We’ve just released Oracle Key Vault (OKV) 21.10, which introduces new capabilities and features that improve security, simplify operations, and increase the value you get from your investment in Key Vault. In OKV 21.10 we have:
- Simplified key management for DBMS_CRYPTO
- Expanded SSH key governance to include Microsoft Windows clients
- Added TDE key management for Autonomous Database Serverless (ADB-S).
- Created a new dedicated, least-privilege role for Key Vault monitoring
- Introduced one-click automatic rotation of OKV’s internal-use certificates
- Added configurable network ports for OKV
- Added support for endpoints running Linux on ARM64 and IBM Z mainframes
As always, this latest update includes full-stack patching to address security and stability issues in the embedded operating system, database, and Key Vault application.
Simplified key management of DBMS_CRYPTO applications
DBMS_CRYPTO is a database package for cryptographic operations like encrypting and decrypting data. A long-running challenge when using DBMS_CRYPTO is key management. Unlike TDE, DBMS_CRYPTO has no built-in key management framework. Starting with OKV 21.10, you can use Key Vault to generate, protect, and distribute keys for DBMS_CRYPTO. Here is an example of DBMS_CRYPTO using Key Vault:
-- Fetch key value from OKV
key_id := okv_key_mgmt.locate_key('', 'finance_dept_key');
key_value := okv_key_mgmt.fetch_key('', key_id);
You can now execute DBMS_CRYPTO’s ENCRYPT and DECRYPT functions using the fetched key just as if you’d generated and embedded a key value in the code.
Key Vault 21.10 introduces a new low-code integration accelerator framework that reduces manual effort. To help you use Key Vault with DBMS_CRYPTO, our first integration accelerator makes it easy for you to use Key Vault to create and centrally manage keys for DBMS_CRYPTO. To take advantage of the accelerator, you just need to download the library package, as shown below, and deploy it following the instructions included in the package. Watch for additional accelerators in future release updates.
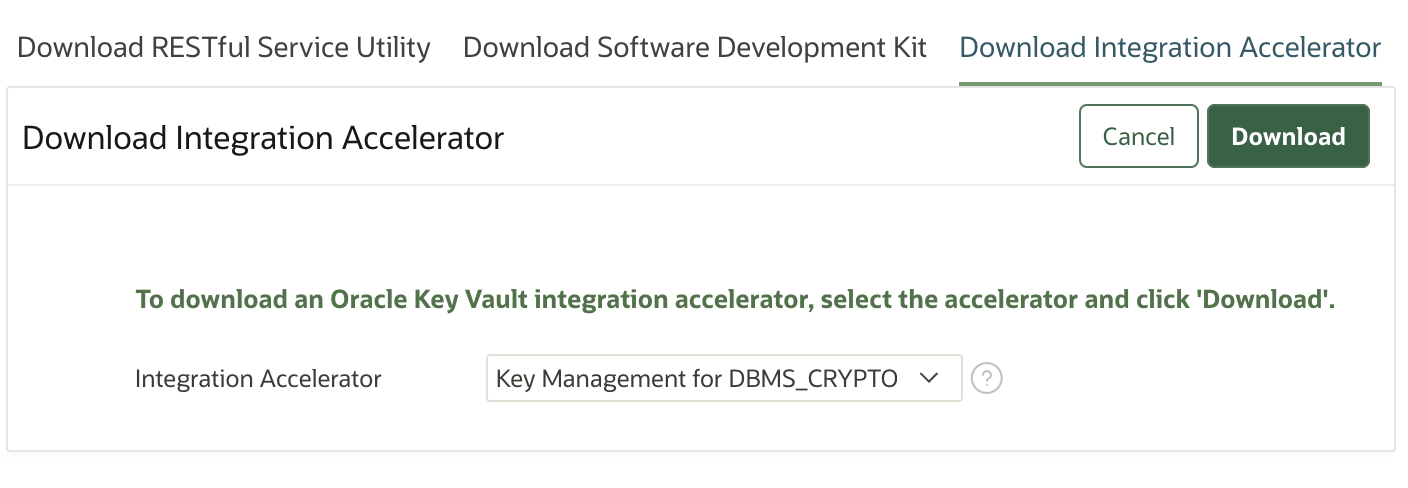
SSH key governance for Microsoft Windows clients
Key Vault 21.7 introduced SSH key governance, allowing you to protect your SSH keys and providing governance of SSH for remote server access. Key Vault 21.10 adds support for SSH key governance for OpenSSH clients running on Microsoft Windows. Now, you can take advantage of centralized management for your SSH keys, including control over which users can access which keys. SSH key governance also gives you ability to report on that access. For an overview of SSH key management with Key Vault, see our earlier blog, Simplify and secure SSH key management with Oracle Key Vault, or try it yourself in this new LiveLabs workshop.
Manage ADB-S TDE master keys in Oracle Key Vault
Key Vault now supports key management for Oracle Cloud customers using Autonomous Database Serverless (ADB-S). Key Vault, deployed in your OCI tenancy from the Oracle Cloud Marketplace, in AWS, GCP, Azure, or your on-premises data center, allows you to retain complete control over your encryption keys rather than relying on a service provider to generate, store, or manage them.
A new dedicated, least-privilege role for monitoring Key Vault
The user account responsible for monitoring Key Vault needs to observe the node health, cluster health, cluster conflicts, network communication, and application health. Because it is important to maintain separation of duties, these monitoring users should not be able to create endpoints, change settings, or impact key operations. OKV 21.10’s new monitor privilege allows you to create least-privileged OKV accounts with the ability to monitor OKV, but not do anything else.
One-click automatic rotation of OKV’s internal-use certificates
Oracle Key Vault uses certificates to secure communication paths originating from or terminating at the Key Vault server. OKV alerts you ahead of time when certificates are due to expire, and customers can now rotate certificates with a click of a button.
Configurable network ports for OKV
Some organizations restrict which network ports can be open for communication between OKV nodes. Until now, Key Vault required port 1522 for communications between read-write pairs and port 22 for SSH connections to the Key Vault server. Oracle Key Vault now allows you to specify which ports you want OKV to use for those purposes.
Full Key Management support for Linux on ARM64 and IBM Z mainframe
OKV 21.10 adds support for Oracle databases running on Linux for ARM64 and Linux on IBM Z. The expanded support includes TDE key management, SSH key governance, and secrets management. The complete Key Vault client software package, including the okvutil command line tool, the PKCS#11 library for TDE, the RESTful services utility for scripted operations, and the C and Java SDKs, along with all features and capabilities are included in this support.
Seamlessly Upgrade to Oracle Key Vault 21.10
Oracle strongly recommends that you upgrade existing deployments to OKV 21.10 for increased stability and security. OKV’s cluster architecture supports zero downtime for database targets during Key Vault upgrades and patching.
For fresh installations, you can download Key Vault 21.10 from the Oracle Software Delivery Cloud. In addition, you can launch Oracle Key Vault 21.10 from the Oracle Cloud Marketplace in your OCI tenancy in minutes (watch “Click to Deploy”).
Addressing security and stability issues
Key Vault 20.10 includes
- Security and stability fixes from Oracle Database release update 19.25 (October 2024) for the embedded OKV repository
- Security and stability fixes for the embedded Oracle Linux 8.10 operating system
- Security and stability fixes for the underlying components, including Oracle GoldenGate, Oracle APEX, Oracle Rest Data Services (ORDS), Java Runtime Environment (JRE), Oracle Instant Client, and Tomcat
About Key Vault
Oracle Key Vault provides continuously available, fault-tolerant, and highly scalable, centralized key and secrets management for Oracle Database, MySQL, GoldenGate, ZFS Storage Appliance, ZDLRA, SSH, and custom applications. You can deploy Oracle Key Vault in Oracle Cloud Infrastructure (OCI), Microsoft Azure, Amazon AWS, Google GCP, and on-premises on dedicated hardware or virtual machines.
Key Vault sets the standard for security, automation, scalability, and continuous availability with its software appliance form factor, fault-tolerant multi-master cluster architecture, hybrid deployment capability, and comprehensive RESTful APIs.
Oracle Key Vault 21, the third major release of Key Vault, simplifies the administration of keys and secrets for environments with many endpoints. It is the only purpose-built key management product designed to support the wide variety of Oracle Database deployment models, including Real Application Clusters (RAC), Data Guard, Globally Distributed (sharded) databases, Multitenant, and cloud databases.
For more information:
Visit the Key Vault product page at:
https://www.oracle.com/security/database-security/key-vault
Test drive Key Vault 21.10 in the Oracle Key Vault LiveLabs workshop at no cost today.
