During the Oracle Solaris 11 launch (November 2011) one of the questions I was asked from the audience was from a retail customer asking for documentation on how to configure Oracle Solaris to pass a PCI-DSS audit. At that time we didn’t have anything beyond saying that Oracle Solaris was secure by default and it was no longer necessary to run the Solaris Security Toolkit to get there. Since then we have produced a PCI-DSS white paper with Coalfire (a PCI-DSS QSA) and we have invested a significant amount of work in building a new Compliance Framework and making compliance a “lifestyle” feature in Solaris core development. We delievered OpenSCAP in Oracle Solaris 11.1 since SCAP is the foundation language of how we will provide compliance reporting. In Oracle Solaris 11.2 we added a new command compliance(1M) for running system assesments against security/compliance benchmarks and for generating html reports from those. A lot of work went into generating the content as well as the framework, and we have been continuously updating and adding the check rules.
When we introduced the compliance framework in Oracle Solaris 11.2 there was no easy way to customise (tailor) the policies to suit individual machine or site deployment needs. While it was certainly possible for users familiar with the XCCDF/OVAL policy language it wasn’t easy to do in away that preserved your customisations while still allowing access to new and policy rules when the system was updated. To address this a new subcommand for compliance(1M) was added in Oracle Solaris 11.3 that allows proides for this customisation. The initial release of tailoring in Oracle Solaris 11.3 allows the enabling and disabling of individual checks, later we added variable level customisation.
There is more functionality for compliance planned for future update releases, but for now here is a reminder of how easy it is to get started with compliance reporting:
# pkg install security/compliance # compliance assess # compliance report
That will give us an html report that we can then view. Since we didn’t give any compliance benchmark name it defaults to ‘Solaris Baseline’, so now lets install and run the PCI-DSS benchmark. The ‘security/compliance’ package has a group dependency for ‘security/compliance/benchmark/pci-dss’ so it will be installed already but if you don’t want it you can remove that benchmark and keep the others and the infrastructure.
# compliance assess -b pci-dss Assessment will be named 'pci-dss.Solaris_PCI-DSS.2014-04-14,16:39' # compliance report -a pci-dss.Solaris_PCI-DSS.2014-04-14,16:39
That will give you the path to an HTML report file that you can view in your browser. The full report has a summary section, over all score at the top, for example:
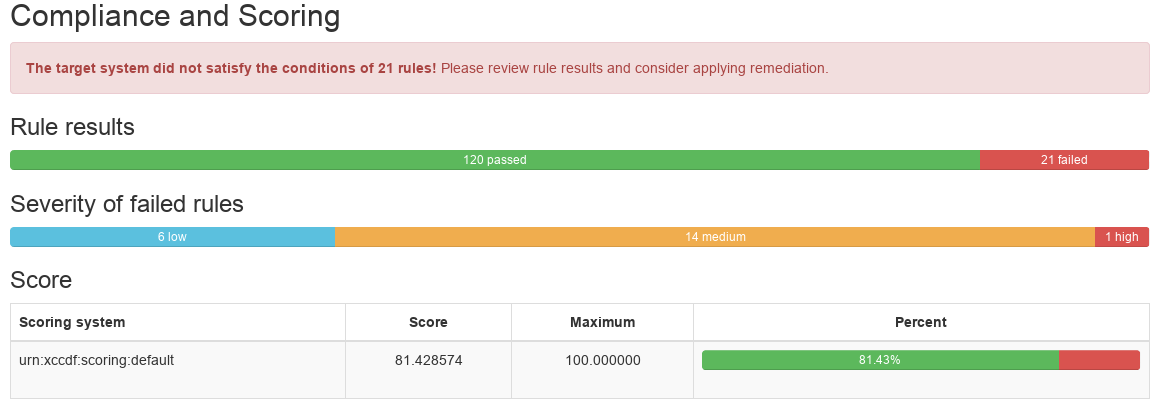
This is followed by the details of each of the checks and their pass/fail status:
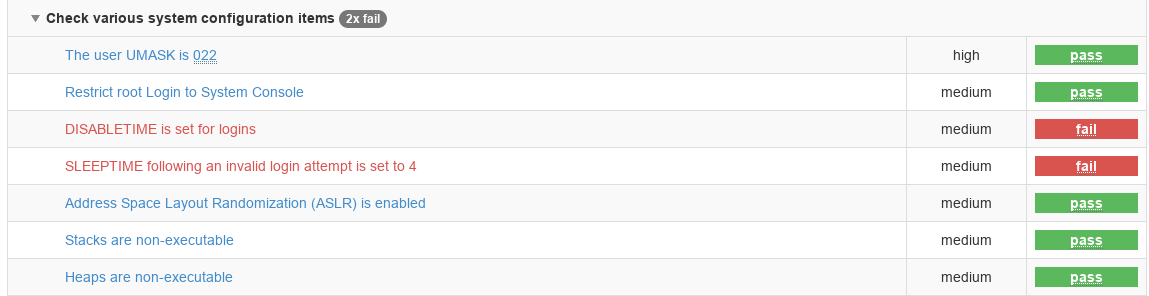
The report is interactive and we can filter it to show only the failing results but we can also do that when we generate the report from the CLI like this:
# compliance report -s fail -a pci-dss.Solaris_PCI-DSS.2014-04-14,16:39
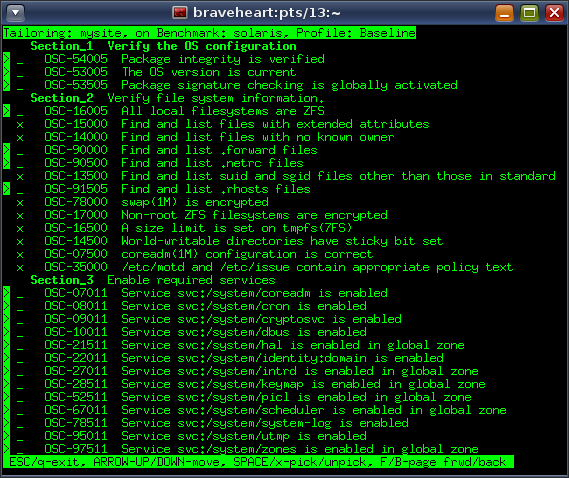
Now lets say we want to turn off some of those checks that are failing because they are not relevant to our deployment. The simplest way of using ‘compliance tailor’ is use the interactive pick tool:
# compliance tailor -t mysite *** compliance tailor: No existing tailoring 'mysite', initializing tailoring:mysite> pick
The above shows the interactive mode where using ‘x’ or ‘space’ allows us to enable or disable an individual test. Note also that since the Oracle Solaris 11.2 release all the tests have been renumbered and now have unique rule identifiers that are stable across releases. The same rule number always refers to the same test in all of the security benchmark policy files delivered with the operating system.
When exiting from the interactive pick mode just type ‘commit’ to write this out to a locally installed tailoring; that will create an XCCDF tailoring file under /var/share/compliance/tailorings. The XML tailoring files should not be copied across update releases, instead use the export functionality.
The ‘export’ action for the tailoring subcommand that allows you to save off your customisations for importing into a different system, this works similarly to zonecfg(1M) export.
$ compliance tailor -t mysite export | tee /tmp/mysite.out set tailoring=mysite # version=2015-06-29T14:16:34.000+00:00 set benchmark=solaris set profile=Baseline # OSC-16005: All local filesystems are ZFS exclude OSC-16005 # OSC-15000: Find and list files with extended attributes include OSC-15000 # OSC-35000: /etc/motd and /etc/issue contain appropriate policy text include OSC-35000
The saved command file can then be used for input redirection to create the same tailoring on another system. You should assume that over time new checks will be added so you will want to periodically, and certainly at update release boundaries, review the list of included and excluded checks.
To run an assessment of the system using a tailoring we simply need to do this:
# compliance assess -t mysite Assessment will be named 'mysite.2015-06-29,15:22' Title Package integrity is verified Rule OSC-54005 Result PASS ...
We have more exciting functionality planned for the future. When Oracle Solaris 11.4 beta is available I’ll be describing some of the new compliance features we have been working on including remote assesment, and graphing historical assesments in the new Web Dashboard.