Securing your databases shouldn’t be a guessing game. For IT admins, DBAs, and security professionals, the pressure to prevent data breaches, pass audits, and keep up with evolving standards like DISA STIG is relentless. As threats and compliance requirements grow more complex, closing configuration gaps is more critical than ever.
Since its debut in 2016, the Database Security Assessment Tool (DBSAT) has helped many organizations worldwide meet audit, compliance, and advanced security goals.
Today, we’re thrilled to introduce DBSAT 4.0, a major leap forward in database security assessment. With DBSAT 4.0, you get expanded checks, support for the latest STIG standards, faster answers, tighter controls, and built-in references to Oracle’s latest security documentation. You can now quickly spot vulnerabilities, understand exactly what needs attention, and get actionable recommendations every step of the way.
We are excited that the Defense Information Systems Agency (DISA) now highlights DBSAT in its Oracle Database 19c Security Technical Implementation Guide (STIG), validating DBSAT as a trusted way to check, fix, and document your database security posture. Specifically, Group ID V-270520 states:
“…for each finding, DBSAT recommends remediation activities that follow best practices to reduce or mitigate risk. Review the security status, provided by the DBSAT report, check the categories (sections) and review the findings by risk level and recommendations. For each recommendation, each organization must determine which remediation activities to implement according to their security policies.”
What’s New in DBSAT 4.0
1. Support for the Latest DISA STIG Compliance Standards
What’s new: We’ve updated our support for the DISA STIG recommendations for Oracle Database 19c to include several STIG-mandated new checks, including checks for users that are locally authenticated, users with passwords about to expire, database file placement, and use of known listener ports. Similar to the existing support for different compliance standards such as CIS and GDPR, we now also have a updated STIG comprehensive review section.
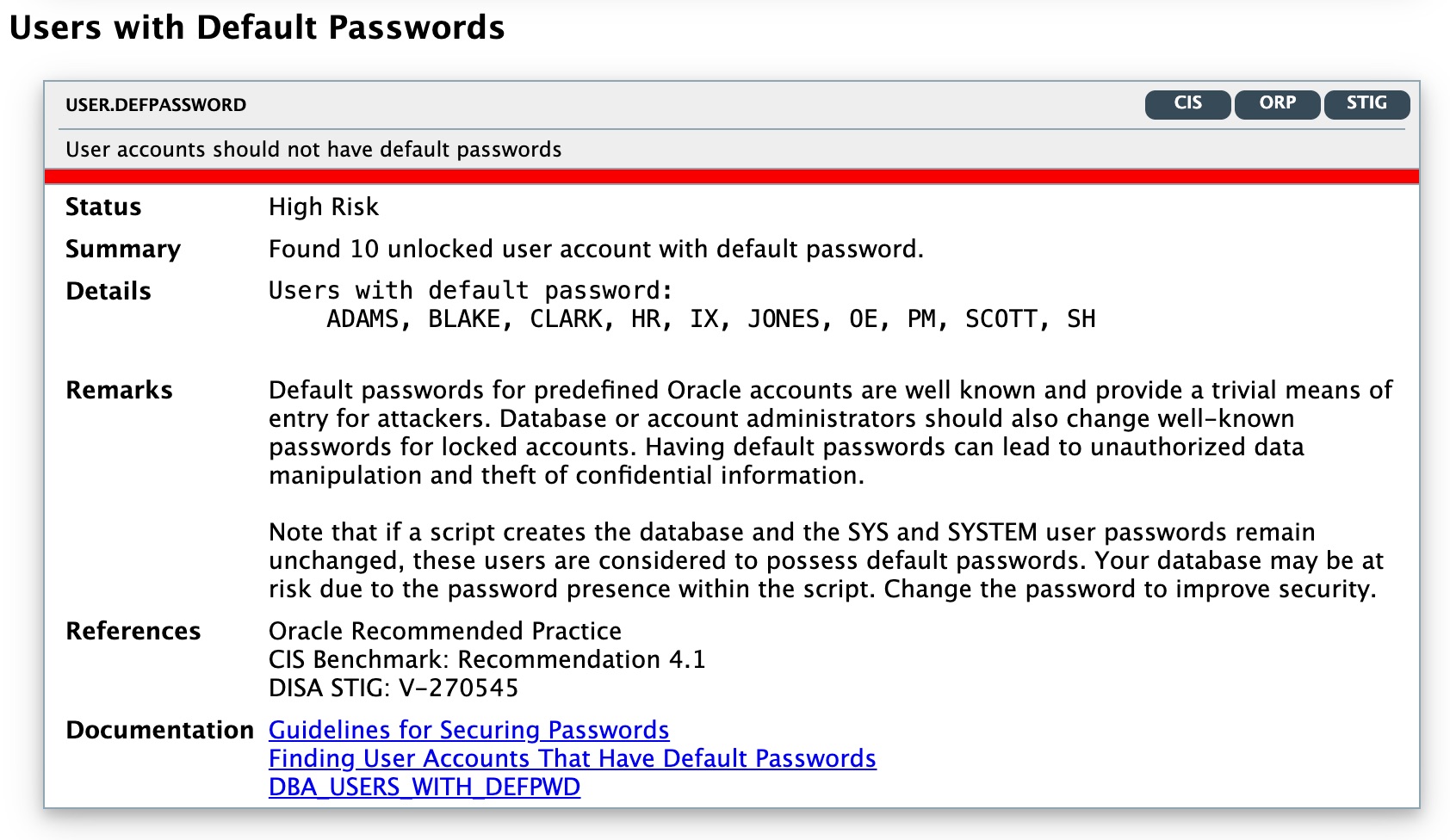
2. Expanded User and Entitlement Assessment
What’s new: Database breaches that aren’t part of a ransomware attack almost always involve compromised database accounts. Most security experts agree that users are the weakest link in the security chain. DBSAT 4.0 adds new checks on user accounts, including users who haven’t logged in for a while (stale accounts), users with passwords expiring within the next 30 days, and locally managed users.
User privilege checks now include the new Oracle Database 23ai schema privileges and which users can modify database resource management plans. Privilege checks now drill deeper, highlighting the rights of proxy users, including those with access to the powerful DBA role.
As Database Vault plays such a major role in controlling privileged user access to data, we’ve included checks on Database Vault setup and separation of duties. Data Redaction and Label Security also receive stronger inspections, with more policy details included in the DBSAT report.
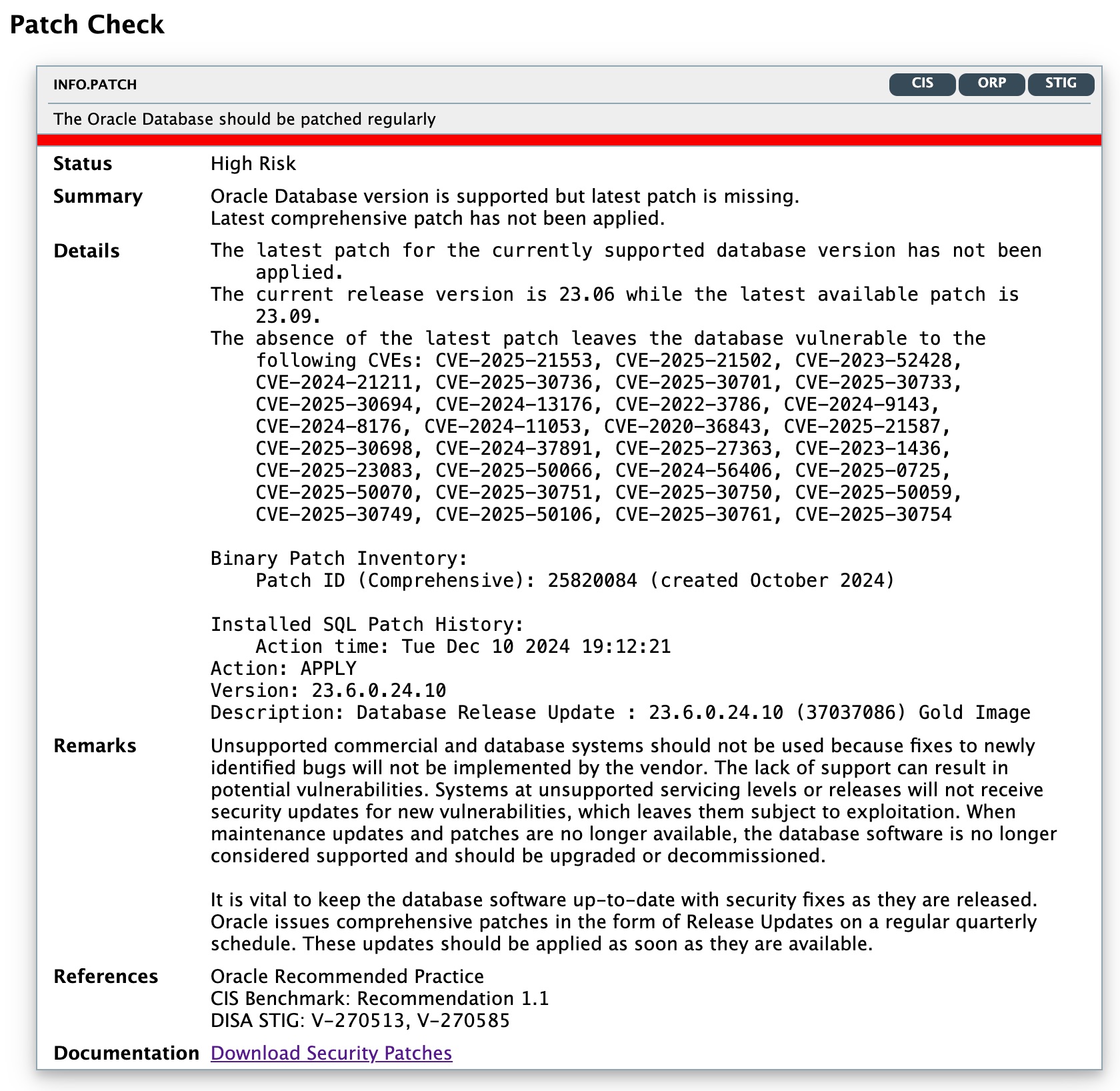
3. Improved Visibility into Unpatched CVEs
The quarterly database release updates (DBRU) not only include fixes for stability and reliability, but also contain fixes for publicly disclosed vulnerabilities identified by Common Vulnerabilities and Exposures (CVE) IDs, along with their associated Common Vulnerability Scoring System (CVSS) severity ratings. As databases with open CVEs are vulnerable to external attacks, it is important to apply DBRU as quickly as possible.
DBSAT 4.0 now provides direct visibility into the open CVEs on your database helping you prioritize patching and help maintain a strong security posture.
4. Focus on Container Databases
DBSAT 4.0 now includes new checks on container databases. These checks include which users have the SET CONTAINER privilege (allowing them to switch between containers and potentially run commands across multiple containers). There is also a look at PDB lockdown profiles settings, which not only let you understand what your lockdown profiles are doing, but if you are using Data Safe or Audit Vault and Database Firewall, will also allow you to track changes to lockdown profiles.
5. Contextual Documentation for Findings
Security findings earlier were broader and lacked immediate context and clarity. Now, direct documentation links appear alongside findings for Oracle Database 19c and 23ai. Each finding provides a release-specific path to help you resolve the issue, accompanied by supporting references.
6. Improved Usability and Integration with External Tools
Security tools that don’t fit real workflows bog down teams. DBSAT 4.0 adds advanced command-line options for easier automation and troubleshooting. For example, you can now specify a single file format for the DBSAT report with the -f flag. Using the new -d flag will display diagnostics information and generate a log file that can be helpful in troubleshooting.
DBSAT Discoverer introduces a new JSON output format, enabling the report to be more easily analyzed by SIEM or data analysis tools. Additionally, it now utilizes more accurate discovery patterns and includes information about sensitive data in database views.
Want to Easily Assess Security for Groups of Databases?
DBSAT is included with every Oracle Database license and does security assessment for one database at a time.
If you want to assess multiple databases or do cloud-scale assessments, we suggest that you use Oracle Data Safe cloud service, that lets you check multiple cloud and on-premises databases at once using the same checks included in DBSAT. If you prefer not to use a cloud service, Oracle Audit Vault and Database Firewall (AVDF) offers the same capabilities to assess and report on security across large groups of databases. Both Data Safe and Audit Vault allow you to set security baselines, detect drift, and automate reporting for all of your Oracle databases very easily.
How To Get Started
Download DBSAT 4.0 from oracle.com or My Oracle Support (Doc ID 2138254.1), unzip, collect data from your database, and create the report. Security assessment requires just three simple commands!
- Unzip: unzip dbsat.zip
- Collect: ./dbsat collect dbsat_admin@pdb1 pdb1assessment
- Report: ./dbsat report pdb1assessment
- Extract: ./dbsat extract pdb1assessment_report
Sensitive data discovery is equally easier – provide connection details and some information about the sensitive types you are interested in the config file, and you are ready to go:
- ./dbsat discover -c Discover/conf/custom_dbsat.config pdb1
- ./dbsat extract pdb1_discover
For step-by-step installation and usage instructions, see the Oracle Database Security Assessment Tool User Guide.
Hands-on Labs
Try Oracle LiveLabs for free and get hands-on with DBSAT, Oracle Data Safe, and Audit Vault and Database Firewall.
