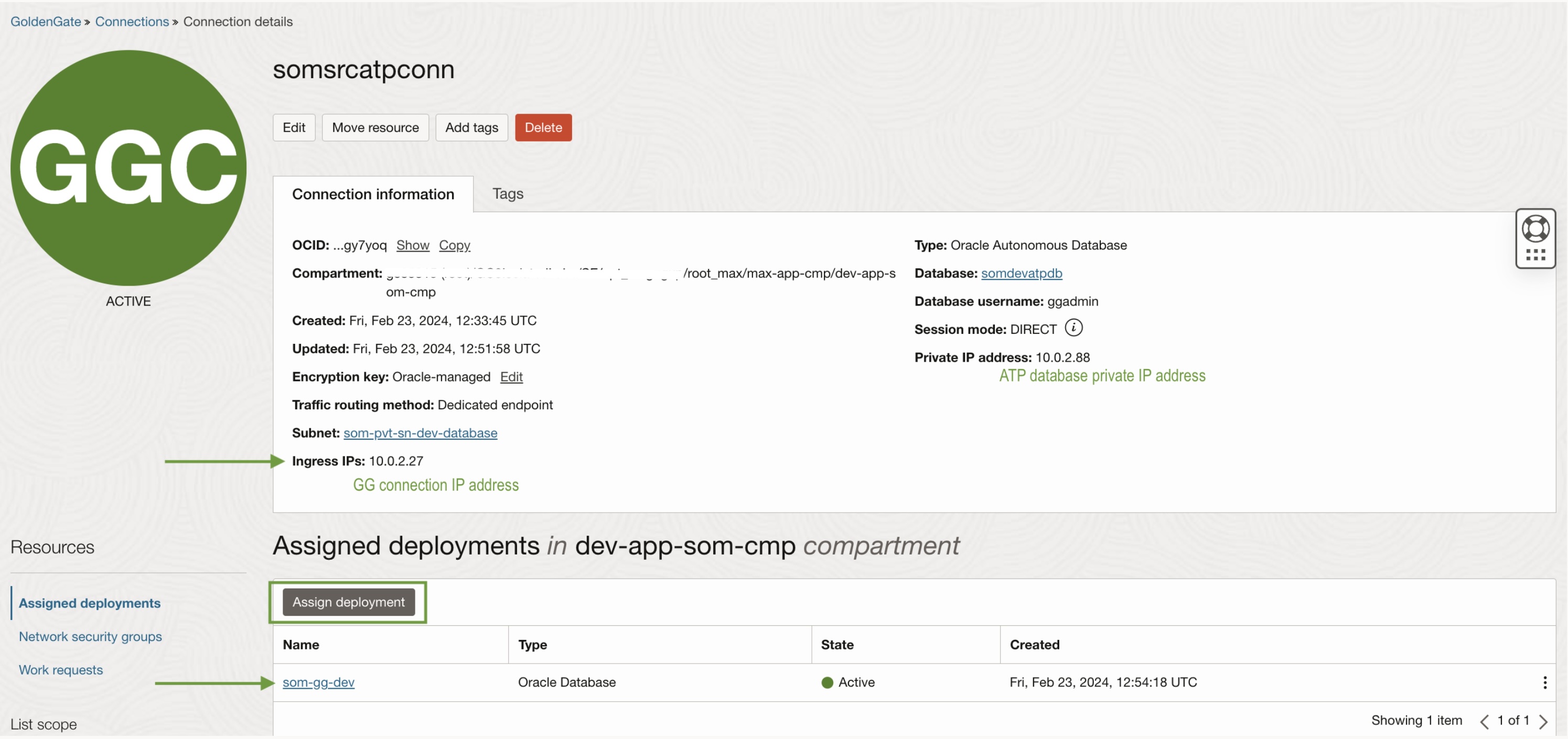
3. Create GoldenGate Database connection.
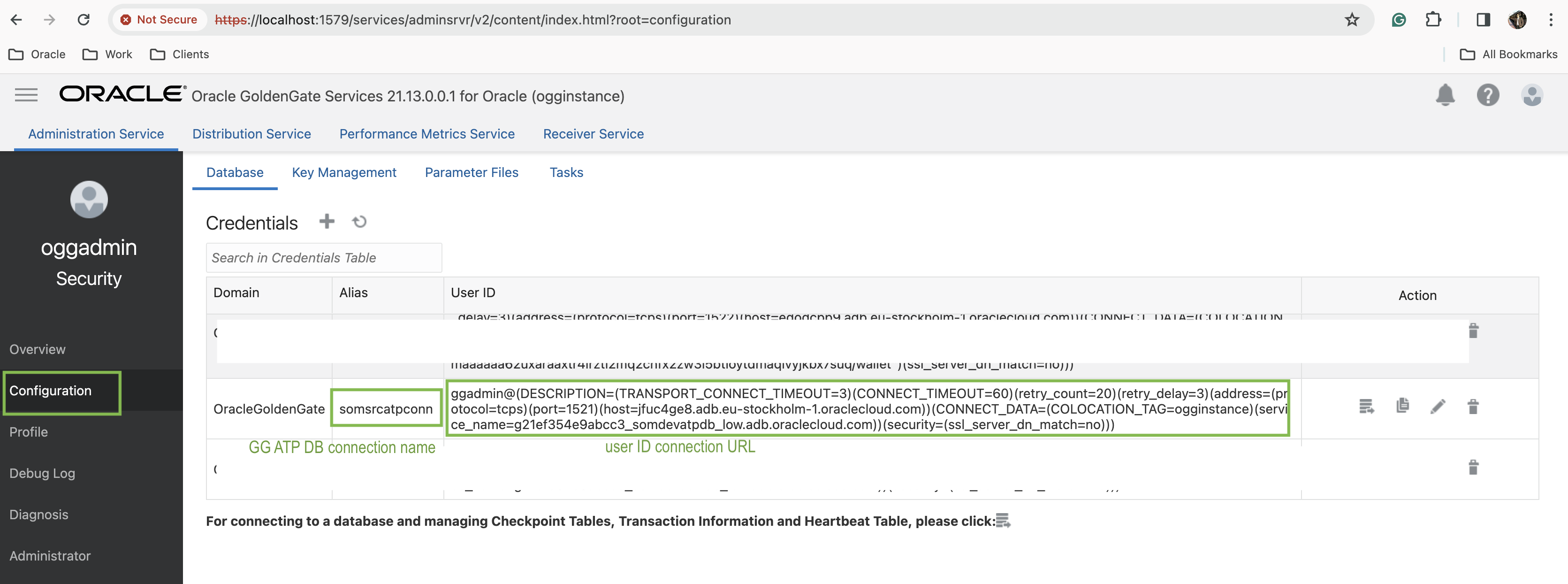
Now, we need to create an Autonomous Database Connection to database “somsrcatpconn” in OCI GoldenGate.
Select database by selecting the compartment “dev-database-som-cmp”. “ggadmin” user in ATP needs to unlock and provide the password in the configuration.
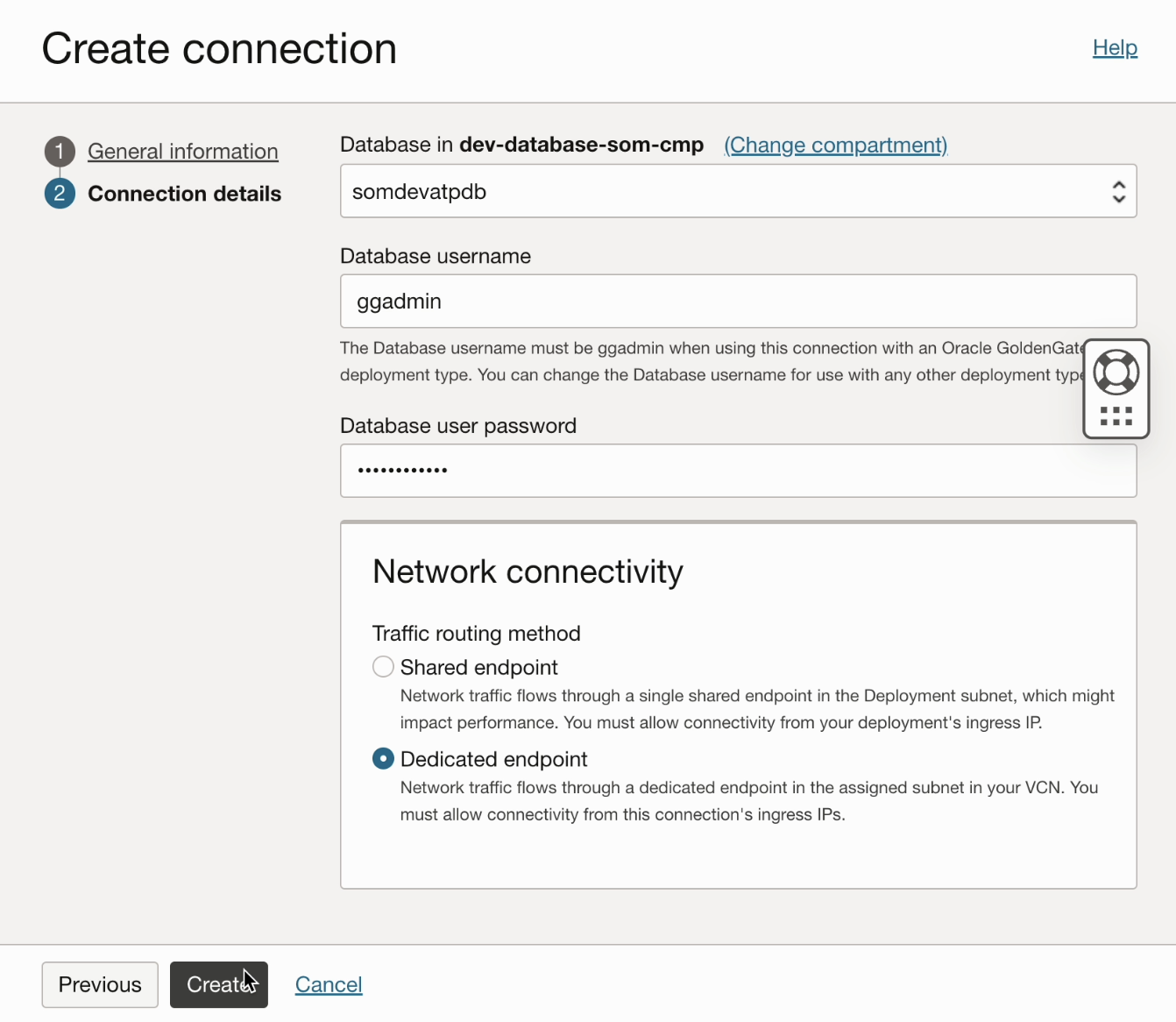
Configure the connection on the GoldenGate connection configuration page and assign it to the GoldenGate deployment.
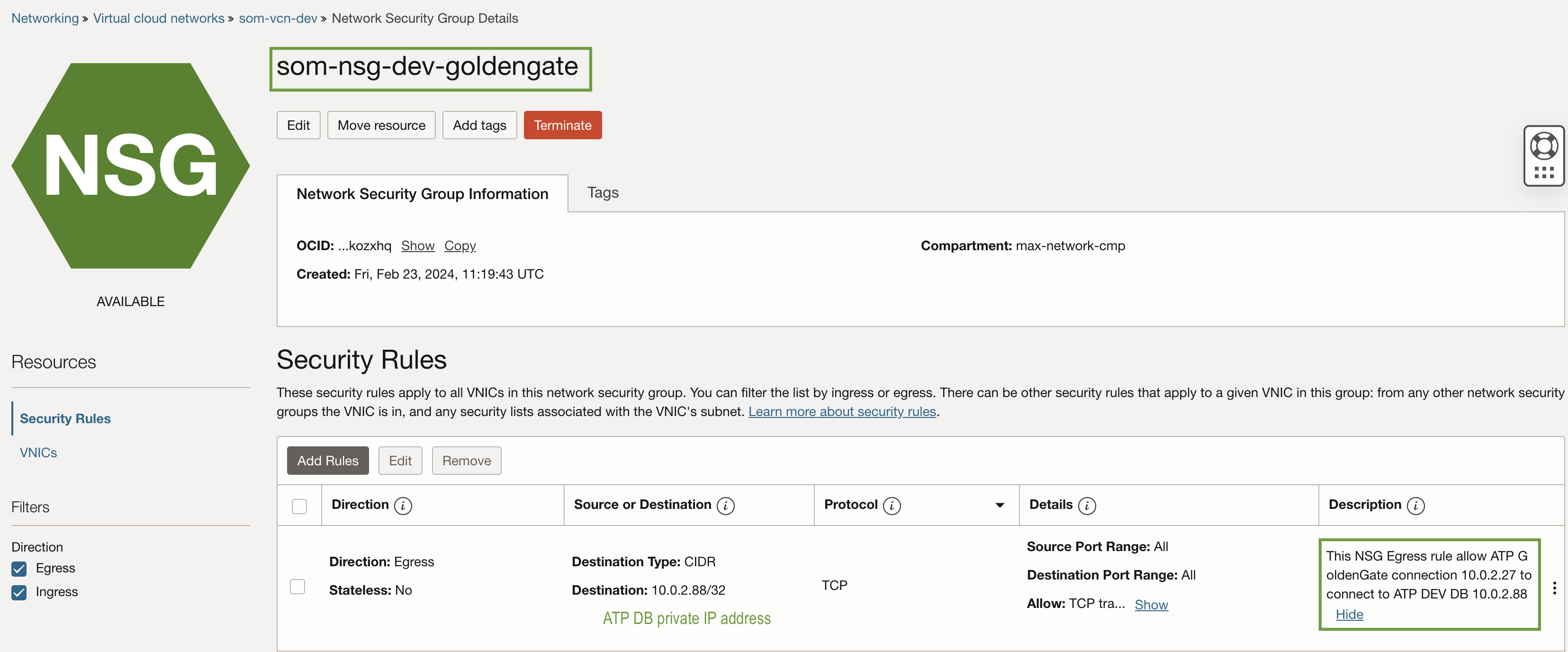
a) Egress rule for GG database connection.
Create an egress rule on the GoldenGate NSG ‘som-nsg-dev-goldengate,’
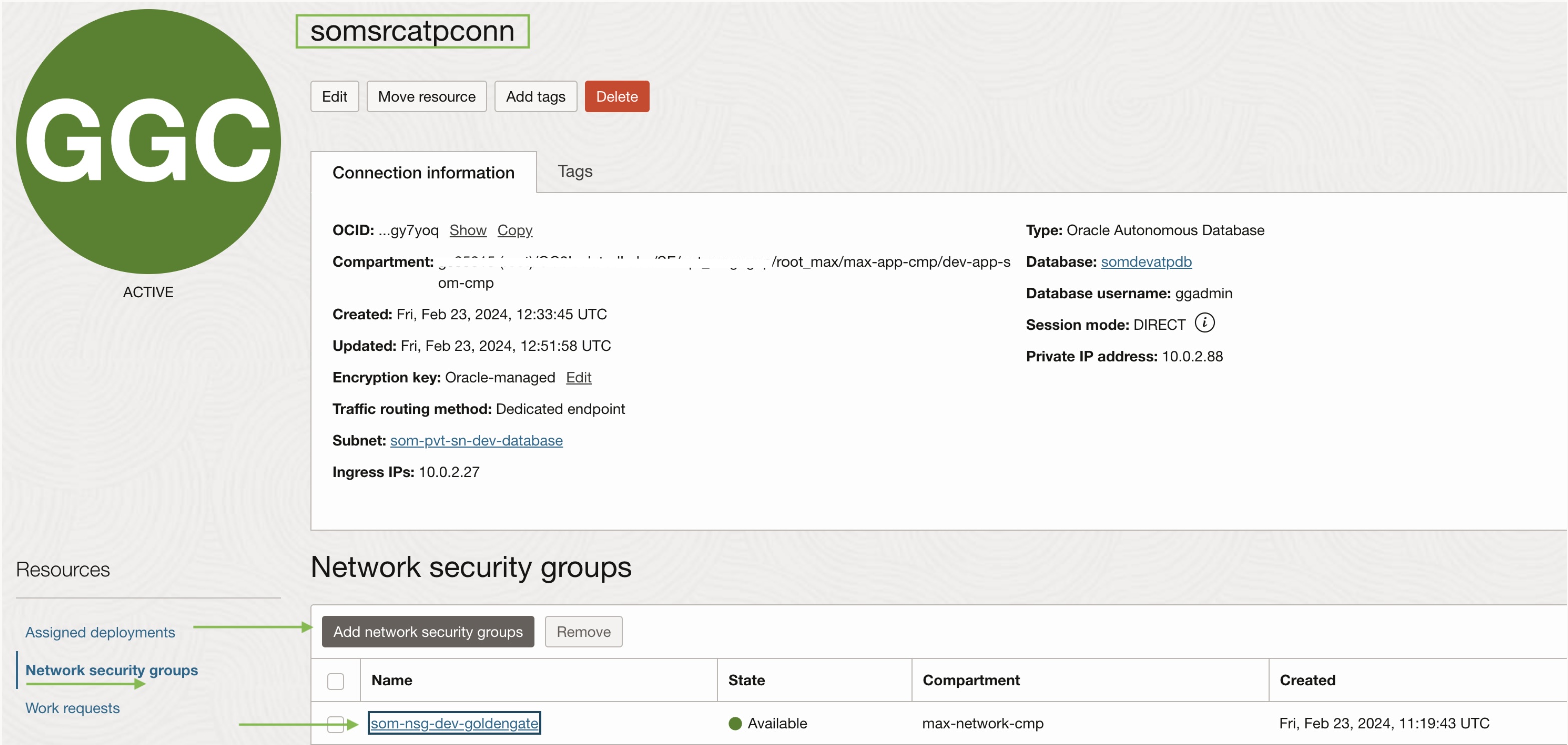
NSG “som-nsg-dev-goldengate” needs to attach to GoldenGate database connection “somsrcatpconn”.
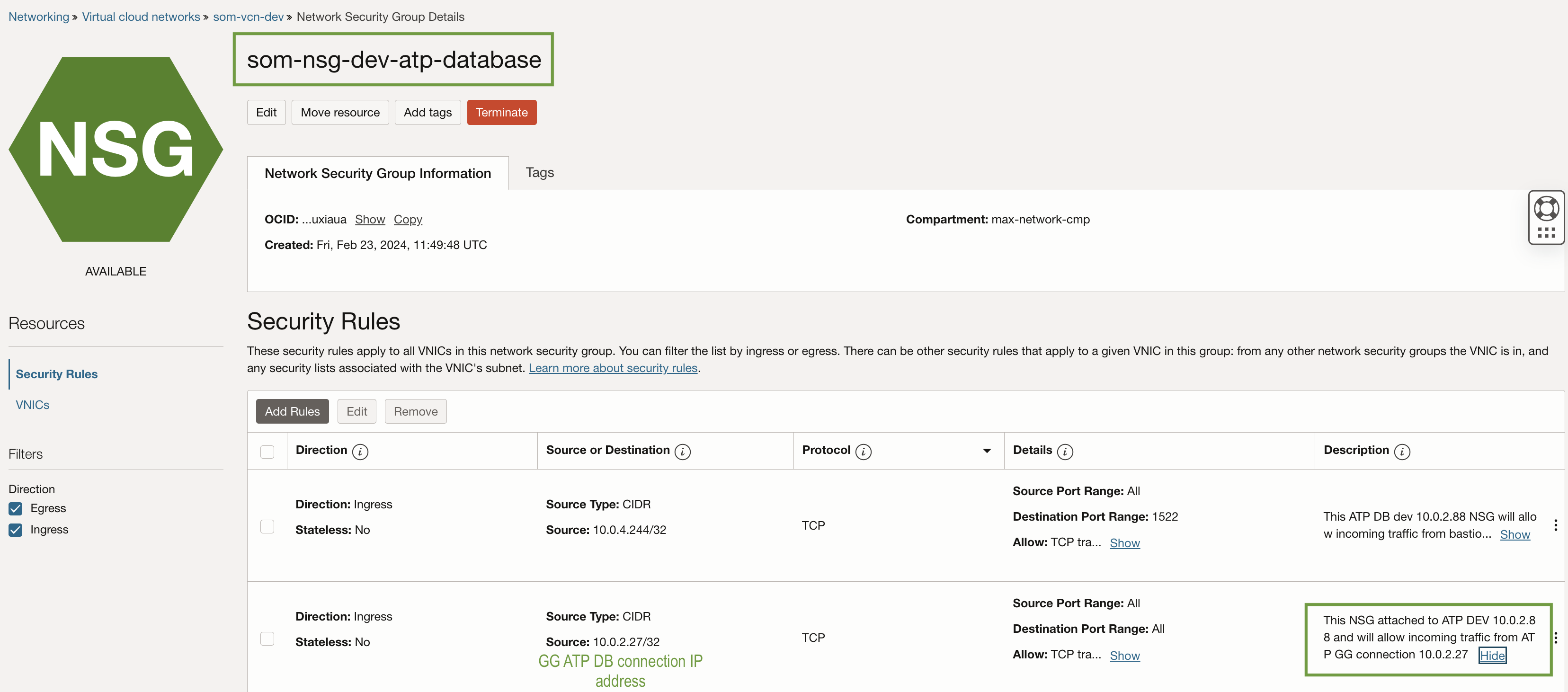
b) Ingeress rule for GG database connection.
Create an Ingress rule on the ATP DB NSG ‘som-nsg-dev-atp-database’ to allow all traffic from the GG DB connection.
After completing all the steps for the GoldenGate Database connection, log in to GoldenGate, and you will find the connection created.
Note : Perform the identical steps to include the target database.
Outcomes : After completing this hands-on demonstration, you will be able to proficiently provision and manage OCI GoldenGate and its associated OCI resources with a focus on security.You will be equipped to create and configure Virtual Cloud Networks (VCNs), Private Subnets, Network Security Groups, and set up precise Ingress/Egress rules for controlled access. Additionally, you will understand how to use the Bastion Service to securely access OCI GoldenGate, the GoldenGate AdminClient, and databases within a private subnet. This knowledge will enable you to implement and maintain a secure and efficient data integration and replication environment within Oracle Cloud Infrastructure.
Part 2: GoldenGate Artifacts Creation
