Don’t be so quick to place blame on external bad actors, IT, or a database administrator. Sophisticated cyber-attacks have increased in the past few years, and it’s almost an everyday incident, but can your business rule out that it was not someone on the inside versus the outside?
Loss of sensitive data, stolen credentials, identity theft, loss of privacy, and others can be prevented when businesses modernize their database configuration management and security compliance management practices.
Often in IT organizations, the focus of breach prevention is on external actors, yet the risk from internal actors is just as high. Privilege misuse and stolen credentials are the most common intentional actions by internal actors for malicious reasons according to reports like Verizon’s 2023 Data Breach Investigations Report (DBIR).
To truly secure and prevent unauthorized access to sensitive data, automated database configuration, and patching security assessment to known industry security standards and best practices must be implemented on day one of database deployment.
Oracle Enterprise Manager (EM) publishes industry and regulatory security compliance standards such as Center for Internet Security (CIS) Benchmarks and Department of Defense (DoD) Security Technical Implementation Guides (STIG). Your organization can use or customize them to create specific security controls that align with your company’s security policies.
The Center for Internet Security publishes CIS Critical Security Controls (CSC) to help organizations better defend against known attacks by distilling key security concepts into actionable controls to achieve greater overall cybersecurity defense. To make it easy to effectively implement these Controls, CIS created three Implementation Groups (IGs) – IG1 (essential cyber hygiene), IG2 (additional set of safeguards), and IG3 (secure sensitive and confidential data). The recommendation is for enterprises to at least implement controls in Implementation Group 1 (IG1) to ensure essential cyber hygiene.
Oracle Enterprise Manager CIS Benchmarks, included as part of the Database Lifecycle Management (DBLM) pack, supports more than 100 unique security controls covering all three Implementation Groups (IGs) that encompass:
- Database parameter settings for listeners and databases
- Oracle connection and login restrictions
- Database users to check for default passwords.
- Privileges, grants, and access control to revoke public and excessive privileges.
- Audit/Logging policies and procedures.
Minimize administrative privileges with principles of zero trust essential for cyber hygiene
Limiting administrative privileges by following the principles of zero trust to prevent privilege misuse is essential for cyber hygiene (IG1). Oracle Enterprise Manager CIS Benchmark has controls that give insight into privileges, and operations that database users perform for auditing requirements.
As an example, Figure 1 shows CIS Benchmark for Oracle Database 19c control to ensure ‘ALL’ is revoked from unauthorized GRANTEE on AUD$. Below are the details of the control, rationale, remediation, and how this control maps to CIS Controls.
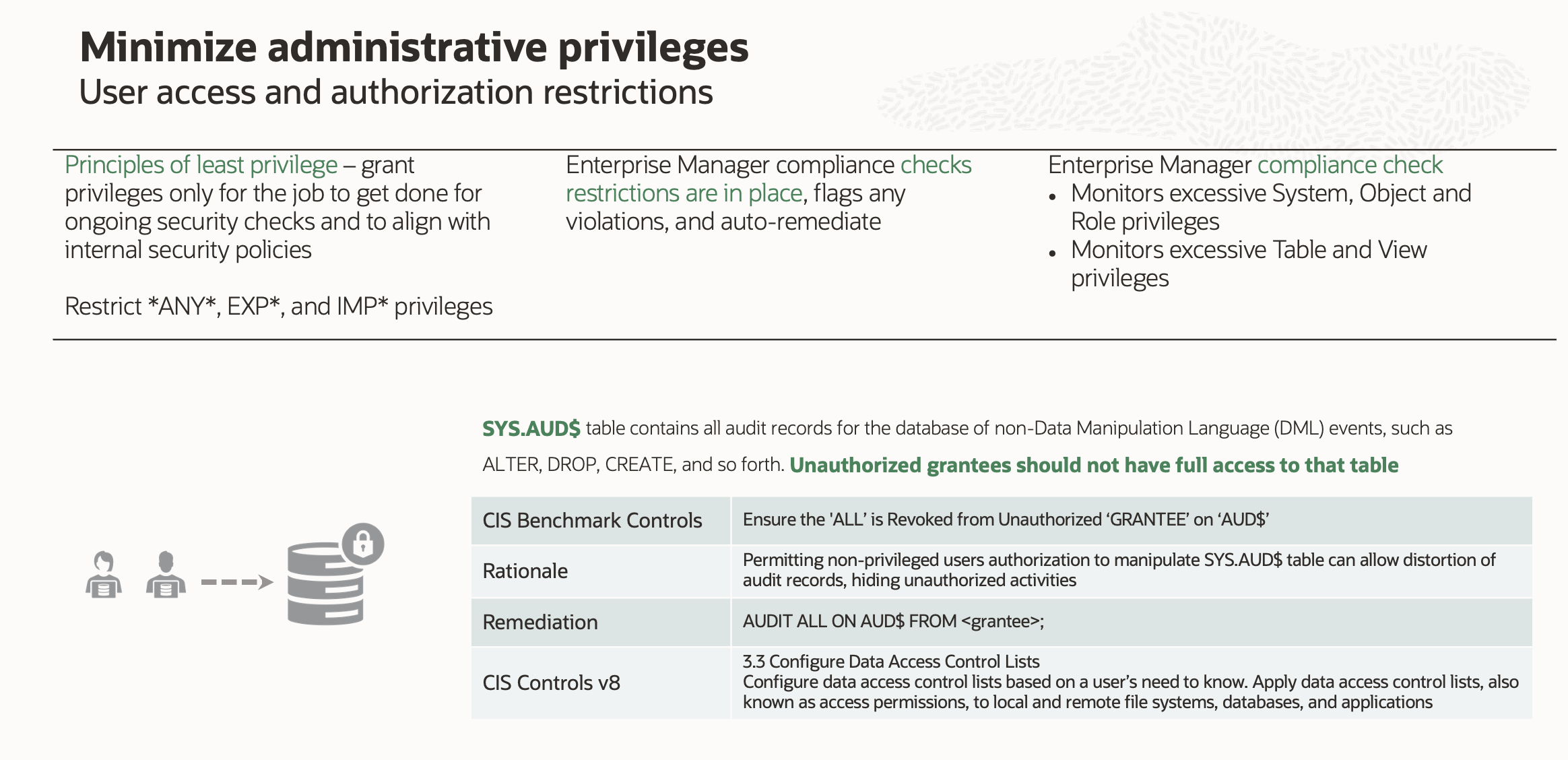
Essential cyber hygiene (IG1) control in CIS Benchmark for Oracle Database 19c ensures unauthorized users don’t have access
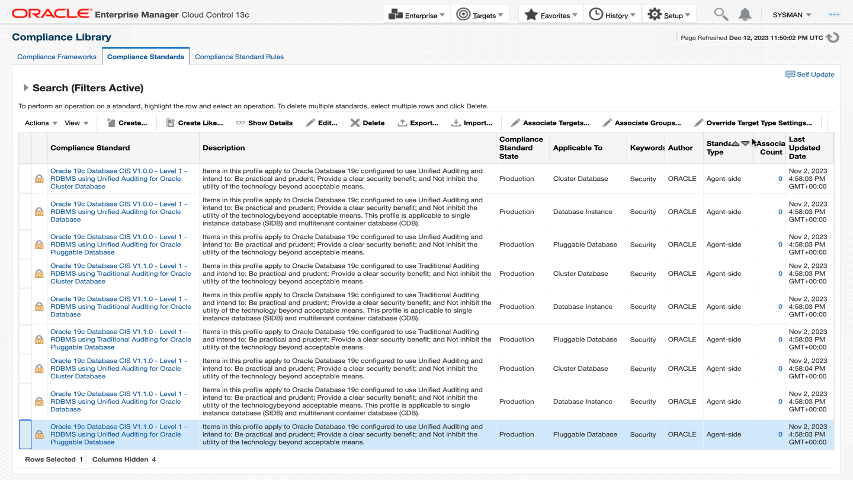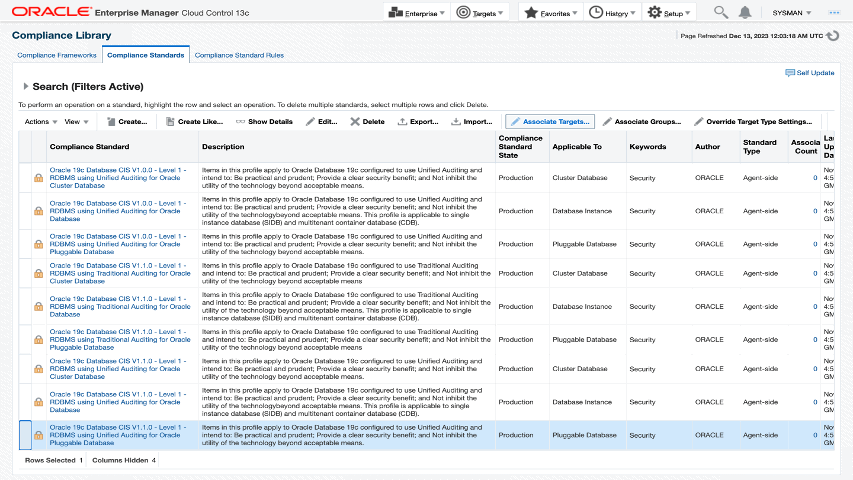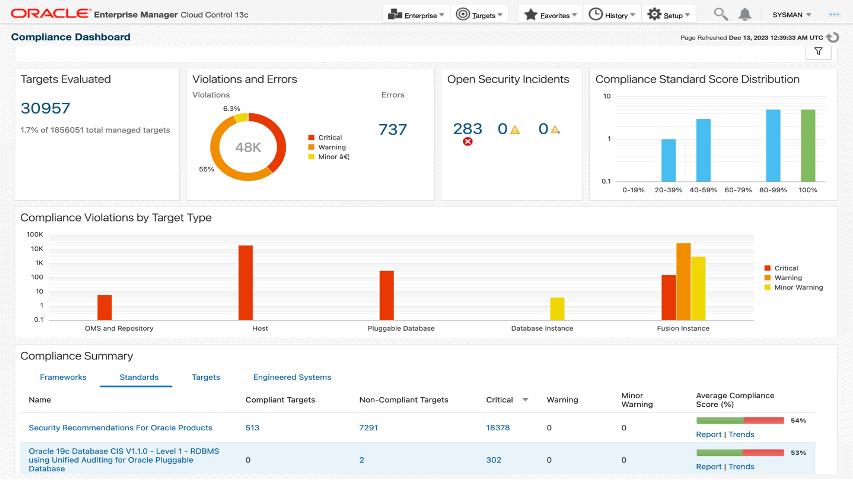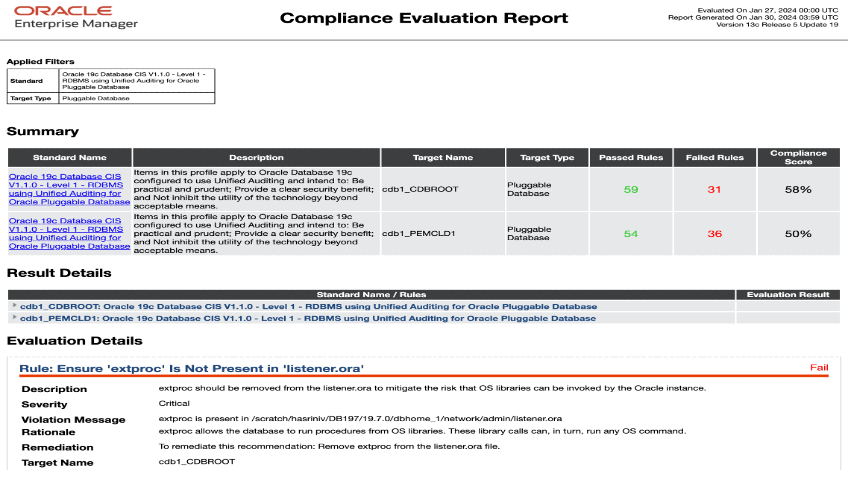
Figure 2 is another example of essential cyber hygiene (IG1) control in CIS Benchmark for Oracle Database 19c is related to ensuring unauthorized users don’t have access to sensitive tables. Below are the details of the control, rationale, remediation, and how this control maps to CIS Controls.
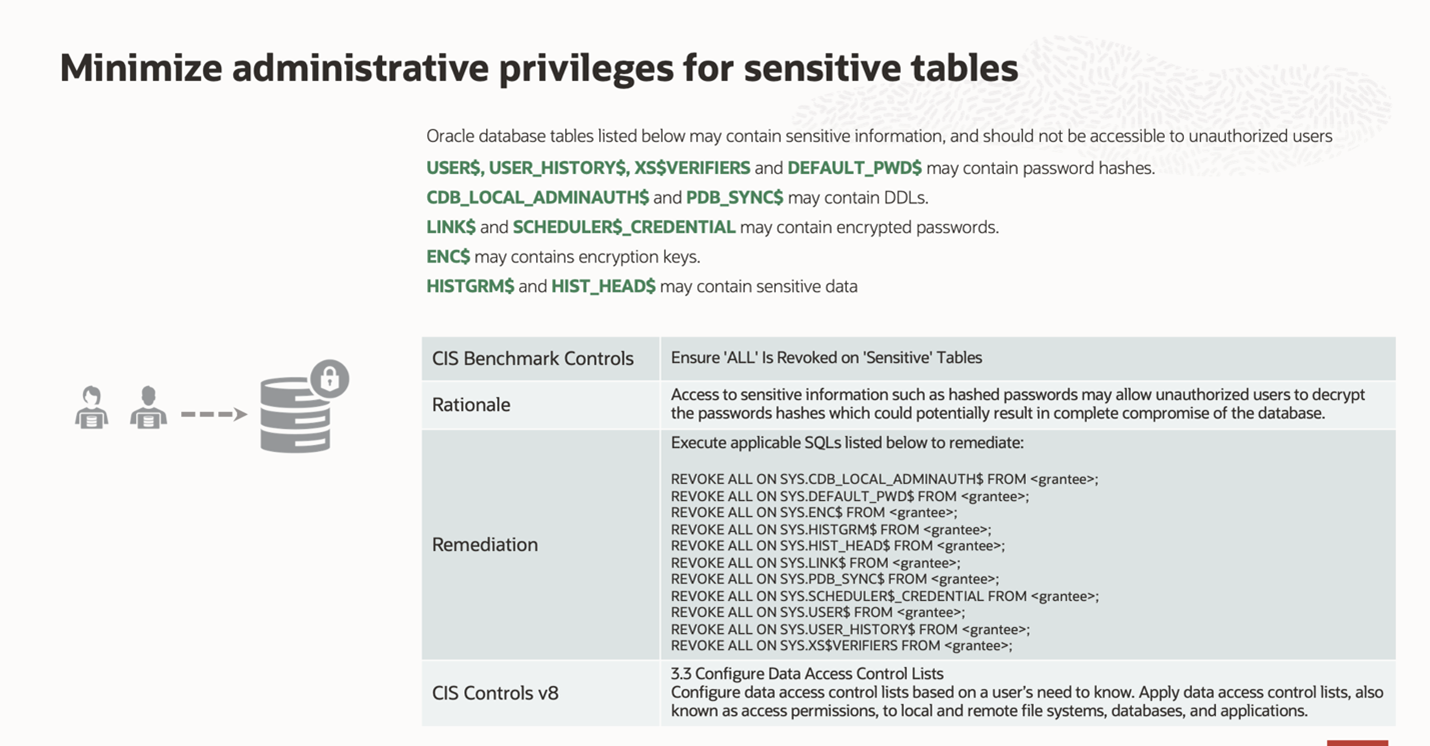
CIS Benchmark provides standard Oracle audit controls for object, statement, and privilege auditing
Administrative privileges provided to limited users, and other CIS Controls implemented, enable the audit of all activities. CIS Benchmark provides standard Oracle audit controls for object, statement, and privilege auditing. Figure 3 showcases the control, rationale, and remediation for tracking activities on SYS.AUD$ table. In addition, the mapping of this to specific CIS controls is viewable.
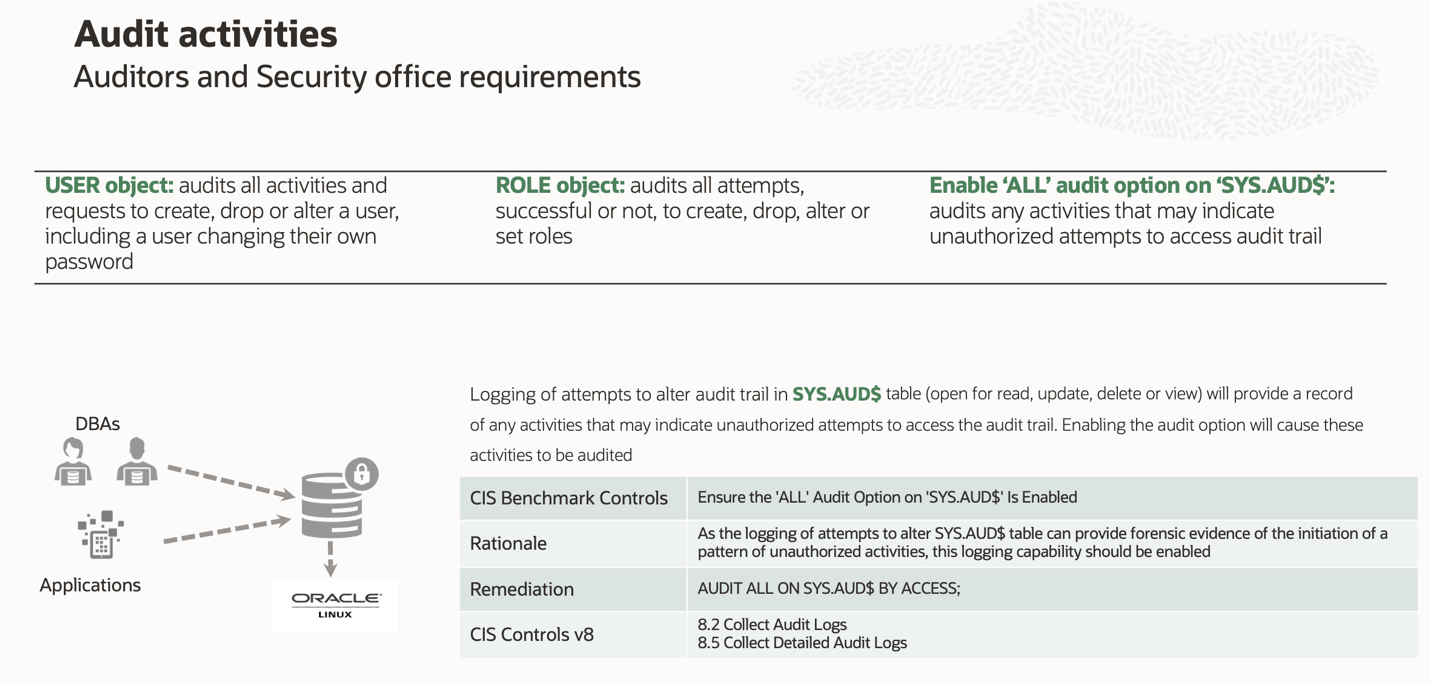
Leveraging the Oracle Enterprise Manager compliance framework has multiple advantages
- One-stop dashboard gives insight into vulnerable databases, security incidence, and overall compliance distribution across all database assets
- Customization of controls to meet your security policies
- Continuous automated checks and remediation of Oracle databases at scale
- Compliance report for internal and external auditing requirements
Oracle Enterprise Manager Compliance dashboard and report for audit
In summary, securing Oracle Databases and hosts through automation and well-defined security controls is crucial. Oracle Enterprise Manager offers a comprehensive compliance solution that enables organizations to modernize their risk governance processes to ensure elevated security posture. By leveraging all the security controls in out-of-the-box CIS Benchmarks, one can ensure deployment of IG3 level in Critical Security Controls (CSC) which is tied to securing sensitive and confidential data to help organizations better defend against known attacks.
