Most organizations already encrypt their sensitive data, but encryption alone is not enough to stop a breach. In many real-world incidents, the weak point is not encryption but key management: how keys are generated, stored, shared, accessed, and monitored over their lifecycle. If attackers gain access to an unprotected or poorly managed key, they can decrypt everything. That is why robust, centralized key management is just as critical as strong encryption. Oracle Key Vault (OKV) is designed to close this gap by centralizing and securing keys for TDE and SSH.
However, many organizations deploy OKV on generic servers, which often introduces unexpected delays and operational risks:
- Complex integration burden: While you may just want key management as a single, integrated solution, you are instead forced to stitch together hardware, OS, networking, storage, and key management tools. This converts every implementation into a custom integration project, rather than letting you focus on business outcomes.
- Hidden infrastructure risks: Running OKV across diverse hardware and software stacks, where components such as storage and NIC drivers may not be fully validated together, can lead to late-stage issues, extended testing, compatibility issues, and support uncertainty.
These infrastructure challenges can delay rollouts by weeks or even months, leaving the keys exposed to avoidable operational risk.
What is Oracle Database Appliance (ODA)?
Oracle Database Appliance (ODA) is a 2U Oracle-engineered system that integrates compute, NVMe flash storage, Oracle Linux, built-in KVM virtualization, and Appliance Manager into a single pre-integrated stack. Unlike generic hardware, ODA is delivered as an Oracle-validated platform with coordinated firmware and OS patch bundles.
How OKV on ODA removes integration and infrastructure friction
As a fully tested Oracle platform, OKV on ODA removes the guesswork from hardware and OS integration, and provides a reliable platform. OKV runs as a dedicated virtual machine on ODA, and every OKV release from 21.12 onward is validated on ODA before it ships, so customers get streamlined support and a single point of accountability across hardware and software.
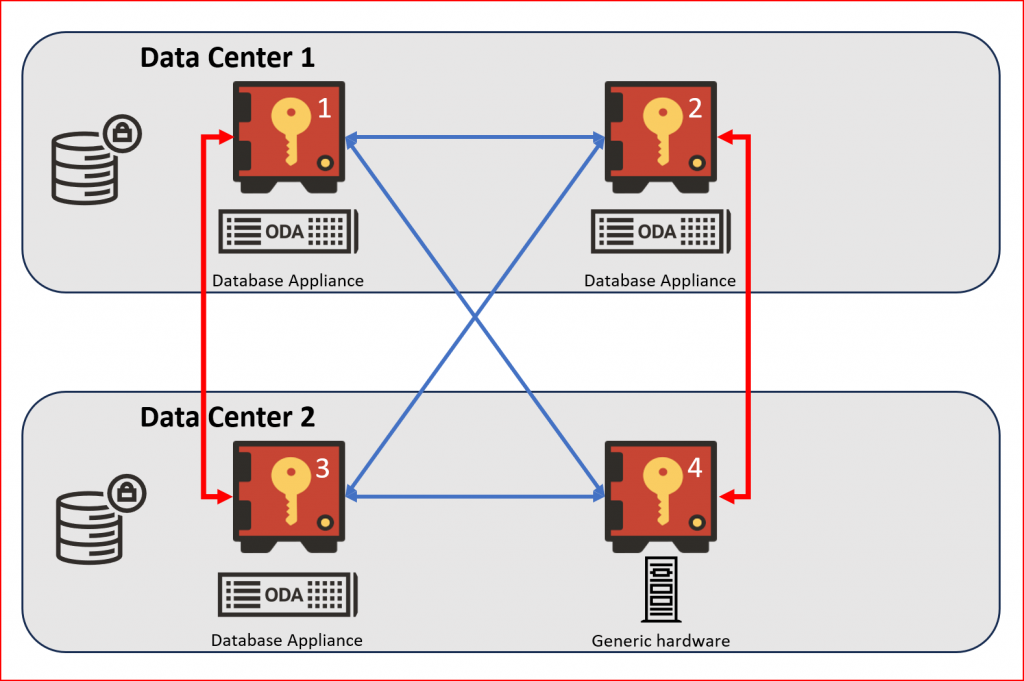
Figure: 4-node OKV Mixed Deployment
- Recommended 4-node cluster: Two read/write pairs spread across data centers for robust HA and fast failover in most enterprise deployments.
- Multi-region HA/DR designs: Deploy OKV on ODA instances across regions, so key management services remain available even if a region goes down.
Migrating existing OKV clusters to ODA
- Step 1 – Deploy OKV on ODA
Deploy Oracle Key Vault 21.12 or later as a dedicated KVM virtual machine on an Oracle Database Appliance X11-S (2U, 32-core AMD EPYC, 256 GB RAM, 13.6 TB NVMe). Configure OKV to match your current OKV cluster settings. - Step 2 – Enroll ODA-based OKV node(s) in the OKV cluster
During a regular RU maintenance window, add the ODA-based OKV node to the existing OKV cluster. The OKV cluster architecture allows you to add new ODA-based OKV nodes without any downtime. - Step 3 – Delete OKV node on generic hardware from the OKV cluster
Once the ODA-based OKV nodes are fully in service and clients are actively using the cluster, decommission the OKV nodes running on generic hardware from the OKV cluster, with no changes required on the client side.
For detailed configuration steps, see the OKV documentation here.
OKV-on-ODA Reference Configuration
- Key Management Software: Oracle Key Vault 21.12 or later
- Deployment Model: Oracle Key Vault 21.12 runs as a KVM virtual machine on an Oracle Database Appliance X11-S.
Benefits of the ODA platform for OKV implementations:
1. OKV on an engineered ODA platform
With OKV on ODA, you get a pre-integrated combination of Oracle hardware, Oracle Linux with built-in KVM virtualization, and Oracle Key Vault. This lets you run OKV, and all required supporting services on a single engineered appliance with strong workload isolation, without needing to design or validate your own key management hardware stack.
2. Pretested lifecycle and coordinated patching
In a generic off-the-shelf environment, you are responsible for continually testing that servers, storage, firmware, network, OS, and OKV still work together as each layer can change independently. With OKV on ODA, Oracle validates the full stack in advance. More importantly, the ODA patch bundle keeps the platform (servers, storage, firmware) in sync, and a separate OKV release update (which also delivers the relevant OS updates for OKV) is applied on top. Together, these coordinated patches reduce your integration effort.
3. Simple deployment and operations: ODA platform management is handled through Appliance Manager for ODA (browser UI, CLI, REST APIs). It gives you a single place to deploy, configure, monitor, and apply coordinated patches, which simplifies day-to-day operations.
4. Capacity-on-demand: Start with as few as 16 cores and scale up as needed, so your OKV deployment can handle more keys and clients over time without redesigning the environment.
5. Security, compliance, and hardening: Your key management stack runs on Oracle Linux hardened with only the required OS services and end-to-end auditing across ODA and OKV, providing a compliant platform.
Conclusion
Deploying Oracle Key Vault on ODA provides strong security, tight integration, reliability, and simplified management. Oracle Database Appliance is more than just a server. It is a fully engineered platform that provides a complete, validated, secured foundation for your key management.
Getting Started:
Refer to the ODA specification sheet (ODA Spec link) for detailed ODA hardware and configuration information.
Use the basic sizing guidance as a starting point, and then contact your Oracle account team to set up an OKV-on-ODA sizing and migration workshop.
Use the Installing Oracle Key Vault on ODA documentation to guide your technical design and day-to-day operations.
