Your database credentials shouldn’t be the weakest link in your security chain. Too many organizations still protect their most valuable data with nothing more than a username and password—a setup as classic as SCOTT/TIGER itself. But attackers have gotten smarter, and regulations are only getting stricter. Many of our database customers already use PKI, Kerberos, and smart cards for their database logins, but if you are still using passwords, you can improve your security posture quickly and easily. Welcome to multifactor authentication (MFA) for database password users!
Toughen Database Security with Multifactor Authentication
Every day, cybercriminals try their luck with phishing, credential stuffing, and brute-force attacks, hoping to capture your users’ database passwords. As much as we hate to admit it, users sometimes reuse passwords, embed them in scripts, or choose easy-to-guess passphrases. Compliance requirements are becoming ever more demanding. Regulations such as PCI DSS, EU DORA, EU NIS2, NIST 800-63, and NIST 800-53 now mandate or strongly recommend stronger authentication measures like MFA. The bottom line: knowledge of a password alone should not be enough to grant access to the database and sensitive information.
How do you stay ahead of attackers and satisfy auditors—without making life harder for your team?
MFA Arrives for Local Oracle Database Users: It’s here!
Until now, enabling MFA meant relying on external identity providers such as Microsoft Entra ID, Oracle Cloud Infrastructure (OCI) Identity and Access Management (IAM), or RADIUS. Starting with the July 2025 database release update (DBRU) for Oracle Database 19c and 23ai, you can enable MFA for database users with local database accounts – yes, even for accounts like SCOTT/TIGER. The new release changes the landscape for local users by adding a second factor through their mobile devices.
Initially, we are supporting two mobile applications: Oracle Mobile Authenticator (OMA) and Cisco Duo on Android and Apple devices.
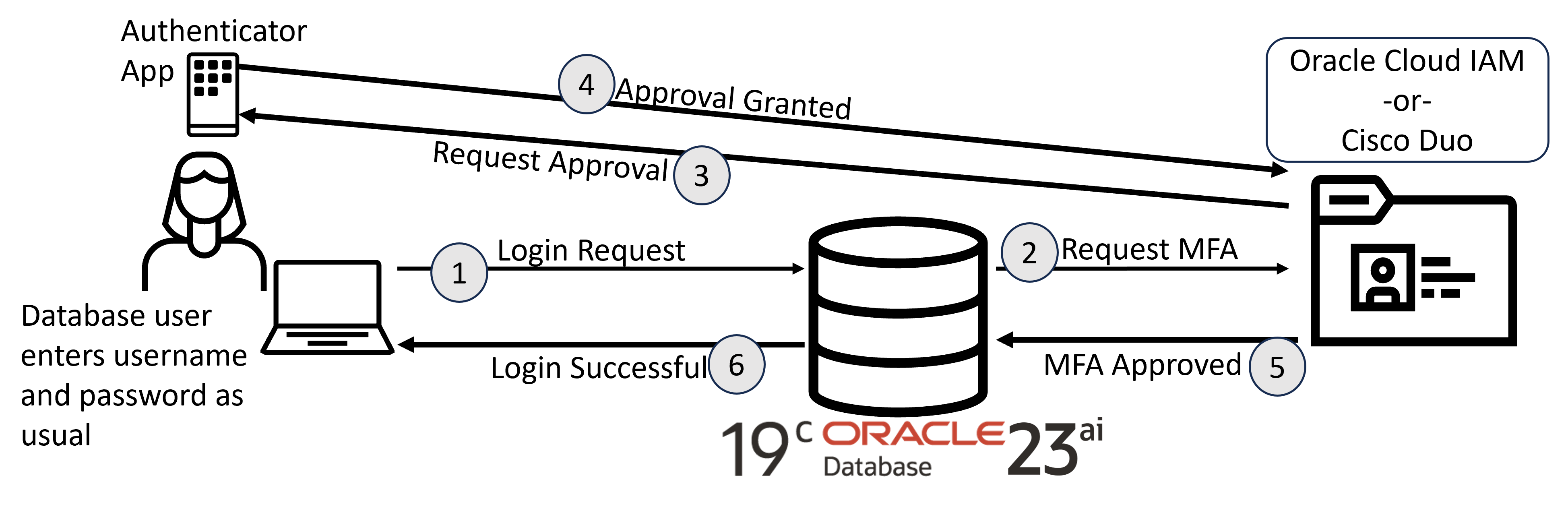
What’s It Like for Users:
- Users begin the login process with their usual credentials (username and password) in SQL*Plus, SQLcl, or any compatible tool.
- The database requests MFA from the push notification service.
- Immediately after, a push notification appears on their registered mobile device, prompting them to confirm the login.
- The user approves the request
- The push notification service notifies the database that the login request is approved
- That’s it – they’re in. No extra codes, no hassle, and ZERO changes to client software configuration, making the rollout easy.
Note: Because this feature relies on an interactive login, it is intended for human users, not applications.
Quick Setup: What You Need
Before turning on MFA, configure these two essentials:
- Service Registration: Your organization will need an account with OCI IAM or Cisco Duo. Both services offer free and paid tiers. Update the database configuration with information about the push notification service. Nothing to install on the database server. You’ll do this once for each pluggable database.
- Email Integration: When you add MFA for your users, they will receive an email with MFA registration instructions. This would require you to configure your database to integrate with your email system.
A single SQL command enables MFA for a user:
ALTER USER scott ADD FACTOR ‘oma_push’ AS ‘scott@email.domain’;
Your user receives an email with step-by-step instructions to download the required authenticator app and register their mobile device.
More Choices: Push notifications or certificate-based MFA
- Push Your Way: Choose between OCI IAM’s Oracle Mobile Authenticator (OMA) app or Cisco Duo’s mobile authenticator app for your MFA push notifications.
- SmartCards, including Common Access Card (CAC) support: Requires both a smartcard (PKI certificate) and a password at login—a strong multifactor solution for users who need it. SmartCards can be used instead of a mobile authenticator.
Watch this space as we extend MFA to add other modes.
Why MFA: Benefits at a Glance
- Works with what you’ve got: Not everyone has access to MFA-enabled directories. Upgrade your existing users’ security in minutes.
- Blocks phishing and stolen passwords: Even if a password is compromised, attackers can’t log in without the registered mobile device.
- Easy on your users: No codes to copy. A quick tap on the phone is all it takes.
- Flexible and compliant: Helps you meet PCI DSS, DORA, and other mandates—and be ready for future standards.
- Easy migration: Select the users for whom you want to set up MFA, leaving other users and application accounts as they are.
- No client updates are needed: No updates needed on the database clients or the drivers. With just database server side update, you can add MFA support for your users.
- Seamless Cloud Integration: Already using Oracle Mobile Authenticator or Cisco Duo? You’re covered—this fits perfectly into your existing identity setup.
Ready to Strengthen Your Database Security?
Don’t let legacy credentials be your Achilles’ heel. Bring multifactor authentication to your Oracle Database 19c and 23ai as part of your regular July 2025 database release update.
Want the technical details? Check out our updated documentation.
Need help integrating MFA with OCI IAM or Cisco Duo? We’re here to support you.
Try out this new feature—your data (and your auditors) will thank you!
